Defending Against Persistent Threats
Threat actors follow a series of events-called the “cyber kill chain framework” from defense perspective-to successfully infiltrate a network and either exfiltrate, destroy, or to cause business disruption. The lifecycle of an attack can be broken into 7 stages: reconnaissance, weaponization, delivery, exploitation, installation, command and control(C2) and lastly actions on objectives.
While the threat actors’ order may be dynamically changing, since they can create their own sequence from the lifecycle stages, the goal is forever the same: to reach the last stage and achieve their objective.
The good news is that, blocking just one of the stages in the attack lifecycle is all you need to do to defend your organization’s network and data from a breach. Just like burglars and thieves, adversaries accurately get prepared for their attacks. They examine, detect, and pick weak points, often using phishing tools or obtaining public information from social profiles or corporate websites. Gathering as much information about the target as possible is their goal, beginning with passive and moving toward more aggressive active reconnaissance which includes scanning for services and applications which can be exploited. The threat actors generate a list of potential victims with a narrow goal in mind, and conducts reconnaissance to isolate those most vulnerable to attack.
Threat actors attempt to use every method available to discover vulnerable attack vectors into your organization available on the surface, deep and Dark Web such as Google Hacks, internet-crawling resources (e.g. Shodan or Censys), Public Repositories (e.g. Github), Paste sites (e.g. Pastebin), Dark Web forums and the treasure of personal information: Social Media. Bad news is that there are countless tools to perform these tasks readily available for free.
Your adversaries may be searching for a broader set of attack vectors such as:
- VIP/C-level executives’ email addresses and information
- Customer information including credentials and credit card info (especially juicy target after GDPR came into effect in May 2018)
- Forgotten domains / web sites / expiry information (remember the special marketing campaign of last summer)
- Forgotten SSL certificates and their grading (remember Equifax breach caused by expiry of SSL certificates)
- IP address ranges
- Active products
- Open ports and services
- Operating systems
- Network applications/services
Specific tools, like next generation firewalls and IPS appliances, can help you stop some of the cyber kill chain stages, especially port scans and host sweeps. But, due to the common nature of the Internet, research by threat actors into your employees, customers, business network and 3rd parties is almost impossible to protect against.
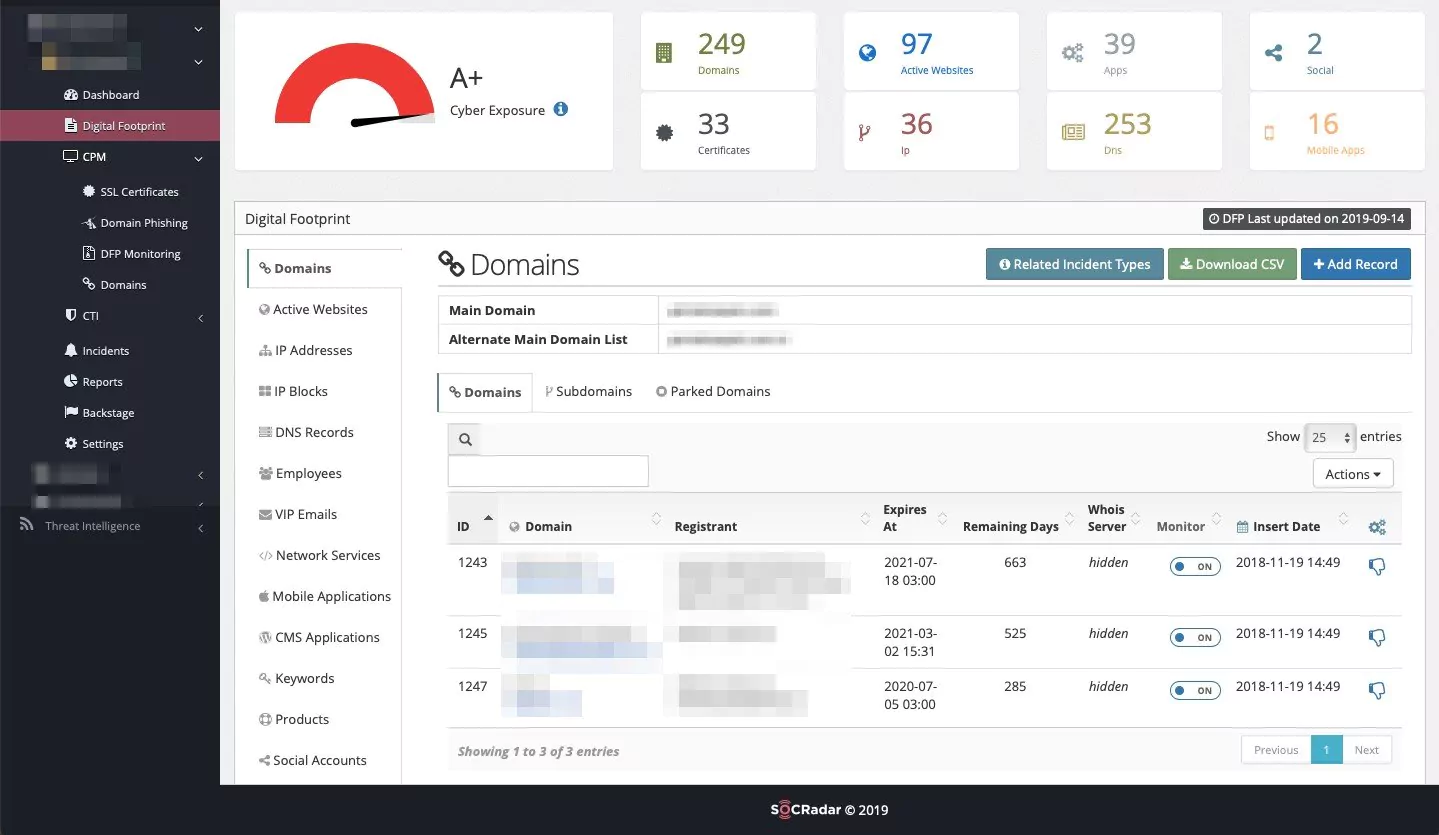
In order to stop threat actors seeing your network an easy target, it’s the best to conduct an evaluation of your assets continuously. However this is extra burden on your security analysts and time-consuming. You can benefit from SOCRadar to handle this job fully automated, eliminated from human error and latency. SOCRadar platform continually scans the entire internet and collect telemetric data to generate a dynamic index of your internet-facing attack surface. This process illuminates websites, third-party JavaScript, mobile apps, URLs, web page content, ASNs, IPs, and nameservers, many of which are often not in your inventory. SOCRadar uncovers all your digital assets, enabling your SOC team to understand the attack surface outside your firewall and viewing your digital footprint from the perspective of a global adversary. You can see SOCRadar as an extension of your team alerting you whenever your sensitive digital assets are exposed across a broad range of online sources.