
CISA Highlights Critical Adobe Security Updates for Acrobat, Magento, and More (CVE-2024-20738, CVE-2024-20719, CVE-2024-20720)
[Update] April 6, 2024: “Threat Actors Exploit CVE-2024-20720 in Magento to Deploy Backdoors”
In a recent alert, CISA highlighted Adobe’s release of security updates to address multiple vulnerabilities across various software products. The most severe vulnerabilities impact Adobe Commerce, Magento, Acrobat and Reader, and FrameMaker Publishing Server.
CISA warns that attackers could exploit some of these vulnerabilities to take control of affected systems. Organizations are advised to review the latest security issues and implement measures to prevent exploitation.
In this blog post, we will outline the most concerning vulnerabilities addressed in Adobe’s updates and provide guidance on elevating your vulnerability management efforts.
Details of the Latest Adobe Vulnerabilities
Below are the most concerning vulnerabilities addressed by Adobe in the recent updates, along with the affected versions of the products:
Adobe Commerce and Magento
Adobe Commerce, known as Magento Commerce before Adobe’s acquisition, is a flexible and scalable commerce platform that enables businesses to create tailored B2B and B2C experiences.
CVE-2024-20719 (CVSS: 9.1): A Stored Cross-site Scripting (XSS) vulnerability affecting Adobe Commerce and Magento, which can lead to arbitrary code execution. Successful exploitation requires the attacker to be authenticated and have admin privileges.
CVE-2024-20720 (CVSS: 9.1): This vulnerability results from Improper Neutralization of Special Elements, leading to OS Command Injection. Like the previous vulnerability, authentication and elevated privileges are prerequisites for exploitation.
Affected Versions (on all platforms):
| Adobe Commerce | 2.4.6-p3 and earlier
2.4.5-p5 and earlier 2.4.4-p6 and earlier 2.4.3-ext-5 and earlier 2.4.2-ext-5 and earlier 2.4.1-ext-5 and earlier 2.4.0-ext-5 and earlier 2.3.7-p4-ext-5 and earlier |
| Magento Open Source | 2.4.6-p3 and earlier
2.4.5-p5 and earlier 2.4.4-p6 and earlier |
Adobe FrameMaker Publishing Server
Adobe FrameMaker Publishing Server is an enterprise software solution. It helps companies streamline the process of distributing extensive technical content produced within Adobe FrameMaker to various channels, formats, and devices.
CVE-2024-20738 (CVSS: 9.8): This vulnerability affects Adobe FrameMaker Publishing Server Version 2022 Update 1 and earlier, leading to an Improper Authentication issue and resulting in a Security Feature Bypass. The exploitation of the vulnerability does not require any privileges, and the attack complexity is considered low.
Adobe Acrobat and Reader
Acrobat is a set of tools and services by Adobe, providing users with the capability to generate, view, modify, and digitally sign PDF documents. There are two primary components: Adobe Acrobat Reader, a no-cost PDF viewer, and Adobe Acrobat, a paid software enabling users to create, edit, merge, and transform PDF files.
CVE-2024-20731 (CVSS: 8.8): A high-severity Use-After-Free vulnerability, posing the risk of arbitrary code execution. Exploiting this vulnerability necessitates user interaction.
Affected Versions (on Windows and macOS):
| Acrobat DC | 23.008.20470 and earlier versions |
| Acrobat Reader DC | 23.008.20470 and earlier versions |
| Acrobat 2020 | 20.005.30539 and earlier versions |
| Acrobat Reader 2020 | 20.005.30539 and earlier versions |
Given the widespread use of Adobe products in various business environments, addressing these vulnerabilities promptly is important. Some of these vulnerabilities could potentially enable attackers to execute arbitrary code, leading to serious consequences. It is advisable to upgrade to the latest secure versions of affected Adobe products to mitigate these risks effectively.
For the latest updates and information on other vulnerabilities affecting Adobe products, see CISA’s alert.
Threat Actors Exploit CVE-2024-20720 in Magento to Deploy Backdoors
Researchers have discovered that threat actors are capitalizing on the critical Magento vulnerability, CVE-2024-20720, to implant a persistent backdoor into e-commerce stores. Sansec reports that the attackers utilized XML code insertion into the layout_update database table. This method facilitated the automatic injection of XML code, allowing them to continually infect the system.
In their analysis, the researchers observed attackers combining the Magento layout parser with the beberlei/assert package, which comes pre-installed, to execute system commands. This execution occurs whenever <store>/checkout/cart is accessed, allowing attackers to establish persistent remote code execution via POST commands.
Utilizing this method, attackers delivered a Stripe payment skimmer, with captured data redirected to hxxps://halfpriceboxesusa[.]com/pub/health_check.php, potentially another compromised Magento store.
To safeguard Magento-based e-commerce sites, administrators are strongly advised to promptly update to versions 2.4.6-p4, 2.4.5-p6, or 2.4.4-p7 and conduct scans for any indicators of malicious actions.
Insights with SOCRadar’s Vulnerability Intelligence
Access comprehensive details regarding vulnerabilities with SOCRadar’s Vulnerability Intelligence module, including exploitability, available exploits, repositories, and updates. This module also enables you to search for vulnerabilities affecting a specific product or vendor, providing detailed information to enhance your cybersecurity posture.
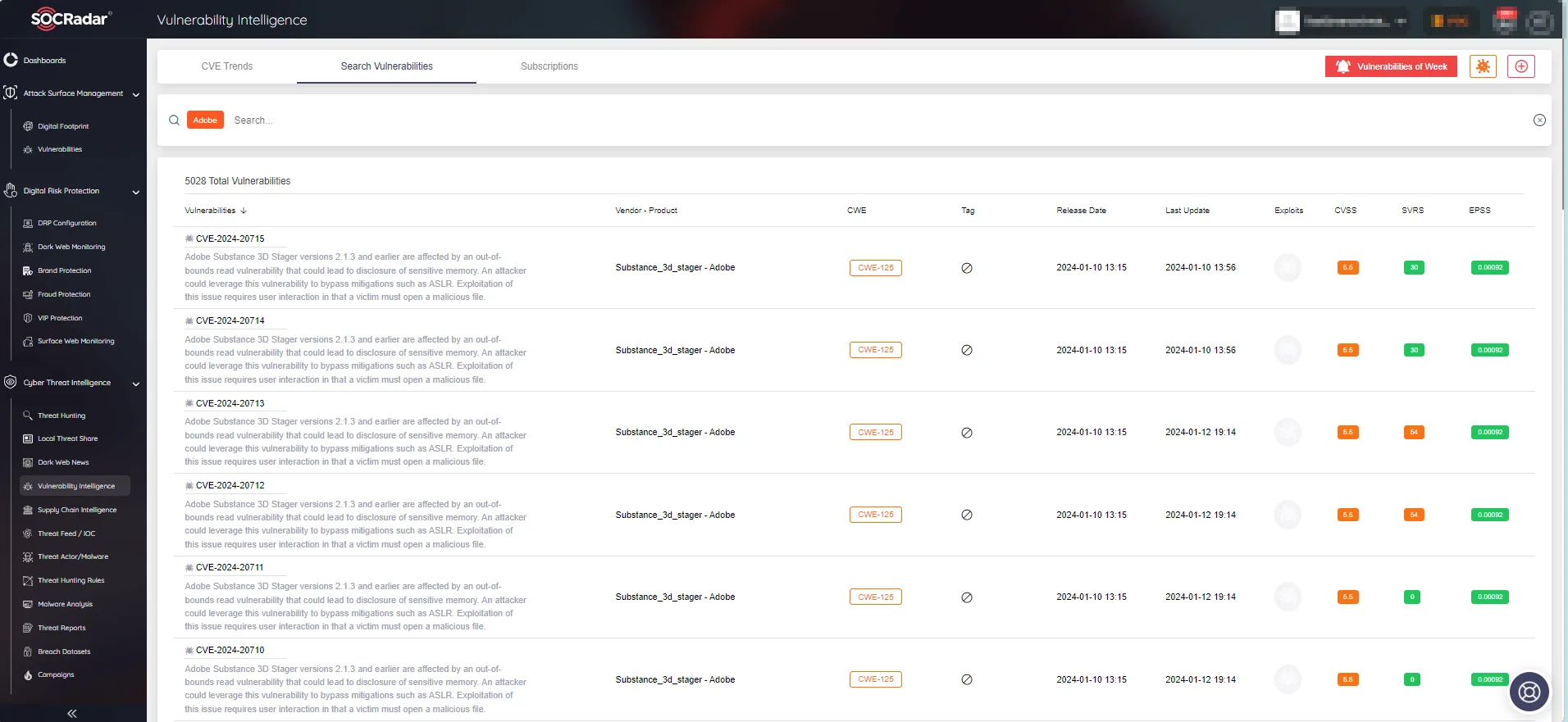
SOCRadar’s Vulnerability Intelligence


































