
Citrix Hypervisor Security Update: Addressing CVE-2023-23583 and CVE-2023-46835 Vulnerabilities
In the dynamic field of cybersecurity, staying abreast of new vulnerabilities is crucial. The recent discovery of two significant vulnerabilities in the Citrix Hypervisor, a widely used virtualization management tool, underscores this necessity. This blog explores these vulnerabilities and discusses the hotfixes Citrix has released to address them.
Citrix Hypervisor Vulnerabilities: A Closer Look
The vulnerabilities, identified as CVE-2023-23583 and CVE-2023-46835, have raised concerns due to their potential impact on systems using Citrix Hypervisor, especially those with specific Intel and AMD processors.
Intel CPU Vulnerability (CVE-2023-23583)
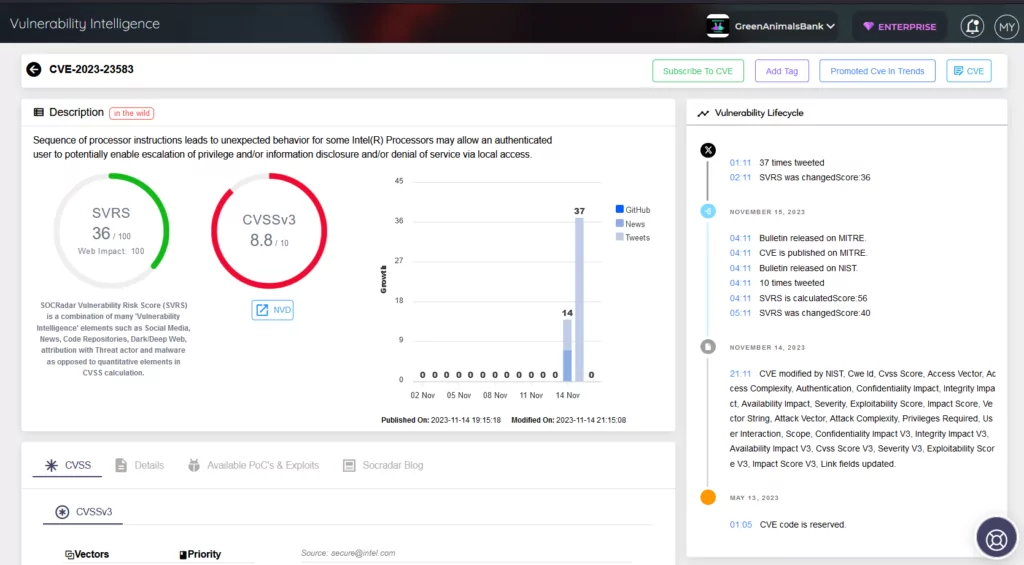
The more severe of the two, this vulnerability is rooted in a sequence of processor instructions that cause unexpected behaviors in some Intel processors. This flaw could allow an authenticated user local access to escalate privileges, disclose information, and deny service. Systems running on Intel Ice Lake or later CPUs are particularly at risk from this vulnerability.
AMD CPU Vulnerability (CVE-2023-46835)
This vulnerability poses a risk for AMD-based hosts. It emerges when malicious privileged code in a guest VM compromises the host through a passed-through PCI device. Only systems with an AMD CPU and a PCI device passed through to the guest VM are affected by this issue.
Mitigation and Prevention: Citrix’s Response
In response to these vulnerabilities, Citrix has released hotfixes, specifically targeting Citrix Hypervisor 8.2 Cumulative Update 1 users. The hotfix, referenced as CTX583402, includes updates to AMD and Intel microcodes, ensuring enhanced security and stability for affected systems.
CVE-2023-23583 exclusively affects systems that are equipped with Intel Ice Lake or later CPUs. On the other hand, CVE-2023-46835 is a concern only for systems that fulfill two specific criteria: they must have an AMD CPU, and they must be utilizing a PCI device that has been passed through to the guest VM by the host administrator. Systems that do not use AMD CPUs or do not employ the PCI passthrough feature are not at risk from the CVE-2023-46835 vulnerability. This information is vital for administrators and users in assessing their systems’ susceptibility to these issues and in taking appropriate security precautions.
Implementing the Hotfix
Applying this hotfix is a critical step in safeguarding systems against these vulnerabilities. Users can install the update via XenCenter or the Citrix Hypervisor Command Line Interface. It’s crucial to back up data before applying the update and to update all servers within a pool sequentially, minimizing the time the pool operates in a mixed state of updated and non-updated servers.
The Importance of Proactive Measures
These incidents highlight the importance of staying vigilant in cybersecurity. At SOCRadar, we emphasize the need for proactive measures and continuous monitoring to preemptively identify and mitigate such vulnerabilities. SOCRadar’s Vulnerability Intelligence plays a vital role in this process, offering insights and actionable intelligence to keep organizations informed and secure.
Staying informed is key to maintaining security. Customers are encouraged to contact Citrix Technical Support for detailed guidance and support and to subscribe to Citrix alerts for the latest updates on security bulletins. In the ever-changing landscape of cybersecurity, awareness and prompt action are the best defenses.




































