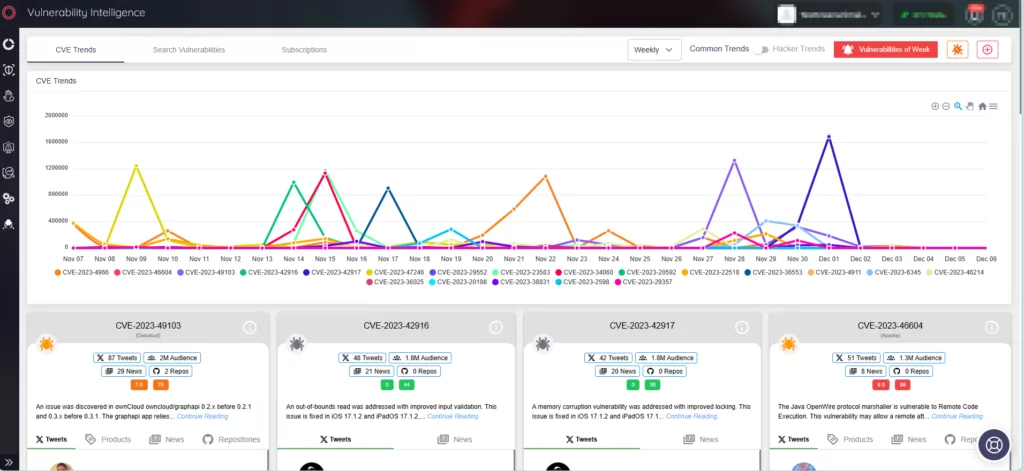
Critical RCE Vulnerabilities in Atlassian Products: CVE-2022-1471, CVE-2023-22522, CVE-2023-22524, and CVE-2023-22523
[Update] December 11, 2023: “CISA Urges Swift Action on Critical Atlassian Vulnerabilities”
Atlassian has issued critical security updates addressing multiple vulnerabilities in its suite of products. Identified as CVE-2022-1471, CVE-2023-22522, CVE-2023-22524, and CVE-2023-22523, these vulnerabilities pose severe risks, including Remote Code Execution (RCE), across various Atlassian Data Center and Server Products.
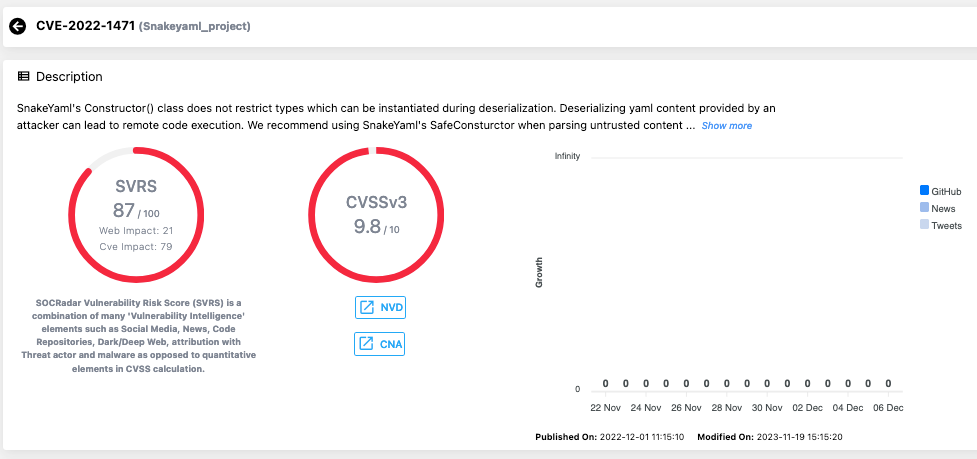
These vulnerabilities have been rated with high CVSS scores, signifying their critical nature and the urgent need for patching. The most severe, CVE-2022-1471 in the SnakeYAML library, has a CVSS score of 9.8, indicating a significant threat level.
Vulnerability Details
CVE-2022-1471 is a deserialization flaw in the SnakeYAML library used by multiple Atlassian products, leading to potential RCE. Similarly, CVE-2023-22522 is an RCE vulnerability in the Confluence Data Center and Server, allowing attackers to inject unsafe user input into Confluence pages. CVE-2023-22524 affects the Atlassian Companion App for MacOS, enabling attackers to execute arbitrary code via WebSockets. Lastly, CVE-2023-22523 is an RCE vulnerability in Assets Discovery, impacting machines with the Assets Discovery agent installed.
Affected Atlassian Products and Versions
A wide range of Atlassian products and versions are affected by these vulnerabilities, including but not limited to Automation for Jira (A4J), Bitbucket Data Center and Server, Confluence Data Center and Server, and the Atlassian Companion App for MacOS. For more information about the affected products, please refer to the advisory.
| Security Advisory | Affected Products | Vulnerabilities |
| SnakeYAML library RCE (Remote Code Execution) Vulnerability impacts Multiple Products |
|
Remote Code Execution (CVE-2022-1471) |
| RCE (Remote Code Execution) Vulnerability in Confluence Data Center and Server |
|
Remote Code Execution (CVE-2023-22522) |
| RCE (Remote Code Execution) Vulnerability in Atlassian Companion App for MacOS |
|
Remote Code Execution (CVE-2023-22524) |
| RCE (Remote Code Execution) Vulnerability in Assets Discovery |
|
Remote Code Execution (CVE-2023-22523) |
Proof-of-Concept (PoC) Exploit Is Available for CVE-2022-1471
A Proof-of-Concept (PoC) exploit code for the CVE-2022-1471 vulnerability in the SnakeYAML library is available on GitHub. It is important to note again that the SnakeYAML library is utilized by various Atlassian products, and the exploitation of CVE-2022-1471 could lead to RCE.
Update Your Atlassian Products to the Latest Version
Atlassian strongly recommends patching affected product installations to the latest or fixed versions as soon as possible. There are no alternative mitigations for these vulnerabilities, emphasizing the importance of timely software updates.
Atlassian has released patches for affected versions across its product range. For instance, Automation for Jira should be updated to version 9.0.2 or 8.2.4, and Confluence Data Center and Server to version 7.19.17 (LTS) or 8.4.5.
CISA Urges Swift Action on Critical Atlassian Vulnerabilities
In a recent alert, the Cybersecurity and Infrastructure Security Agency (CISA) shared Atlassian’s official advisories addressing the CVE-2022-1471, CVE-2023-22522, CVE-2023-22524, and CVE-2023-22523 vulnerabilities.
CISA cautions that attackers may exploit these vulnerabilities to gain control of affected systems and urges users and administrators to review the advisories in order to take the necessary actions. In response to the CISA alert, organizations should promptly address these critical vulnerabilities, adhering to their vulnerability management principles.
Empowering Defense with SOCRadar’s Vulnerability Intelligence
To stay ahead of such critical vulnerabilities, SOCRadar XTI provides real-time alerts and comprehensive Vulnerability Intelligence. This service is crucial for organizations to keep abreast of vulnerabilities exploited by threat actors, offering actionable insights and context. Utilizing SOCRadar’s solutions ensures enhanced cybersecurity measures and timely response to emerging threats.