CISA Warns for Vulnerabilities in Industrial Control Systems (ICS)
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) warns about multiple security vulnerabilities in GE Digital, Siemens, Contec, and Mitsubishi Electric products. The agency issued four ICS (Industry Control Systems) advisories for the vulnerabilities on January 17, 2023.
The advisories mention various vulnerability types, and the CVSS scores range from 5.9 to 10.0.
Affected Products
The vulnerabilities are specific to products and do not affect them equally. All affected products are listed below:
GE Digital:
- Proficy Historian v7.0 and higher versions
Siemens:
- SINEC INS: versions prior to V1.0 SP2 Update 1
Contec:
- CONPROSYS HMI System (CHS): Ver.3.4.4 and prior
- CONPROSYS HMI System (CHS): Ver.3.4.5 and prior
Mitsubishi:
- MELSEC iQ-F Series with serial number 17X**** or later:
- MELSEC iQ-F Series with serial number 179**** and prior:
- FX5U-xMy/z x=32,64,80, y=T,R, z=ES,DS,ESS,DSS: Versions 1.074 and prior
- MELSEC iQ-F Series FX5UC-32MT/DS-TS, FX5UC-32MT/DSS-TS, FX5UC-32MR/DS-TS: Versions 1.280 and prior
- MELSEC iQ-R Series R00/01/02CPU: All versions
- MELSEC iQ-R Series R04/08/16/32/120(EN)CPU: All versions
ICS Historians of GE Digital are Vulnerable
The most important vulnerability that affects GE Digital’s Proficy Historian is CVE-2022-46732. A Historian server manages all client and collector interfaces for storing and retrieving data.
Historian servers are a desirable entry point for attackers looking to move from the IT network to the OT systems because they share process data with enterprise systems.
Process control, performance, and maintenance data are important to a threat actor. Attackers target historian servers to gather information about industrial processes, change or remove data in an automation process to disrupt operations, and damage equipment.

CVE-2022-46732 (CVSS score: 9.8): It is an authentication bypass vulnerability that makes use of a different path or channel.
Regardless of authentication status, a flaw in GE Digital’s Proficy Historian solution could lead to code execution. The requested command might still be executed even if the local service authentication fails.
Vulnerabilities Affecting Siemens’ Products

Siemens has fixed a total of 12 vulnerabilities, the most critical of them are as follows:
CVE-2022-45092 (CVSS score: 9.9): It is a path traversal vulnerability found in Siemens SINEC INS that may allow remote code execution. The affected product’s web-based management (443/TCP) could allow an authenticated remote attacker to read and write arbitrary files to and from the device’s file system.
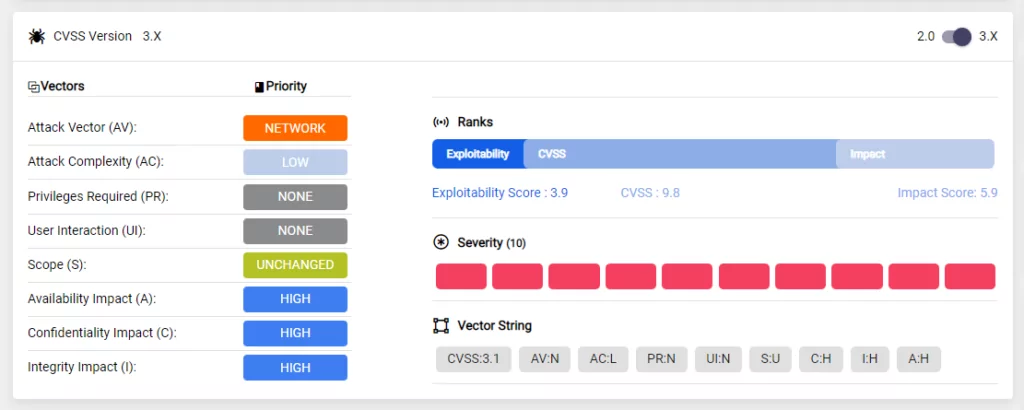
CVE-2022-2068 (CVSS score: 9.8): It is an OS command injection flaw found in Siemens SINEC INS that could lead to remote code execution.
Code review discovered additional instances where the c_rehash script fails to properly sanitize shell metacharacters to prevent command injection, in addition to the c_rehash shell command injection identified in CVE-2022-1292.
When CVE-2022-1292 was fixed, the code review did not find any other instances in the script where the file names of hashed certificates might have been passed to a command run through the shell.
Some operating systems distribute this script in a way that causes it to run automatically. An attacker could use the script’s privileges on these operating systems to execute any arbitrary commands. The OpenSSL rehash command line tool should be used instead of the c_rehash script.
CVE-2022-35256 (CVSS score: 9.8): It is an authentication bypass flaw in the llhttp parser that threat actors could use in remote code execution. The header fields not terminated with CLRF are not handled correctly by the llhttp parser in the http module of Node.js v18.7.0. HRS might result from this.
CVE-2022-2274 (CVSS score: 9.8): It is an out-of-bounds write vulnerability in the OpenSSL library that could be used for remote code execution.
For X86 64 CPUs supporting the AVX512IFMA instructions, an important bug in the RSA implementation was introduced with OpenSSL 3.0.4. This problem causes RSA to be implemented incorrectly on these machines with 2048-bit private keys, and memory corruption will occur while the computation is done.
An attacker could cause remote code execution on the computer performing the calculation because of memory corruption. This problem affects SSL/TLS servers or other servers using 2048-bit RSA private keys running on machines supporting AVX512IFMA instructions of the X86_64 architecture.
More Details
CISA updated the ICS advisory for Contec, which was originally issued in January 2022, and detailed the critical command injection vulnerability tracked as CVE-2022-44456. The vulnerability in Contec CONPROSYS HMI System has a CVSS score of 10 and could allow a remote attacker to send specially crafted requests to execute malicious commands.

The software has since been discovered vulnerable to four additional flaws that could result in information disclosure and unauthorized access, even though Contec patched this flaw in version 3.4.5.
It is advised that users of the CONPROSYS HMI System update to version 3.5.0 or later and take precautions to isolate these devices from corporate networks and reduce their network exposure.
Furthermore, the collective of Mitsubishi products was affected by an authorization bypass vulnerability tracked as CVE-2022-40267, which is assigned a CVSS score of 5.9.
Recommendations
CISA strongly advises all administrators and users to visit the advisories and implement appropriate security measures. If vendor fixes and mitigations are currently available, they are included in the advisories.
Keep track of the latest security vulnerabilities and keep your products and software up to date. SOCRadar continuously monitors digital assets and sends warnings whenever a vulnerability emerges and makes its way into your organization’s system.
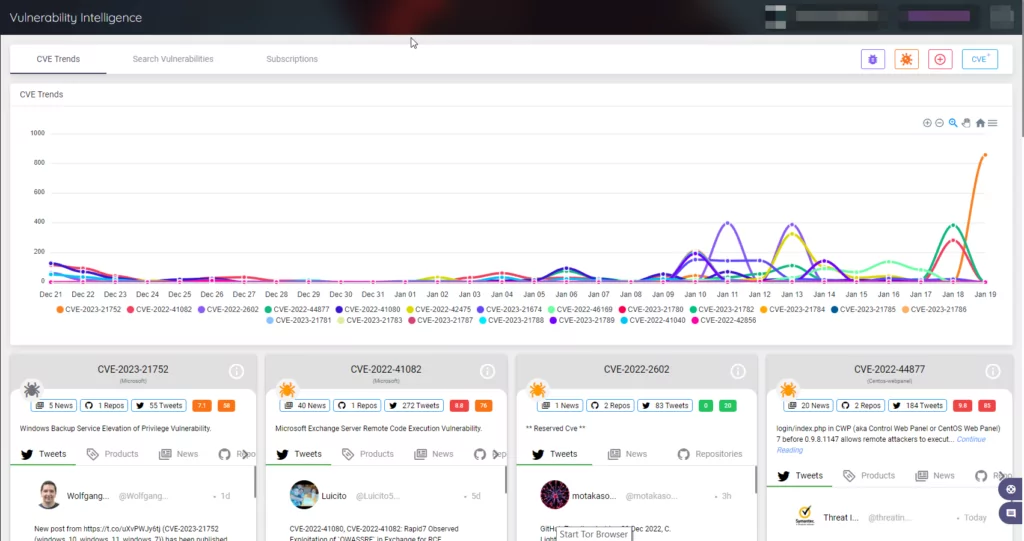
SOCRadar’s Vulnerability Intelligence can help you better manage vulnerability issues and prioritize patches. Here you can search for vulnerabilities and find detailed information about them, as well as see the lifecycle of a vulnerability. Below is an example page of the CVE-2022-2068 vulnerability in Siemens SINEC INS.
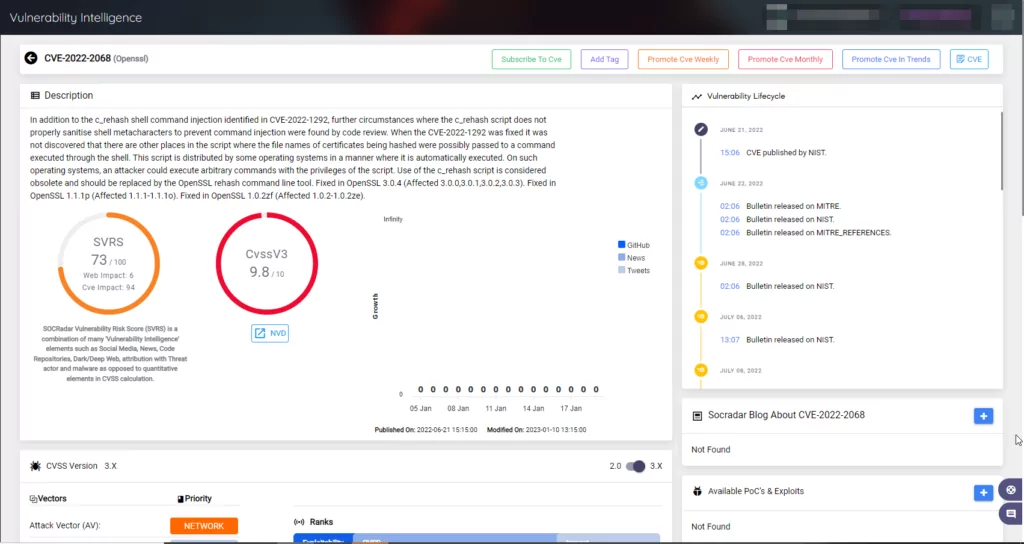
Discover the most recent information about a vulnerability, including its exploitability status, attack vectors used, and complexity.