
‘Dirty Pipe’ Linux Vulnerability Discovered
A “Dirty Pipe” vulnerability with CVE-2022-0847 and a CVSS score of 7.8 has been identified, affecting Linux Kernel 5.8 and higher. The vulnerability allows attackers to overwrite data in read-only files. Threat actors can exploit this vulnerability to privilege themselves with code injection.
What Happened?

The vulnerability, discovered in April 2021 by cybersecurity researcher Max Kellermann, is called Dirty Pipe. It took a year for the exposure to be fully understood when he got to the root of customers’ “uncompressible access logs” problem.
When it was discovered that the vulnerability could be exploited, it turned out that all Android versions based on vulnerable Linux kernel versions could also be affected. Dirty Pipe also makes version 5.10.43 vulnerable to attacks, such as the Pixel 6 and Samsung Galaxy S22.
How Critical is It?
The Dirty Pipe vulnerability has a CVSS score of 7.8, which indicates many reasons to consider it. The cyber threat actor must have read permissions, write must not exceed a page limit, and the file must not be resized to exploit the vulnerability.
Threat actors can exploit the CVE-2022-0847 vulnerability by creating a pipe, filling it with arbitrary data (to set the PIPE_BUF_FLAG_CAN_MERGE flag on ring inputs), emptying the pipe by leaving the pipe_buffer flag in the pipe_inode_info ring, opening the target file with O_RDONLY, and write arbitrary data into the pipe.
What Can be Done?
The Dirty Pipe vulnerability applies to Linux Kernel version 5.8 and higher and Android-based devices based on this version. Linux fixed the issue with 5.16.11, 5.15.25, 5.10.102 versions, and the Android patch.
How to Detect Dirty Pipe Vulnerability?
Although the Android kernel has been merged with the current updates, there are no indications that devices relying on vulnerable Linux versions have been fully fixed. For this reason, users should assume that their device may be susceptible to Dirty Pipe.
SOCRadar regularly monitors your assets and the technologies you use, along with their current versions. In this way, you will always be aware of your current inventory. With the Vulnerability Intelligence page, you can get detailed information about the vulnerability you want. We can examine the news on the agenda and share on the subject. If you’re going to follow the developments, you can subscribe if there are technology and products.
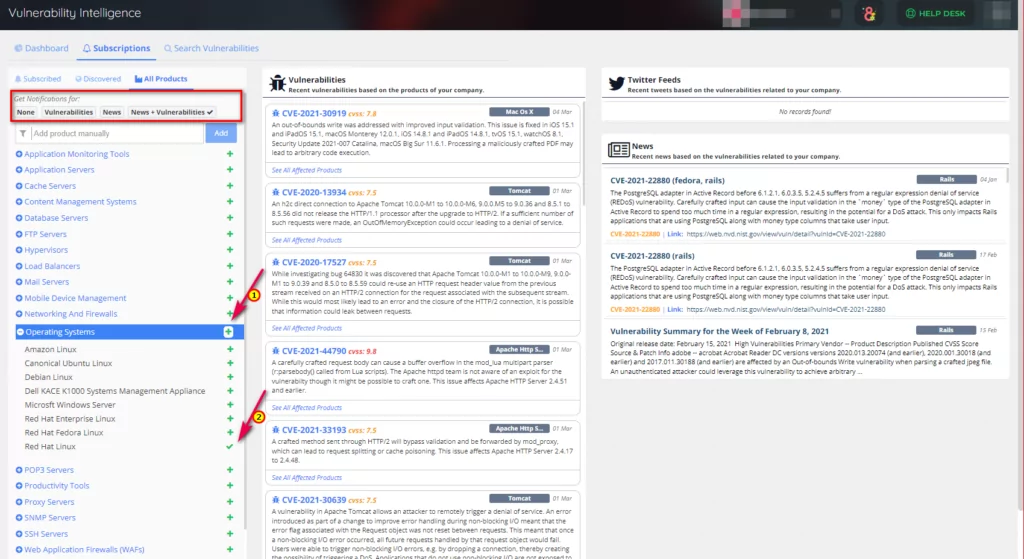
If you wish, you can arrange this process to be aware of the vulnerability only or aware of both the exposure and the information shared on Twitter and news channels.
Discover SOCRadar® Free Edition
With SOCRadar® Free Edition, you’ll be able to:
- Discover your unknown hacker-exposed assets
- Check if your IP addresses tagged as malicious
- Monitor your domain name on hacked websites and phishing databases
- Get notified when a critical zero-day vulnerability is disclosed
Free for 12 months for 1 corporate domain and 100 auto-discovered digital assets. Get free access

































