
Digital Predators of 2023: Exposing Top Cyber Threat Actors
In 2023, the digital landscape continued to evolve rapidly, but so did the sophistication and audacity of cyber threat actors. From ransomware to sophisticated phishing campaigns, the threat landscape has been dominated by groups that have advanced their technical capabilities and expanded their targets globally. This introduction provides a glimpse into the most dangerous threat actors of the year, each with their distinct methods and significant impacts across various sectors. Their activities underscore the importance of staying vigilant in cybersecurity and understanding the evolving threats in the digital world. For a comprehensive review of last year’s threat landscape, SOCRadar’s 2023 End-of-Year Report offers detailed insights into these and other topics.
CLOP Ransomware

The CLOP Ransomware group came to the fore in 2023 with the GoAnywhere and MOVEit attacks.
The CLOP Ransomware, known for its involvement with the CryptoMix family, has been a significant cyber threat since 2019. Its evolution includes targeting large organizations and exploiting vulnerabilities like the zero-day in GoAnywhere MFT, Fortra’s secure file transfer solution. In 2023, CLOP made headlines for adopting torrents to distribute stolen data, enhancing their extortion tactics. This change in strategy indicates a shift to more accessible and efficient data dissemination methods, making it harder for law enforcement to intervene. CLOP has targeted various sectors, including finance, IT, and manufacturing, focusing particularly on Western countries like the US, UK, Canada, and Germany.
LockBit 3.0 Ransomware
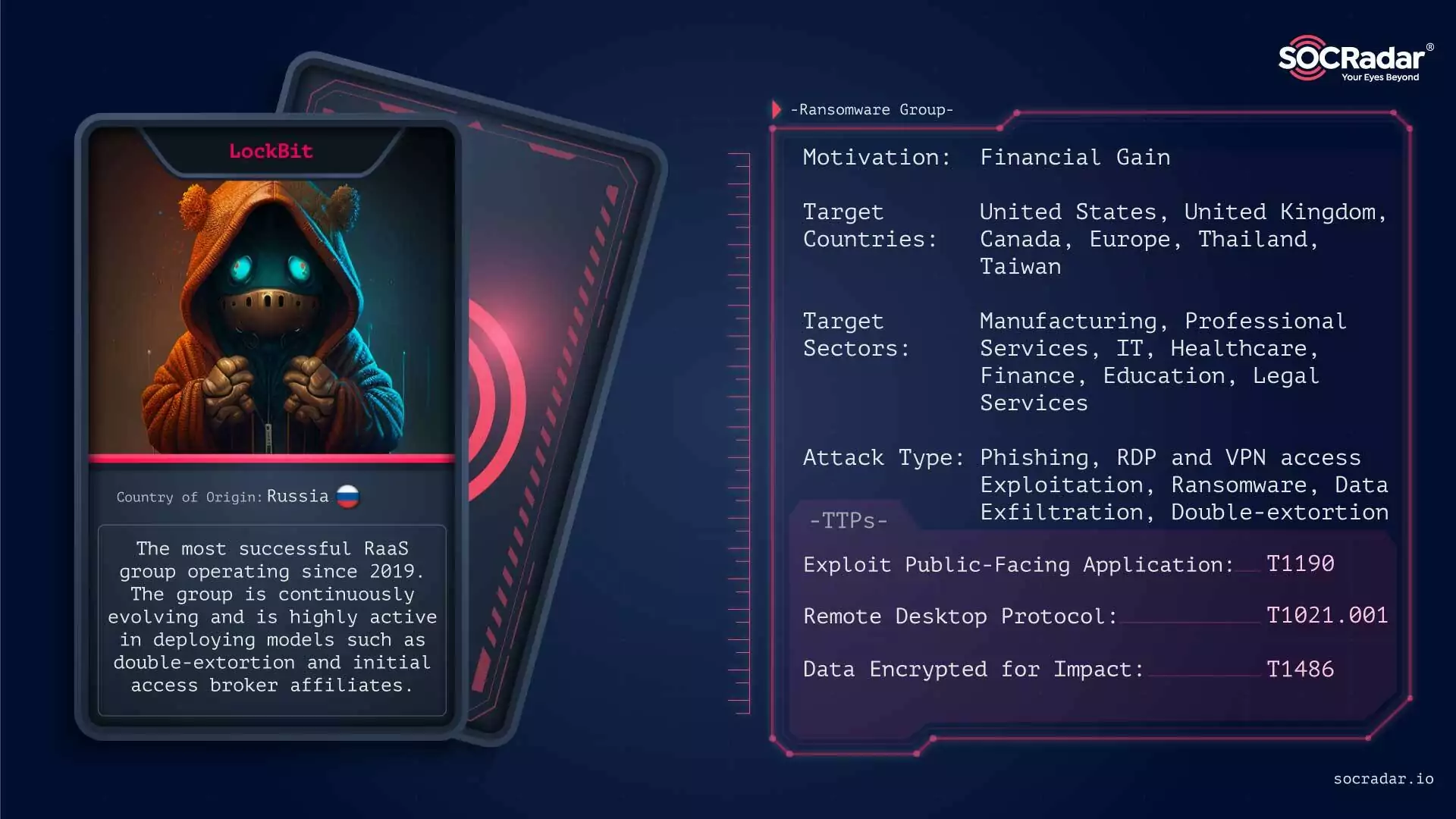
As in previous years, LockBit became one of the most active threat actors in 2023.
LockBit 3.0 Ransomware, active since 2019, became particularly notorious in 2022, continuing its high-impact activities into 2023. As the most active ransomware group, LockBit targeted a wide range of industries, including manufacturing and healthcare, across various countries, primarily in the U.S. In 2023, LockBit expanded its capabilities, developing ransomware that could target more systems like Apple, Linux, FreeBSD, and different CPU architectures. Despite operational challenges and fluctuating activities, LockBit remained a significant threat, continuously evolving its methods and targeting strategies.
BlackCat (ALPHV) Ransomware

BlackCat made headlines with various high-profile attacks.
BlackCat (ALPHV) Ransomware, known for its innovative use of the Rust programming language, has been a significant cyber threat. In 2023, it made headlines with various high-profile attacks, including a 7TB data theft from Barts Health NHS Trust and compromising Reddit, resulting in 80 GB of data theft. The group’s tactics, using malicious Windows kernel drivers like POORTRY for evasion and its focus on triple extortion methods, have marked it as a formidable adversary in the cybercrime landscape.
8Base Ransomware
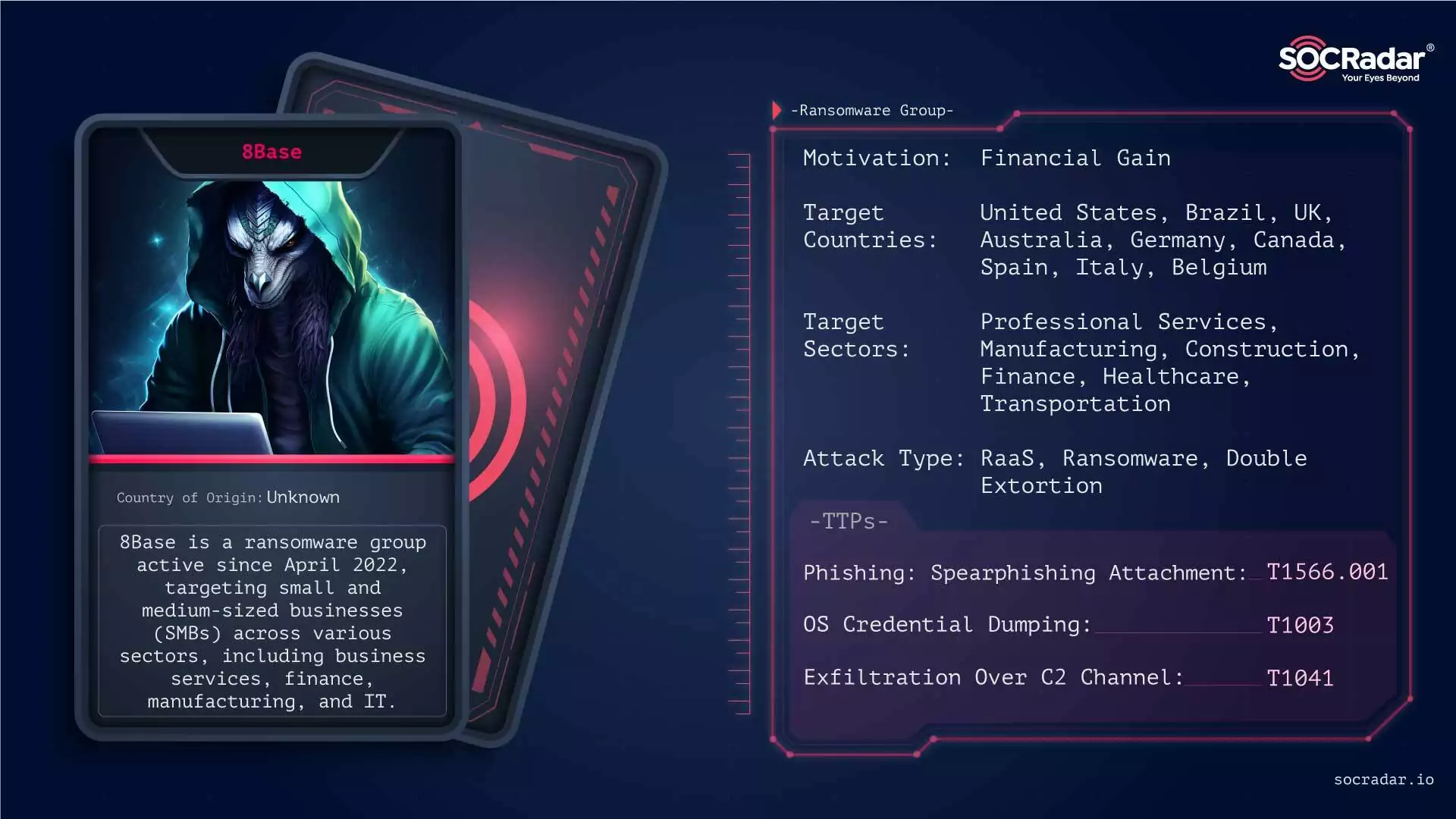
8Base added organizations from almost every industry to its list of victims in 2023.
8Base Ransomware, active since April 2022, has quickly become a notable threat, especially to small and medium-sized businesses across various sectors like business services, finance, manufacturing, and IT. Characterized by double-extortion tactics, 8Base threatens to publish encrypted files unless a ransom is paid, adding significant pressure on victims. The group’s rapid rise and the considerable number of victims have marked them as a major player in the ransomware landscape.
Play Ransomware
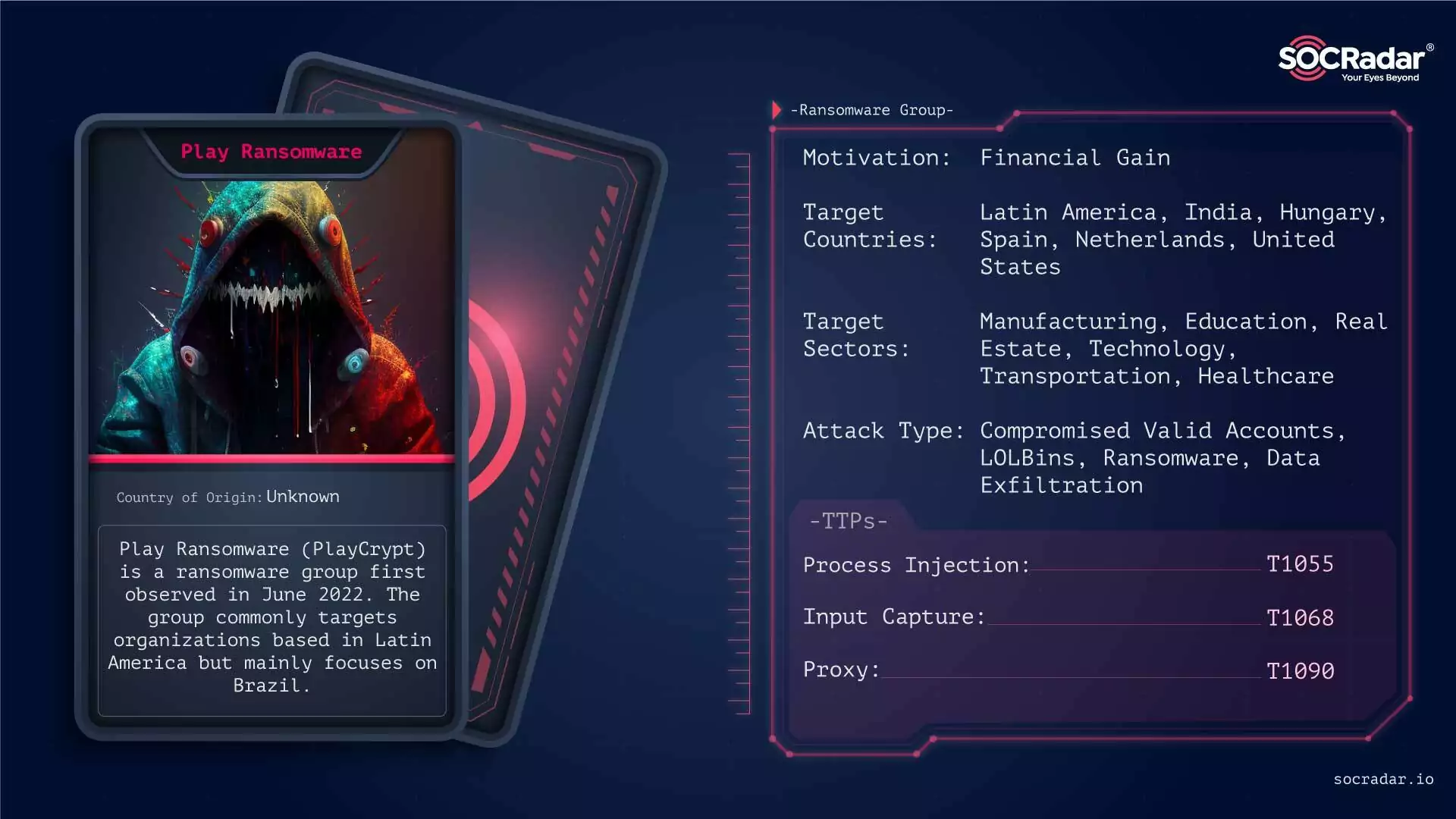
Play Ransomware’s RaaS model also attracts other threat actors.
Play Ransomware, active since mid-2022, has demonstrated a significant threat in 2023 with its advanced techniques and broad targeting. It gained attention for its unique intermittent encryption method, enhancing evasion. Key attacks included significant breaches at a Swiss IT firm affecting government entities, a major Spanish bank, and a U.S. communications firm. The group also shifted to a Ransomware-as-a-Service (RaaS) model, indicating a potential increase in future incidents due to the ease of deployment for other threat actors.
Rhysida Ransomware

The Rhysida group is a threat actor in 2023 especially targeting Latin America.
The Rhysida Ransomware group emerged in May 2023 as a significant cyber threat. Known for their first major attack on the Chilean Army, they have since targeted various sectors, notably Education and Manufacturing, in North America, Europe, and Australia. Rhysida utilizes Cobalt Strike deployment or phishing campaigns, employing a double-extortion strategy. They pose a serious risk due to their strong encryption techniques and strategic targeting of military and government institutions.
Royal Ransomware

Royal Ransomware group particularly targets the manufacturing industry.
The Royal Ransomware group, active since September 2022, is known for its expertise in ransomware operations, particularly targeting the manufacturing industry. Their attacks frequently involve callback phishing, tricking victims into installing malware disguised as legitimate software. Royal Ransomware employs a double-extortion method, demanding ransoms between $250,000 to over $2 million, and has a significant impact on its victims, including those in Europe and the Americas.
Medusa Ransomware
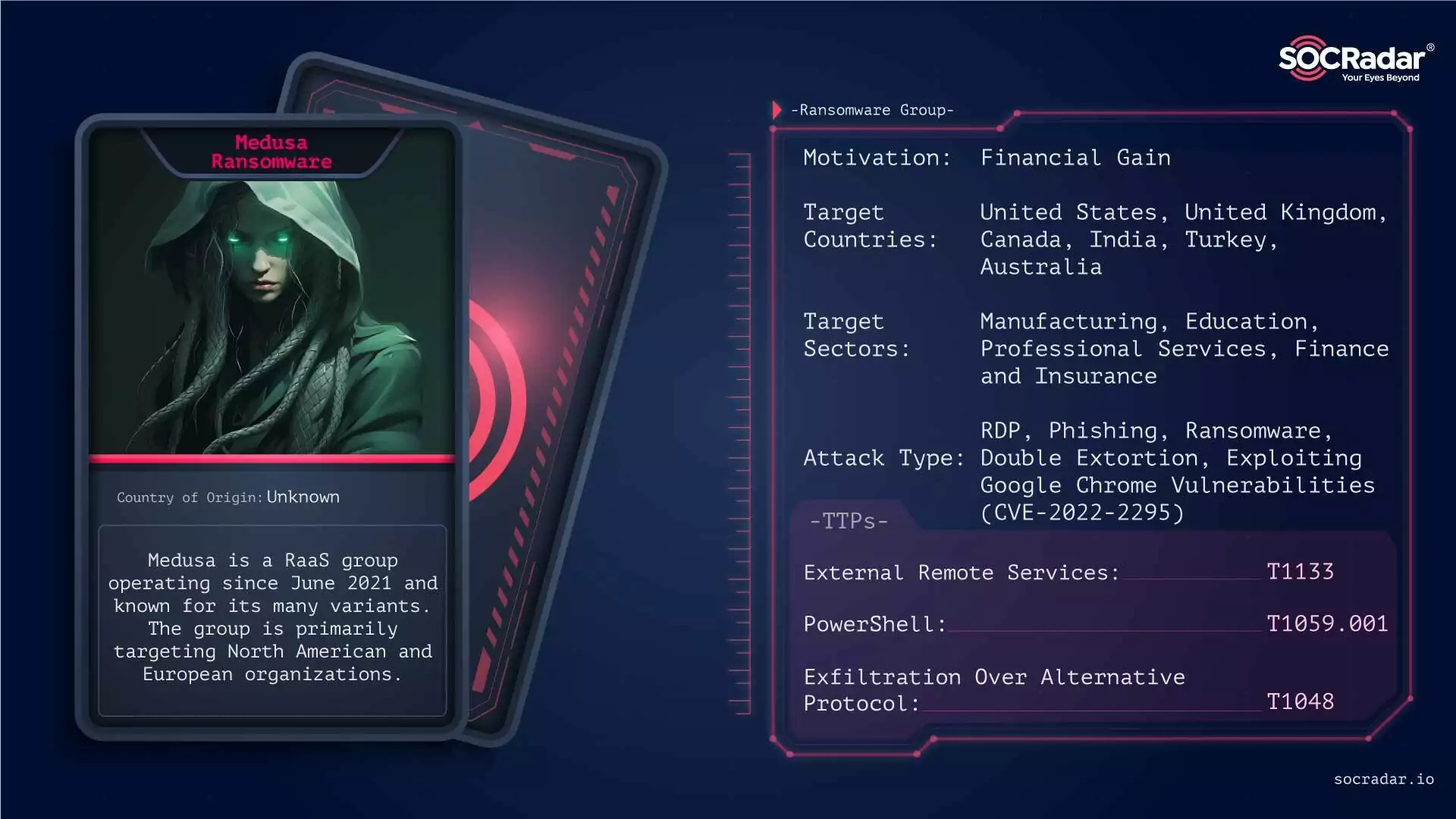
The attacks of the Medusa ransomware group against education significantly impacted the industry in 2023.
The Medusa Ransomware group has been a formidable cyber threat since its first appearance in June 2021. Operating on a Ransomware-as-a-Service (RaaS) model, Medusa targets a wide range of sectors across North and South America and Europe. Their methods include exploiting vulnerabilities in Remote Desktop Protocols and phishing campaigns. Medusa is notorious for its impactful attacks, such as the significant breach against the Minneapolis school district in March 2023, demanding $1 million in ransom. The group’s strategy of targeting corporate entities and institutions amplifies the severity of its attacks.
In conclusion, 2023 witnessed the rise of significant ransomware groups, each posing unique threats in the cyber world. Their targeted attacks have impacted various sectors globally, underlining the critical need for robust cybersecurity measures. For a comprehensive overview of the year’s cyber threats, SOCRadar’s 2023 End-of-Year Report provides in-depth insights and analyses.



































