Cybercriminals Seek to Turn Humanitarian Crisis Into Opportunity
On Monday, February 6, 2023, Turkey and Syria woke up to the morning of a major natural disaster. Two devastating earthquakes, 7.7 and 7.6 magnitudes, struck southeastern Turkey and Syria, with millions of people in dozens of different cities affected, and the death toll exceeded thousands. The Turkish government declared a Level 4 alert, the highest level, and requested international assistance for the disaster area. While national and international emergency teams fight against time in disaster areas with all their means, aid and support continue to be collected through many platforms and organizations, especially on the internet and social media.
Unfortunately, even in the face of disaster, it has been determined that threat actors who want to abuse people’s goodwill covet the aid provided for the disaster area.
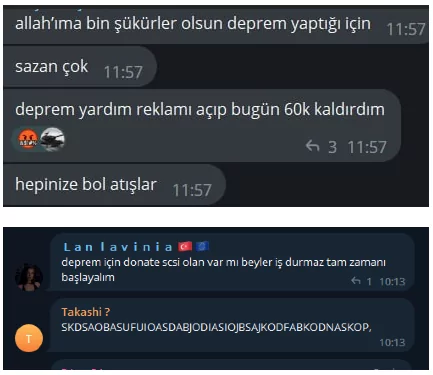
Telegram messages: Thank God for the earthquake – too many s*ckers – I opened an earthquake relief ad (scam) and raised 60k today – good luck to you all.
Telegram messages 2: Does anyone have a donate script for the earthquake? Guys, let’s get started. It’s high time work doesn’t stop.
Threat actors who abuse people’s goodwill and willingness to help steal donation money, preventing donations from reaching those in genuine need and causing people’s trust to be shaken and their desire to help to disappear.
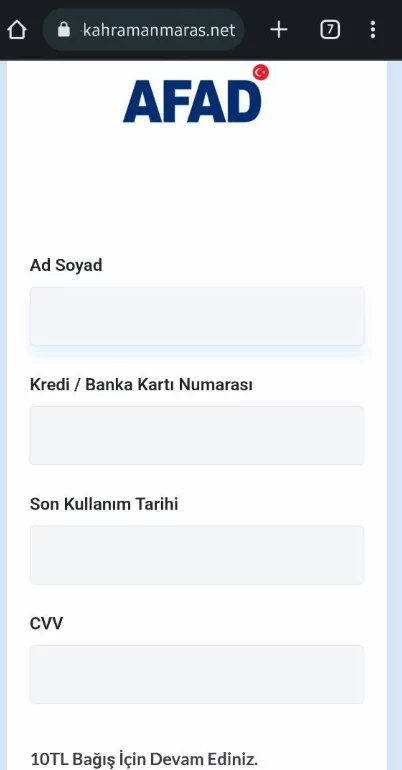

The scammers are not only operating from within Turkey and Syria but are also coveting the money of the international community. A fake charity organization Bitdefender spotted was one of the first phishing attacks discovered.
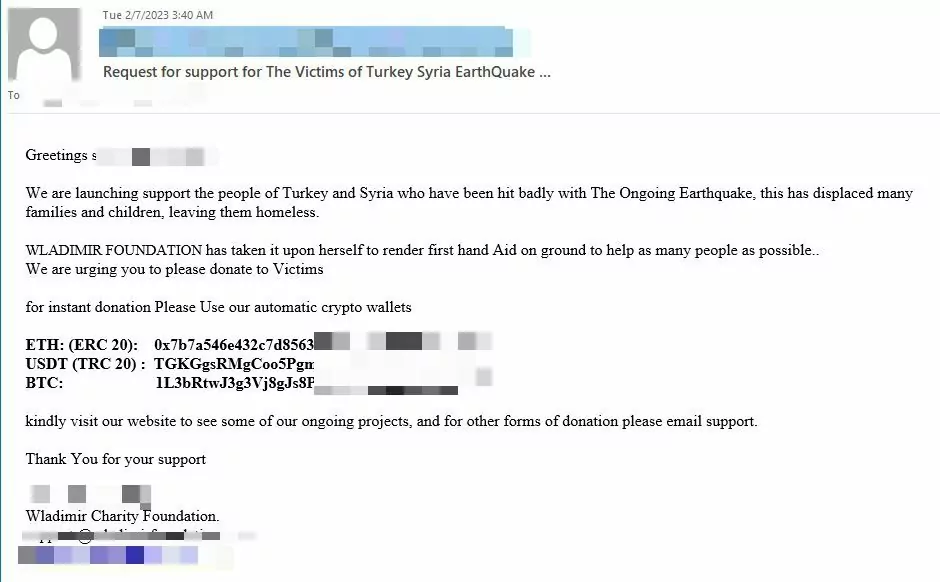
According to the researchers’ analysis, South Korea comes first with 49%, Vietnam with 19%, and the US and India with 7% each among the countries targeted by this email. Fraudsters also try to steal money with crypto wallets by impersonating humanitarian aid organizations such as UNICEF.
How to Detect Impersonating Sites?
First of all, it is important not to rely on any sources other than official news outlets in order to access the right information sources and donation channels, but even experienced internet users can fall into this trap as threat actors use phishing attack techniques by impersonating official sources. In particular, fake websites that try to rank high in searches using Google ads can cause great harm. Here’s what to do to recognize such fake websites:
- If you want to access a charity through Google searches, you should be careful when clicking on sites with Paid sponsored ads or Ads at the top because a popular phishing technique recently is to use Google’s ad feature to rank fake websites.
- Attention should be paid to site extensions, official institutions use the gov extension and this extension cannot be used by other organizations. For Türkiye, this extension is gov.tr while for Syria it is gov.sy.
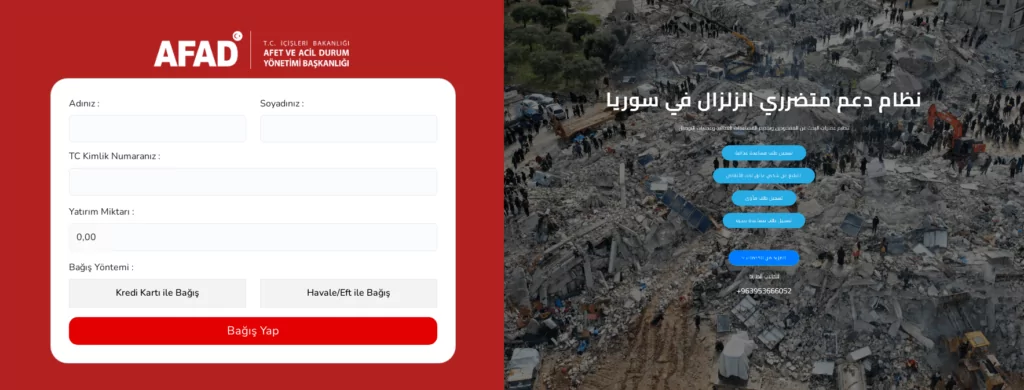
- Donation methods that directly ask for your credit card details or other personal information instead of giving a wire transfer number may also be an indicator. It is very important not to provide such information to a source that you are not absolutely sure of its accuracy.
- Phishing websites contain typosquatting in URL addresses or social media accounts in usernames. Threat actors cannot do the exact same most of the time because the real name is already in use. So they try to mislead the careless eyes with similar names and addresses. Another reason could be to trick people who mistype the URL address, which could be an example of an extra letter for misspellings.
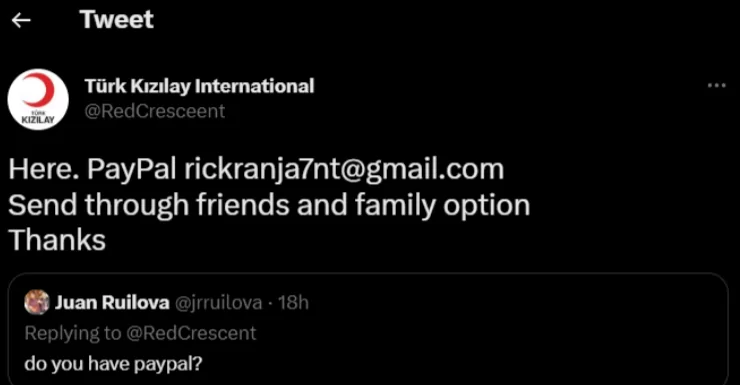
- Scam sites can often be designed quickly and lack many functional features. As an indicator of these kinds of phishing sites, buttons on the website may not lead anywhere, and contact information pages may be missing or inaccurate.
Report Suspicious Domains and Accounts

Threat actors continue to abuse people’s goodwill with no moral boundaries. Cybercriminals, aiming to profit by impersonating donation charities in the Ukraine-Russia war that started recently, are trying to turn a humanitarian crisis into an opportunity once again.
SOCRadar has been monitoring threat actors carrying out fraud and phishing attacks targeting official aid organizations by impersonating them and all activities that may lead to disinformation since the disaster that deeply affected Turkey and Syria, and has taken the necessary actions to prevent abuse. We created a GitHub page to track the detected fraud domains and IP addresses.
If you share the fraud attempts you have detected with us via [email protected] email address, we will take necessary actions immediately.


































