
Dark Web Threat Profile: Conti Ransomware Group
Getting Acquainted with Conti
Conti Ransomware, an active and dangerous ransomware gang threatening corporations in multiple sectors, is a force to be reckoned with. The gang was first observed in December 2019 and began operating persistently in July 2020. The group uses the alias WizardSpider. And it is believed to be located in Saint Petersburg, Russia.
Conti Ransomware group is responsible for the attack on the Irish Health Service Executive, which resulted in delays in COVID-19 tests and the cancellation of patient appointments in Ireland. The gang is also known for some attacks on a government agency in Scotland and a government board in New Zealand. These attacks had catastrophic results for organizations, which shows how dangerous the Conti Ransomware group can be.
The FBI explains that the Conti Ransomware gang has victimized over 400 organizations worldwide, with around 290 in the United States. The ransomware group has mainly targeted emergency medical services, 911 dispatch centers, municipalities, and law enforcement agencies within the last year. According to the FBI, the group’s ransom demands have been as high as $25 million.
What are Conti’s Targets?
According to an analysis done by Sophos, the group mainly targets organizations from retail, manufacturing, construction, and healthcare industries and government organizations which are mainly from the United States. The Conti group affects the United Kingdom, Canada, and Western European countries the most after the US.
How Do They Get In? An overview of Conti’s Tactics, Techniques, and Procedures
The group’s main tactic is to steal the victims’ files and encrypt them to request a ransom payment. The group exfiltrates the data first, then encrypts the data, making the attack a “double extortion attack”. If the victim does not comply and pays the ransom, the gang threatens to publish their stolen data on a leak site that the group manages.
SOCRadar’s DarkMirror monitors the ransomware gangs’ sites on the Dark Web and provides visibility into the ransomware threats, new victims as well as leaked information.
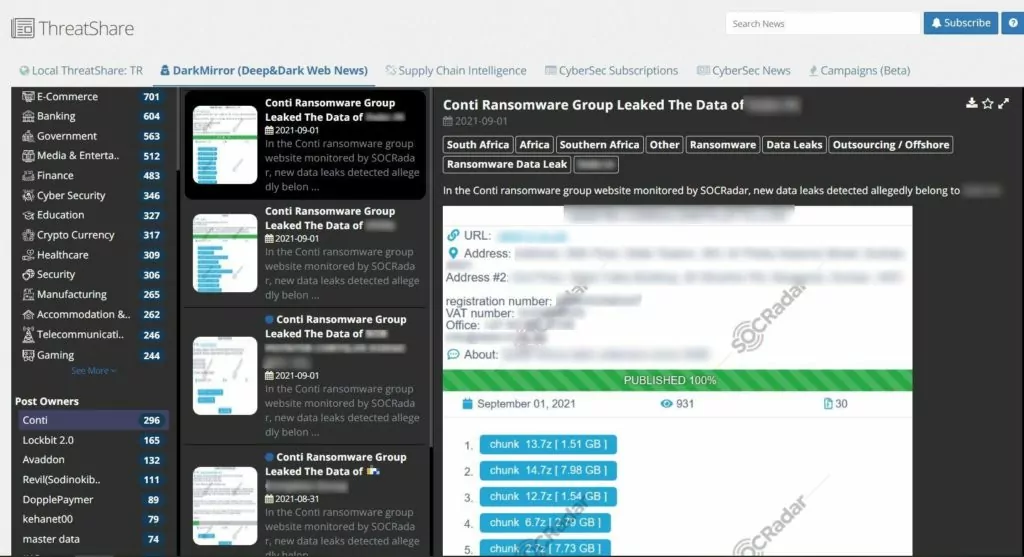
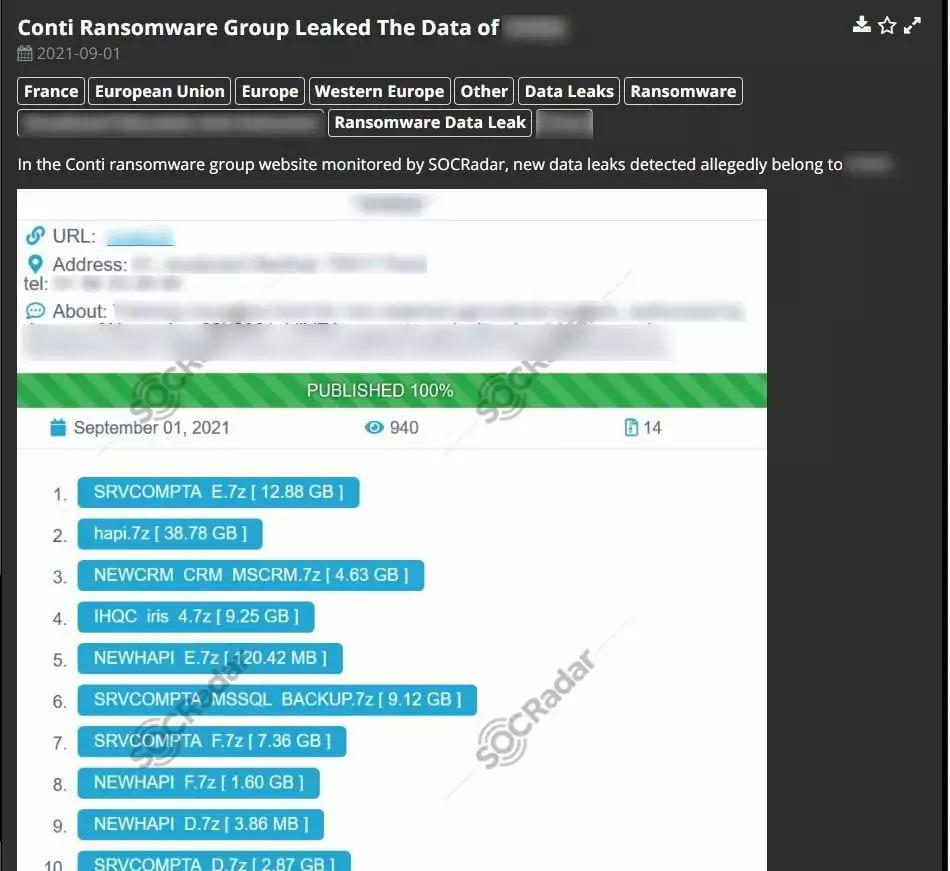
Evading Conti and Ransomware in General
The Conti Ransomware Group is known to have a human operator during the attacks instead of an automated process. The group prefers a speed-over-stealth method in their attacks by using up to 32 logic threads. The ransomware is utilized as Ransomware-as-a-Service (RaaS), and it has code similarities with the Ryuk Ransomware.
Conti’s main attack vectors are phishing e-mails, malicious attachments, stolen credentials , and exposed RDP servers. Once the group enters the system, the human operator’s first objective is to disable particular security and backup services on the system. After disabling the services, the operator deletes the existing backups and adds the required tools. The preparation before the execution of the Conti ransomware usually takes from four days up to three weeks. After the Conti ransomware is executed, the victims are informed about the situation, and the Conti group demands a ransom payment.
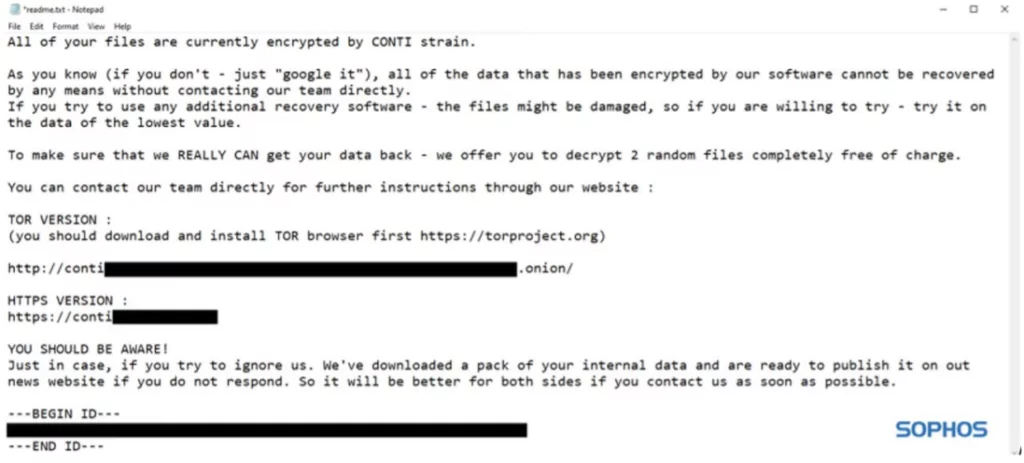
Conti’s ransom note to the victims can be found below:
To evade ransomware attacks and minimize risks, SOCRadar suggests that:
- The Company data is backed up regularly.
- Two-factor authentication (2FA) is implemented where possible.
- The employees are advised to use strong passwords, and their passwords are periodically updated.
- Unused RDP ports are disabled, and all RDP ports are monitored.
- Software used by the company is regularly updated.
- Administrator credentials are required to install additional software.
Discover SOCRadar® Free Edition
With SOCRadar® Free Edition, you’ll be able to:
- Discover your unknown hacker-exposed assets
- Check if your IP addresses tagged as malicious
- Monitor your domain name on hacked websites and phishing databases
- Get notified when a critical zero-day vulnerability is disclosed
Free for 12 months for 1 corporate domain and 100 auto-discovered digital assets.
Try for free



































