
Complex RCE Vulnerability (CVE-2023-39143) in PaperCut Application Servers
PaperCut NG and PaperCut MF are extensively utilized software solutions for print management servers.
CVE-2023-39143 refers to path traversal vulnerabilities found in PaperCut NG and PaperCut MF versions released prior to v22.1.3. These vulnerabilities could potentially allow unauthorized access to read, delete, and upload arbitrary files onto a vulnerable application server.
1. What is the CVE-2023-39143 vulnerability in PaperCut application servers about?
These vulnerabilities could potentially allow unauthorized access to read, delete, and upload arbitrary files onto a vulnerable application server under certain circumstances.
The vulnerability specifically impacts PaperCut servers operating on Windows. When the external device integration setting is enabled, it opens the possibility for file uploads that could lead to remote code execution. It is worth noting that this setting is enabled by default in certain PaperCut installations, such as the PaperCut NG Commercial version or PaperCut MF.
CVE-2023-39143 enables unauthenticated attackers to execute code remotely, potentially leading to unauthorized access to the application server and allowing them to read, delete, and upload arbitrary files.
2. How does the complexity of CVE-2023-39143 differ from a previously leveraged vulnerability in PaperCut?
Unlike a previously leveraged vulnerability (CVE-2023-27350) in PaperCut, CVE-2023-39143 is more complex to exploit. It requires multiple issues to be chained together to successfully compromise a server.
3. Which versions of PaperCut NG and PaperCut MF are affected by CVE-2023-39143?
CVE-2023-39143 affects versions released before v22.1.3.
4. What can attackers potentially achieve by exploiting CVE-2023-39143?
By exploiting CVE-2023-39143, attackers can remotely execute code on vulnerable PaperCut application servers. This could result in unauthorized access and manipulation of files on the compromised servers.
5. How has the vulnerability been fixed, and when was the patch released?
The vulnerability was fixed in late July with the release of PaperCut NG and MF 22.1.3.
6. Were there any additional vulnerabilities addressed in the same release that fixed CVE-2023-39143?
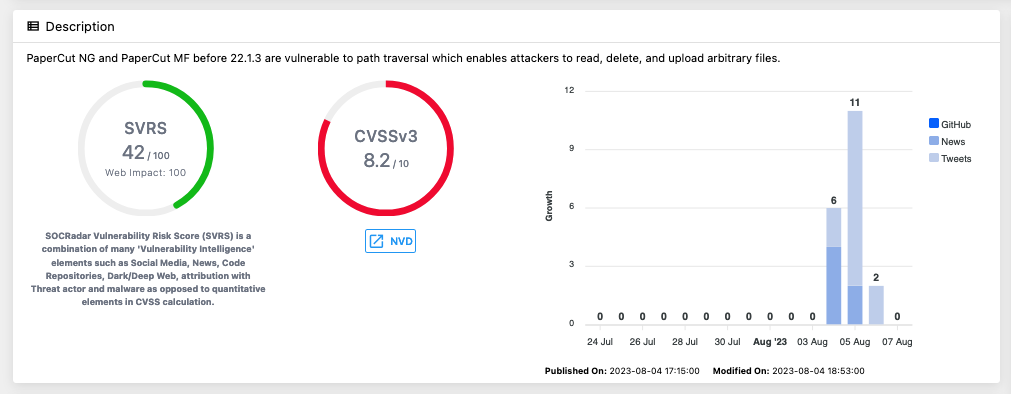
The same release that fixed CVE-2023-39143 also addressed a potential Denial of Service (DoS) vulnerability (CVE-2023-3486) reported by Tenable researchers and an escalation of privileges issue found by Trend Micro researchers in a third-party dependency used by PaperCut.
7. How can PaperCut server administrators check if their systems need upgrading to protect against CVE-2023-39143?
Horizon3.ai researchers have shared commands that customers can use to check whether their PaperCut servers need upgrading to protect against CVE-2023-39143. They advise users to plan an upgrade to the latest release (v22.1.3) to ensure they are protected.
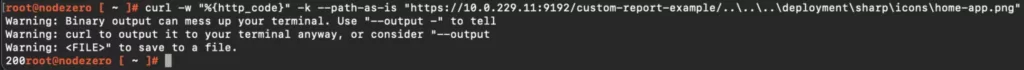
The following command checks if a PaperCut server is not patched and running on Windows.
curl -w “%{http_code}” -k –path-as-is “https://
A 200 response indicates the server has not been patched and is running on Windows. A 404 response indicates the server has been patched or not running on Windows.
Horizon3.ai is not releasing further details at this time to provide users adequate time to upgrade.
8. Apart from patching, what other mitigation measures can be taken to reduce the risk of exploitation for CVE-2023-39143?
To mitigate the risk of exploitation, administrators can set up an allow-list and populate it with device IP addresses permitted to communicate with the server. This additional security measure can help reduce the exposure to potential attackers. Please also refer to the PaperCut security best practices guide for more information about mitigation.
9. What details have Horizon3.ai researchers shared about the vulnerability, and why are they withholding further information for now?
Horizon3.ai researchers have shared some details about the vulnerability, but they have not released the proof-of-concept (PoC) code at this time. They have chosen to withhold further information to provide users adequate time to upgrade and protect their systems.
10. Leveraging SOCRadar to Mitigate Vulnerabilities like CVE-2023-39143
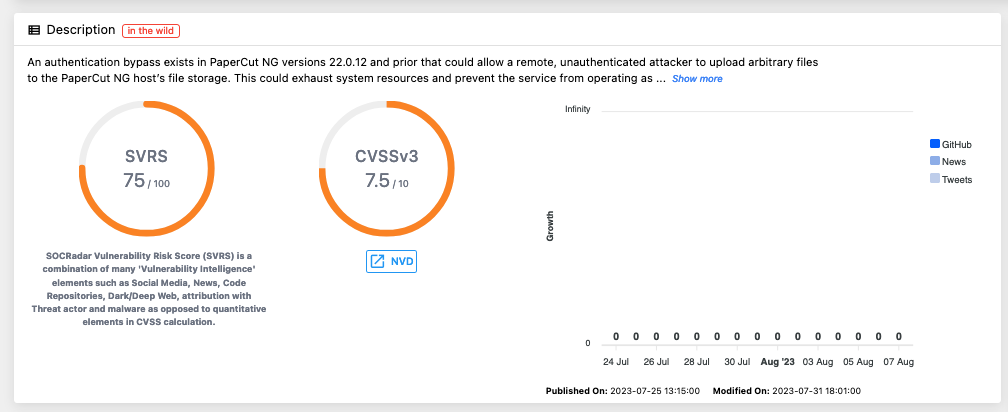
SOCRadar offers a powerful Vulnerability Intelligence module that assists organizations in addressing potential threats such as CVE-2023-39143 and similar vulnerabilities. Threat actors constantly monitor vulnerability trends and seek weak points in public-facing services and technology. With SOCRadar, businesses can receive real-time alerts whenever a new critical vulnerability or exploit is identified for pre-defined product components and technologies associated with their auto-discovered digital footprint. This proactive approach allows organizations to stay ahead of potential risks and take immediate action to patch and secure vulnerable systems.



































