
Critical RCE Vulnerability (CVE-2024-4577) in PHP on Windows: Patch Now Available
[Update] August 21, 2024: “CVE-2024-4577 Exploited to Deploy Msupedge Backdoor”
[Update] June 13, 2024: “CISA Adds Critical PHP Vulnerability (CVE-2024-4577) to KEV Catalog, Urges Organizations to Patch”
[Update] June 11, 2024: “CVE-2024-4577 in PHP Actively Exploited by TellYouThePass Ransomware”
A remote code execution (RCE) vulnerability in PHP has been discovered by DEVCORE during their continuous offensive research. Due to the widespread use of PHP in the web ecosystem and the ease of exploitability, the severity of the vulnerability has been classified as critical (CVSS score 9.8).
This issue was promptly reported to the PHP official team, who released a patch on June 6, 2024. Below is a detailed timeline and description of the vulnerability.

The visual by DEVCORE, the team discovered the vulnerability.
The vulnerability is due to an oversight in the implementation of PHP on Windows, specifically related to the Best-Fit feature of encoding conversion. This oversight allows unauthenticated attackers to bypass previous protections (such as CVE-2012-1823) through specific character sequences, enabling the execution of arbitrary code on remote PHP servers via an argument injection attack.
What is the impact of the vulnerability?
This vulnerability affects all versions of PHP installed on the Windows operating system. The affected versions are:
- PHP 8.3 < 8.3.8
- PHP 8.2 < 8.2.20
- PHP 8.1 < 8.1.29
Since PHP 8.0, PHP 7, and PHP 5 are End-of-Life and no longer maintained, server administrators should refer to the “How to check if your system is vulnerable?” section for temporary patch recommendations in the Mitigation Measure section.
How to check if your system is vulnerable?
For common configurations like Apache HTTP Server and PHP, server administrators can use the two methods listed below to determine whether their servers are vulnerable. It should be noted that Scenario-2 is also the default configuration for XAMPP for Windows, making all versions of XAMPP installations on Windows vulnerable by default.
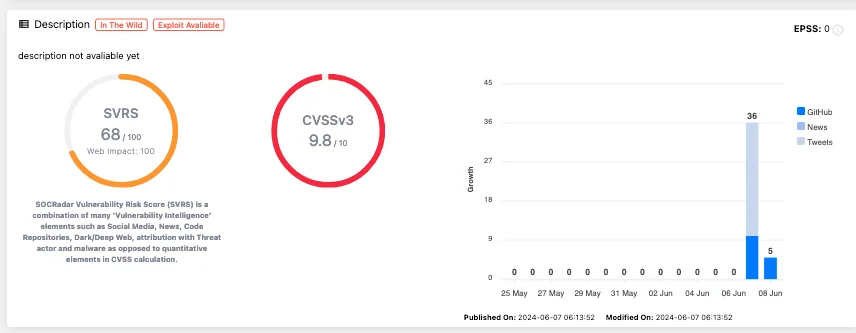
Vulnerability card of CVE-2024-4577, SOCRadar’s Vulnerability Intelligence Momdule
Scenario 1: Running PHP under CGI mode
When configuring the Action directive to map corresponding HTTP requests to a PHP-CGI executable binary in Apache HTTP Server, this vulnerability can be exploited directly. Common configurations affected include, but are not limited to:
AddHandler cgi-script .php Action cgi-script “/cgi-bin/php-cgi.exe”
Or
<FilesMatch “.php$”>
SetHandler application/x-httpd-php-cgi
</FilesMatch>
Action application/x-httpd-php-cgi “/php-cgi/php-cgi.exe”
Scenario 2: Exposing the PHP binary (also the default XAMPP configuration)
Even if PHP is not configured under the CGI mode, merely exposing the PHP executable binary in the CGI directory is affected by this vulnerability, too. Common scenarios include, but are not limited to:
- Copying php.exe or php-cgi.exe to the /cgi-bin/ directory.
- Exposing the PHP directory via ScriptAlias directive, such as:
-
ScriptAlias /php-cgi/ “C:/xampp/php/”
-
As of this writing, it has been verified that when Windows is running in the following locales, an unauthorized attacker can directly execute arbitrary code on the remote server:
- Traditional Chinese (Code Page 950)
- Simplified Chinese (Code Page 936)
- Japanese (Code Page 932)
For Windows running in other locales such as English, Korean, and Western European, it is currently not possible to completely enumerate and eliminate all potential exploitation scenarios due to the wide range of PHP usage scenarios. Therefore, it is recommended that users conduct a comprehensive asset assessment, verify their usage scenarios, and update PHP to the latest version to ensure security.
The vulnerability under the radar of threat actors
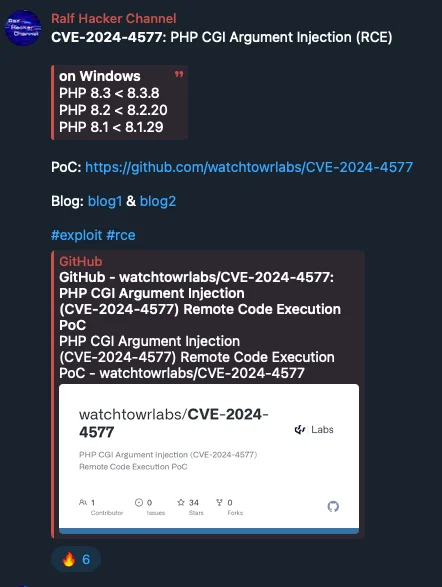
In the threat actors’ Telegram channels, it is already being spoken about.
By SOCRadar’s analysts, it has been observed that the vulnerability is being spoken about and exploitation code published by watchTowr has been already shared.
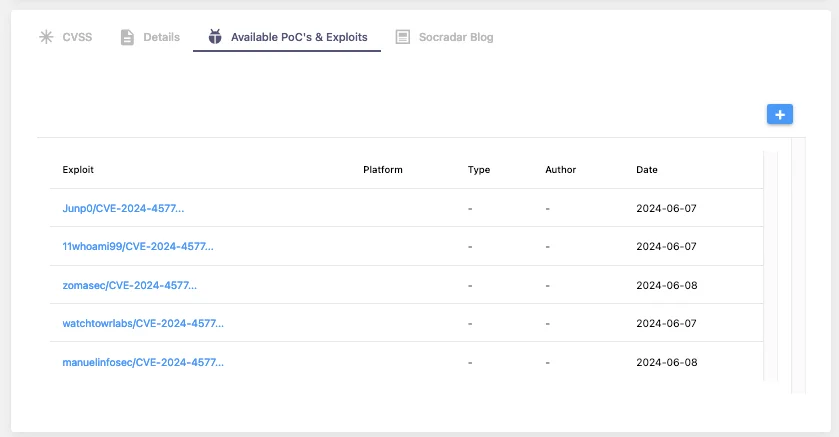
Publicly accessible PoC repositories detected by SOCRadar CTI Platform
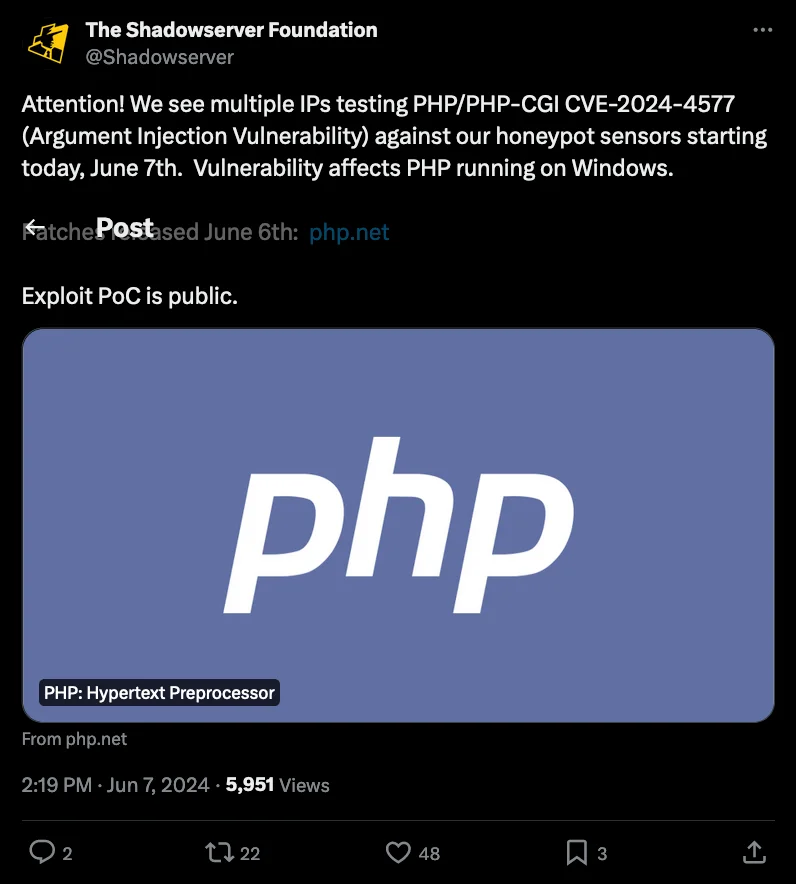
Tweet by Shadowserver Foundation states multiple IPs testing PHP/PHP-CGI vulnerability CVE-2024-4577
On June 7, The Shadowserver Foundation posted a tweet on X (formerly Twitter) that they have observed multiple IPs trying to exploit this vulnerability against their honeypots.
CVE-2024-4577 in PHP Actively Exploited by TellYouThePass Ransomware
The critical PHP vulnerability, CVE-2024-4577, is currently being exploited to deploy TellYouThePass ransomware. The attackers behind the ransomware operation leverage the vulnerability to bypass security measures and execute arbitrary code on vulnerable PHP servers.
Reportedly, threat actors began exploiting CVE-2024-4577 as early as June 8, 2024, using it to deliver the TellYouThePass ransomware.
TellYouThePass, a persistent threat since 2019, previously exploited various vulnerabilities, notably including Apache Log4j (CVE-2021-44228) and an RCE in Apache ActiveMQ (CVE-2023-46604).
The ransomware group exploits the CVE-2024-4577 vulnerability to execute arbitrary PHP code, which then triggers an HTML application file from an attacker-controlled server. This file leads to the deployment of a .NET variant of the TellYouThePass ransomware; furthermore, attackers use Living Off the Land (LOTL) tactics in these attacks, complicating detection efforts.
It is vital for organizations to patch this vulnerability immediately and implement comprehensive security measures to defend against such sophisticated attacks.
CISA Adds Critical PHP Vulnerability (CVE-2024-4577) to KEV Catalog, Urges Organizations to Patch
The Cybersecurity and Infrastructure Security Agency (CISA) issued a new alert to announce that it has added the critical PHP vulnerability, CVE-2024-4577, to its Known Exploited Vulnerabilities (KEV) Catalog.
The vulnerability was recently discovered to be exploited in attacks deploying TellYouThePass ransomware. The US agency emphasizes that such vulnerabilities are common attack vectors, posing significant risks to the federal enterprise. Consequently, CISA is mandating that federal organizations patch this vulnerability by July 3, 2024.
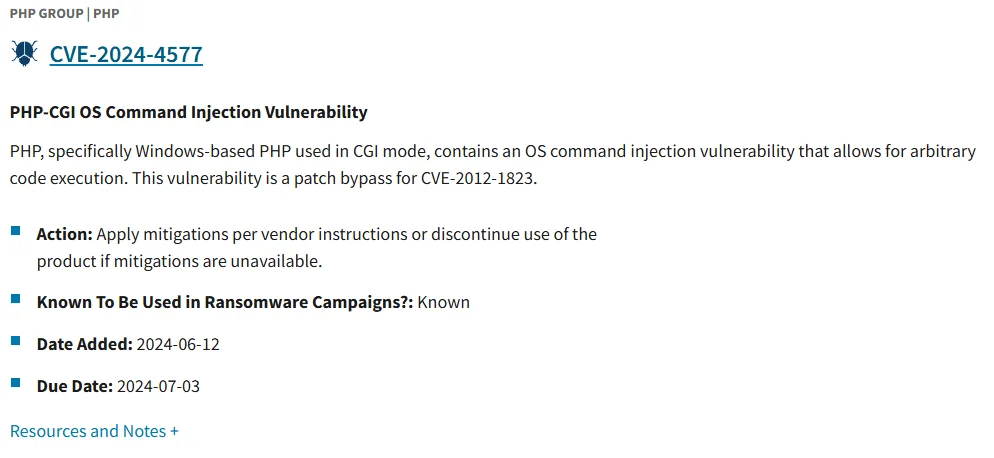
CISA KEV listing of the CVE-2024-4577 vulnerability in PHP
CVE-2024-4577 Exploited to Deploy Msupedge Backdoor
Threat actors exploited the severe PHP vulnerability, CVE-2024-4577, to install a newly discovered backdoor called ‘Msupedge’ on a university’s Windows systems in Taiwan. The malware was delivered in the form of two DLL files, weblog and wmiclnt, the first loaded by the httpd.exe Apache process.
Reportedly, Msupedge uses DNS traffic to communicate with its Command and Control (C2) server, which employs DNS tunneling for data exchange. This allows attackers to run a variety of commands, such as file downloads and process creation., while remaining stealthy.
Researchers at Symantec discovered the backdoor and observed increased scanning activity for vulnerable systems, but the motivation and attribution are undetermined.
Is there any patch or mitigation to fix the vulnerability?
It is strongly recommended that all users upgrade to the latest PHP versions of 8.3.8, 8.2.20, and 8.1.29. For systems that cannot be upgraded, the following instructions can be used to temporarily mitigate the vulnerability.
Since PHP CGI is an outdated and problematic architecture, it is still recommended to evaluate the possibility of migrating to a more secure architecture such as Mod-PHP, FastCGI, or PHP-FPM.
For users who cannot upgrade PHP:
The following Rewrite Rules can be used to block attacks. Please note that these rules are only a temporary mitigation for Traditional Chinese, Simplified Chinese, and Japanese locales. It is still recommended to update to a patched version or migrate the architecture in practice.
apache
RewriteEngine On
RewriteCond %{QUERY_STRING} ^%ad [NC]
RewriteRule .? - [F,L]
For users who use XAMPP for Windows:
XAMPP has not yet released corresponding update files for this vulnerability at the time of writing this article. If the PHP CGI feature is not needed, exposure to the vulnerability can be avoided by modifying the following Apache HTTP Server configuration:
apache C:/xampp/apache/conf/extra/httpd-xampp.conf
Locate the corresponding lines:
apache ScriptAlias /php-cgi/ "C:/xampp/php/"
And comment them out:
apache # ScriptAlias /php-cgi/ "C:/xampp/php/"
Timeline
- 2024/05/07 – The issue was reported by DEVCORE through the official PHP vulnerability disclosure page.
- 2024/05/07 – PHP developers confirmed the vulnerability and emphasized the need for a prompt fix.
- 2024/05/16 – PHP developers released the first version of the fix and requested feedback.
- 2024/05/18 – PHP developers released the second version of the fix and requested feedback.
- 2024/05/20 – PHP entered the preparation phase for the new version release.
- 2024/06/06 – PHP released new versions 8.3.8, 8.2.20, and 8.1.29.
Ensuring the security of PHP installations on Windows systems is crucial. Administrators are strongly encouraged to apply the patch and follow the mitigation measures as necessary to protect against potential exploits.
Enhance Your Security with SOCRadar’s Advanced Intelligence and Monitoring Tools
SOCRadar enhances your vulnerability management strategy with two essential services: the Vulnerability Intelligence feature and the Attack Surface Management (ASM) module.
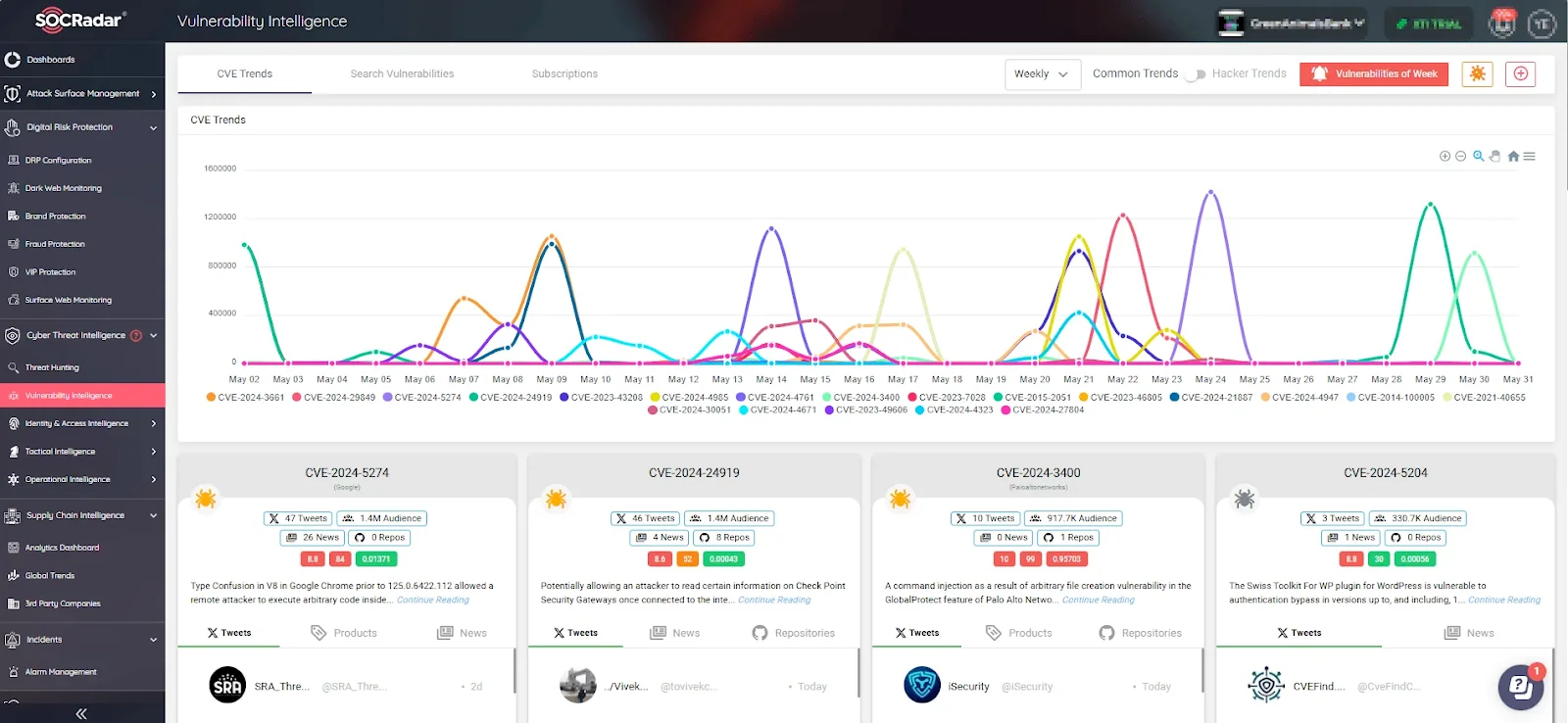
The Vulnerability Intelligence page offers continuous updates about emerging CVEs and hacker trends
The Vulnerability Intelligence feature offers a detailed view of identified security vulnerabilities. It provides real-time alerts and comprehensive insights into emerging threats, enabling organizations to stay ahead of potential breaches by monitoring new exploits and developments across various platforms. The Vulnerability Intelligence page delivers continuous updates on emerging CVEs and hacker trends.
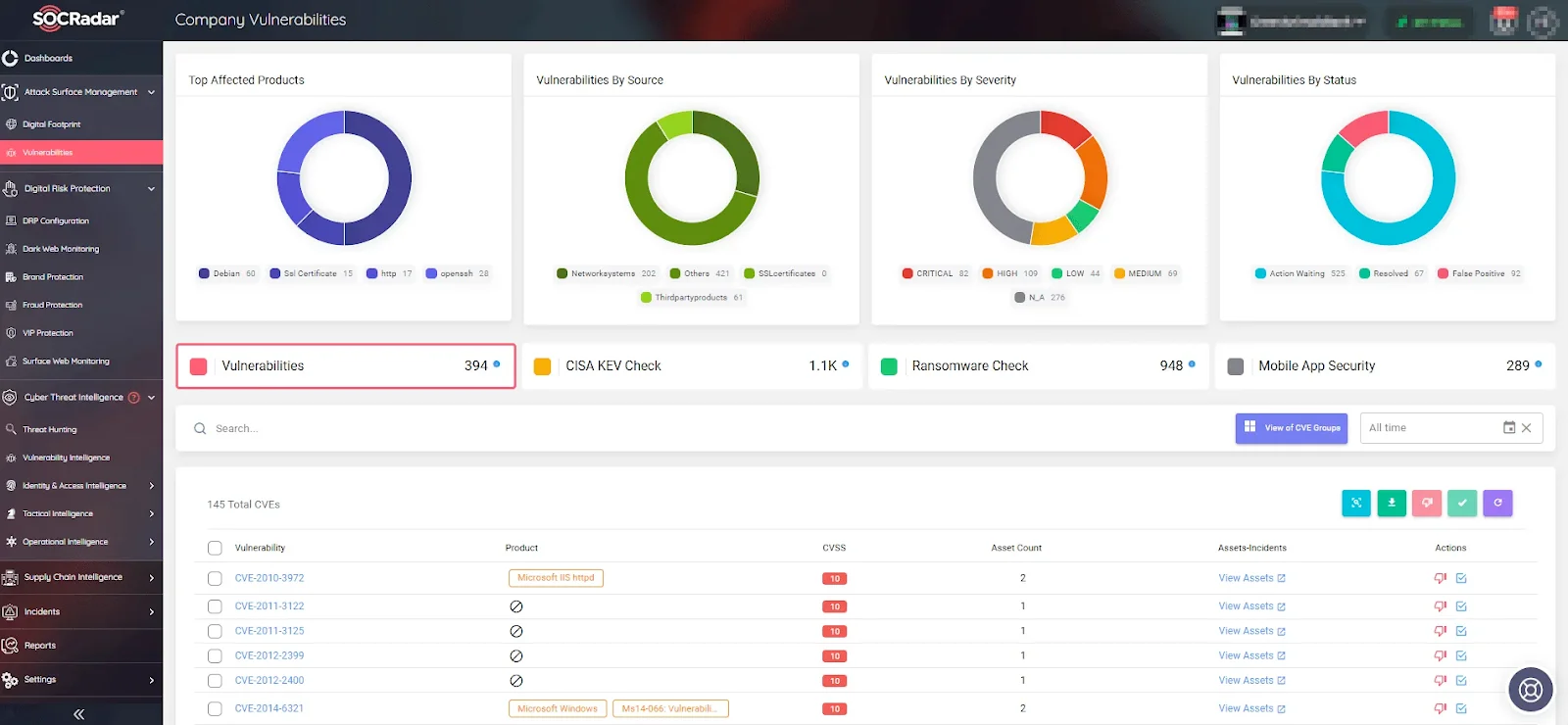
SOCRadar’s ASM module, Company Vulnerabilities page
The Attack Surface Management (ASM) module complements this by providing continuous surveillance of your digital assets. It identifies and highlights security gaps, offering actionable insights through alarms to mitigate risks effectively. The ASM module’s Company Vulnerabilities page is a crucial component of this monitoring.
Together, these tools empower businesses to proactively manage and respond to threats, ensuring robust protection against exploitation threats.



































