
Critical Vulnerability in Zyxel Firewall and VPN Products Exploited
Threat actors exploit the critical vulnerability affecting Zyxel’s firewall and VPN devices. The vulnerability allows attackers to inject arbitrary commands without authentication remotely. Zyxel has recently released patches for it.
The vulnerability, code CVE-2022-30525, is “critical” with a CVSS score of 9.8. It allows threat actors to gain full access to corporate networks and devices. In an article published on Rapid7, researchers also shared a technical analysis of the details of the exploit.
Threat actors are closely watching vulnerability trends and your public-facing services and technologies to find a backdoor. Use SOCRadar for vulnerability intelligence and see which vulnerabilities are leveraged by threat actors.
Allows to Create “Reverse Shell”
According to cybersecurity researchers, attackers who exploit the vulnerability can execute commands as “nobody user.” The vulnerability is exploited via the /ztp/cgi-bin/handler URI and by passing commands to os.system in lib_wan_settings.py.
With this method, cyber attackers can create a reverse shell using normal bash GTFOBin.
Which Zyxel Products Does the Vulnerability Affect?
Zyxel shared the affected products and patches with its users in its security advisory:
|
Affected model |
Affected firmware version |
Patch |
|
USG FLEX 100(W), 200, 500, 700 |
ZLD V5.00 through ZLD V5.21 Patch 1 |
ZLD V5.30 |
|
USG FLEX 50(W) / USG20(W)-VPN |
ZLD V5.10 through ZLD V5.21 Patch 1 |
ZLD V5.30 |
|
ATP series |
ZLD V5.10 through ZLD V5.21 Patch 1 |
ZLD V5.30 |
|
VPN series |
ZLD V4.60 through ZLD V5.21 Patch 1 |
ZLD V5.30 |
Rapid7 researchers announced that they detected close to 17,000 devices connected to the internet in their scan through Shodan for vulnerable Zyxel products.
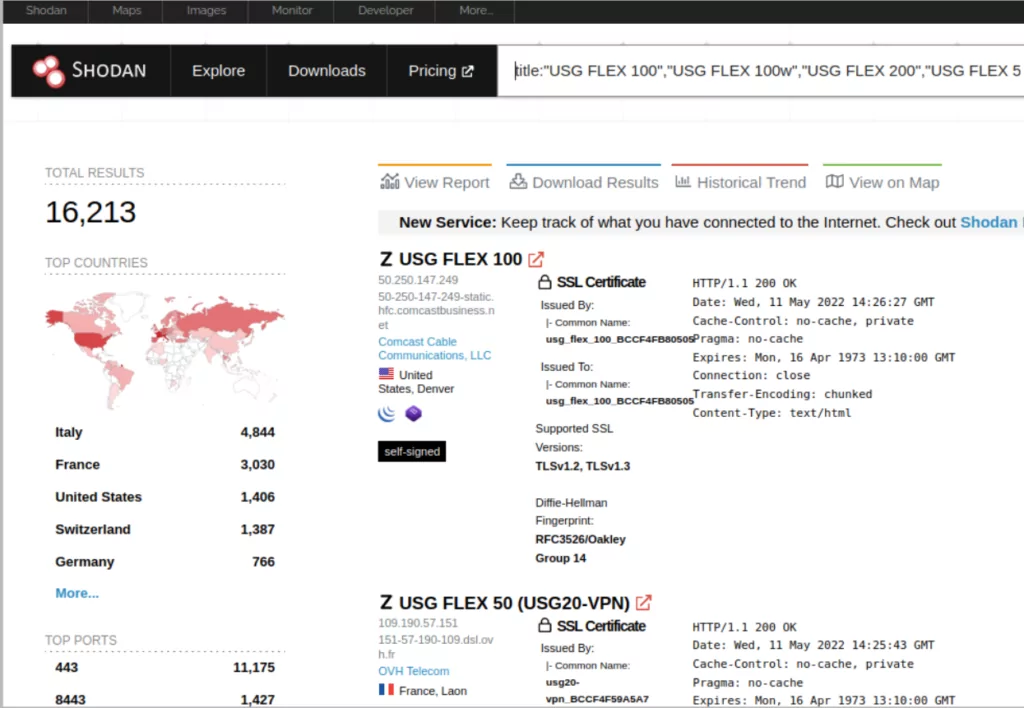
Cybersecurity experts point out the damage that the vulnerability can cause and that it is actively exploited and state that it is of great importance to update software versions.
SonicWall Releases Patches for Vulnerabilities Affecting SSLVPN SMA1000 Devices
SonicWall announced that it had released patches for three vulnerabilities, including the critical “unauthenticated access control bypass” vulnerability. Its security advisory stated that the vulnerabilities affect firmware versions 12.4.0 and 12.4.1 running SMA 6200, 6210, 7200, 7210, and 8000v.
Here is the complete list of vulnerabilities:
- CVE-2022-22282 (CVSS 8.2): Unauthenticated Access Control Bypass Vulnerability
- CVE-2022-1702 (CVSS 6.1): Open Redirection Vulnerability
- CVE-2022-1701 (CVSS 5.7): Use of Hard-coded Cryptographic Key Vulnerability
The vulnerabilities do not affect SMA 1000 series, SMA 100 series, CMS, and remote access users running versions before 12.4.0.
Discover SOCRadar® Free Edition
With SOCRadar® Free Edition, you’ll be able to:
- Discover your unknown hacker-exposed assets
- Check if your IP addresses tagged as malicious
- Monitor your domain name on hacked websites and phishing databases
- Get notified when a critical zero-day vulnerability is disclosed
Free for 12 months for 1 corporate domain and 100 auto-discovered digital assets.
Get free access.


































