
Different Kinds of Impersonating: Phishing & Domain Squatting
Phishing and domain squatting are commonly used by threat actors to achieve different kinds of goals against an organization. Among these goals are;
- Stealing personally identifiable information (PII) and selling it on black markets for profit.
- Malware injection to attain network access.
- Brand abuse to take down competitors, and many other different malicious actions.
Using social engineering skills and of course other hacking skills, threat actors send legitimate-looking emails, impersonated domains, or create completely cloned websites to create traps for organizations. In able to thwart these actions, you should know what the difference between these types of cybercrimes is.

What is phishing?
Not to be confused with fishing, but the logic is similar. A hacker targeting an individual, or group of individuals, prepares a trap with the hope that the target will fall for it. So you get it why the logic is similar to fishing.
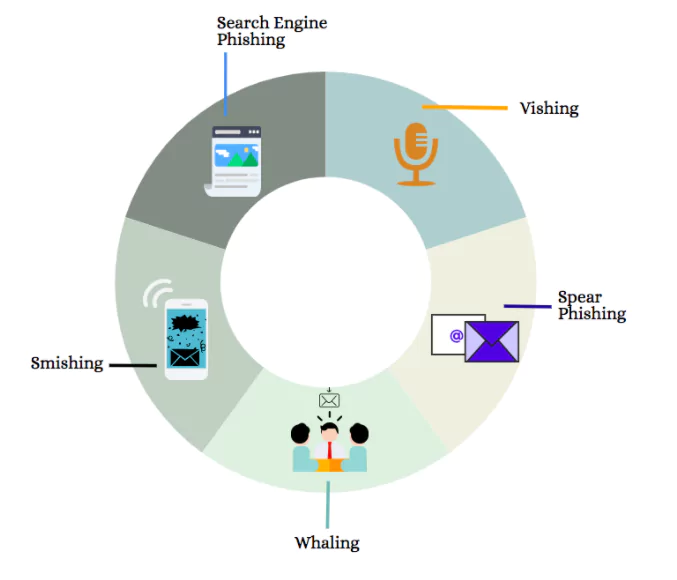
Phishing attacks can be performed through different channels, therefore they can be divided into some categories: vishing, smishing, the most common form – spear phishing, whaling, and search engine phishing. You may have heard of all these if you are in the cyber part of the world.
Now let’s see what their difference is.
Vishing
A portmanteau word from “voice” and “phishing” – vishing is a technique for stealing sensitive information through calls using Internet Telephone Service. For instance, you get a call from someone impersonating a bank staff personnel who asks for your account number and other sensitive information to reset your password because it has been compromised.
Smishing
Another portmanteau word from “SMS” and “phishing” – in smishing, personal information is stolen through text or SMS messages. People tend to trust text messages more than emails, but the way of stealing information is pretty similar. There’s usually a link, that, of course, will look legitimate to you or lures you to open it, and when opened it will gather personal information.

Spear phishing
This is a cybercrime that mainly targets individuals of an organization. The hacker usually sends a personalized email containing a malicious downloadable file or a link to a malicious site, making it look like a legitimate email by impersonating another individual, and hoping the receiver will fall prey to it. Normal phishing though is when the same email is sent to a group of people, without any intention to catch a specific individual, and any fallen prey means profit for the hacker.
Whaling
Also called CEO fraud, whaling is a form of spear phishing. Though the targeted individual is more specified, here only the high-rank executives of an organization are targeted. An example of abusing a compromised VIP account is using it to send emails to other employees, and get personal information from them, to further post them on the dark web. There are two types of launching whaling emails, one is name spoofing, the other is email spoofing. In the first, the sender uses only the high executive’s name, and another email address similar to the original but with some typos, hoping the receiver won’t notice. In email spoofing, both the name and email belong to the executive.
Search engine phishing
This phishing type is a bit different. There is no link sent on an email, text message, or phone call received. This kind of phishing refers to a fake website, somehow managed to get indexed by a search engine. A very well-known form to lure people into giving away their sensitive information is by creating an online shopping website, offering very cheap or completely free products, and asking for bank or credit card information to proceed with shipping payment.
There are different forms of cyber threats that intend to steal customers or their data, even worse, there are others that intend to take down competitors’ websites. The most common way of achieving these kinds of goals is cybersquatting.
What is cybersquatting?
Cybersquatting, or domain squatting, is the act of intentionally registering or even using a domain name of an existing business that is trademarked but doesn’t have a related website yet. The main goal here is to park that domain, so when the organization wants to use it in the future, the cybersquatter can profit by selling it to them.
Typosquatting
This is a type of cybersquatting, and there is just a slight difference between them. This squatting method means registering a domain of a trademarked business name, which again doesn’t have a website, but this time there is a typo in it. In this case, the company may already have a website with the trademarked name, but since the squatted domain has a missing or an extra letter, or even a simple misspelling, it is not a problem to register it. Let’s say the legitimate domain is example[.]com the domain squatter can use exampl[.]com, examplle[.]com or even exampel[.]com
As you can see, for someone who doesn’t pay much attention to the domain before clicking ‘enter’, which is most of us, it is difficult to understand that you are visiting a non-legitimate website.

Top-level domain squatting
Another type of cybersquatting is Top-level domain squatting. It means using the same brand name, but with a different TLD. A top-level domain is the .com .org .net and so on, that is added to each domain. Usually, cybercriminals try to find which TLD is not used by the company and purchase a domain with it. Another form of TLD squatting is by purchasing a different country code TLD (ccTLD).
Despite the difference between these cybercrimes, they all pose the same risk to businesses: Bad reputation. Domain squatters usually have similar intentions when using trademarked business names as their domains, and some of them include starting phishing campaigns to get customer data, making the company buy the squatted domain, or simply spreading abusive advertisement about the brand with the intention to take a competitor down.
Protect yourself!
SOCRadar uses a very complex and robust algorithm to detect possible Phishing Domains that can impact a brand’s reputation.
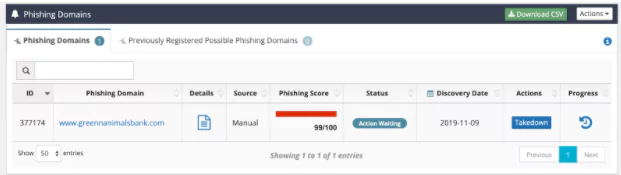
A very important feature in the SOCRadar Digital Risk Protection platform is the Integrated Takedown, which can be done with a one-click request.

































