Comparing MEA (Middle East and Africa) and Europe against the Dark Web Threats
Companies that wish to safeguard customers and employees typically invest in Dark Web monitoring solutions to warn them if their compromised data are offered or sold on dark web forums since they cannot do so alone. Most technologies are used to find stolen credentials on public sites with automated scanners, crawlers and scrapers.
Sadly, the data are typically available for months or years in criminal private groups when stolen credentials are published on the deep and dark web.
The important thing is to detect exposures before criminals might utilize them.
It is becoming harder to lay out the threat landscape. Attackers not only create new technologies to avoid security systems, but threats in targeted attacks are increasing in complexity and precision.
SOCRadar publishes a series of reports, which provide relevant insights on the evolution of cyber threats. The content of the report is intended to be agnostic with industry and vendors and provides enough references about the threat in the Dark Web. The method was based on in-depth research.
According to the report, there is an increase in Phishing, and Ransomware holding its place as cyber criminals’ top motivation; and the COVID-19 environment fueling attacks on homes, businesses, governments and critical infrastructure.
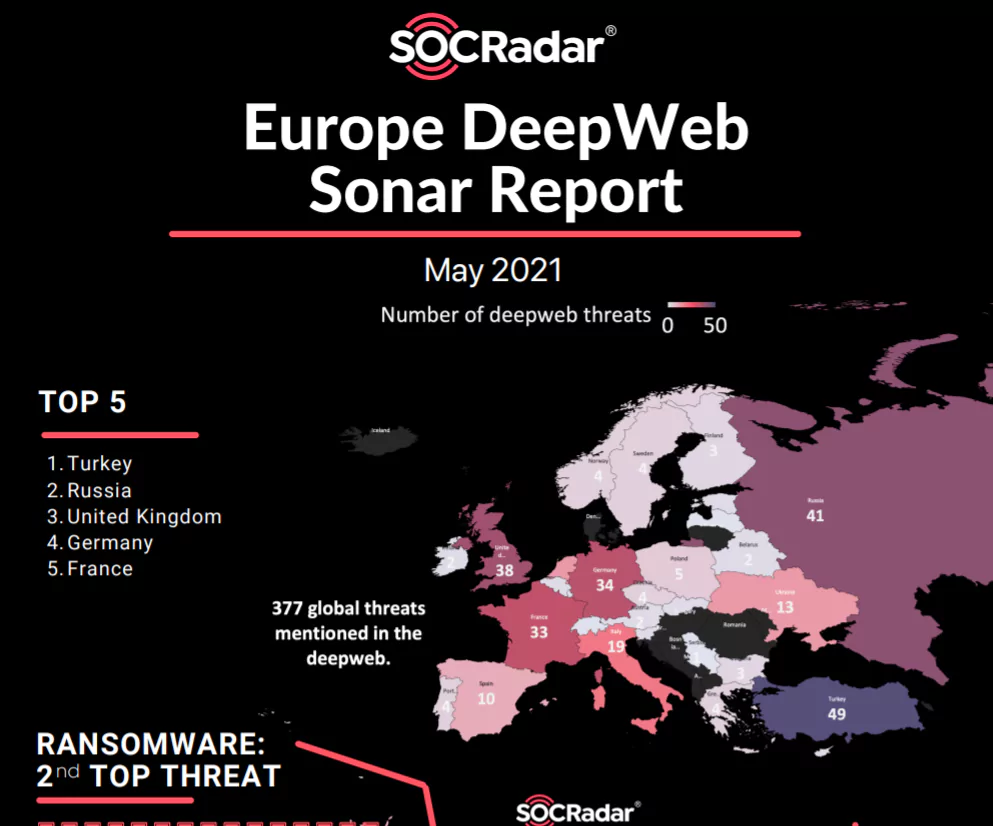
Cyber Threats against Europe
The report states that there were 377 global threats on the Dark Web in May. Using data from SOCRadar DarkMirror, the figure below shows the top European countries that have the greatest number of Deep Web threats.
Figure 1 – The list of the top European countries that have the greatest number of Deep Web threats
Turkey comes in first place, with 49 threats. The malware attacks in Turkey in 2020 increased by 81% to 1.6 million. China, USA, Taiwan and Russia take the lead amongst the origins of cyber-attacks against Turkey.
In May, Ransomware versions have grown to incorporate exfiltration of data, involvement in DDoS operations and anti-detection components. One variation deletes files, whether a payment has been paid or not. The ability to lock club-based backups while systems are continually backed up in real time is another alternative. Additional versions are targeted towards mobile phones and IoT devices. In the report, ransomware mentioned the top 2nd top threat. 30% of deep web threats are from ransomware gangs.
Figure 2 – Top Threats
Top ransomware contributors are Avaddon, Conti, REvil (Sodinokibi).
Figure 3 – Top Contributors
A Remote Desktop Protocol Attack is a data breach occurring through the remote desktop protocol of the user (or RDP). An RDP enables one computer to connect without direct touch to another computer or to a network. As more people work from home, RDP attacks increase.
Figure 4 – Top Access Methods
Threats to the security of e-commerce in online trade cause disasters. Up to 32,4% of all effective threats are reported by industry every year. In general hackers utilize countless harmful tactics to attack e-commerce websites and customers.
Figure 5 – Top Industries in Deep Web Index
Cyber Threats against Middle East and Africa
In the MEA region, Israel is at the top of the list with 20 cyber threats in May. Israel is experiencing a new cyber-attack wave related to ideological hacktivism motivated by geopolitics. Iranian hackers to the present cyber campaign, masking them as Russian groups. The actors of the same threat were considered accountable for Israel’s recent cyber campaign.
Figure 6 – The list of the top MEA countries that have the greatest number of Deep Web threats
Based on the study the top Dark Web threat is data breach. A data breach may involve personal health information (PHI), personally identifiable information (PII), trade secrets or other confidential information. 37% of deep web posts share data (mostly customer data) for free.
Figure 7: Top Dark Web Threats
When it comes to ransomware gangs, REvil group targets the MEA region more than Europe.
Figure 8 – Top Contributors
Attacks against access require some form of capacity for intrusion. These can be so easy as obtaining the credentials of an account holder to connect foreign devices directly to the network infrastructure. These cyberattacks are as sophisticated as they are. Often these access attacks may be equated to recognition in logical or physical terms; logical on the Internet and physical on the social engineering side. The network access is the top access method for the MEA region.
Figure 9 – Top Access Methods
Government was at the top of the list for the most affected industries in May with 14,58%. It is obvious that cyberware between countries never stops. E-commerce is just right after the government sector with 10,42%. E-commerce security threats are causing havoc in online trading. The industry experiences up to 32.4% of all successful threats annually. Hackers usually target e-commerce store admins, users, and employees using a myriad of malicious techniques.
Figure 10: Top Industries in Dark Web Index
Based on the reports, following trends are observed:
- Cyber security attack surfaces continue to grow as we approach a new digital transformation period.
- A new social and economic standard will be introduced after COVID-19, which will be even more dependable and secure.
- In targeted cyberattacks the use of social media platforms is a major trend, reaching many areas and types of threats.
- Carefully designed and carried out state-sponsored actors thoroughly and consistently target high values (e.g., intellectual property and state secrets).
- Subjects such as credential theft are used to massively disperse short-lived and widespread attacks.
- Subjects such as credential theft are used to massively dispersed short-lived and widespread assaults.
- Financial motivation is still underlying most cyber-attacks.
- Ransomware is pervasive to many organizations with expensive repercussions.
- Many issues with cybersecurity remain unrecognized or take a long time.
- With greater security automation, organizations are investing more in preparation utilizing the core capacity of cyber threat intelligence (CTI).
- Since it leverages the human dimension and supply chain as the weakest links, the number of phishing victims continues to grow.
Do you want to know more about what’s happening with the Dark Web?
If yes, then try SOCRadar.
RECEIVE A FREE DARK WEB REPORT FOR YOUR ORGANIZATION
SOCRadar, the early warning system for information security, analyzes thousands of deep web resources including hacker forums and social channels every day.
- Deep web mentions
- Compromised credentials
- Malware/bot-infected users
- Highly critical data exposure findings
- Date of the latest exposure
Discover SOCRadar® Community Edition for free
With SOCRadar® Community Edition, you’ll be able to:
- Discover your unknown hacker-exposed assets
- Check if your IP addresses tagged as malicious
- Monitor your domain name on hacked websites and phishing databases
- Get notified when a critical zero-day vulnerability is disclosed
Free for 12 months for 1 corporate domain and 100 auto-discovered digital assets.
Try for free



































