
Cisco Fixed Critical CSRF Flaws in Expressway Gateways (CVE-2024-20252 and CVE-2024-20254)
Cisco patched multiple security vulnerabilities, including critical ones, affecting its Expressway Series gateways and TelePresence Video Communication Server (VCS). The vulnerabilities could enable an attacker to carry out arbitrary actions on affected devices.
Cisco Expressway Series (Expressway) is designed for comprehensive collaboration services, with established firewall-traversal technology, whereas Cisco TelePresence VCS is a product that streamlines telepresence conference control and session management.
The company has announced that it will not be releasing security updates for the TelePresence VCS gateway, which reached end-of-support at the end of 2023.
Details of the Latest Critical Vulnerabilities in Cisco Expressway (CVE-2024-20252 and CVE-2024-20254)
The critical vulnerabilities in Cisco Expressway, identified as CVE-2024-20252 and CVE-2024-20254, have CVSS scores of 9.6 and could allow for Cross-Site Request Forgery (CSRF) attacks. Cisco also addressed a high-severity CSRF vulnerability, labeled as CVE-2024-20255 (CVSS: 8.2).
Cisco discovered these vulnerabilities during internal security testing, and in the advisory, the term ‘Cisco Expressway Series’ is used to refer to Cisco Expressway Control (Expressway-C) and Cisco Expressway Edge (Expressway-E) devices.
The vulnerabilities are caused by insufficient CSRF protections for the web-based management interface. As a result, attackers can exploit them to perform arbitrary actions with the affected user’s privilege level.
CVE-2024-20254 and CVE-2024-20255 affect Cisco Expressway Series devices with default configurations. Also, CVE-2024-20252 can only be used to attack gateways that have the Cluster Database (CDB) API feature enabled; by default, this feature is disabled.
An unauthenticated, remote attacker may deceive authenticated API users into visiting or clicking malicious content in order to exploit the critical vulnerabilities, CVE-2024-20252 and CVE-2024-20254, and eventually perform arbitrary actions with the affected user’s privileges, such as code execution.
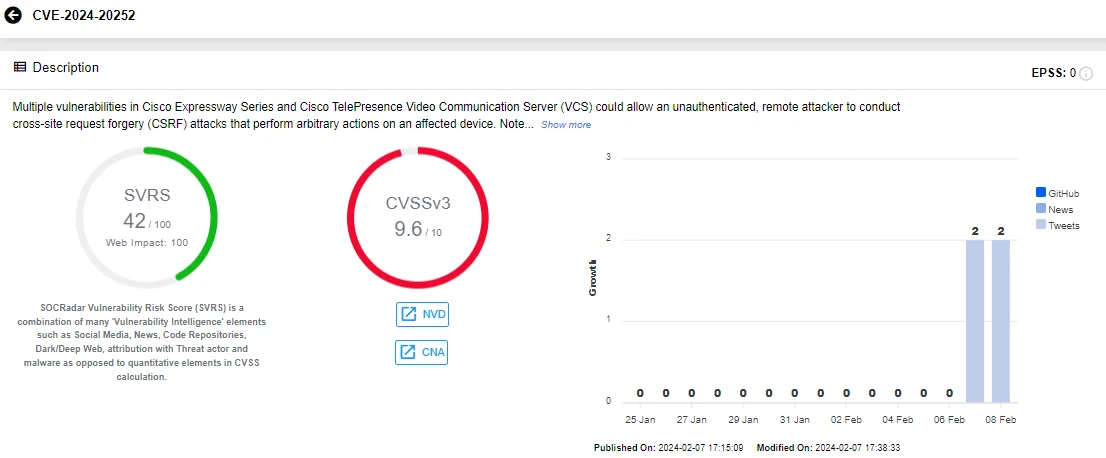
SOCRadar Vulnerability Card of CVE-2024-20252, Cisco
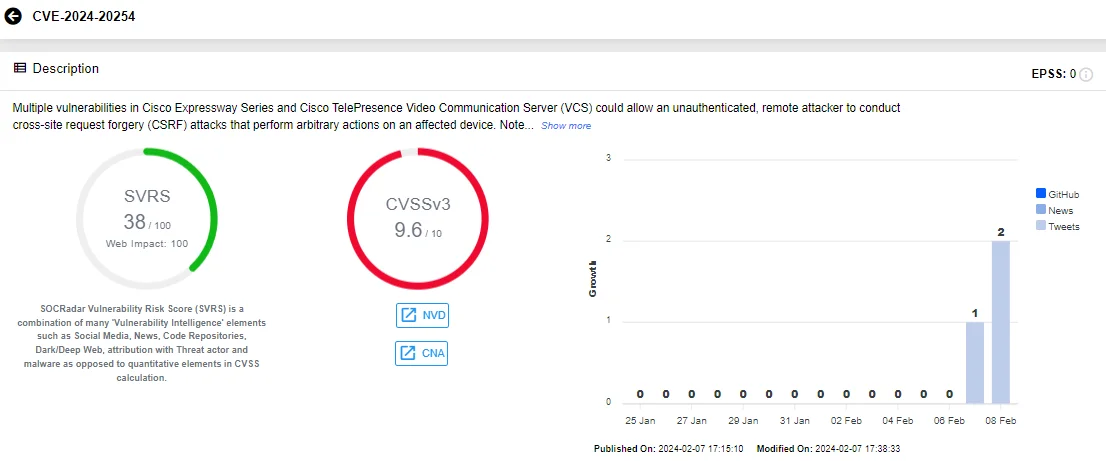
SOCRadar Vulnerability Card of CVE-2024-20254, Cisco
According to Cisco, if the affected user has administrative privileges, the attacker may modify the system configuration and create new privileged accounts with those privileges.
CVE-2024-20255, the third CSRF security vulnerability in Cisco’s advisory, could allow unauthenticated, remote attackers to change the configuration of vulnerable systems, leading to a Denial-of-Service (DoS) condition by causing the affected system to reload.
The vulnerability has been found in the SOAP API of Cisco Expressway Series and Cisco TelePresence VCS. An attacker could exploit CVE-2024-20255 by convincing a user of the REST API to click on a crafted link.
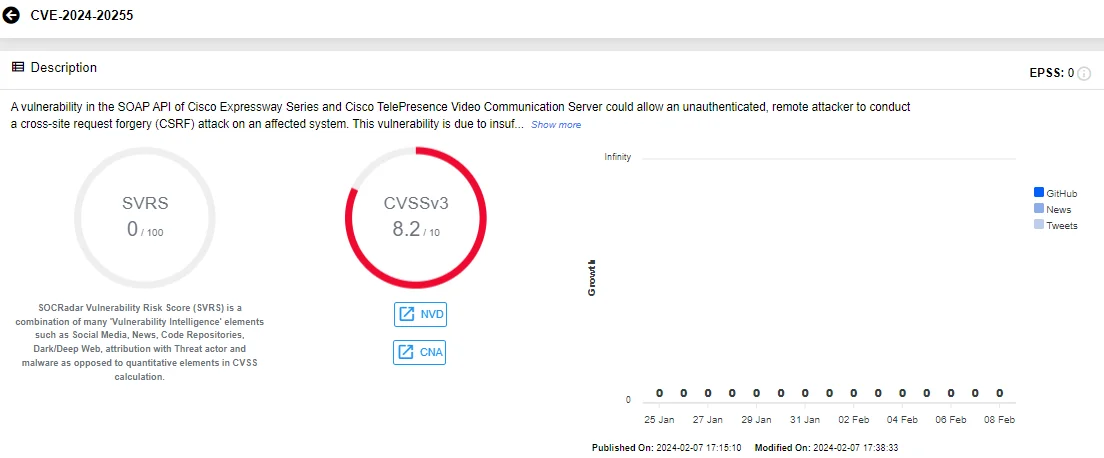
SOCRadar Vulnerability Card of CVE-2024-20255, Cisco
Are There Any Reports of Exploitation? Patch the Cisco Expressway Vulnerabilities
Cisco asserts that there is currently no evidence of public Proof-of-Concept (PoC) exploits or exploitation attempts targeting these vulnerabilities.
A Shodan search displays over 20,000 instances of Cisco Expressway exposed on the internet, indicating the extent of the potential attack surface and the number of potential targets for attackers.
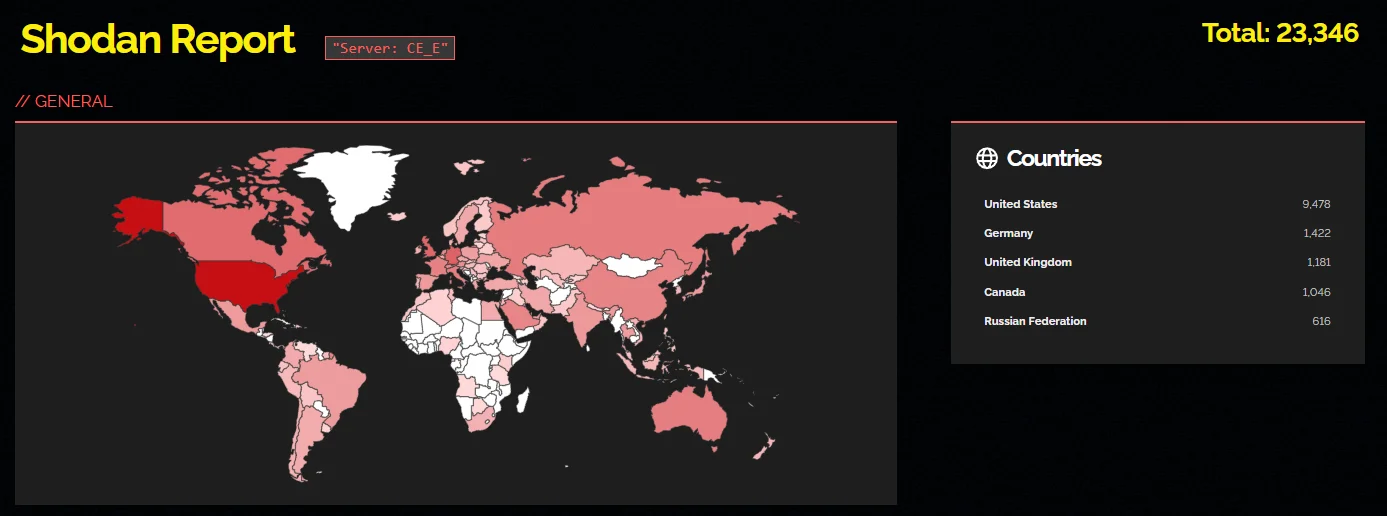
Shodan results for exposed Cisco Expressway Series instances
It is recommended that you update your products to prevent exploitation; patches for the vulnerabilities are available in Cisco Expressway Series versions 14.3.4 and 15.0.0.
Visit Cisco’s advisory for additional information and remediation guidance.
SOCRadar’s Attack Surface Management (ASM) module tracks and analyzes potential security vulnerabilities in your digital infrastructure. By providing real-time insights into organizations’ attack surface and emerging vulnerabilities, ASM enables them to identify and mitigate potential threats in advance.
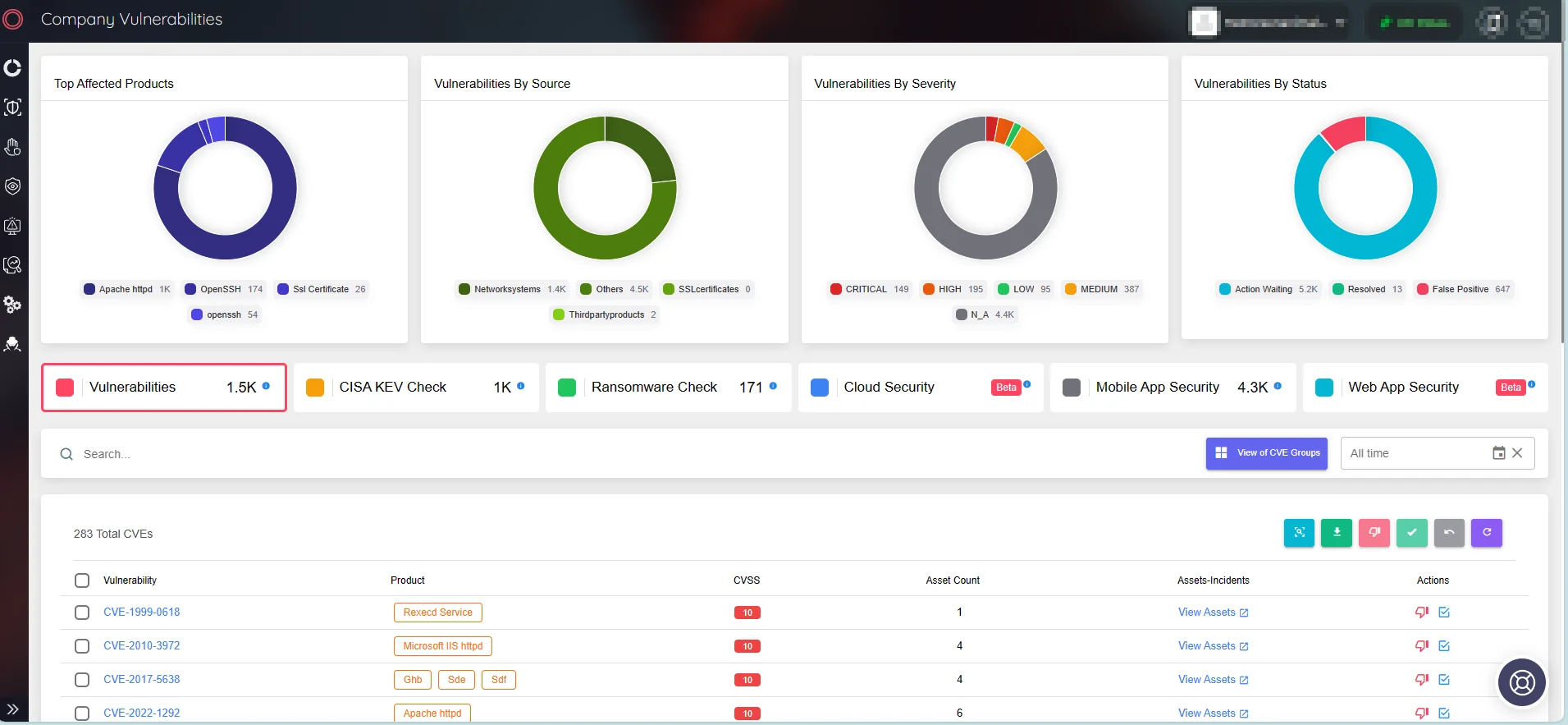
Company Vulnerabilities on SOCRadar’s Attack Surface Management module
CISA Alert: VMware Released Security Updates for Aria Operations for Networks
In other news, CISA issued an alert to highlight that VMware has released security updates to address vulnerabilities in Aria Operations for Networks (formerly vRealize Network Insight).
The update addresses five vulnerabilities, ranging from medium to high severity. CISA warns that these vulnerabilities could allow attackers to gain control of affected systems. Organizations are urged to review the VMware advisory and take immediate action to remediate these vulnerabilities to prevent exploitation.
Two vulnerabilities, CVE-2024-22237 (CVSS: 7.8) and CVE-2024-22239 (CVSS: 5.3), involve local privilege escalation, enabling a console user to gain regular root or shell access, respectively.
Additionally, CVE-2024-22238 (CVSS: 6.4) and CVE-2024-22241 (CVSS: 4.3) are Cross-Site Scripting (XSS) vulnerabilities. The former allows an attacker with admin privileges to inject malicious code into user profile configurations, while the latter permits the same to take over user accounts.
The last vulnerability, CVE-2024-22240 (CVSS: 4.9), is a local file read vulnerability enabling a malicious actor with admin privileges to access sensitive information.
To mitigate these risks, all users of VMware Aria Operations for Networks version 6.x are advised to upgrade to version 6.12.0. For more information, review the VMware advisory.
To access detailed information on vulnerabilities and details such as exploitability, available exploits, repositories, and updates, you can use SOCRadar’s Vulnerability Intelligence module. Through the module, you can also search for vulnerabilities specific to a product or vendor.
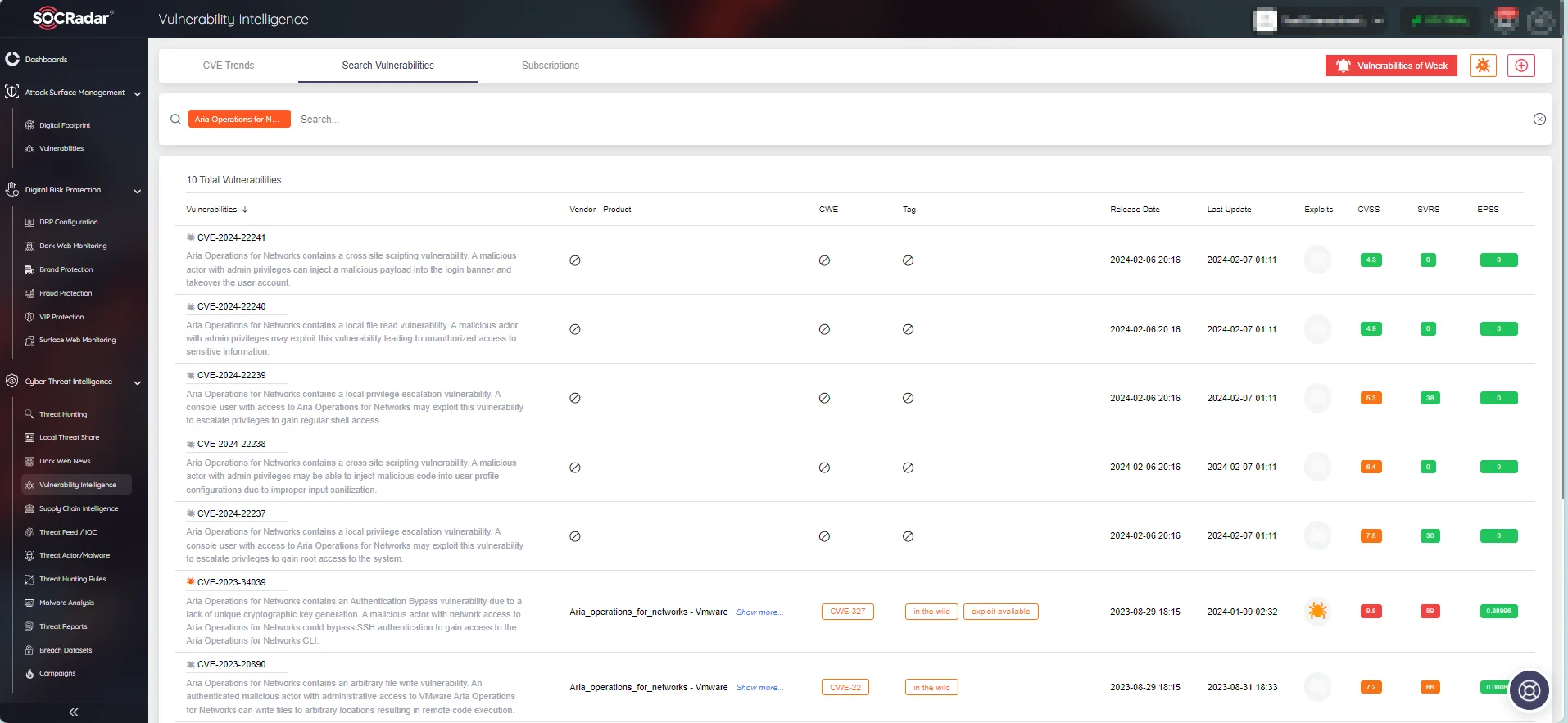
SOCRadar’s Vulnerability Intelligence




































