
Critical Veritas NetBackup & JFrog Artifactory Vulnerabilities (CVE-2024-28222, CVE-2023-42662); CISA Alert for Cisco Flaws
New critical vulnerabilities have surfaced in Veritas NetBackup and JFrog Artifactory, solutions that are widely utilized in global operations regarding data backup, and software supply chain. These vulnerabilities require immediate attention to mitigate potential risks and safeguard organizational assets against exploitation.
Furthermore, in a recent alert, the Cybersecurity and Infrastructure Security Agency (CISA) underscored the latest Cisco security updates, addressing two high-severity vulnerabilities.
Critical RCE in Veritas NetBackup (CVE-2024-28222): Patch Now
The most critical vulnerability in this blog is a Remote Code Execution (RCE), affecting Veritas NetBackup servers and clients.
Widely used in enterprises, Veritas NetBackup faces CVE-2024-28222, rated 9.8 on the CVSS scale. This vulnerability resides in the NetBackup BPCD process, which fails to validate file paths adequately, enabling unauthenticated attackers to upload and execute custom files.
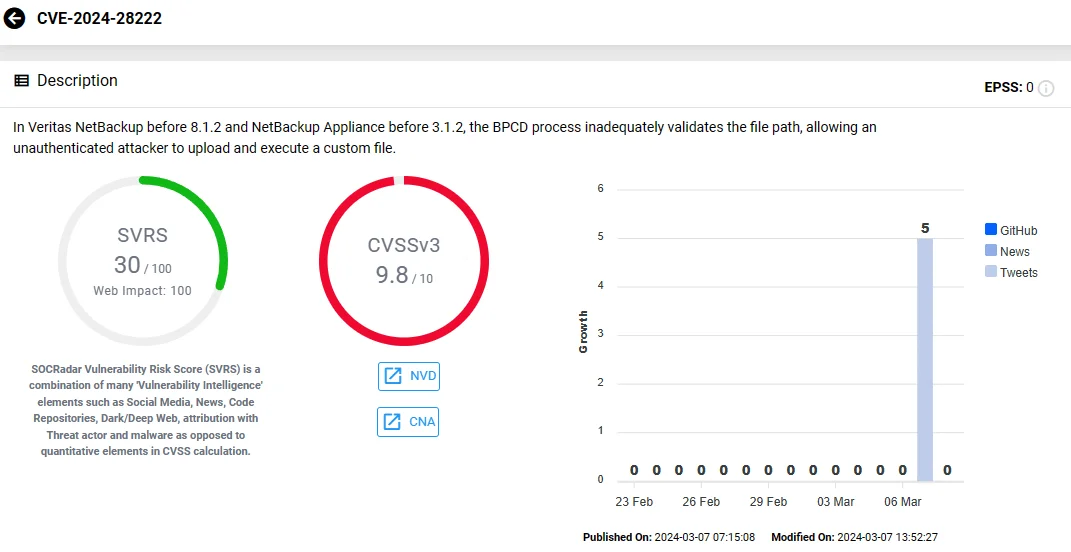
Vulnerability card of CVE-2024-28222 (Veritas NetBackup) on the SOCRadar platform.
This vulnerability allows remote, unauthenticated attackers to deploy malware, disrupt backup recovery, steal data, and potentially infiltrate networks.
Affected Versions of Veritas NetBackup
According to Veritas’ advisory, the affected products and versions encompass NetBackup primary server, media server, and clients predating 8.1.2, as well as NetBackup Appliance predating 3.1.2.
How Can You Safeguard Against Exploitation?
It is recommended to upgrade NetBackup to version 8.3.0.2 or later. If you are currently running version 8.1.2 or higher, no action is required.
For NetBackup Appliance, if on a version prior to 3.1.2, upgrade to version 3.3.0.2 MR2 or later to mitigate the risk of exploitation.
Visit Veritas’ official advisory for CVE-2024-28222 for additional details.
SOCRadar’s Attack Surface Management (ASM) module, with its extensive monitoring capabilities, can proactively identify vulnerabilities in your company’s digital assets. The SOCRadar platform delivers instant insights into vulnerabilities that affect your assets, allowing you to take swift action and enhance patching strategies.
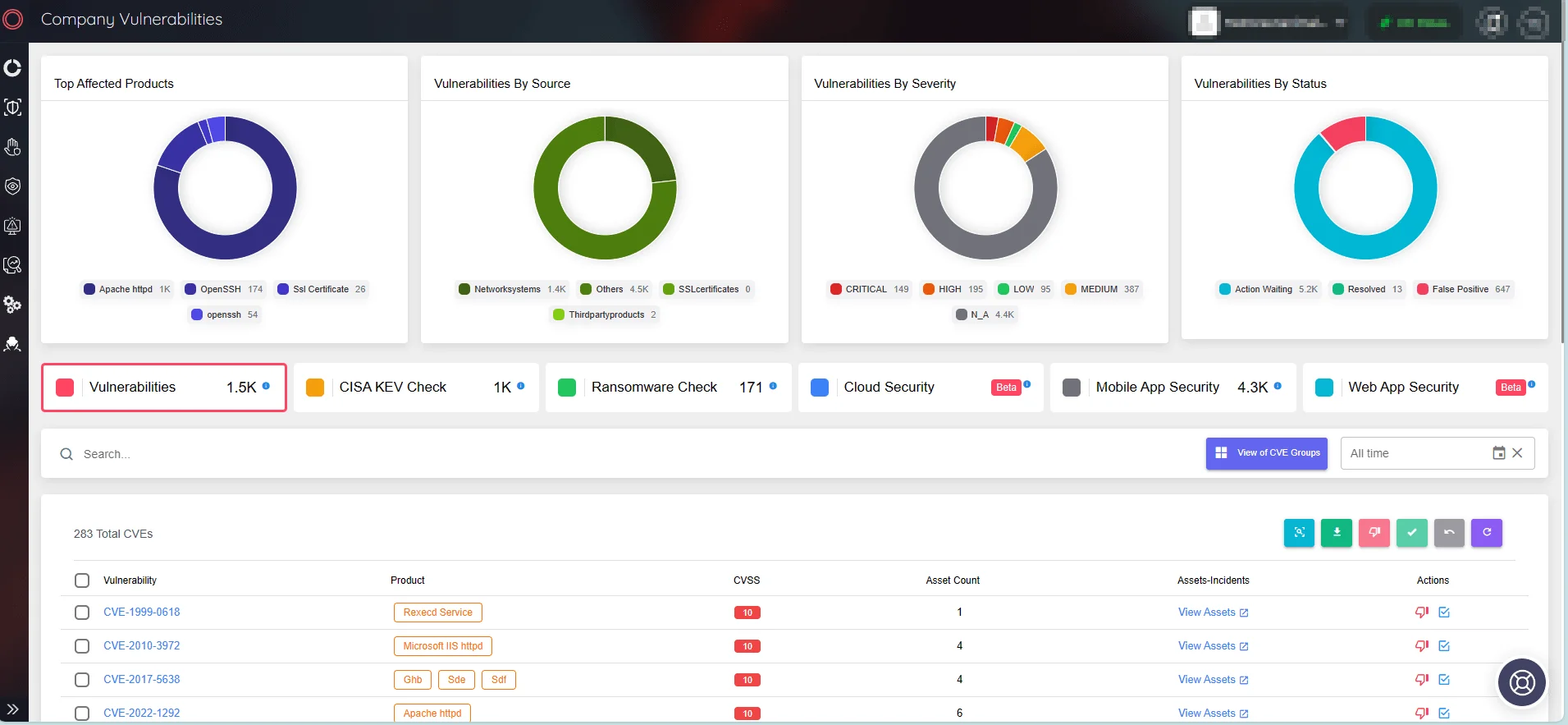
Monitor company vulnerabilities with SOCRadar’s ASM module.
Vulnerability in JFrog Artifactory Could Expose User Access Tokens: CVE-2023-42662
JFrog Artifactory, a solution for managing software components across the supply chain, faces several significant vulnerabilities. The most severe one of these, CVE-2023-42662 (CVSS: 9.3, Critical), exposes user access tokens via manipulated URLs, stemming from improper handling of CLI/IDE browser-based Single Sign-On (SSO) integration.
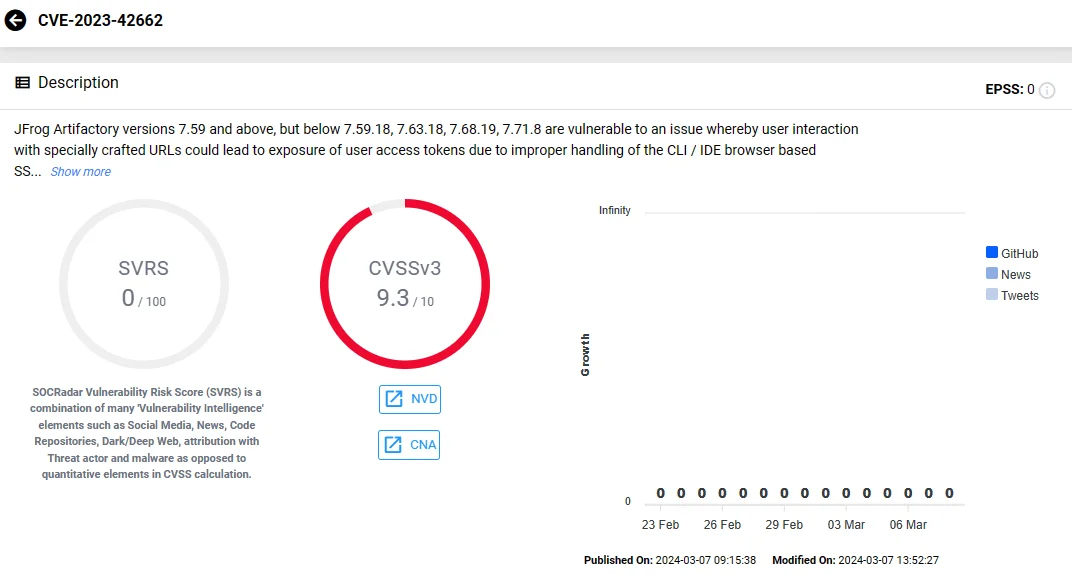
Vulnerability card of CVE-2023-42662 (JFrog Artifactory) on the SOCRadar platform.
Additional issues with high severity include CVE-2023-42661 (CVSS: 7.2) and CVE-2023-42509 (CVSS: 6.6), potentially leading to arbitrary file write and secret leakage, respectively.
JFrog has released fixes; prompt updating is advised to avoid exploitation of the vulnerabilities.
If updating is not feasible soon, consider blocking access to the CLI token exchange API endpoint, as it is a recommended workaround for the critical CVE-2023-42662 vulnerability.
See the JFrog security advisories for detailed guidance on remediation.
CISA Alert Highlights Vulnerabilities in Cisco Secure Client (CVE-2024-20337, CVE-2024-20338)
In a recent alert, CISA highlighted Cisco’s release of security updates for vulnerabilities in Cisco Secure Client and Secure Client for Linux: CVE-2024-20337 and CVE-2024-20338.
These high-severity vulnerabilities allow remote attackers to inject code and elevate privileges to root, posing significant risks.
The first vulnerability, CVE-2024-20337, possesses a CVSS score of 8.2. It affects Cisco Secure Client for Linux, macOS, and Windows, and enables a remote, unauthenticated attacker to execute a Carriage Return Line Feed (CRLF) injection attack during the SAML authentication process.
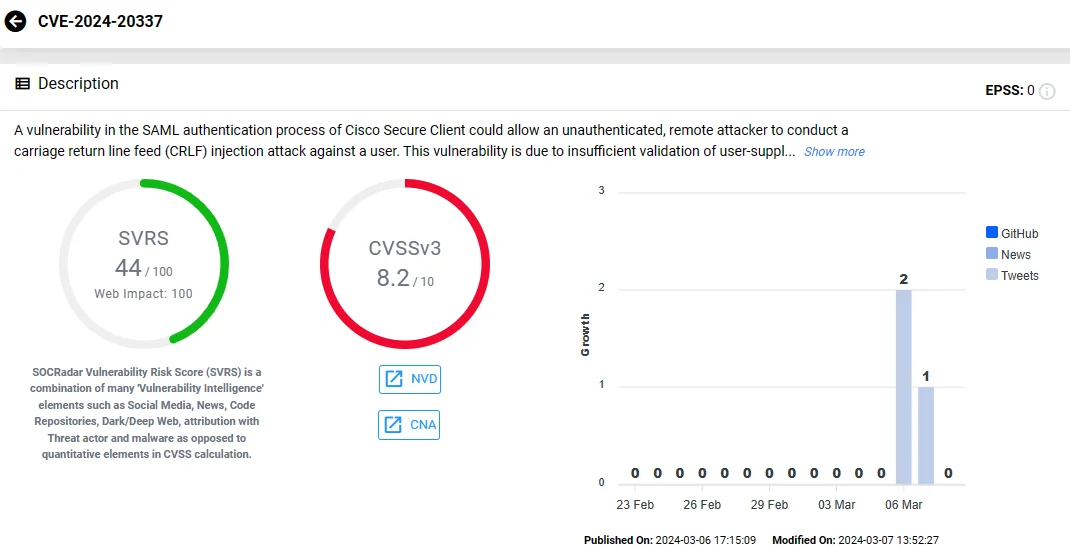
Vulnerability card of CVE-2024-20337 (Cisco Secure Client) on the SOCRadar platform.
Insufficient validation of user input permits attackers to exploit the vulnerability by tricking users into clicking malicious links while initiating a VPN session.
Successful exploitation of CVE-2024-20337 could grant attackers arbitrary script code execution or access to sensitive browser-based data, including valid SAML tokens. With the token, attackers can establish remote access VPN sessions as the affected user, albeit requiring additional credentials for accessing individual hosts and services.
Cisco advises checking VPN headend configurations using the “show running-config tunnel-group” command in Cisco ASA or FTD Software CLI to mitigate potential exploits.
Cisco has provided an example in its advisory to illustrate how the output of the command would appear for a device with the SAML External Browser feature enabled:
ciscoasa# show running-config tunnel-group
tunnel-group EXAMPLE_GROUP type remote-access
tunnel-group EXAMPLE_GROUP webvpn-attributes
authentication saml
saml external-browser
saml identity-provider EXAMPLEThe second vulnerability, CVE-2024-20338, has a CVSS score of 7.3 and affects the ISE Posture (System Scan) module of Cisco Secure Client for Linux. It permits an authenticated, local attacker to escalate privileges on an affected device.
Exploiting this vulnerability involves placing a malicious library file in a specific directory and convincing an administrator to restart a particular process. This grants the attacker root privileges on the affected device.
CISA advises users and administrators to swiftly apply updates to prevent potential exploitation of these vulnerabilities.
Master Vulnerability Intelligence With Continuous Monitoring and AI Insights
SOCRadar’s Vulnerability Intelligence simplifies tracking vulnerability trends and accessing comprehensive information about identified vulnerabilities, including news material mentioning them, their lifecycle, available exploits, IoCs, and related repositories.
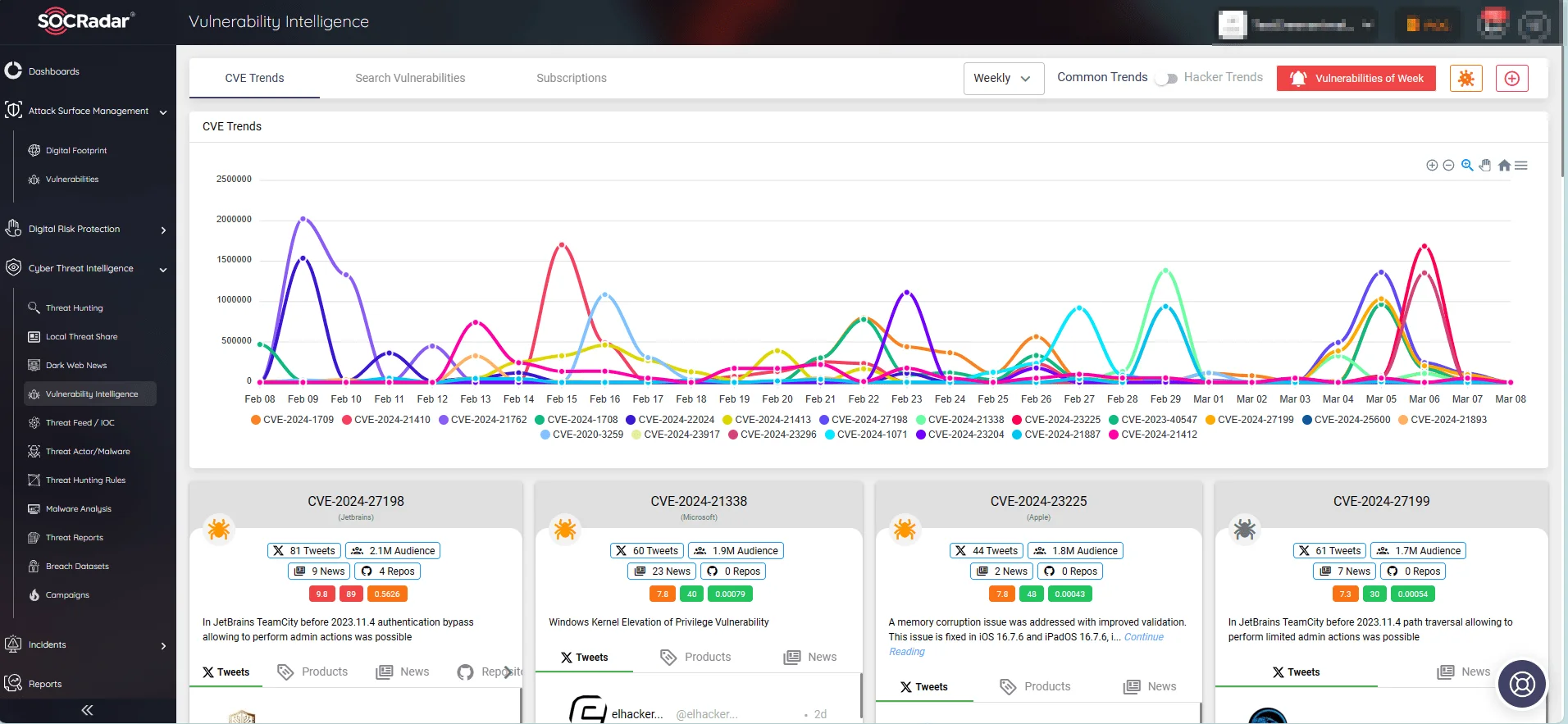
Follow common trends/hacker trends for vulnerabilities and see the emerging threats.
The Vulnerability Intelligence module also enriches the user experience by offering AI insights on each vulnerability. You can receive concise reports with the AI insights feature, containing key facts and mitigation strategies, enabling a deeper understanding of the vulnerability’s significance in the cyber landscape.
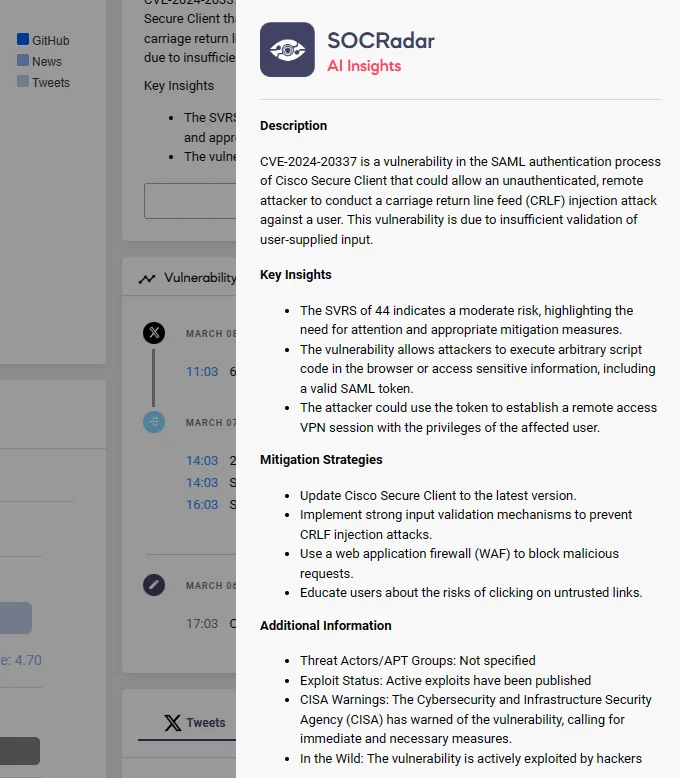
The AI insights feature of SOCRadar Vulnerability Intelligence.
You can try out the features of the SOCRadar XTI platform with Free Edition:




































