Dark Bounty – From Out of Scope to Out of Interest
The digital realm thrives on the continuous push and pull between cybersecurity experts and malicious actors. Within this dynamic ecosystem, bug bounty programs have emerged as a critical line of defense, offering a platform where individuals—commonly referred to as bug bounty hunters—can report vulnerabilities in software and systems in exchange for rewards. These programs, sponsored by organizations ranging from tech giants to startups, aim to identify and fix security flaws before hackers can exploit them.
So, at their core, bug bounty programs are a call to arms for cybersecurity enthusiasts and professionals to legally hack into systems to find security weaknesses. Unlike malicious hacking, these efforts are sanctioned by the organizations to strengthen security measures. Rewards for these findings are primarily monetary but often include recognition, swag, and sometimes even employment opportunities.
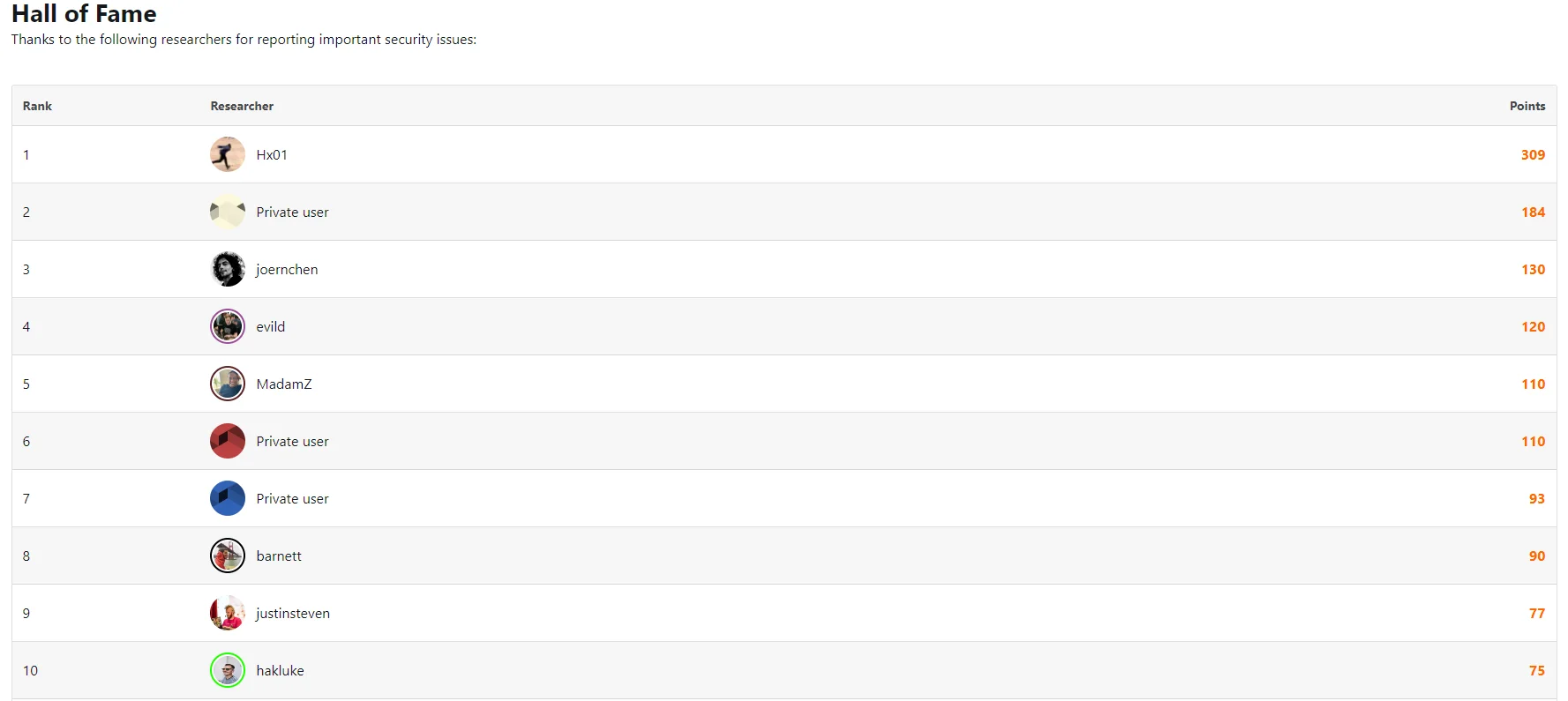
Bugcrowd’s Hall of Fame page
Becoming a successful bug bounty hunter requires a mix of technical skills, persistence, and a bit of luck. Hunters may spend countless hours sifting through code, running tests, and researching vulnerabilities, often in their own time and without any guarantee of payment. The work is highly competitive; only unique and previously unreported bugs qualify for rewards, and the payout can vary widely depending on the severity of the vulnerability and the policies of the sponsoring organization. This is where things get nasty.
The Forbidden Fruit
Despite its many challenges, the allure of bug bounty hunting is undeniable. For some, it’s the thrill of the hunt—the intellectual challenge of cracking a system that draws them. But for many others, it’s the potential for significant financial gain. High-profile programs can offer rewards in the tens or even hundreds of thousands of dollars for critical vulnerabilities. Moreover, the recognition that comes from finding a significant bug in a widely used software can catapult a hunter’s reputation within the cybersecurity community.
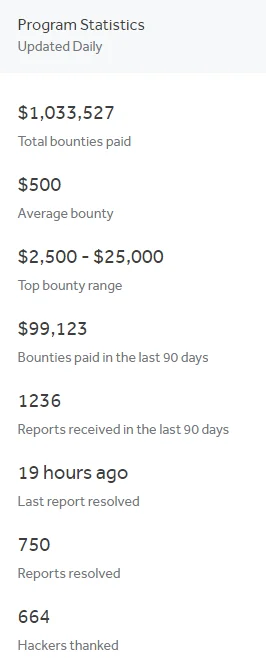
Hackerone’s Bug Bounty Program Statistics
The journey from being a defender of cyberspace to navigating its shadowy underbelly is a tale of disillusionment and temptation. As bug bounty hunters delve deeper into the world of cybersecurity, they encounter a landscape marked not only by triumphs but also by significant challenges. The allure of the Dark Web and hacker forums presents a seductive alternative to the often thankless and rigorous path of ethical hacking. This transition from white-hat to black-hat activities marks a critical pivot in the cybersecurity narrative.
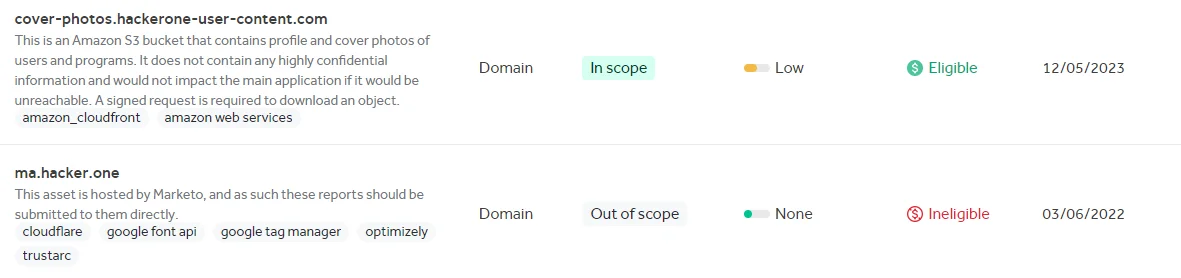
Policy Scopes on Hackerone
Scopes are notified by the organization running the bug bounty program, and the activities to be carried out must be within these limits. Domains or vulnerabilities within the scope but of low severity may be eligible for payment, but the amount could be low.
Several factors contribute to the disillusionment faced by bug bounty hunters. The primary issue stems from the economic realities of bug hunting. Despite investing substantial time and effort, many hunters find that the financial rewards do not always reflect the value of their contributions. The competitive nature of these programs means that not every discovery leads to a payout, and when they do, the compensation can sometimes be disappointingly low, especially for vulnerabilities deemed less critical or out of scope.
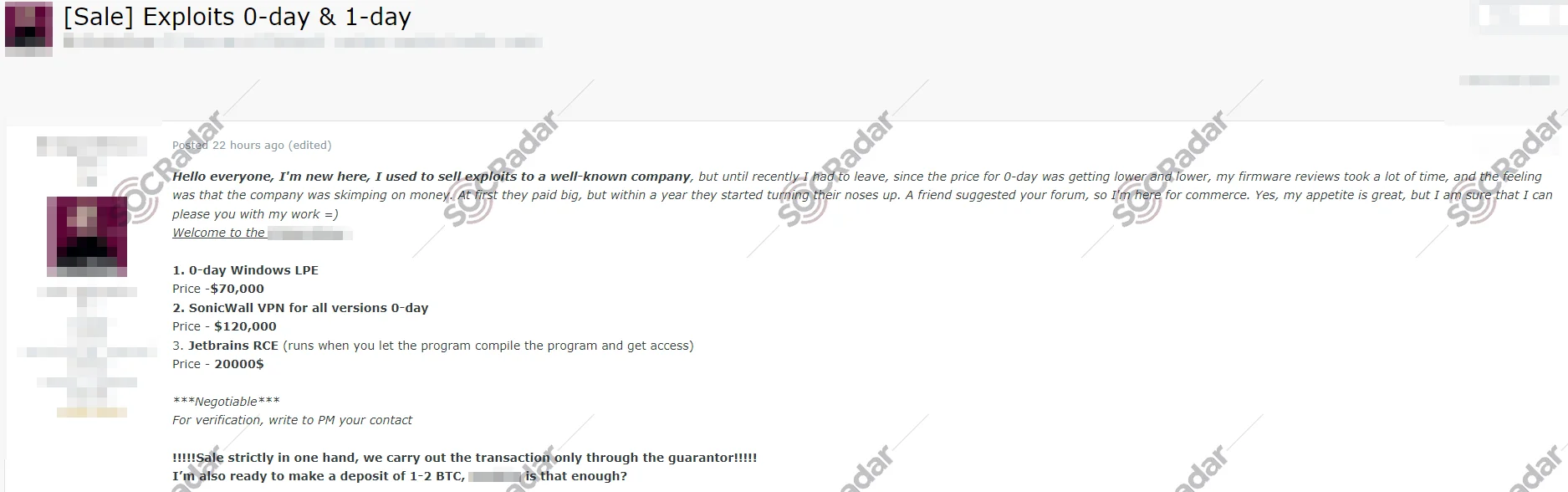
A vulnerability sale on a hacker forum, bounty hunter turns to the dark side for more money.
Moreover, the restrictions placed on the scope of permissible hacking can lead to frustration. Discovering a potentially devastating vulnerability, only to learn it falls outside the program’s scope, can be a bitter pill to swallow. Such discoveries are often unrewarded, leaving hunters feeling undervalued and questioning the efficacy of their ethical stance.
The Lure of the Dark Web
Against this backdrop of frustration and economic uncertainty, the Dark Web offers an alternative marketplace for cyber skills. Hacker forums and illicit marketplaces operate outside the bounds of legality, offering anonymity and financial incentives for those willing to sell their discoveries to the highest bidder. The Dark Web does not concern itself with the ethical implications of such transactions; instead, it provides a platform where the value of a vulnerability is directly related to its potential impact, regardless of ethical considerations.
The transition to black-hat activities is not a decision taken lightly. It involves a fundamental shift in perspective, from viewing vulnerabilities as problems to be solved for the greater good, to seeing them as opportunities for personal gain. This shift is often justified by the disillusionment with the traditional bug bounty system, where hunters may feel their skills are undervalued and their potential stifled by arbitrary limitations.
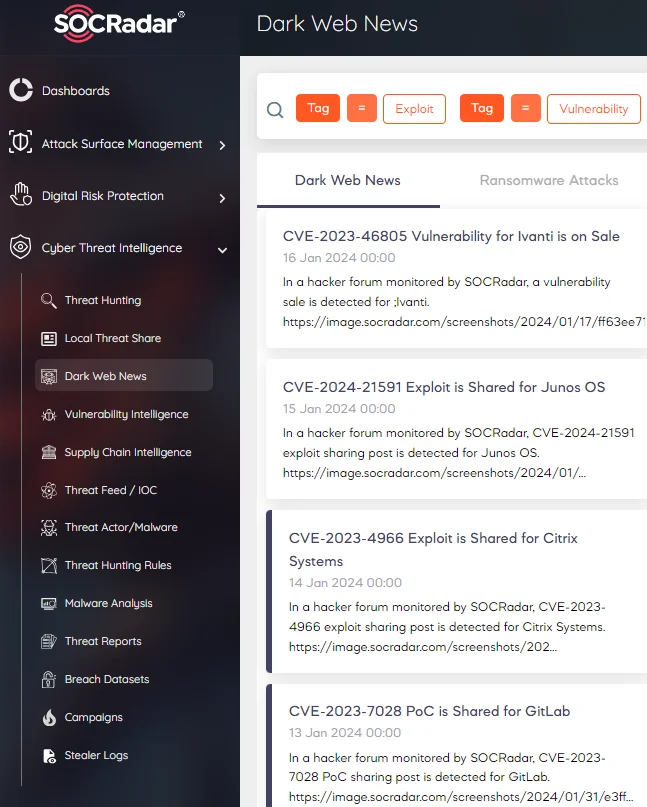
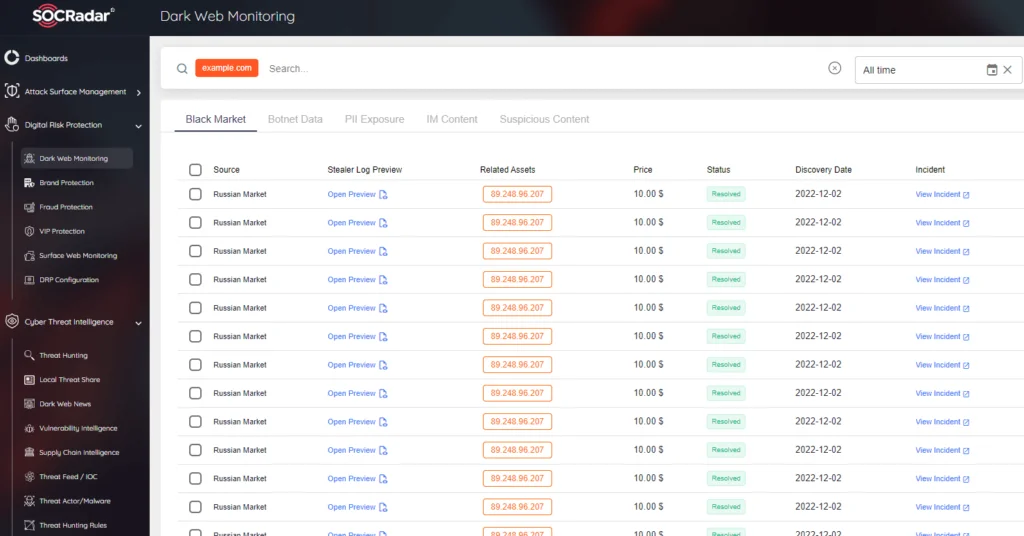
On SOCRadar Platform Dark Web News tab many exploit sales are monitored every day.
On the Dark Web, the economics of zero-day exploits—vulnerabilities unknown to the software vendor and thus more valuable for their potential to be exploited in malicious ways—are vastly different. Here, the price of an exploit is determined by its rarity, the potential for damage, and the demand in the underground market. This can lead to significant financial rewards for those willing to cross the ethical line, offering a tempting proposition for disillusioned bug bounty hunters.
Threat Landscape
The turn to the dark side is fraught with ethical dilemmas. It represents a departure from the principles of cybersecurity, where the goal is to protect and defend. Selling vulnerabilities on the Dark Web not only compromises the security of countless systems and users but also undermines the trust and collaborative spirit of the bug bounty community. The decision to engage in black-hat activities is a personal and moral crossroads, marking a definitive shift in a hunter’s career trajectory.
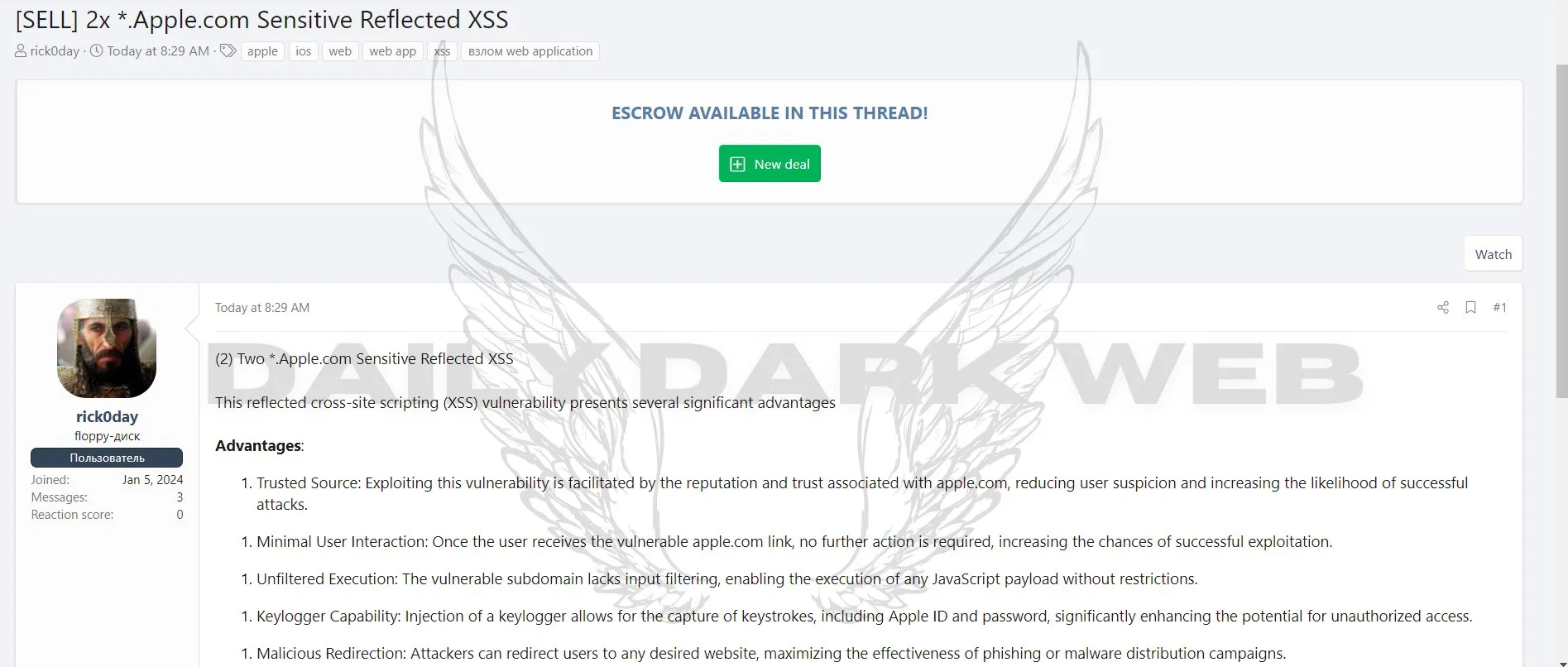
Another threat actor is selling XSS vulnerabilities of Apple’s website, despite Apple’s bug bounty program.
Disillusionment with the bug bounty system, combined with the lure of financial gain on the Dark Web, can lead some down a path from which return is difficult. This journey into the darker aspects of cybersecurity reflects the broader challenges facing the industry, where the line between defender and adversary can sometimes blur, driven by the very human quest for recognition and reward.

Some threat actors may also distribute such exploits for free in hacker forums to gain popularity.
As in the figures, threat actors easily access infrastructures like payment methods and marketplaces to sell vulnerabilities. While ethical bug bounty programs aim to deter them from venturing into these darker avenues, determining the boundary between right and wrong remains challenging. The situation is further complicated by the potential for blackmail, constantly expanding “ethical” hacker numbers, and the continuously expanding digital realm and attack surfaces…
Solutions and Preventive Measures
Fostering Ethical Hacking
Central to mitigating these risks is the promotion of ethical hacking. By enhancing the appeal and viability of bug bounty programs, organizations can encourage hackers to report vulnerabilities directly to them, rather than turning to the Dark Web. This includes offering fair and competitive rewards, expanding the scope of programs to cover more potential vulnerabilities, and ensuring prompt and transparent communication with contributors. Recognition and career development opportunities also play a crucial role in retaining talent within the ethical hacking ecosystem.
However, a critical point in this context is that in addition to the promotion of ethical hacking, it is critical to adjust and meet the expectations of people entering this landscape. In the opposite case, individuals who are talented and knowledgeable but cannot find platforms to direct these abilities can potentially expand the threat landscape greatly.
Strengthening Legal Frameworks
On the legislative front, stronger laws and regulations are needed to deter the sale and purchase of exploits on the Dark Web. This includes international cooperation to track and prosecute individuals involved in these markets, as cybercrime often transcends national boundaries. Additionally, legal protections for ethical hackers, such as safe harbor provisions, can encourage more individuals to report vulnerabilities without fear of prosecution.
Enhancing Cybersecurity Education
Educating the next generation of cybersecurity professionals about the ethical, technical, and legal aspects of hacking is paramount. This includes not only formal education but also community initiatives, workshops, and online resources that promote responsible hacking practices. Awareness campaigns that highlight the consequences of illicit activities and the value of ethical hacking can also shift perceptions and encourage positive engagement with cybersecurity.
Collaboration and Community Engagement
Finally, fostering a collaborative cybersecurity community that includes businesses, ethical hackers, law enforcement, and policymakers can address the systemic issues that lead individuals to the Dark Web. By sharing knowledge, resources, and best practices, this community can build a more robust defense against cyber threats and create a supportive environment for those who wish to contribute positively.
Conclusion
The shift from ethical hacking to selling vulnerabilities on the Dark Web poses a significant challenge to cybersecurity, threatening not just individual organizations but the very fabric of digital society. Addressing this issue requires a concerted effort from all stakeholders in the cybersecurity ecosystem. By promoting ethical hacking, strengthening legal frameworks, enhancing education, and fostering collaboration, it is possible to mitigate the impact of these activities and secure a safer digital future for all.
It is important to embrace after solutions as well as preventions, and you can get Dark Web solutions within the scope of SOCRadar Platform. SOCRadar offers a comprehensive monitoring solution for the Dark & Deep Web, allowing organizations to detect and counteract threats across the surface, deep, and dark web. Leveraging our unmatched surveillance capabilities and in-depth threat analysis, we provide actionable insights to proactively protect your organization. By integrating automated external cyber intelligence with the expertise of a dedicated analyst team, we empower SOC teams to extend their security reach beyond their traditional boundaries.