
Detecting IoT Devices For Your Company
From smart wearables to interconnected industrial devices the IOT is becoming a larger part of our lives since the first coinage of the term in 1999 at a P&G presentation (although the idea goes far back in to the 1980s.).
In 2020 Gartner was predicting the size of the IOTs to be 20 billion, which fell short of 31 billion connected devices this year with a market value of over 520 billion USD by the end of 2021 according to research firm Statista. [1]
There are various security risks associated with IoTs as we would all remember the Mirai Botnet which scared us in to thinking that our fridge may not be up to any good while we are sleeping. Just to refresh our memories, in 2016 a DDOS attack brought down a big portion of the internet in the US east coast. Threat actors took advantage of vulnerabilities in IoT devices, which usually lack a mechanism to update its software on top of having security misconfigurations such as default passwords.
An even worrying trend is in the industrial IoT space is expanding as factory equipment is also increasingly becoming interconnected for improved productivity. Industrial IoT is predicted to account for 30% of the global GDP by 2030.[2] Recent cyber-attacks that targeted nuclear power plants or water treatment facilities by involved abuse of industrial IoT devices.
Tracking IoT Devices
A simple open-source research, for example using Shodan, can reveal the extent of internet connected industrial IoT. Below a US based Siemens automation device can be seen internet exposed via port 161:
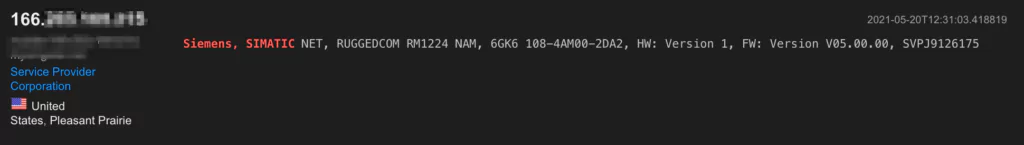
This type of reconnaissance requires knowledge of the specific devices that is being searched for. Nevertheless, from the verbose http response a lot of useful information can be detected.
There are a number of ways to track IoTs as part of the attack surface. In one interesting study, researchers at Max Planck Institute looked at sample traffic flows and were able to deduce IoT devices from the traffic patterns even in NAT networks. [3] This was done by looking at port numbers and a list of destination IPs, where these devices were likely connecting to
In above Siemens example, the port number is one signature that helps with detection. Other features can be destination Ips (as the devices connect with the manufacturers), protocols, or domains.
Once detected, incorporating the IoTs into attack surface monitoring with a tool like SOCRadar to monitor against existing vulnerabilities or zero-days will provide better visibility against cyber threats. This allows timely patch management and mitigation of various security misconfigurations.
Discover SOCRadar® Free Edition
With SOCRadar® Free Edition, you’ll be able to:
- Discover your unknown hacker-exposed assets
- Check if your IP addresses tagged as malicious
- Monitor your domain name on hacked websites and phishing databases
- Get notified when a critical zero-day vulnerability is disclosed
Free for 12 months for 1 corporate domain and 100 auto-discovered digital assets.
Try for free

































