
Create More Effective SOC With the Mitre ATT&CK Framework
The ATT&CK framework is a powerful tool to improve cyber defence and to create a more effective SOC. According to the SANS report, the MITRE ATT&CK creates;
- The threat intelligence groups that are known to utilize these attack methods
- Unique methods used by malicious actors in implementing the attacks
- Mitigations and detection methods for preventing or identifying attacker techniques
Shortly, by using the knowledge body of MITRE ATT&CK, SOC teams build more effective cyber defence strategies and fasten the decision-making process.
What is MITRE ATT&CK framework?
Founded in 1958, MITRE is a non-profit company whose mission is to solve the problem of a safer world. A new curated knowledge base, known as MITRE ATT&CK, which stands for Adversarial Tactics, Techniques, and Common Knowledge is a platform that organizes and categorizes tactics, techniques, and procedures (TTPs) used by threat actors in the digital world to help organizations identify gaps in their cyber defences.
What is MITRE PRE-ATT&CK?
Building on ATT&CK, PRE-ATT&CK provides the ability to prevent an attack before the adversary has a chance to get in. The 15 tactic categories for PRE-ATT&CK were derived from the first two stages (recon and weaponize) of a seven-stage Cyber Attack Lifecycle (aka Lockheed Martin’s Cyber Kill Chain.
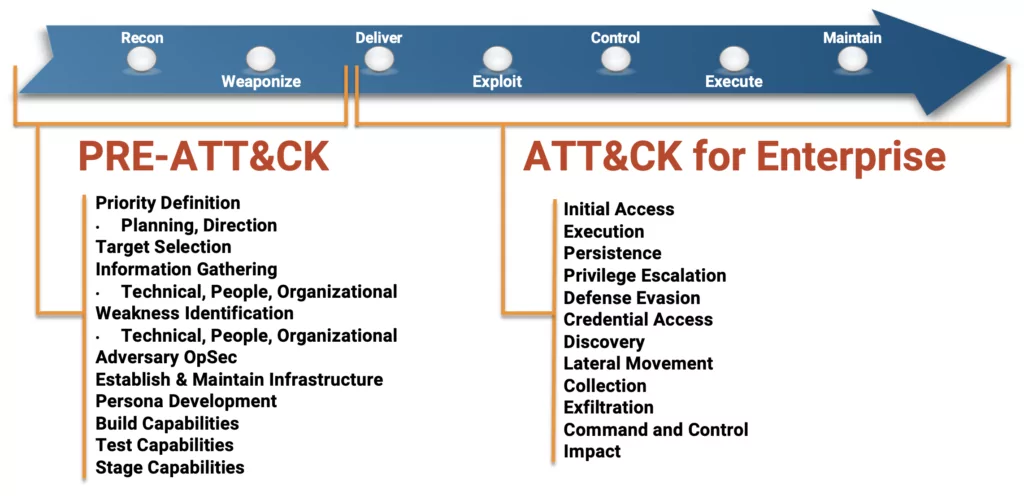
PRE-ATT&CK provides defenders with the ability to answer questions such as:
- Are there signs that the adversary might be targeting you?
- What commonly used techniques does the adversary use against you?
- How should you prioritize cyber threat intelligence data acquisitions and analytics to gain additional insights to “see” the adversary before the exploit occurs?
On October 27, 2020, MITRE published ATT&CK v8. This release deprecates and removes the PRE-ATT&CK domain from ATT&CK, replacing its scope with two new Tactics in Enterprise ATT&CK Reconnaissance and Resource Development. A new platform has also been added to ATT&CK to represent the environment these techniques occur in, PRE.
Understanding ATT&CK matrices
MITRE has divided ATT&CK into many various matrices: enterprise, mobile, and PRE-ATT&CK. Each matrix includes different strategies and tactics relevant to the topic of the matrix.
The ATT&CK Matrix for Enterprises describes what an attacker normally does when infiltrating a corporate network. The information collected during an attack is presented in the form of a matrix of TTPs as well as information about the tactics, techniques, and procedures of the attacker.
- Tactics; ATT&CK framework consists of 14 tactics that outline the “why” behind an adversary’s approach and represent the objective of their attack.
- Techniques; ATT&CK techniques are “how” an adversary achieves an objective.
- Procedures; Procedures are the specific steps an adversary takes to execute and implement a Technique.
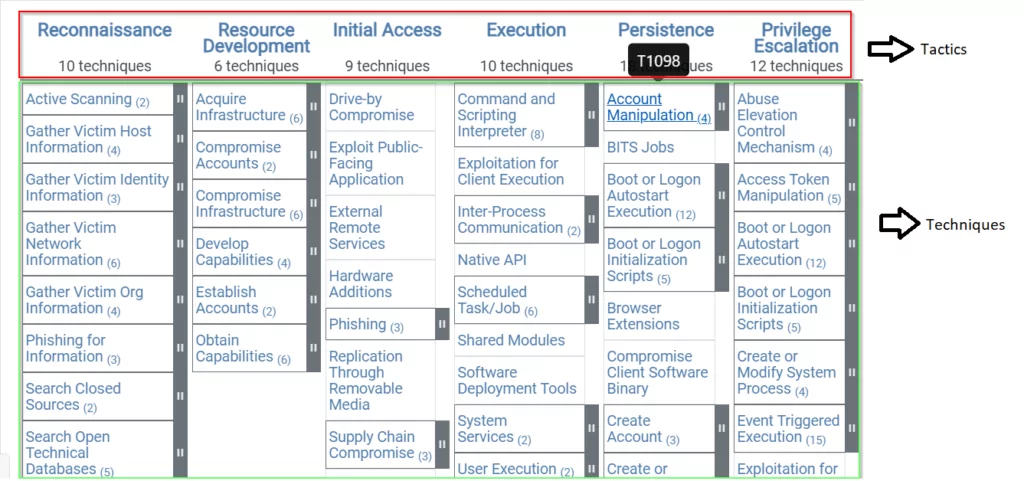
These techniques represent the various ways in which a cyber-attacker can achieve goals, goals, and tactics. It can provide a comprehensive solution to prevent and mitigate cybersecurity threats. By combining these two solutions, an organization’s defences can be improved by counteracting enemy actions at all stages of the attack lifecycle.
For each technique listed in the MITRE ATT&CK, the following information is provided:
- An identifier
- The tactic that it’s associated with
- The platform’s applicable to
- System or permission requirements
- Defence strategies bypassed
- Data sources that identify the use of the technique
- Mitigations and detection methods
The information in the ATT&CK matrix is part of a continuously updated collection of data to understand various methods of cybersecurity. MITRE has joined forces in its ongoing cybersecurity work and was originally developed for internal project deployment. It includes information about cybercriminals who use various attack techniques, tactics, techniques, and procedures of cyber attackers.
What can be done with ATT&CK?
The ongoing development of ATT&CK demonstrates that SOC teams have to continue upgrading their methodologies as quickly as adversaries go by discovering new threats and avoiding data breaches.
The information provided by ATT&CK framework is used by SOC teams to prioritize which scope areas must first be addressed and to locate vulnerabilities in security measures.
ATT&CK techniques, tactics, and procedures can be used for prioritizing threat mitigation and uncovering security gaps.
- Threat intelligence mapping; The organized and accessible listing of attackers’ TTPs is a valuable guide for threats to SOC teams. In the supposition that an attacker’s potential activity is predictive on the basis of previously experienced TTPs, it is useful for all cyber-defence and threat analysis teams to structured record this information (including supporting details).
- Gap identification; In addition to information on how to identify, detect, and mitigate the technique, each technique in ATT&CK is described. And you can illustrate the exposure gaps in an enterprise by programmatically removing information from the database for interesting techniques. ATT&CK helps you to reflect on what data is lacking and have a deeper view of the organization’s defensive capability.
- Detections and investigations; ATT&CK procedures and tactics observed or detected can be cited by the Security Operations Center (SOC) and incident response unit. This allows explaining where defence capabilities and faults are and validate controls for prevention and identification and can expose misconfigurations and other organizational problems.
- Mapping defensive controls; When reference is made to ATT&CK techniques and the techniques they implement, defensive controls may have well-knowing meaning.
- Threat hunting; ATT&CK defences mapping gives you a road map of defensive vulnerabilities to provide the perfect place for hunters to find missed attacking activities.
- Tool integrations; Different tools and resources will standardize tactics and techniques for ATT&CK to include security which is often deficient in cohesion.
- Sharing; Defenders should maintain shared awareness by using ATT&CK tactics or techniques while exchanging information on an offence, an actor or party, or defensive controls.
- Red team / Penetration test activities; Planning, execution, and reporting of red team, purple team, and penetration test activities can use ATT&CK to speak a common language with defenders and report recipients as well as amongst themselves.
- Referencing actors; Actors and groups can be associated with specific, definable behaviors.
Use case: Application of threat intelligence
In addition to detected attackers, threat intelligence data is passed to most SOCs. These teams are frequently mixed up in the intellect of attack. They are most commonly used to decode breach events and attempt to fix high-priority warnings. You can frankly admit that you have no time to stand back and look at the picture more strategically.
MITRE ATT&CK gives you the ability to incorporate the risk information that you believe is related to your organization’s highly dangerous operation and to make it permanently part of your cyber defence. The threats most definitely can be mapped to potential intruder strategies and methods they use. MITRE ATT&CK allows you to chart the vulnerabilities in the face of such challenges. You will then create a strategy to fill these holes and strengthen the defenses.
Challenges when using ATT&CK
- Not all techniques are always malicious
- Not all techniques are easy to detect
- Some techniques have many possible methods of execution
- Some techniques are listed under multiple tactics
ATT&CK projects and resources
Following projects help organizations to use ATT&CK more efficiently.
Caldera is MITRE’s automated attach technique emulation tool
Cascade is MITRE’s blue team automation toolset
Attack Navigator is a web application you can use to make notes and track your ATT&CK status
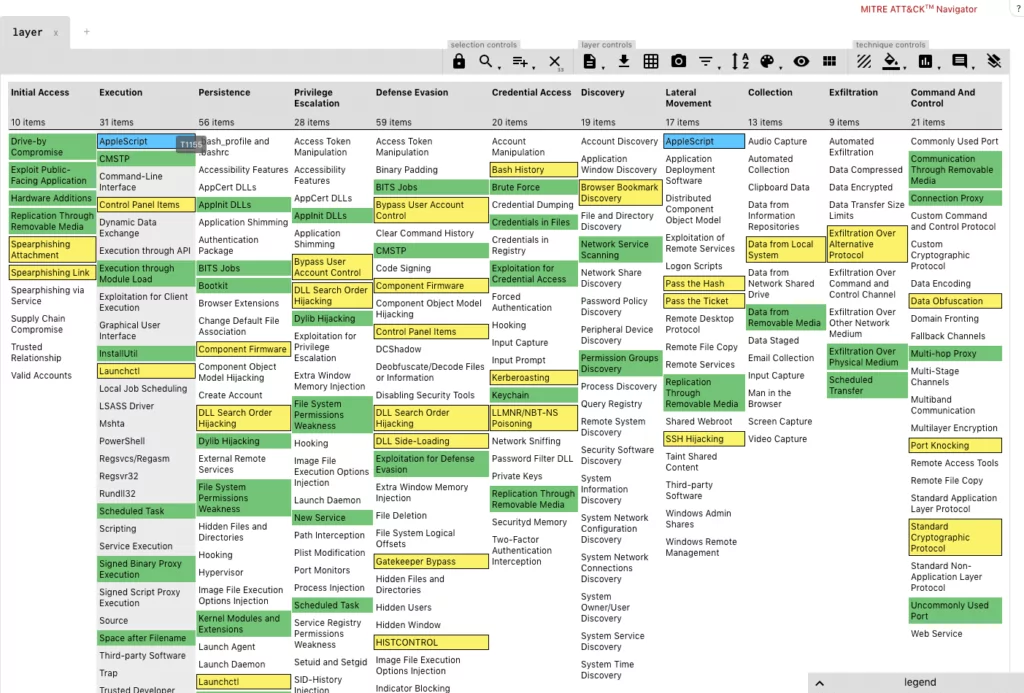
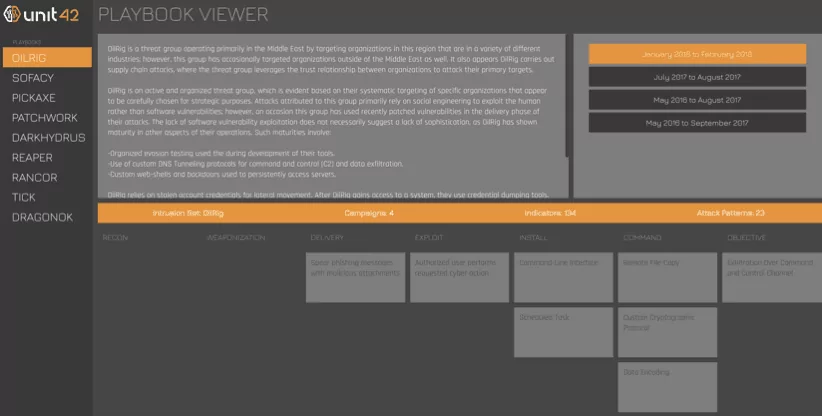
Unit42 is Palo Alto’s Adversary Playbook built on the ATT&CK model
MITRE’s Cyber Analytics Repository is a separate project from ATT&CK that tracks detailed information about how to detect techniques
ATT&CK Tableau Table by Cyb3rPanda: Cyb3rPanda has loaded ATT&CK into a public Tableau instance for easy pivoting and filtering
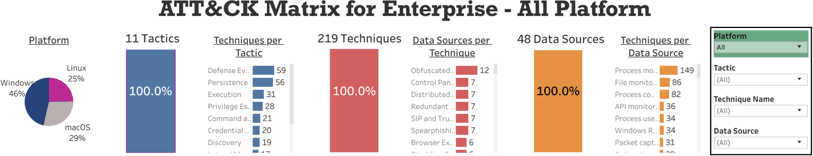
SOC teams can use SOCRadar solutions for high visibility into the ATT&CK tactics, techniques, and procedures of the most skilled adversaries’ for accurate threat detection.
Discover SOCRadar® Community Edition for free
With SOCRadar® Community Edition, you’ll be able to:
- Discover your unknown hacker-exposed assets
- Check if your IP addresses tagged as malicious
- Monitor your domain name on hacked websites and phishing databases
- Get notified when a critical zero-day vulnerability is disclosed
Free for 12 months for 1 corporate domain and 100 auto-discovered digital assets.


































