
CISA KEV 2024 Review: Key Vulnerabilities and Exploitation Trends from the Past Year
Imagine a bustling city with gates left unlatched, each representing a potential weak point in an organization’s defenses. Threat actors exploit these gaps, causing financial losses, operational disruptions, and irreparable damage to reputations. For cybersecurity professionals, staying ahead of these threats is a race against time – one where understanding the most critical vulnerabilities can make the difference between resilience and catastrophe.
In this challenging landscape, resources like the Known Exploited Vulnerabilities (KEV) Catalog play an integral role. While not a direct solution to the issue of vulnerabilities, the catalog provides essential insights into the security vulnerabilities actively targeted by attackers. By focusing on these critical flaws, organizations can refine their strategies and prioritize efforts to reduce risk efficiently.
The Role of the KEV Catalog in Strategic Defense
The CISA Known Exploited Vulnerabilities (KEV) Catalog is a vital resource in the cybersecurity ecosystem. It tracks vulnerabilities exploited by adversaries, offering a guide patching and mitigation. The KEV Catalog by CISA is a compliance mandate for federal agencies under the Binding Operational Directive (BOD) 22-01. This directive requires federal entities to identify and remediate vulnerabilities listed in the KEV catalog within strict deadlines, ensuring a baseline level of security across critical infrastructure.
By enforcing compliance, CISA aims to close gaps in defense that could otherwise be exploited by adversaries. The KEV catalog serves as a prioritized roadmap, helping organizations align their vulnerability management efforts with regulatory requirements. For private-sector organizations, while not mandatory, the catalog offers a valuable benchmark to adopt similar best practices and improve overall resilience against emerging threats.
Yearly Statistics and Trends in the CISA KEV Catalog (2024 Update)
The 2024 update to the CISA Known Exploited Vulnerabilities (KEV) catalog reflects a continued commitment to tracking and mitigating actively exploited vulnerabilities. As of now, the catalog includes a total of 1,251 vulnerabilities.
In 2024, 186 new vulnerabilities were added to the catalog, aligning closely with 2023, which saw 187 additions – just one more than this year. This consistency indicates a stable pattern in identifying exploited vulnerabilities. However, it also underscores the ongoing nature of threats, as adversaries continue to leverage known vulnerabilities to compromise systems.

Annual vulnerability additions to the KEV catalog
The year 2022 remains the peak year for additions, with an impressive 555 vulnerabilities incorporated. However, as also mentioned in our 2023 CISA KEV Review blog post, many of these vulnerabilities have older CVE identifiers, signaling that they were actively exploited over time but added retroactively after the KEV catalog’s first year of operation in 2021.
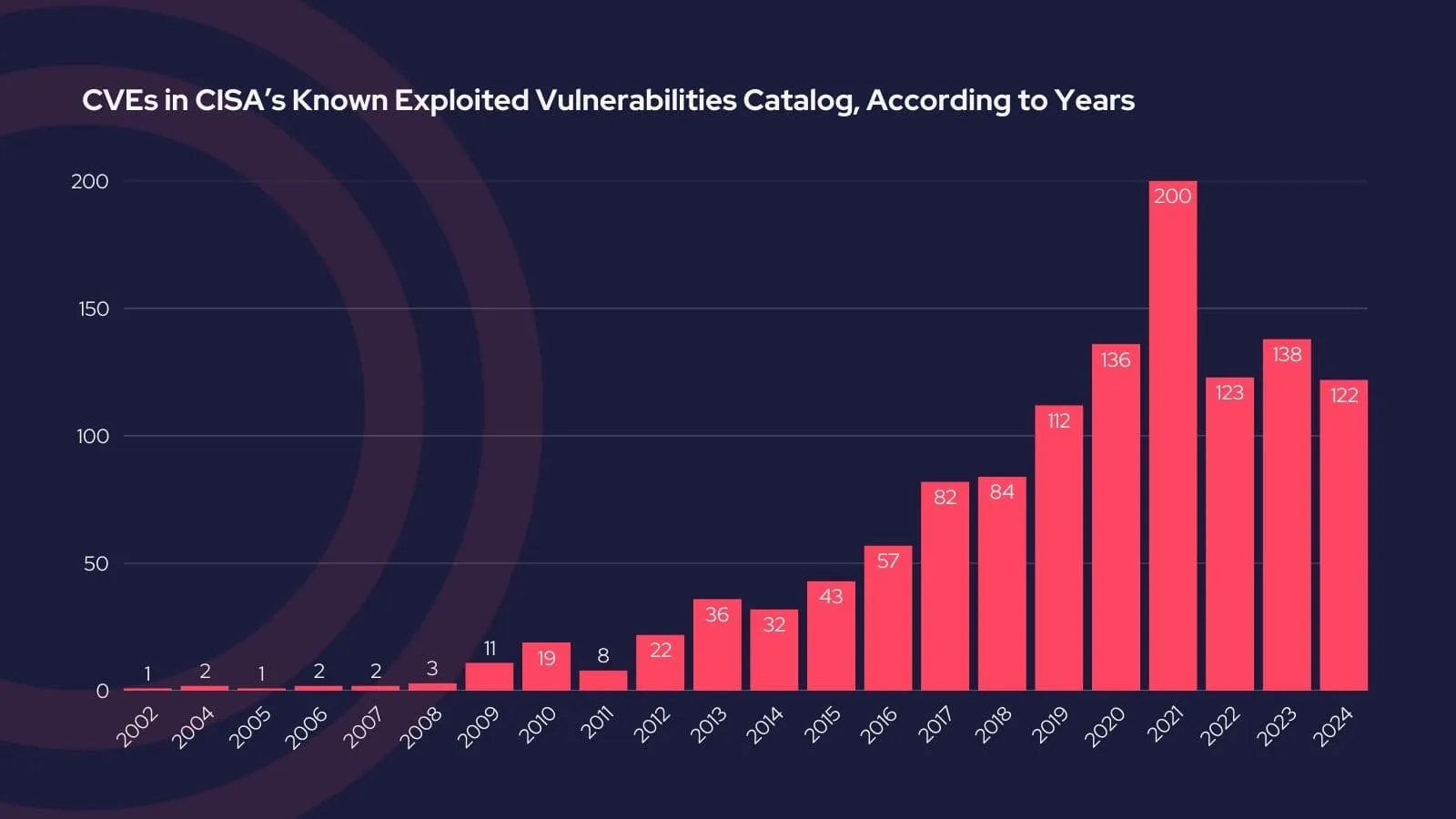
Breakdowns of CVE identifiers by year, showcasing the presence of older vulnerabilities
Top Vendors and Vulnerabilities in 2024
In 2024, Microsoft continues to dominate as the top vendor with the most vulnerabilities actively exploited and listed in the CISA KEV catalog. A total of 36 vulnerabilities in Microsoft products were included, accounting for 19.5% of the catalog’s additions, an increase from 15.5% in 2023. This upward trend reflects the ongoing targeting of Microsoft’s widespread software solutions, which remain integral to critical infrastructure and business operations globally.
Interestingly, the second spot saw a shift. While Apple held this position in 2023, it has now been overtaken by Ivanti, which had 11 vulnerabilities in the KEV catalog. Similarly, the third and fourth spots saw changes as Google and Adobe replaced Samsung and Cisco from 2023’s rankings.
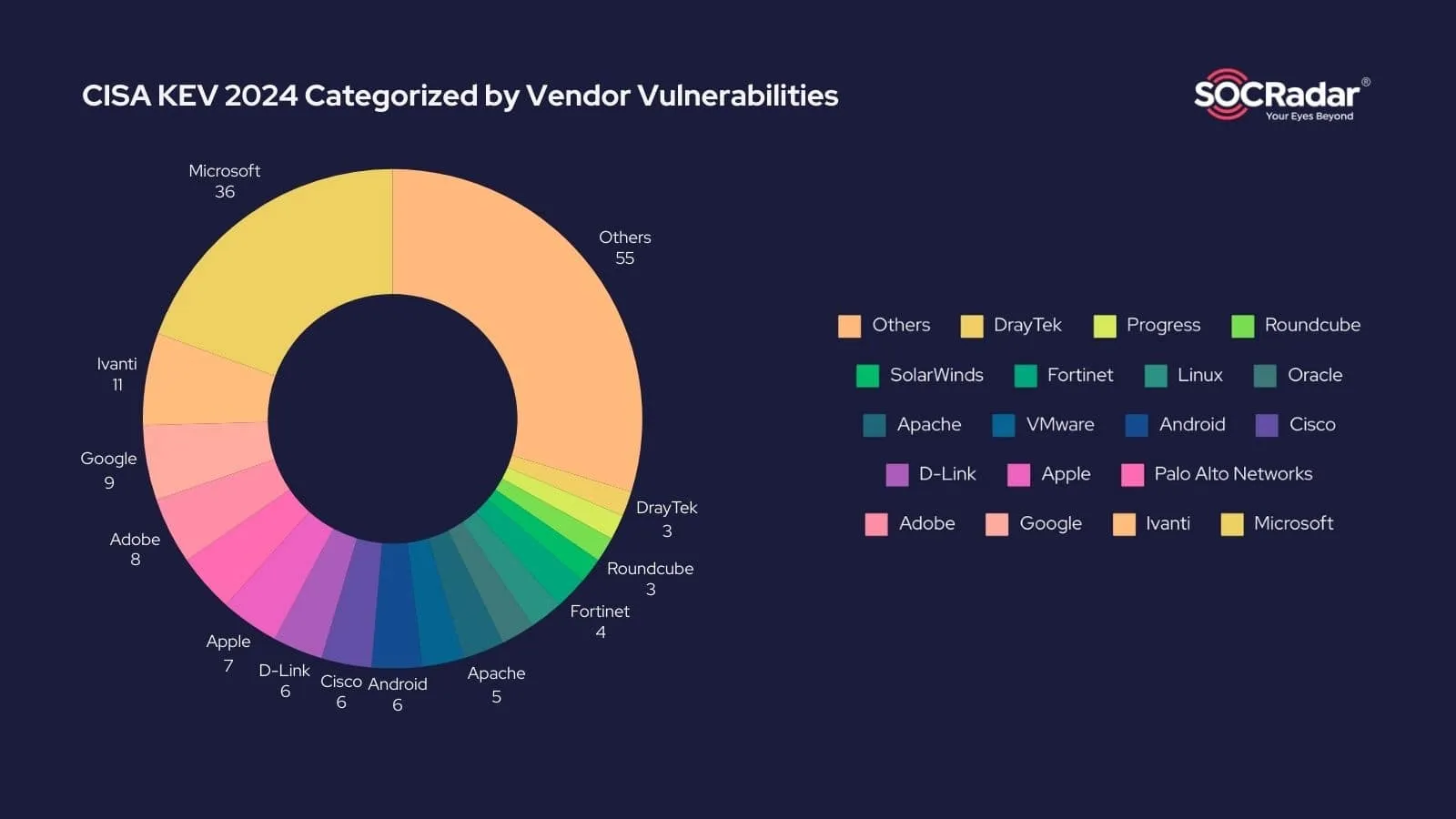
CISA KEV 2024 Vendors Analysis
The changes in vendor rankings and vulnerability types highlight how threat actors are adjusting their focus to target vendors with vulnerabilities that affect broader sectors, often influenced by industry adoption trends. For instance, the rise of Ivanti and Adobe in the KEV catalog points to increased targeting of enterprise-focused solutions and creative software platforms, both of which are integral to sectors such as healthcare, telecommunications, and media production.
Trends in Attack Vectors
When analyzing the types of vulnerabilities added to the KEV catalog in 2024, a few key trends emerge:
- Command Injection took the lead with 21 vulnerabilities, indicating a growing emphasis by attackers on exploiting input validation flaws to execute unauthorized commands on target systems.
- Privilege Escalation and Authentication Bypass vulnerabilities followed closely, with 14 and 10 vulnerabilities respectively. Privilege escalation’s prominence reflects its critical role in enabling attackers to expand their control post-compromise. The 2024 CISA KEV Catalog also listed 10 deserialization vulnerabilities.
- Other significant categories included Code Execution and Path Traversal vulnerabilities, each contributing 9 vulnerabilities to the list.
Compared to 2023, this marks a continuation of trends where privilege escalation and command injection remained prevalent. However, the decline in Code Execution vulnerabilities’ dominance, which previously led the KEV catalog, suggests that attackers are diversifying their exploitation tactics to focus on broader attack vectors.
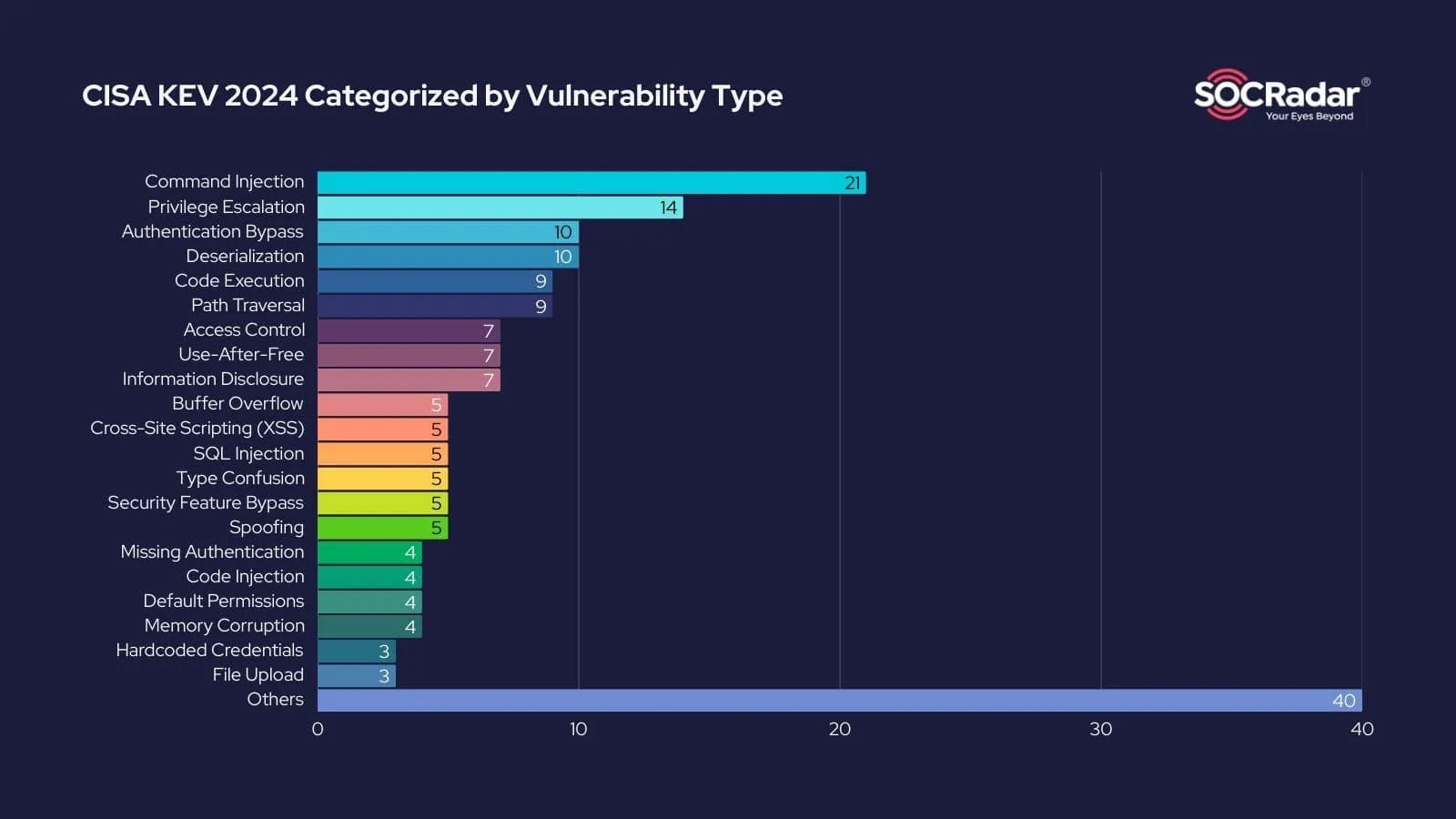
Vulnerability types in CISA KEV 2024
Vulnerabilities are constantly being exploited, and timely action is essential to prevent costly breaches. SOCRadar’s Attack Surface Management (ASM) and Vulnerability Intelligence modules work together to provide continuous visibility into your digital assets, track real-time vulnerabilities, and prioritize your security efforts.
Monitor your digital assets and vulnerabilities with SOCRadar ASM
With SOCRadar ASM, you can identify and address vulnerabilities before they’re exploited, keeping your organization’s perimeter secure. Vulnerability Intelligence provides in-depth insights into the most critical risks, aiding your team in patching vulnerabilities and reducing your attack surface. Stay proactive, stay secure, with SOCRadar’s integrated solutions designed to help you mitigate risks and stay ahead of emerging threats.
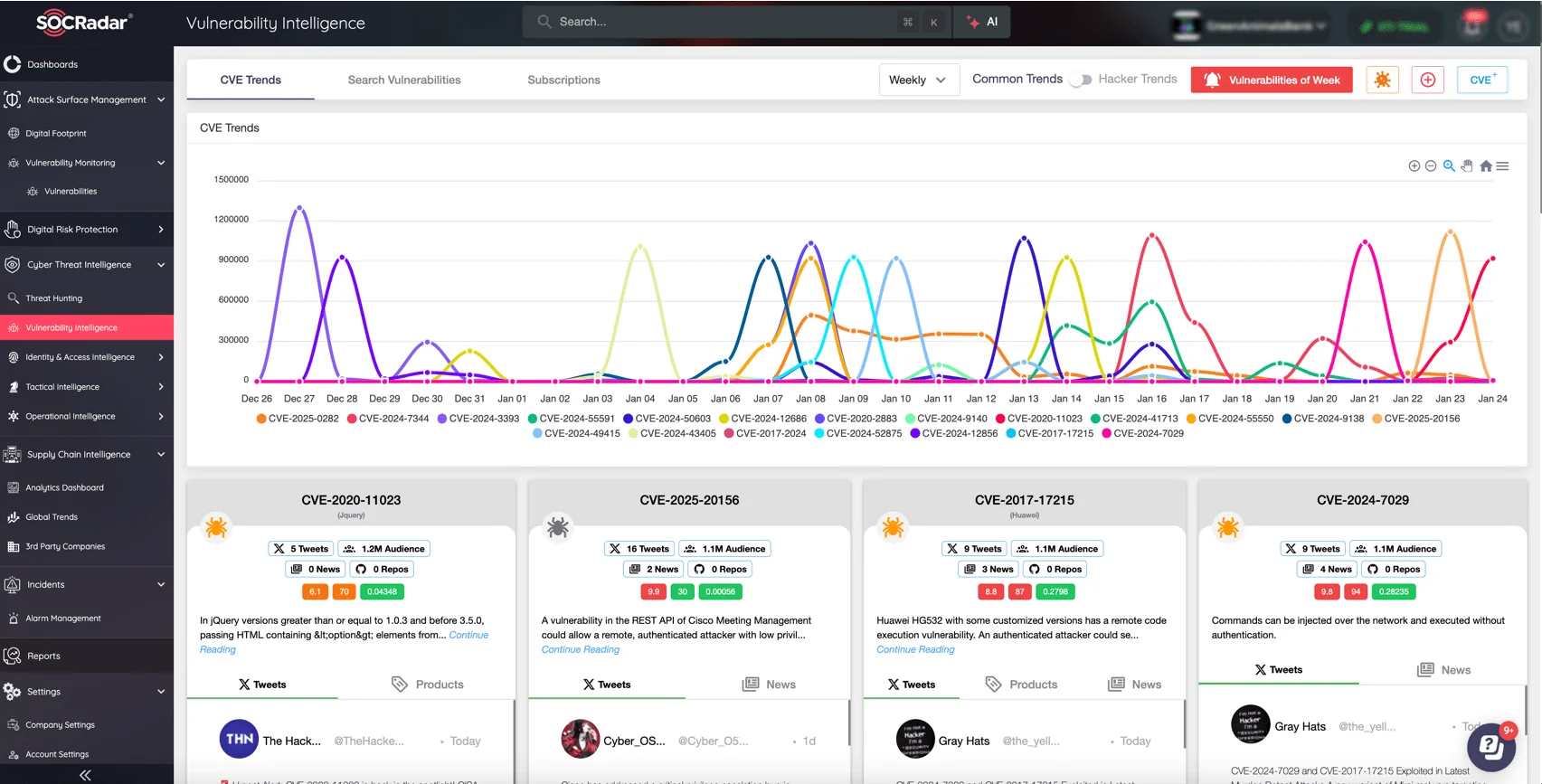
Track the latest CVEs, exploits, and trends with SOCRadar Vulnerability Intelligence
The Ransomware Connection: Vulnerabilities and Ransomware Campaigns
The link between known vulnerabilities and ransomware campaigns is an important area of focus in cybersecurity. The CISA Known Exploited Vulnerabilities (KEV) catalog helps organizations identify vulnerabilities that ransomware groups actively exploit, enabling them to prioritize and address critical security gaps.
According to the latest statistics, a significant percentage of vulnerabilities listed in the KEV catalog are associated with ransomware exploitation. For instance, in 2024, 24 vulnerabilities added to the catalog were explicitly linked to ransomware campaigns, comprising a substantial subset of the total vulnerabilities tracked for the year.
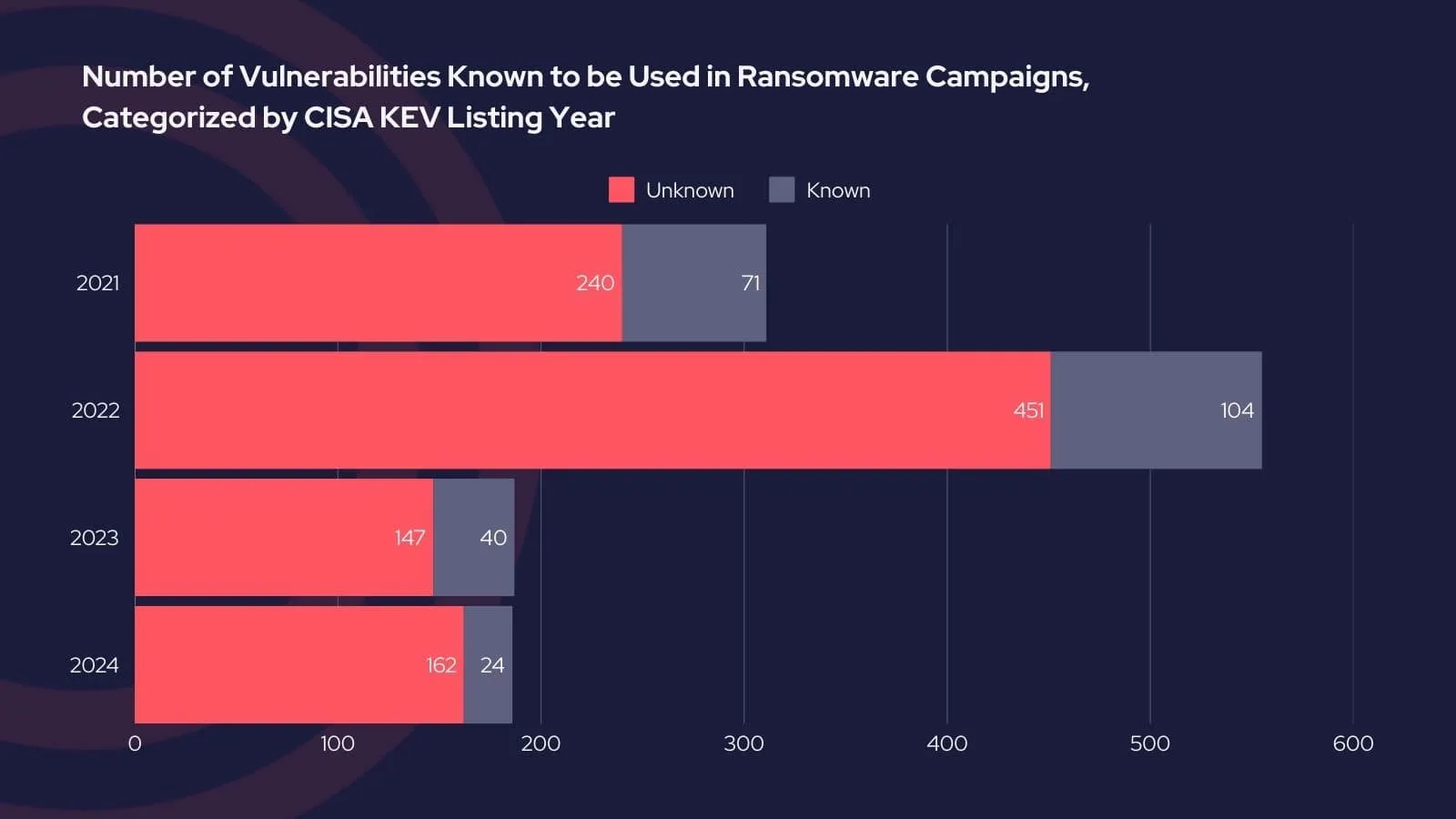
Number of vulnerabilities in CISA KEV 2024 that have been targeted by ransomware
The targeting of critical industries like healthcare, telecommunications, and supply chain services by ransomware operators further amplifies the urgency to address these vulnerabilities. By leveraging known vulnerabilities, threat actors have successfully orchestrated attacks on multiple organizations simultaneously, exposing sensitive data and disrupting operations. Notably, the Cl0P ransomware group’s exploitation of Cleo file transfer vulnerabilities in a recent mass extortion scheme underscores this trend.
CISA’s emphasis on tagging vulnerabilities associated with ransomware campaigns helps organizations prioritize remediation efforts. This targeted approach enables defenders to anticipate attack patterns and protect high-risk sectors, reducing the likelihood of successful intrusions.
Secure Your Attack Surface with SOCRadar ASM: CISA KEV & Ransomware Threat Monitoring
With SOCRadar ASM, continuously monitor your attack surface and assess risks from both CISA-listed vulnerabilities and emerging ransomware threats. Integrated intelligence enables you to prioritize remediation efforts, secure your digital assets, and enhance overall cybersecurity resilience.
The ASM module includes critical features like CISA KEV Check and Ransomware Check, ensuring you’re aware of and can act on vulnerabilities listed in the CISA KEV catalog and those targeted by ransomware actors.
Recent Additions to the CISA KEV Catalog (2024)
- Introduce recent additions to the catalog, focusing on their impact and why they matter.
- Highlight a few key vulnerabilities that have been actively exploited, providing details (like CVE numbers and CVSS scores) and examples of attacks.
December 2024: Cleo File Transfer (CVE-2024-50623 and CVE-2024-55956)
Vulnerabilities CVE-2024-50623 and CVE-2024-55956, found in Cleo’s file transfer software (Harmony, VLTrader, and LexiCom), have emerged as significant security concerns due to their active exploitation by the Cl0P ransomware group.
Although Cleo released an initial patch for CVE-2024-50623 in October 2024, security researchers found it insufficient, leaving systems vulnerable to exploitation. By December, attackers were leveraging the vulnerability to deploy backdoors, steal data, and infiltrate networks. On December 13, 2024, CISA officially added CVE-2024-50623 to its Known Exploited Vulnerabilities (KEV) catalog, underscoring its critical nature and requiring remediation by affected organizations.
The situation worsened with the discovery of CVE-2024-55956 in December 2024, which exploited similar mechanisms to bypass the previous patch; this vulnerability was also added to the KEV Catalog, on December 17, 2024.
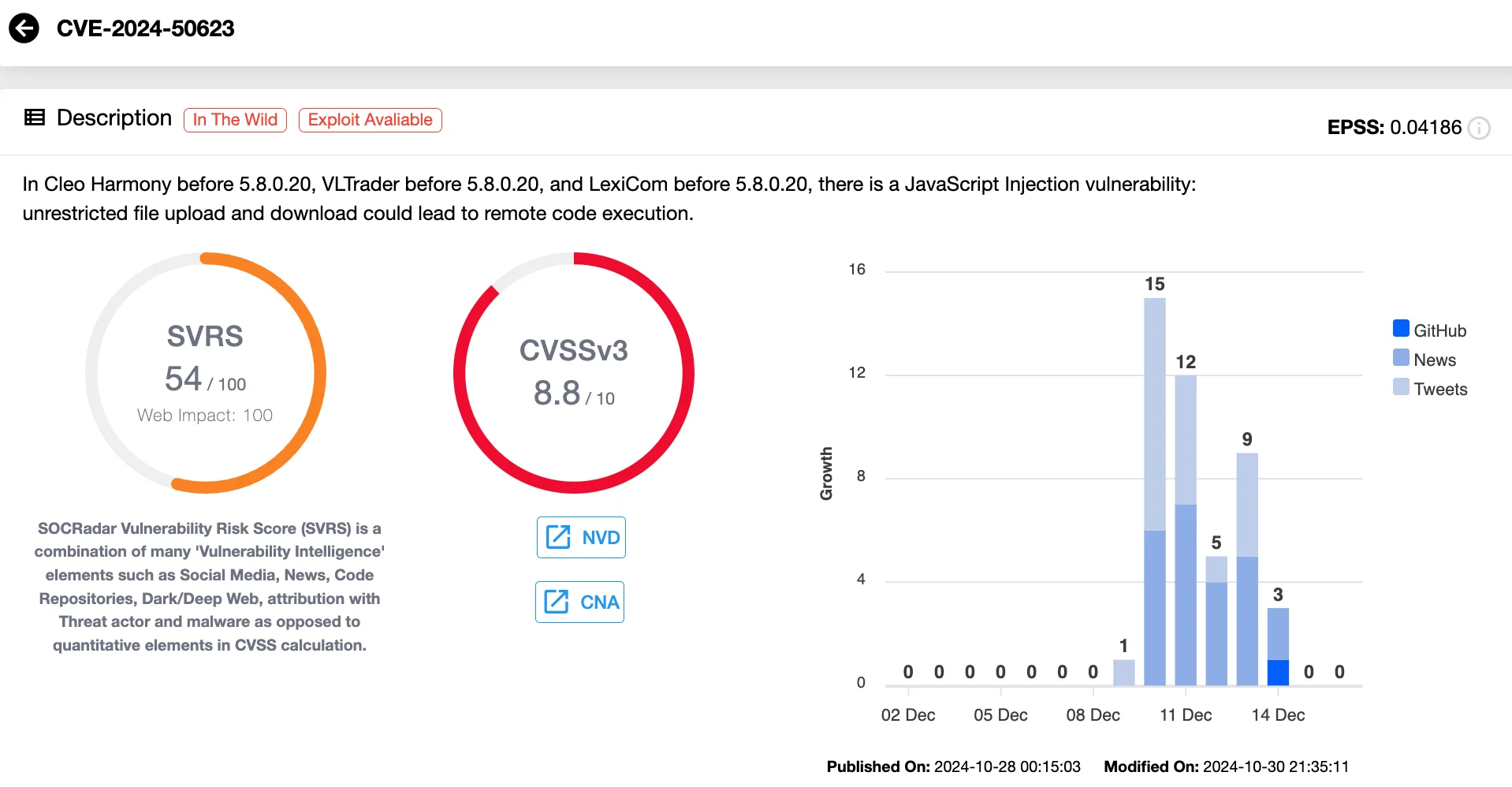
Vulnerability card of CVE-2024-50623 (SOCRadar Vulnerability Intelligence)
November 2024: PAN-OS Firewalls (CVE-2024-0012 and CVE-2024-9474)
Two zero-day vulnerabilities, CVE-2024-0012 and CVE-2024-9474, discovered in Palo Alto Networks’ PAN-OS devices, were added to the CISA KEV catalog on November 18, 2024. CVE-2024-0012 allows attackers to gain administrative access via the management web interface without user interaction, and exploiting this flaw enables attackers to manipulate system configurations and launch additional attacks.
The second vulnerability, CVE-2024-9474, is a privilege escalation flaw that lets malicious administrators elevate their access to root-level permissions.Palo Alto Networks has tied these vulnerabilities to Operation Lunar Peek, a campaign targeting exposed management interfaces globally.
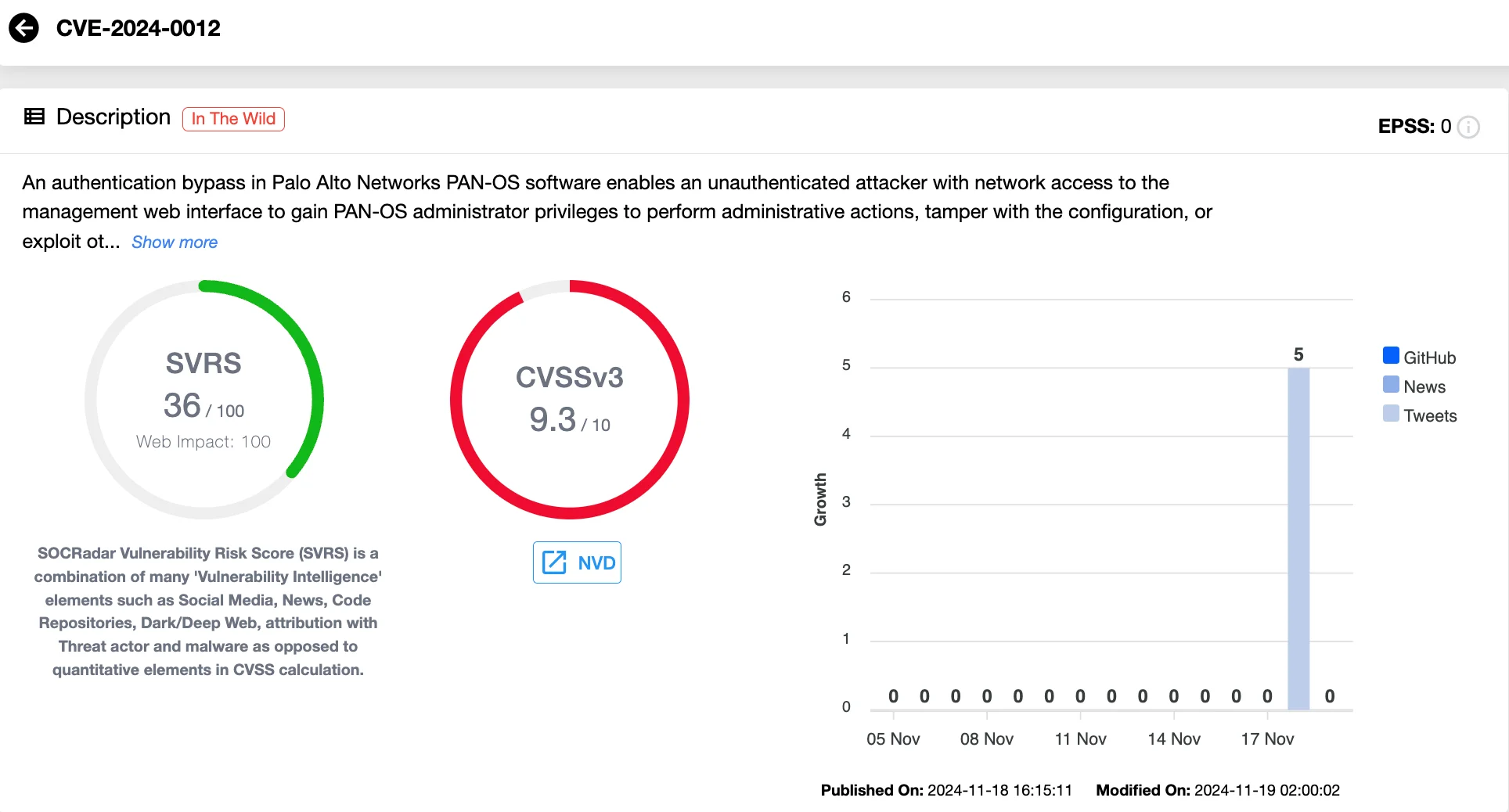
Vulnerability card of CVE-2024-0012 (SOCRadar Vulnerability Intelligence)
October 2024: Ivanti EPM (CVE-2024-29824)
On October 2, 2024, CISA added CVE-2024-29824 to the Known Exploited Vulnerabilities (KEV) catalog. This critical SQL injection vulnerability affected the Core Server of Ivanti Endpoint Manager (EPM), enabling unauthenticated attackers on the same network to execute arbitrary code, posing a significant risk to organizational systems.
A Proof-of-Concept (PoC) exploit for the vulnerability was made publicly available in June 2024, and the evidence of active exploitation included SQL logs showing the use of the ‘xp_cmdshell’ command to perform system-level tasks.
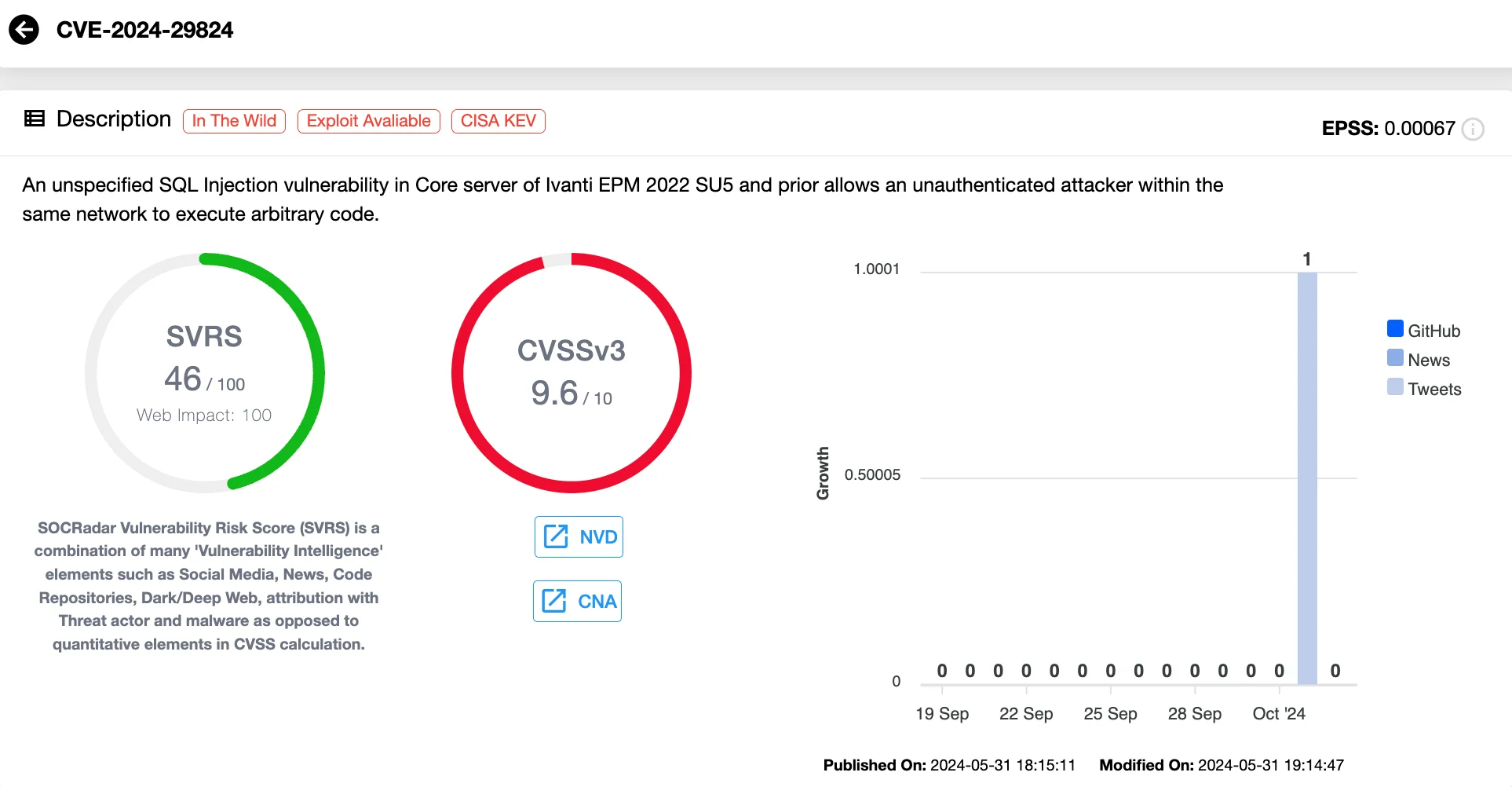
Vulnerability card of CVE-2024-29824 (SOCRadar Vulnerability Intelligence)
Conclusion
The CISA Known Exploited Vulnerabilities (KEV) Catalog offers a structured, actionable approach to help organizations align with compliance requirements. Additionally, it is a great resource for reviewing vulnerabilities actively exploited by threat actors. As the catalog expands each year, we continue to shed light on emerging risks and help organizations prepare for what’s ahead.
Through its collaboration with the cybersecurity community, CISA ensures organizations stay informed and ready to address vulnerabilities before they can be exploited. To further strengthen defenses, tools like SOCRadar’s Attack Surface Management (ASM) and Vulnerability Intelligence, as well as features like the KEV Check offer extensive protection.
With real-time insights into vulnerabilities and trends, SOCRadar equips organizations to combat emerging threats, quickly responding to risks highlighted in the KEV catalog.




































