
Data of Many Governments are on Sale
Powered by DarkMirror™
Data held by states is valuable to many threat actors. This information is sometimes used for fraud and sometimes for larger attacks. Data from missile systems companies such as NATO, Italian Ministry of Defense, Philippine Intelligence and MBDA have been put up for sale on the dark web last week.
Here are other noteworthy dark web incidents from last week.
Find out if your data has been exposed.
Confidential Data from Acer are on Sale
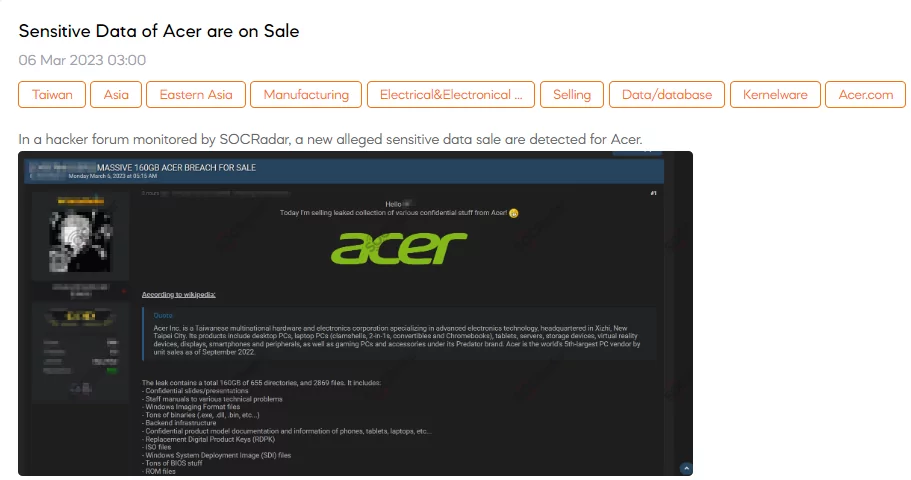
SOCRadar detected a new post on a hacker forum that claimed to sell a database that allegedly belongs to Acer, a Taiwanese multinational hardware and electronics corporation. Acer has confirmed a data breach in which a threat actor hacked a server containing private documents for repair technicians. The threat actor claims to have stolen much data, including technical manuals, software tools, infrastructure details, product model documentation, BIOS images, ROM files, ISO files, and replacement digital product keys. As proof, the threat actor shared screenshots of technical schematics and confidential documents related to the Acer V206HQL display.
While the breach has been confirmed, Acer states that its investigation does not indicate that customer data has been impacted. The leaked data reportedly includes 655 directories and 2869 files, totaling 160GB. The threat actor is reportedly attempting to sell the stolen data on a popular hacking forum.
New Ransomware Group Identified: Dark Power Claims Ten Victims

A new ransomware group was identified by SOCRadar dark web team while monitoring activity on the dark web. According to their website, the Dark Power ransomware group has claimed responsibility for ten victims. The total estimated revenue of the victim companies is 200 million dollars. Among the countries affected are Turkey, Egypt, Peru, Israel, the Czech Republic, Algeria, and France.
The New Ransomware Victim of Medusa Team: Minneapolis Public Schools
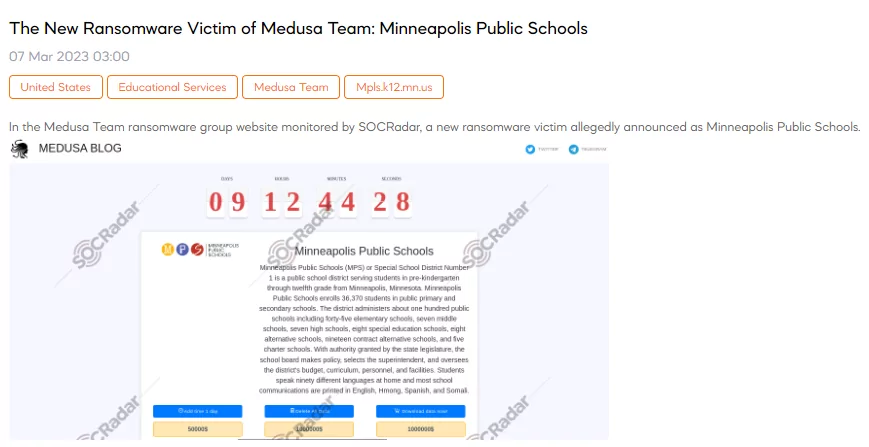
SOCRadar detected a new post that the Medusa team had included Minneapolis Public Schools in their list of victims, where the student population in their primary and secondary schools is 36,370. The ransomware attackers are demanding a $1,000,000 payment from the Minneapolis Public Schools (MPS) district to erase the data they allegedly stole during the ransomware attack. They are asking for an equal amount to sell the data to interested parties, and they are willing to extend the data publication deadline for one day for $50,000. The ransomware group has released a video almost 51 minutes long, showing all the data they claim to have stolen and sold for the same amount.
Data of Many Governments are on Sale
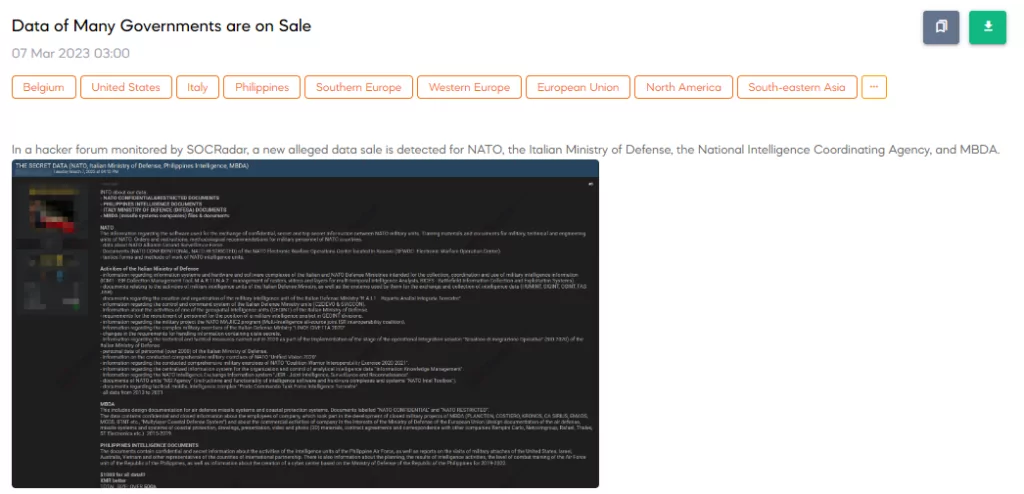
SOCRadar detected a post on a hacker forum in which a threat actor claimed to have sold confidential information, including files and documents belonging to organizations such as NATO, the Italian Ministry of Defence, the Philippines Intelligence, and missile systems companies like MBDA. The price for all the data is $1000, with the preferred payment method being XMR (Monero cryptocurrency). They also shared samples of the data they claimed to have captured on their Telegram channels.
Powered by DarkMirror™
Gaining visibility into deep and dark web threats can be extremely useful from an actionable threat intelligence and digital risk protection perspective. However, monitoring all sources is simply not feasible, which can be time-consuming and challenging. One click-by-mistake can result in malware bot infection. To tackle these challenges, SOCRadar’s DarkMirror™ screen empowers your SOC team to follow up with the latest posts of threat actors and groups filtered by the targeted country or industry.




































