
Critical Security Updates for Git SCM: CVE-2024-32002 & CVE-2024-32004 Lead to RCE
[Update] May 17, 2024: “Exploit for the Critical Git Vulnerability (CVE-2024-32002)”
The Git SCM project has recently announced updates to address a series of critical security vulnerabilities. These vulnerabilities, if left unpatched, could pose significant threats, including unauthorized access, data manipulation, and even Remote Code Execution (RCE) attacks, which could severely compromise the security of development environments.
Git CSM is an essential tool for developers worldwide due to its free and open source distributed source code management (SCM) and version control capabilities (git-scm.com)
The latest release highlights particular concerns around two vulnerabilities, CVE-2024-32002 and CVE-2024-32004, due to their potential to enable RCE attacks.
Which Git Versions Are Affected?
The recent security update for Git SCM covers a wide range of versions. The versions affected by the vulnerabilities include:
- v2.45.0
- v2.44.0
- All versions up to and including v2.43.3
- All versions up to and including v2.42.1
- v2.41.0
- All versions up to and including v2.40.1
- All versions up to and including v2.39.3
Users of these versions are strongly encouraged to upgrade to the latest release as soon as possible to mitigate the risks associated with these vulnerabilities.
What is CVE-2024-32002? Critical Git RCE Flaw, Explained
CVE-2024-32002, rated with a CVSS score of 9.1, represents a significant security threat within Git’s functionality, specifically in how submodules are handled during clone operations on Windows and macOS platforms. Its exploitation could lead to Remote Code Execution (RCE), without user awareness or consent.
When cloning a repository that includes submodules, Git should typically restrict file writing to the submodule’s designated worktree. However, CVE-2024-32002 allows for a malicious manipulation where Git is deceived into writing files directly into the .git/ directory instead.
Potential threat actors can craft repositories with submodules that trick Git into executing a hook from the .git/ directory upon cloning. This hook execution occurs before the user has the chance to inspect the actual code being run, leading directly to RCE.
This directory manipulation is achieved through a carefully crafted repository setup, which has a directory and a symbolic link that differs only in case, enabling Git to write one.
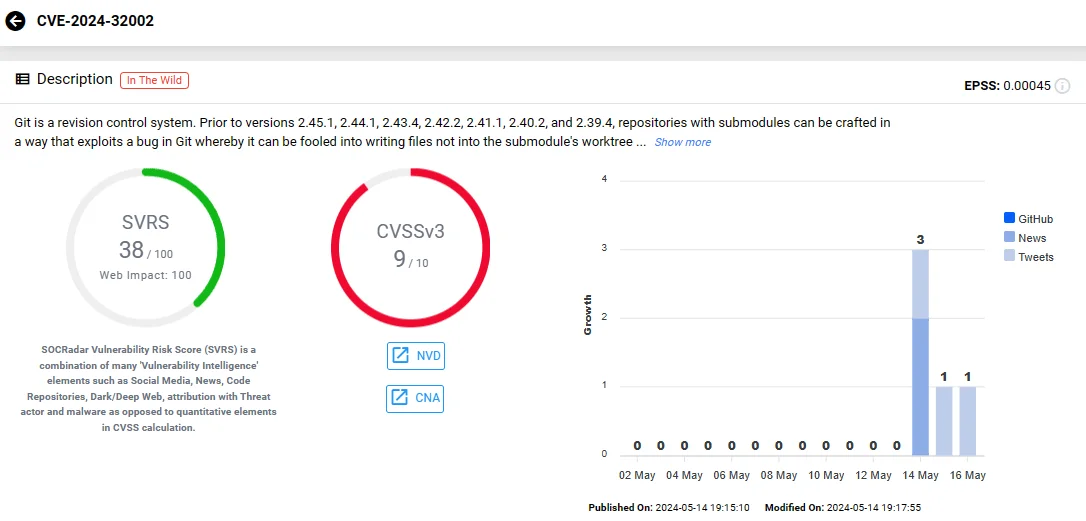
Vulnerability card of CVE-2024-32002 (SOCRadar Vulnerability Intelligence)
The ability to execute arbitrary code on a user’s system through a common operation like cloning a repository represents a substantial security risk. The widespread use of Git in software development also broadens the attack surface.
Take advantage of SOCRadar’s Attack Surface Management (ASM) module to receive alerts on security vulnerabilities affecting your digital assets; SOCRadar’s rapid insights will enable security teams to respond to threats much sooner and more efficiently.
Track company vulnerabilities and take quick actions through the ASM module (SOCRadar)
Exploit for the Critical Git Vulnerability (CVE-2024-32002)
A security expert from Halborn, a blockchain security company, has developed a functional exploit for the critical Git vulnerability, CVE-2024-32002.
The expert notes that the exploit is straightforward, crafted from zero in just 20 minutes.
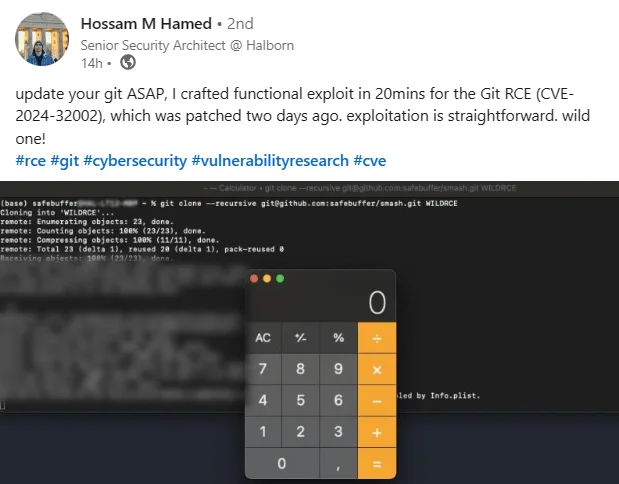
Exploit for the Git vulnerability, CVE-2024-32002 (Source: LinkedIn)
Although the exploit’s specifics are not detailed in the post, the image shows a git clone command with the –recursive option to clone a repository into a directory named “WILDRCE.” The recursive flag ensures that submodules within the repository are also cloned, triggering the exploit.
In this showcase, the ‘Calculator’ application was launched, demonstrating that the vulnerability can be used to execute unauthorized code.
On May 19, security researcher Amal Murali has released the technical details of CVE-2024-32002 along with another Proof-of-Concept (PoC) demonstration.
The researcher’s PoC exploit involved replacing the post-checkout hook with injection code. By examining the patch, Murali found that the exploit is in the subtle interaction between case-insensitive filesystems; by crafting a repository with a specially crafted submodule and a symbolic link, an attacker could exploit the vulnerability, deceiving Git into executing a malicious hook script during the clone process and leading to RCE.
See the full exploit on GitHub.
High-Severity Vulnerabilities in Git SCM: CVE-2024-32004 and CVE-2024-32465
Alongside the critical CVE-2024-32002, Git SCM’s recent patch included other significant vulnerabilities, namely CVE-2024-32004 and CVE-2024-32465.
CVE-2024-32004, with a CVSS score of 8.2, affects Git environments on multi-user machines. This vulnerability allows attackers to craft local repositories that appear as partial clones, missing an object.
When such a repository is cloned, it can trigger arbitrary code execution. What makes CVE-2024-32004 particularly dangerous is that it grants attackers the ability to execute malicious code at the same privilege level as the Git user performing the clone operation.
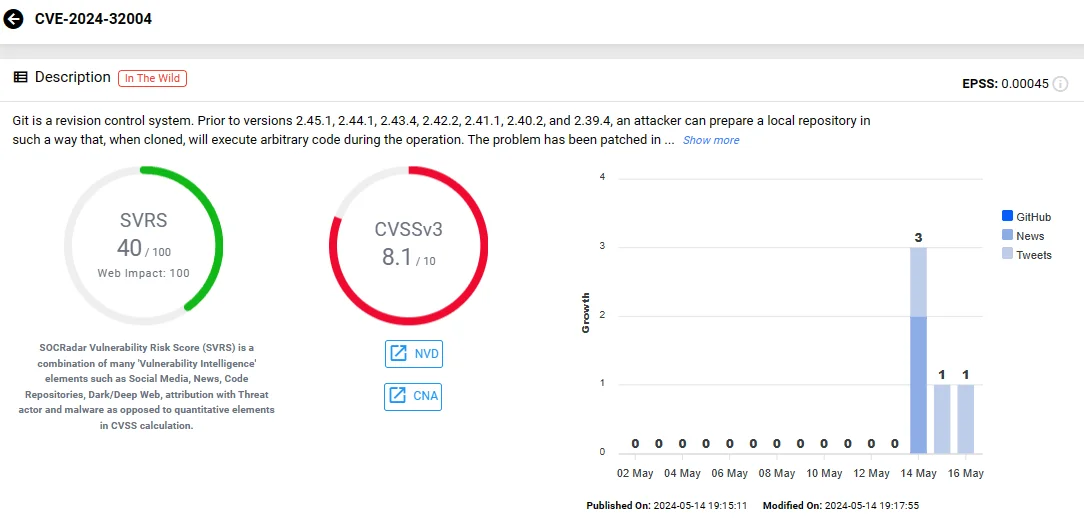
Vulnerability card of CVE-2024-32004 (SOCRadar Vulnerability Intelligence)
The second vulnerability, CVE-2024-32465, scores a 7.4 on the CVSS scale and affects all setups by allowing the bypass of protections meant for cloning untrusted repositories.
According to GitHub’s advisory related to their updates for this Git release, there are scenarios where the patches for CVE-2024-32004 might not suffice. For instance, in the case of CVE-2024-32465, when a .zip file containing a full copy of a Git repository is obtained, it should not automatically be considered safe. Such archives could include configured hooks that are set to run within the repository context, posing risks similar to those found in CVE-2024-32004.
PoC Exploits Available for Lower Severity Flaws, CVE-2024-32021 and CVE-2024-32020
In the latest security updates from Git, two vulnerabilities with lower severity ratings—CVE-2024-32021 and CVE-2024-32020—have also been addressed, each involving specific risks associated with local clones that could lead to unauthorized access and data manipulation.
For both CVE-2024-32021 and CVE-2024-32020, Proof-of-Concept (PoC) exploits have been made available on their GitHub advisories.
CVE-2024-32021 arises when symbolic links (symlinks) in local repositories are improperly handled during cloning. This could result in hard-linking to arbitrary files within the objects/ directory of a Git repository.
Similarly, CVE-2024-32020 concerns local clones on the same disk, where untrusted users might have the opportunity to modify hard-linked files in the cloned repository’s object database.
These vulnerabilities could be exploited to access or manipulate sensitive data within the repository.
To stay up-to-date on the latest advisories and security issues related to Git, visit the Git Security page on GitHub.
Are There Any Workarounds Available?
For users who may face delays in updating their Git installations, the following workarounds have been suggested for specific vulnerabilities:
- CVE-2024-32002: Disabling symbolic link support in Git (git config –global core.symlinks false) can mitigate this vulnerability. However, it’s always advisable to avoid cloning repositories from untrusted sources to minimize risks.
- CVE-2024-32004 and CVE-2024-32465: Users should refrain from cloning repositories from untrusted sources and avoid using Git with repositories obtained via archives from untrusted sources.
Improvements Regarding Recent Vulnerabilities
It is also important to mention that GitHub has implemented a few measures to address vulnerabilities involving submodules and hooks, which are identified by Git SCM to be a pattern in recent security updates. These enhancements include:
- Improved Handling of Symbolic Links and Directories: Prevents files from being written to unintended locations during cloning.
- Secured Hook Execution Process: Ensures unauthorized code cannot run during operations like cloning.
- More Secure Configuration Settings: Protects the Git templates directory from accidental or malicious modifications.
- Warnings for Risky Symbolic Links: Alerts users about symbolic links that could pose security risks.
Which Git Versions Include Fixes?
While there have been no reported exploitations of the newly disclosed vulnerabilities in Git, the potential risks they pose make it important for users to update their installations without delay.
The Git SCM project has promptly released patched versions to address these vulnerabilities and ensure the security of its users. Here are the available patched versions:
- v2.45.1
- v2.44.1
- v2.43.4
- v2.42.2
- v2.41.1
- v2.40.2
- v2.39.4
Git users are encouraged to regularly check for updates and apply patches as soon as they become available. For the latest updates, visit the official Git SCM website’s Downloads section.
Staying current with patches is essential, but it is only part of a complete vulnerability management strategy. Use SOCRadar’s Vulnerability Intelligence to easily manage vulnerabilities and better prioritize patches.
Vulnerability Intelligence features updates on known vulnerabilities, exploits, repositories, and emerging hacker trends. Such insights can assist organizations in improving vulnerability management and protecting against potential cyberattacks.
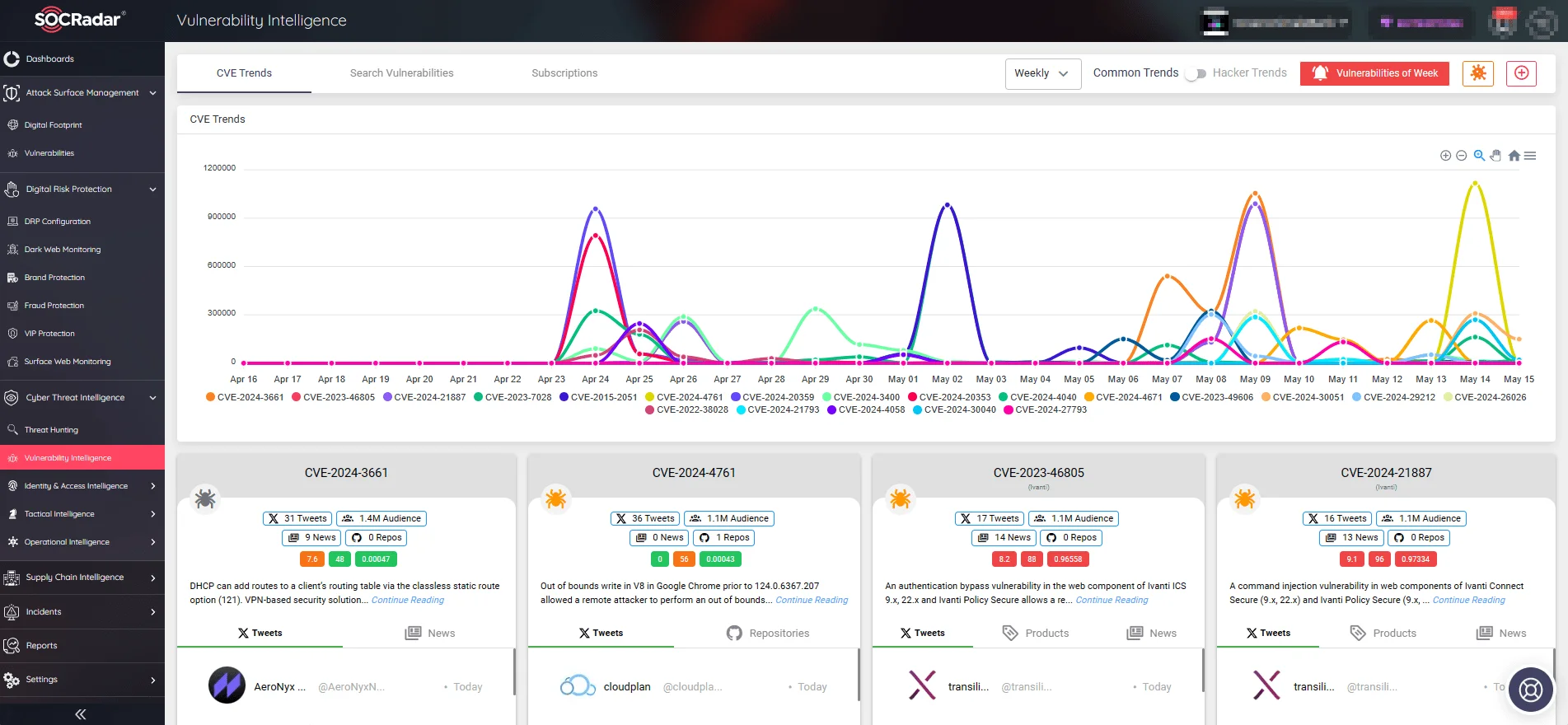
SOCRadar’s Vulnerability Intelligence: CVE trends, exploitation activities, and more
Apply for Freemium to test out SOCRadar’s vulnerability management capabilities, among other CTI features.




































