
CISA Alert: Ransomware Gangs Take Advantage of Holidays
It’s not hard to say that many security teams worldwide are understaffed and overworked.
On August 31, 2021, The FBI and the CISA released an advisory: “Ransomware Awareness for Holidays and Weekends” aiming to mention confronted risks during out-of-office times by observing ransomware attacks in the United States as soon as the July 4th holiday in 2021. The report is created considering recent actor tactics, techniques, and procedures (TTPs) with mitigations to deal with cyber threats. Here is a snapshot of the CISA directives.
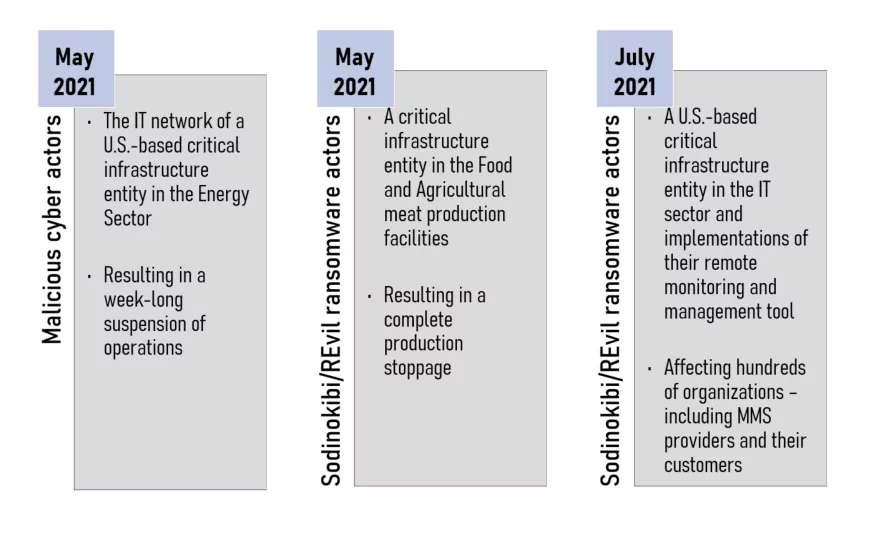
Overview: Significant Ransomware Incidents on Holidays
Since network defenders and IT support organizations are at limited capacity on holidays and weekends, these timeframes are appropriate for malicious actors’ head start. CISA spotted several ransomware attacks below that occurred on off-days:
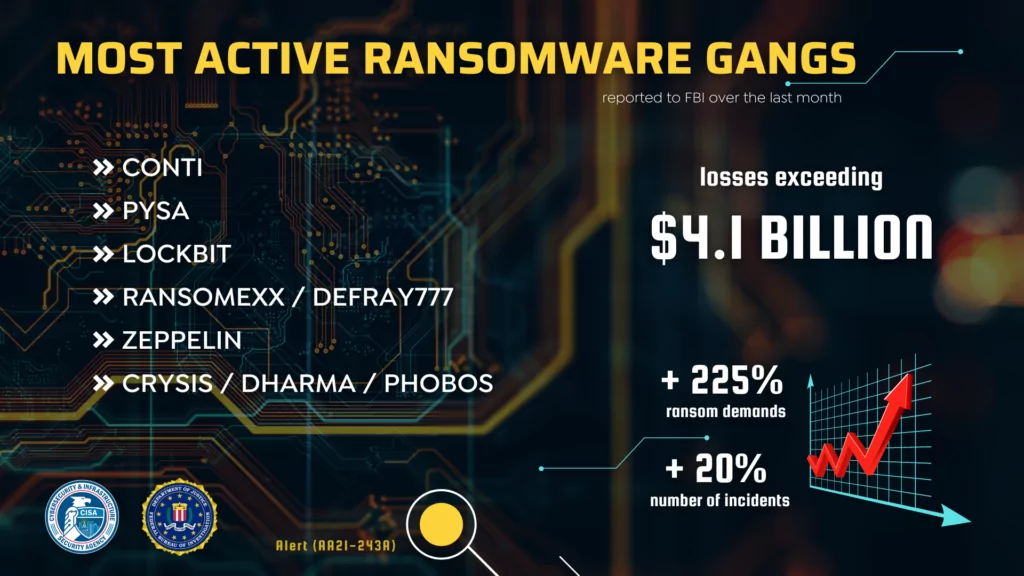
The advisory offers some statistics extracted from the FBI’s Internet Crime Complaint Center (IC3) including startling losses exceeding $4.1 billion.
The active ransomware groups mentioned in the advisory are also continually monitored by SOCRadar platform: Conti, PYSA, LockBit, RansomEXX/Defray777, Zeppelin, Crysis/Dharma/Phobos.
Common Techniques for Initial Infection
→ The two most preferred techniques performed by cybercriminals are
- Phishing
- Brute forcing unsecured RDP endpoints.
→ The additional common means of initial infection are
- deployment of precursor or dropper malware exploitation of software or operating system vulnerabilities
- exploitation of managed service providers with access to customer networks; and the use of valid, stolen credentials
Capabilities of Precursor Malware
- To conduct reconnaissance on victim networks
- To steal credentials
- To escalate privileges
- To exfiltrate information
- To move laterally on the victim network
- To obfuscate command-and-control communications
How to Hunt Threats
Threat hunting is possible obtaining certain strategies:
→ Understand the IT environment’s routine activity and architecture by establishing a baseline.
→ Review data logs.
→ Employ intrusion prevention systems and automated security alerting systems.
→ Deploy honeytokens.
How to Detect Suspicious Early Warning Signals
You can look for the early signals listed below to detect the attacks:
→ Unusual inbound and outbound network traffic,
→ Compromise of administrator privileges or escalation of the permissions on an account,
→ Theft of login and password credentials,
→ Substantial increase in database read volume,
→ Geographical irregularities in access and log in patterns,
→ Attempted user activity during anomalous logon times,
→ Attempts to access folders on a server that are not linked to the HTML within the pages of the web server, and
→ Baseline deviations in the type of outbound encrypted traffic since advanced persistent threat actors frequently encrypt exfiltration.
All in all, CISA Advisory includes threat overview in holidays and weekends, shares threat hunting strategies with ransomware practices and mitigations which are not included in the summary.
Full report can be accessed here:
Discover SOCRadar® Free Edition
With SOCRadar® Free Edition, you’ll be able to:
- Discover your unknown hacker-exposed assets
- Check if your IP addresses tagged as malicious
- Monitor your domain name on hacked websites and phishing databases
- Get notified when a critical zero-day vulnerability is disclosed
Free for 12 months for 1 corporate domain and 100 auto-discovered digital assets.
Try for free



































