CISA Issues ICS Advisories on Mitsubishi, Delta, Franklin Electric, BD & Unitronics PLCs’ Active Exploitation
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has recently issued four new advisories for Industrial Control Systems (ICS).
CISA released the advisories on November 28, 2023, regarding current security issues, vulnerabilities, and exploits affecting ICS products of Delta Electronics, Franklin Electric, Mitsubishi, and BD.
Accompanying the release of these ICS advisories, CISA has also released an advisory about Unitronics Programmable Logic Controllers’ (PLCs) active exploitation, to provide information and guidance.
Critical Vulnerabilities in Delta Electronics InfraSuite Device Master Could Allow RCE
Delta Electronics’ InfraSuite Device Master, versions 1.0.7 and prior are affected by multiple vulnerabilities. CISA notes that exploiting these ICS vulnerabilities successfully could enable an attacker to execute arbitrary code and acquire plaintext credentials. Additionally, these vulnerabilities involve low attack complexity and are susceptible to remote exploitation.

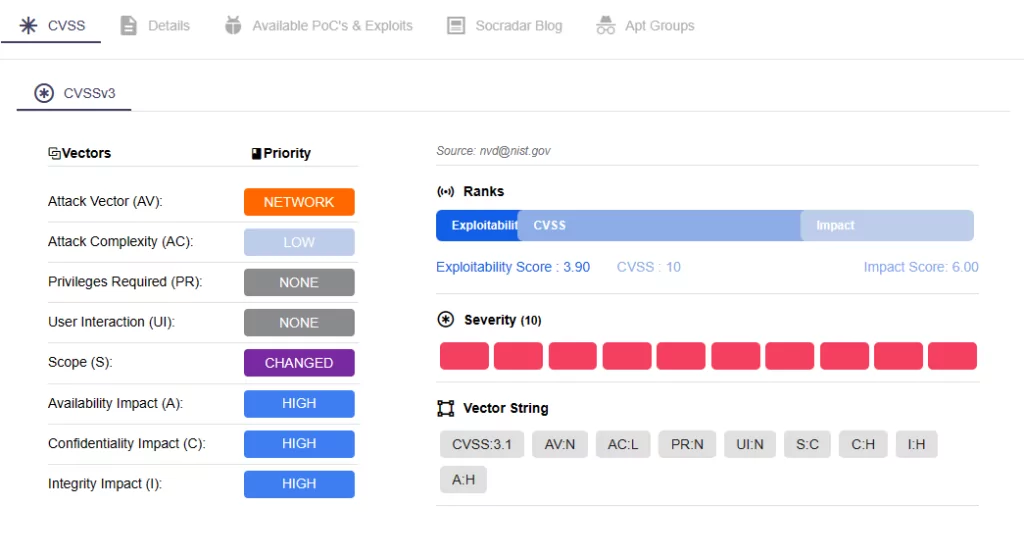
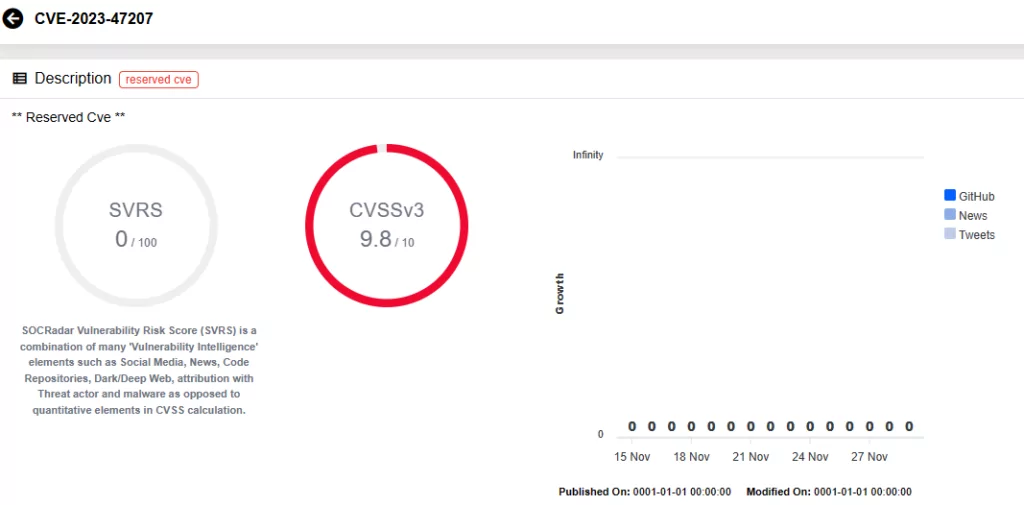
CVE-2023-47207 (CVSS Score: 9.8, Critical): It could allow an unauthenticated attacker to execute code with local administrator privileges.
CVE-2023-39226 (CVSS Score: 9.8, Critical): It could allow an unauthenticated attacker to execute arbitrary code via a single UDP packet.
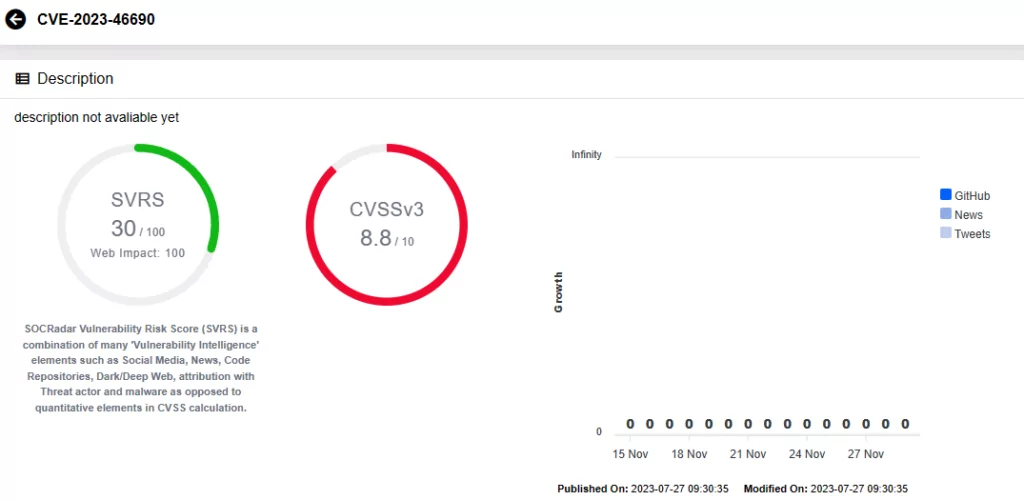
CVE-2023-46690 (CVSS Score: 8.8, High): The vulnerability could allow an attacker to write to any file in any location of the file system, which could lead to Remote Code Execution (RCE).
CVE-2023-47279 (CVSS Score: 7.5, High): The vulnerability could enable an unauthenticated attacker to disclose user information via a single UDP packet, obtain plaintext credentials, or perform NTLM traversal.
Franklin Electric Fueling Systems Colibri Is Vulnerable to Path Traversal
The advisory pertaining to Franklin Electric Fueling Systems details a single vulnerability impacting the FFS Colibri product, which carries a medium severity score.
CVE-2023-5885 (CVSS Score: 6.5, Medium): The discontinued FFS Colibri product allows a remote user to access files on the system, including files containing login credentials of other users.
Mitsubishi Electric GX Works2 Vulnerabilities Could Lead to DoS Attacks
Mitsubishi Electric’s GX Works2, across all versions, is susceptible to two vulnerabilities outlined in the advisory: CVE-2023-5274 and CVE-2023-5275. These vulnerabilities can allow an attacker to cause a Denial-of-Service (DoS) condition within the simulation function of GX Works2.

The vulnerabilities stem from improper input validation, and exploitation occurs when the attacker sends specifically crafted packets. However, the attacker must send the packets from the personal computer running the function.
Both CVE-2023-5274 and CVE-2023-5275 carry a low CVSS score of 2.9.
Multiple Vulnerabilities in BD FACSChorus Pose Security Risks
The advisory for Becton, Dickinson and Company (BD) lists a total of seven vulnerabilities, with CVSS scores ranging from 2.4 to 5.4. According to the CISA ICS advisory, the vulnerabilities affect BD FACSChorus’ HP Z2 G9 workstation, in several versions: v3.0, v3.1, v5.0 and v5.1.
CISA cautions that an attacker with physical access to the device can exploit these vulnerabilities to alter configurations, access sensitive data, or manipulate system components.

Vulnerabilities affecting BD FACSChorus v5.0, v5.1, v3.0 and v3.1:
CVE-2023-29060 (CVSS Score: 5.4, Medium): The respective workstation operating system does not restrict which devices can interact with USB ports. If exploited, a threat actor with physical access to the workstation could gain access to system information and potentially infiltrate data.
CVE-2023-29061 (CVSS Score: 5.2, Medium): The vulnerability occurs because the workstation does not have a BIOS password. A threat actor with physical access to the workstation has the potential to exploit this vulnerability to access the BIOS configuration and change the drive boot order and BIOS pre-boot authentication.
CVE-2023-29062 (CVSS Score: 3.8; Low): The operating system hosting the FACSChorus application is configured to allow the transmission of hashed user credentials upon user action without adequately authenticating the requested resource. This is possible through the use of LLMNR, MBT-NS or MDNS and results in NTLMv2 hashes being sent to a malicious entity location on the local network. These hashes can then be brute-force attacked and cracked if a weak password is used. This attack will only apply to domain-joined systems.
CVE-2023-29063 (CVSS Score: 2.4, Low): The workstation does not block physical access to PCI express (PCIe) slots, which could allow a threat actor to insert a PCI card designed for memory capture. A threat actor could isolate sensitive information, such as a BitLocker encryption key, from a dump in the workstation RAM during initialization.
Vulnerabilities affecting BD FACSChorus v5.0 and v5.1:
CVE-2023-29064 (CVSS Score: 4.1; Medium): The software contains sensitive information stored in plain text. A threat actor could intercept hard-coded secrets used by the application, including tokens and passwords for administrative accounts.
CVE-2023-29065 (CVSS Score: 4.1; Medium): The software database is directly accessible with the privileges of the currently logged in user. A threat actor with physical access could potentially obtain credentials and use those credentials to modify or destroy data stored in the database.
CVE-2023-29066 (CVSS Score: 3.2; Low): The software does not properly assign data access privileges for operating system user accounts. A non-administrative operating system account can modify information stored in local application data folders.
Municipal Water Authority of Aliquippa Attacked by CyberAv3ngers, Exploiting Unitronics PLCs
CISA issued an advisory in response to active exploitation of Unitronics PLCs. The advisory states that threat actors targeted PLCs used in Water and Wastewater Systems (WWS) sector, notably a Unitronics PLC at a U.S. water facility.
On November 27, 2023, WaterISAC released an advisory about the cyber incident. According to WaterISAC, an Iranian-backed group, CyberAv3ngers, attacked the Municipal Water Authority of Aliquippa in Pennsylvania on November 25, 2023.

Upon discovering the incident, the Aliquippa authority took systems offline. They reported that although the threat actors gained control of a remote booster station serving two townships, there were no known risks to drinking water.
CISA emphasized that attempts to compromise WWS integrity through unauthorized access threaten the ability of WWS facilities. WWS facilities utilize PLCs for water and wastewater treatment processes to supply water, as well for managing compliance data collection, and critical alarm announcements.
It is suggested that threat actors likely exploited cybersecurity weaknesses, such as poor password security and internet exposure, to access the affected device – a Unitronics Vision Series PLC with an HMI.
CISA has provided several recommendations for WWS facilities to bolster security measures against potential threats. These include changing default passwords on PLCs, implementing Multi-Factor Authentication (MFA) for all remote access to the OT network, disconnecting PLCs from the open internet, utilizing a different TCP port than the default, updating devices, and maintaining backups of PLC logic and configurations.
In addition to these recommendations, CISA, in collaboration with WWS sector partners, has developed tools and resources. These resources are available through the advisory.
Review the Advisories and Stay Vigilant with SOCRadar
Stay informed about the latest security vulnerabilities and ensure your products and software are regularly updated.
CISA recommends that administrators and users check the advisories and apply necessary security measures. Any available vendor fixes and mitigations are provided in the advisories.
SOCRadar actively monitors digital assets, issuing alerts whenever a vulnerability is identified and poses a potential threat to your organization’s system.
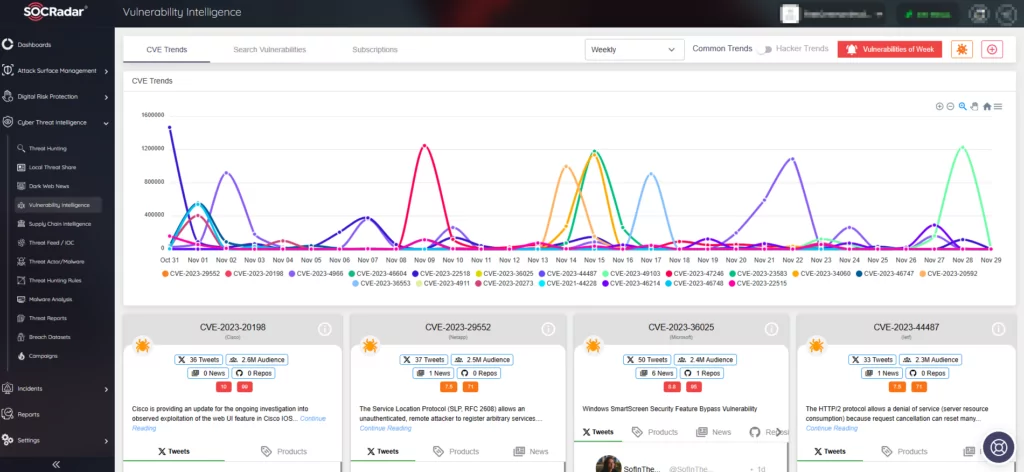
Leverage SOCRadar’s Vulnerability Intelligence to enhance your vulnerability management and patch prioritization. Explore vulnerabilities, access detailed information, and track the lifecycle of each vulnerability through the vulnerability cards available via SOCRadar’s Vulnerability Intelligence. You can also view CVEs’ exploitability status, utilized attack vectors, and complexity: