
Critical Patches for Oracle Products including MySQL (CVE-2023-20862), WebLogic Server (CVE-2023-26119) and VirtualBox VM (CVE-2023-22018) with critical vulnerabilities
Oracle has recently released 508 security updates on July 18, addressing critical vulnerabilities in 32 of its products, including MySQL, WebLogic Server, and VirtualBox VM. This patch has a total of 183 unique CVEs, of which 76 patches are for fixing critical issues.
Notably, Oracle MySQL, WebLogic Server and VirtualBox VM are three products that come to the front due to the severity of the identified vulnerabilities and products’ roles in the enterprise infrastructure.
For MySQL, Oracle has issued 24 patches to address a staggering 11 vulnerabilities that, if left unpatched, could be exploited by attackers to achieve remote exploitation without requiring authentication. Equally alarming is the fact that Oracle Database Server contains one remotely exploitable issue that does not require authentication, presenting a significant security risk.
Red Alarm for Oracle MySQL and Oracle Database Server
The Oracle MySQL Risk Matrix, as disclosed in the vendor’s blog post, highlights two critical level issues with CVSS scores of 9.8 and 9.1, which stand out at the top of the list.
CVE-2023-20862 is one of the critical vulnerabilities that impacts the MySQL Enterprise Monitor’s Monitoring: General (Spring Security) component. If successfully exploited by remote attackers without authentication, this vulnerability could compromise the confidentiality, availability, and integrity of affected assets. Oracle warns that versions 8.0.34 and earlier are vulnerable to this issue.
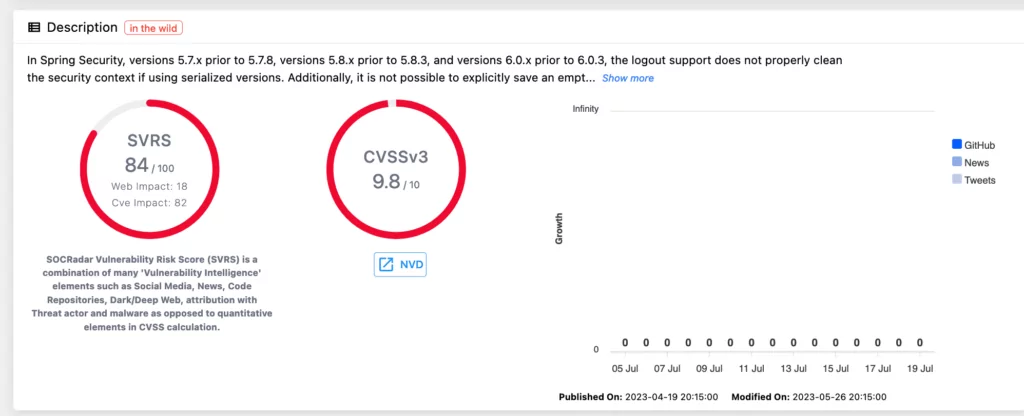
Another vulnerability affecting MySQL Enterprise Monitor’s Monitoring: General (Apache Ivy) component is assigned CVE-2022-37865, having a CVSS score of 9.1. While this vulnerability also allows remote attackers to exploit the issue without authentication, its impact is limited to availability and integrity, sparing confidentiality. Both vulnerabilities in the Oracle MySQL family are deemed relatively easy to exploit.
Oracle WebLogic Server in the list with a high level vulnerability – CVE-2023-26119
Moving on to Oracle WebLogic Server, it too presents a high-level vulnerability, specifically CVE-2023-26119, which holds a CVSS score of 9.8. This vulnerability pertains to the Centralized Thirdparty Jars (NekoHTML) component of WebLogic Server, and if successfully exploited by a remote attacker without requiring special privileges, it could severely compromise the confidentiality, integrity, and availability of the targeted system. Versions 12.2.1.4.0 and 14.1.1.0.0 of WebLogic Server are reported as affected.
VirtualboxVM’s RDP protocol is vulnerable to exploitation of remote attackers without authentication – CVE-2023-22018
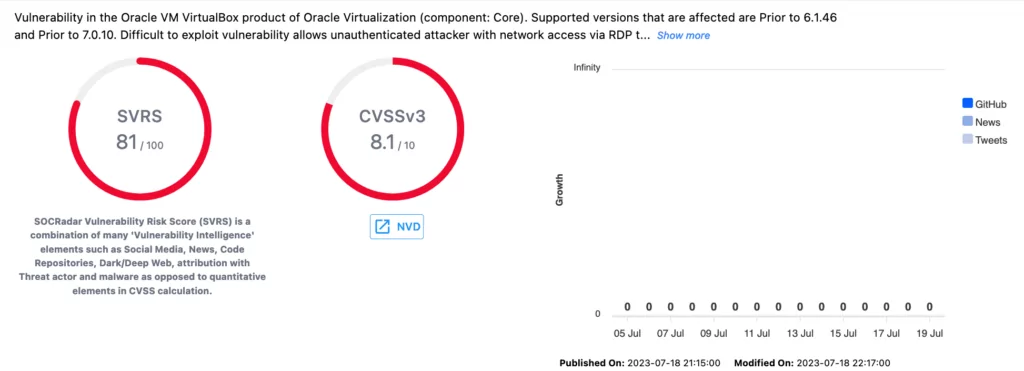
VirtualBox VM also made it to the list of critical vulnerabilities with CVE-2023-22018. This vulnerability affects the RDP protocol of the Core component of VirtualBox VM. Despite its high attack complexity level, the issue can be exploited by a remote attacker without authentication.
Once successfully compromised, the targeted system’s integrity, availability, and confidentiality are at great risk. Versions prior to 6.1.46 and prior to 7.0.10 of VirtualBox VM are reported to be vulnerable to this issue across all operating systems.
What should users do?
Protecting your systems from potential attacks should always be a top priority, and prompt patching is an essential step towards safeguarding your valuable data and resources.
Given the severity of these vulnerabilities, it is imperative for users to take immediate action. Oracle strongly advises all customers to apply the relevant patches provided in the July 2023 Critical Patch Update (CPU). For comprehensive details on the patches and affected products, please refer to the official advisory released by Oracle.
You can refer to the vendor’s blog for detailed information. https://www.oracle.com/security-alerts/cpujul2023.html
Strengthening Cybersecurity Defenses Against Critical Vulnerabilities with SOCRadar Vulnerability Intelligence
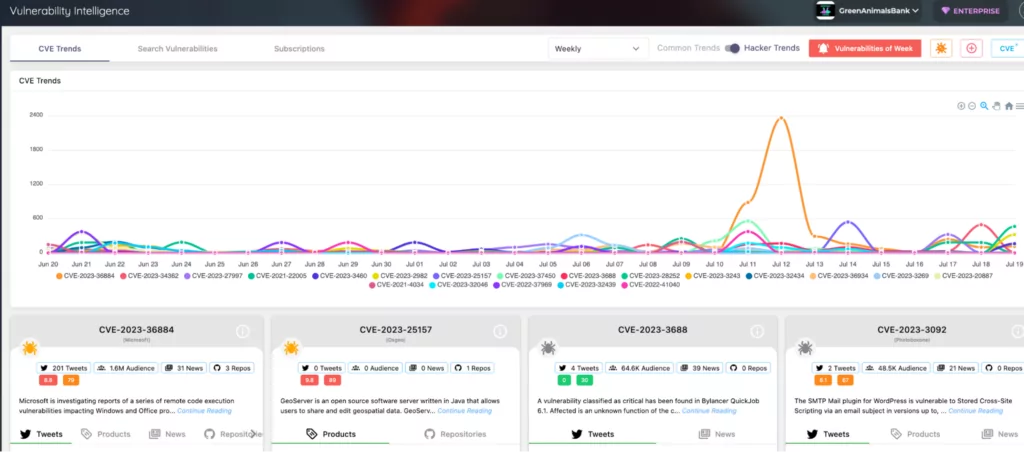
SOCRadar’s Vulnerability Intelligence module is a vital asset for organizations facing issues like the critical vulnerabilities announced by Oracle. By closely monitoring vulnerability trends and threat actor activities, SOCRadar ensures real-time alerting whenever a new critical vulnerability or exploit relevant to an organization’s digital footprint is detected. This enables prompt action to prevent potential disruptions to the business.
Through auto-discovery of an organization’s digital footprint, including public-facing services and technologies, SOCRadar helps identify potential attack vectors and vulnerable areas. The platform provides targeted vulnerability insights, allowing organizations to swiftly assess and verify the vulnerability levels of their systems, specifically addressing affected components like MySQL, WebLogic Server, and VirtualBox VM.
SOCRadar’s analysis of threat actor activities further enhances cybersecurity readiness. By understanding the vulnerabilities actively exploited by threat actors, organizations can prioritize patch management efforts, streamlining vulnerability management processes. Armed with contextual awareness about vulnerabilities, including severity, impact, and affected versions, organizations can make informed decisions, allocate resources efficiently, and proactively safeguard their digital assets against emerging threats.



































