
Old Cisco ASA Vulnerability (CVE-2014-2120) Fuels Androxgh0st Botnet Activity
Cisco has issued a fresh warning regarding CVE-2014-2120, a decade-old vulnerability in its Adaptive Security Appliance (ASA). Despite its medium severity with a CVSS score of 4.3, the vulnerability is now under exploitation by threat actors.
At the time of its original disclosure, in 2014, Cisco noted that exploitation required tricking users into accessing a malicious link, while recent reports indicate threat actors’ interest in leveraging the flaw for broader malicious campaigns.
Cisco’s updated warning comes as the Androxgh0st botnet has been observed exploiting this vulnerability, alongside others, to enable unauthorized access and malware distribution.
Why Is CVE-2014-2120 in Cisco ASA Back in the Spotlight?
On December 2, 2024, Cisco updated its original advisory for CVE-2014-2120, citing exploitation attempts. Cisco’s Product Security Incident Response Team (PSIRT) reported observing active in-the-wild attacks targeting the vulnerability as early as November 2024.
CVE-2014-2120 results from insufficient input validation in the WebVPN login page of Cisco’s Adaptive Security Appliance (ASA). This flaw allows unauthenticated, remote attackers to conduct Cross-site Scripting (XSS) attacks against users of the affected appliance.
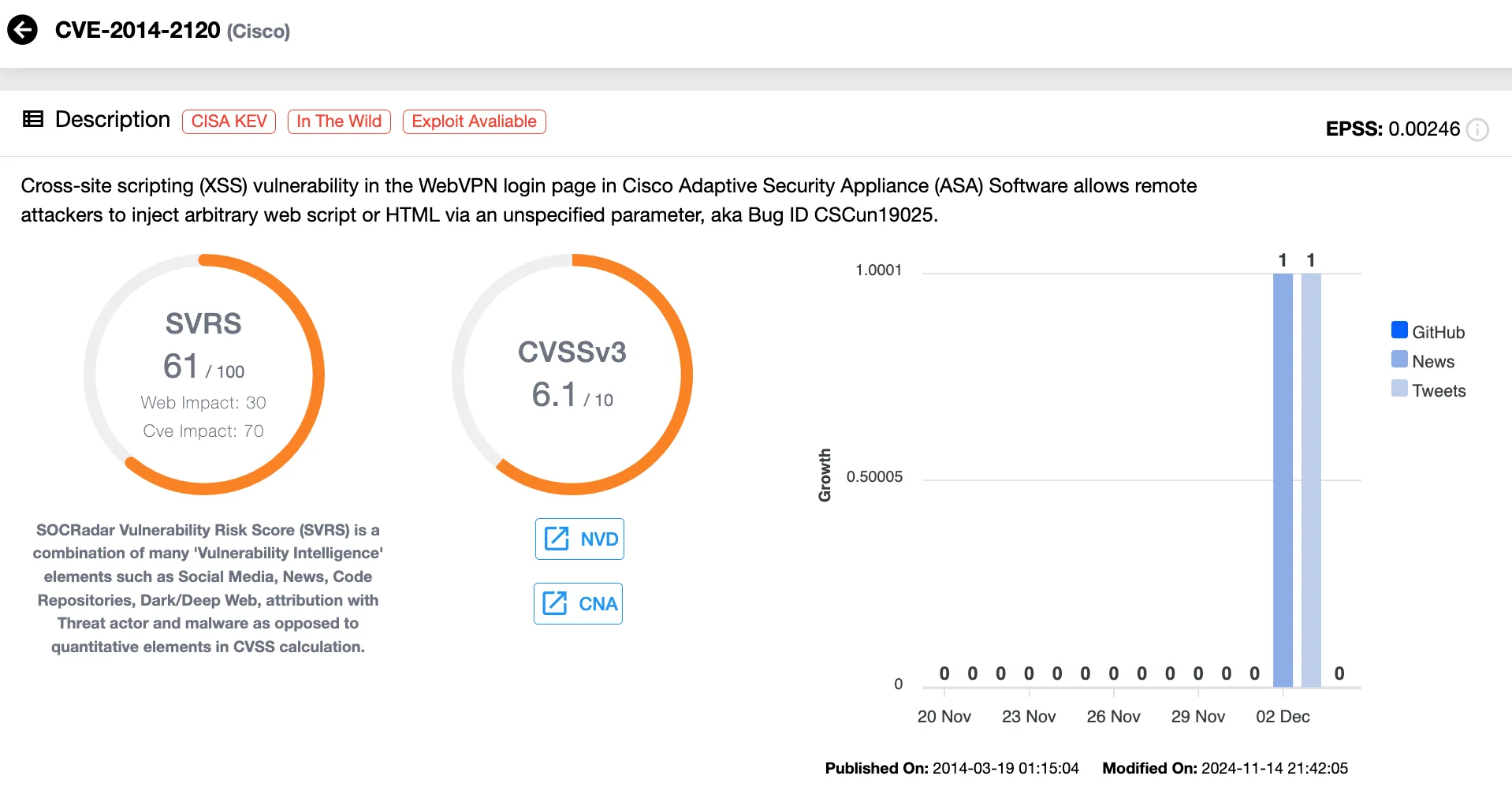
Explore the details of CVE-2014-2120 on the SOCRadar platform. Gain insights into its lifecycle, available exploits, and the latest updates through the Vulnerability Intelligence module.
Cisco’s updated advisory emphasizes the growing risk of exploitation despite the flaw’s age and medium severity rating. The company continues to recommend that customers running vulnerable ASA versions upgrade to patched releases to mitigate potential threats. This activity underscores the importance of addressing even older vulnerabilities, as they can be revived and exploited in evolving threat campaigns.
Staying secure starts with knowing your vulnerabilities and exposure. Cyber threats evolve quickly, and unpatched systems or unknown assets can become an open invitation for attackers. SOCRadar’s Attack Surface Management (ASM) module maps your digital assets to uncover exposures you may not know about, while Vulnerability Intelligence keeps you informed about emerging CVEs and exploits in real-time.
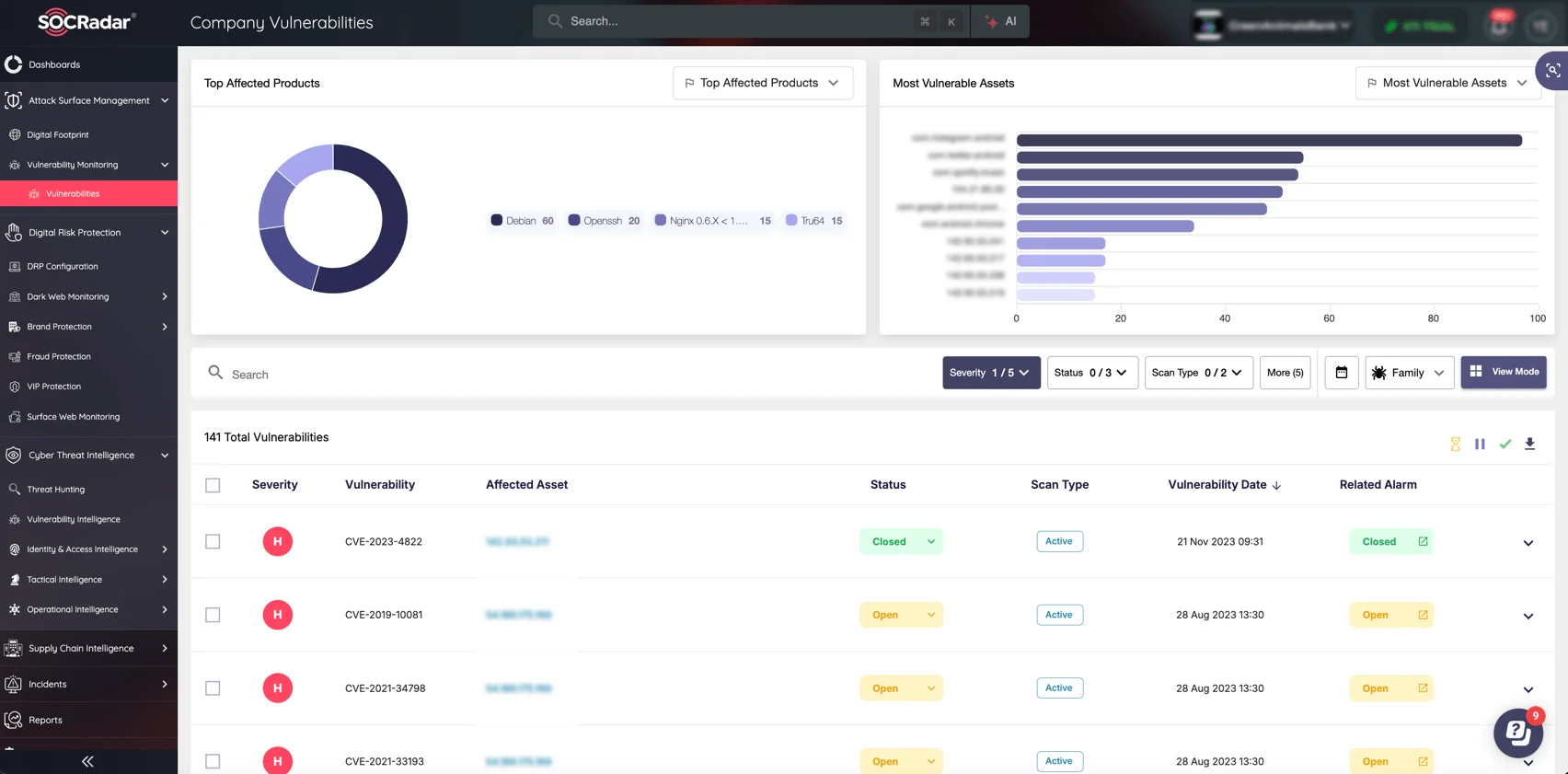
SOCRadar’s ASM module, Company Vulnerabilities page
By monitoring your attack surface and delivering actionable insights on vulnerabilities, SOCRadar empowers you to prioritize critical patches and mitigate risks. Gain visibility, control, and peace of mind, ensuring your defenses stay ahead of the latest threats.
The Role of CVE-2014-2120 in Androxgh0st’s Malware Distribution
A research from late November 2024 sheds light on the evolving Androxgh0st botnet, which has been exploiting a range of vulnerabilities, including CVE-2014-2120 in Cisco’s Adaptive Security Appliance (ASA). This botnet, active since January 2024, leverages these vulnerabilities to achieve unauthorized access and perform Remote Code Execution (RCE), facilitating the distribution of malware.
Below are the key findings from the research, outlining the recent Androxgh0st botnet activity and its exploitation of the Cisco ASA vulnerability.
- Operational Insights and Expansion with Mozi Botnet
Androxgh0st, primarily targeting web servers, has recently exhibited expanded capabilities. Command and control (C2) logs reveal its deployment of IoT-focused Mozi botnet payloads, broadening its operational reach across various technologies. The integration with Mozi marks a concerning evolution in its tactics, indicating the botnet’s adaptability and increasing threat potential.
- Exploitation of CVE-2014-2120 and Other Vulnerabilities
While exploiting CVE-2014-2120 to inject arbitrary web script or HTML into systems, Androxgh0st also targeted vulnerabilities in high-profile products like Atlassian JIRA, Sophos Firewall, Oracle EBS, and various PHP frameworks. Researchers highlight its use of an appending method with the Cisco ASA flaw to spread malicious code across PHP files, enhancing persistence and establishing additional backdoors.
CISA Highlights CVE-2014-2120 Exploitation Alongside Other Botnet-Targeted Vulnerabilities
In mid-November 2024, CISA added the CVE-2014-2120 vulnerability in Cisco ASA to its Known Exploited Vulnerabilities (KEV) Catalog. This addition underscores the active exploitation of this decade-old flaw by threat actors. Alongside CVE-2014-2120, two other vulnerabilities exploited in the Androxgh0st botnet campaign were included in the catalog:
- CVE-2021-26086: A path traversal vulnerability in Atlassian Jira Server and Data Center.
- CVE-2021-41277: A local file inclusion vulnerability in the Metabase GeoJSON API.
The patch deadline for these vulnerabilities had been set for December 3, 2024, and federal organizations that failed to patch these issues in a timely manner may face compliance challenges due to increased security risk. Cisco strongly advises all users to update to a fixed software version to mitigate the CVE-2014-2120 vulnerability and prevent further exploitation.
For a detailed list of Indicators of Compromise (IOCs) and tailored mitigation strategies associated with the Androxgh0st botnet, refer to CISA’s official advisory. Additionally, you can find more details on the botnet campaign in this research blog.
Monitor for Botnet Activity with SOCRadar
Threats often emerge in hidden places like the Dark Web, where stolen data and malicious campaigns originate. Without visibility into these underground activities, your organization could be caught off guard.
SOCRadar’s Dark Web Monitoring module continuously scans hidden forums, marketplaces, and botnet data for mentions of your brand or compromised assets. Its Botnet Data Monitoring feature provides early warnings of malicious networks targeting you.
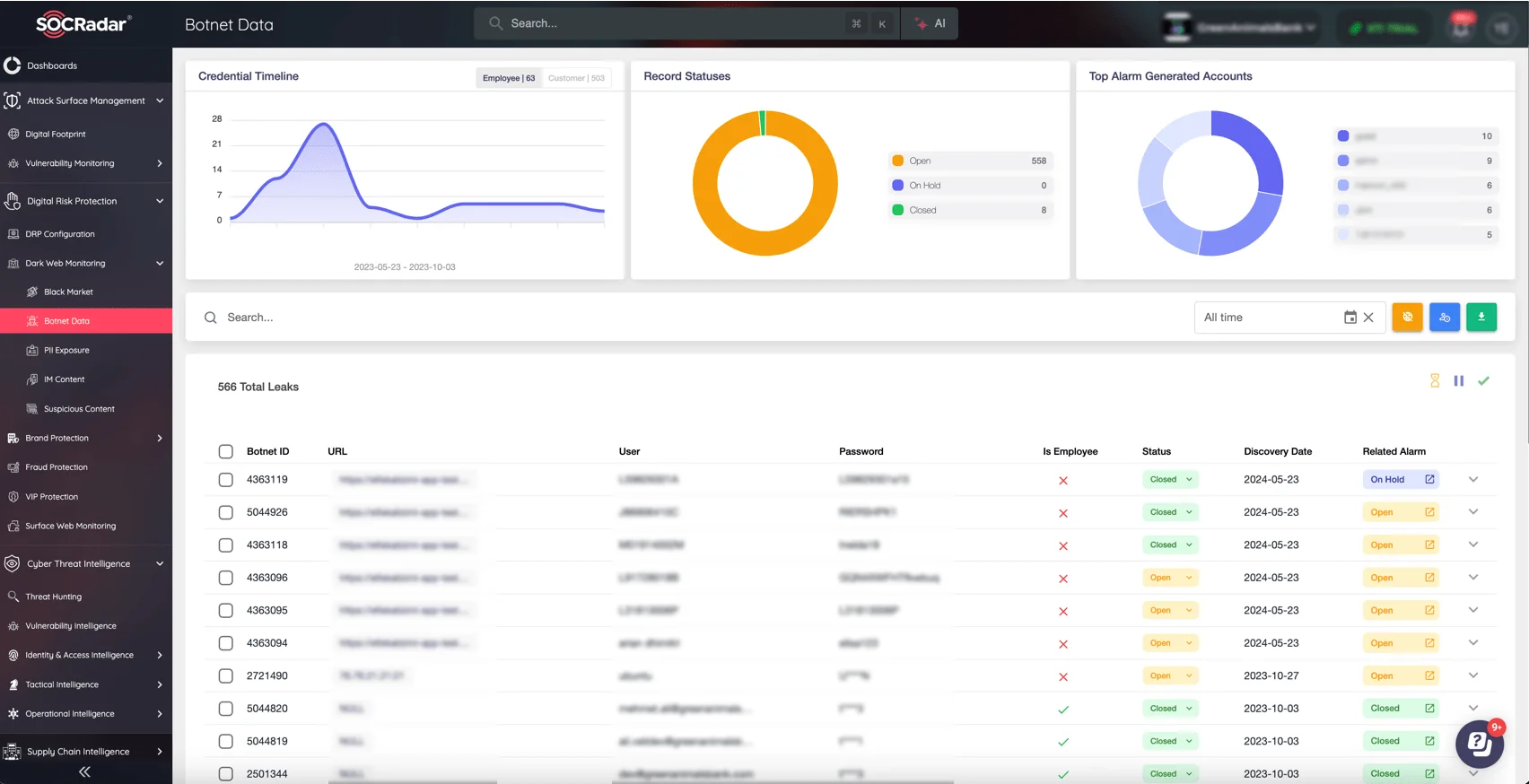
SOCRadar’s Dark Web Monitoring module, Botnet Data page
By detecting potential threats early, SOCRadar equips you to prepare proactive defense strategies and safeguard your organization against data breaches, botnet-driven attacks, and more. Stay informed, secure, and ahead of the threat landscape.
In other news, a recent critical vulnerability, CVE-2024-42448, has emerged in Veeam’s Service Provider Console (VSPC), posing a risk of Remote Code Execution (RCE). Veeam has released updates to address this issue—prompt action is advised.



































