
EagerBee: Advanced Backdoor Attacks on Middle Eastern Governments and ISPs
In recent years, the cybersecurity landscape has witnessed a surge in sophisticated and highly targeted cyberattacks, with the EagerBee campaign emerging as one of the most complex and impactful threats. Specifically targeting government entities and Internet Service Providers (ISPs) in the Middle East, this advanced backdoor campaign has caused significant disruption.

AI illustration of the EagerBee Campaign
In this blog, we will outline the EagerBee campaign, examining the vulnerabilities it exploits, the tactics it employs, and the essential strategies organizations can implement to defend against such threats and safeguard their systems.
What is the EagerBee Campaign?
The EagerBee campaign is attributed to the cyber espionage group CoughingDown, a threat actor with a proven track record of targeting critical government and ISP infrastructures in the Middle East.
Known for their sophisticated backdoor techniques, CoughingDown operates with remarkable stealth, leaving behind minimal traces while maintaining extensive control over compromised systems. Their tactics often involve social engineering, credential dumping, and system manipulation, allowing them to achieve their objectives with precision and without detection.

AI-generated visual depiction of the Coughing Down threat group
- Advanced Backdoor Capabilities: These include file system manipulation, remote access, and process discovery.
- Command Execution: The malware is designed to deploy additional payloads, enabling full control over compromised systems.
The EagerBee campaign primarily targets key countries in the Middle East, including Saudi Arabia, the United Arab Emirates, Qatar, Kuwait, Bahrain, and Oman. These regions are often focal points for geopolitical tensions and digital espionage activities, making them prime targets for cyber attacks.
These attacks go beyond harming individual organizations, posing broader risks to regional stability and security. Thereby, government entities and Internet Service Providers (ISPs) in these countries are at high risk, with the EagerBee group utilizing sophisticated tactics to infiltrate sensitive systems and gather valuable information.
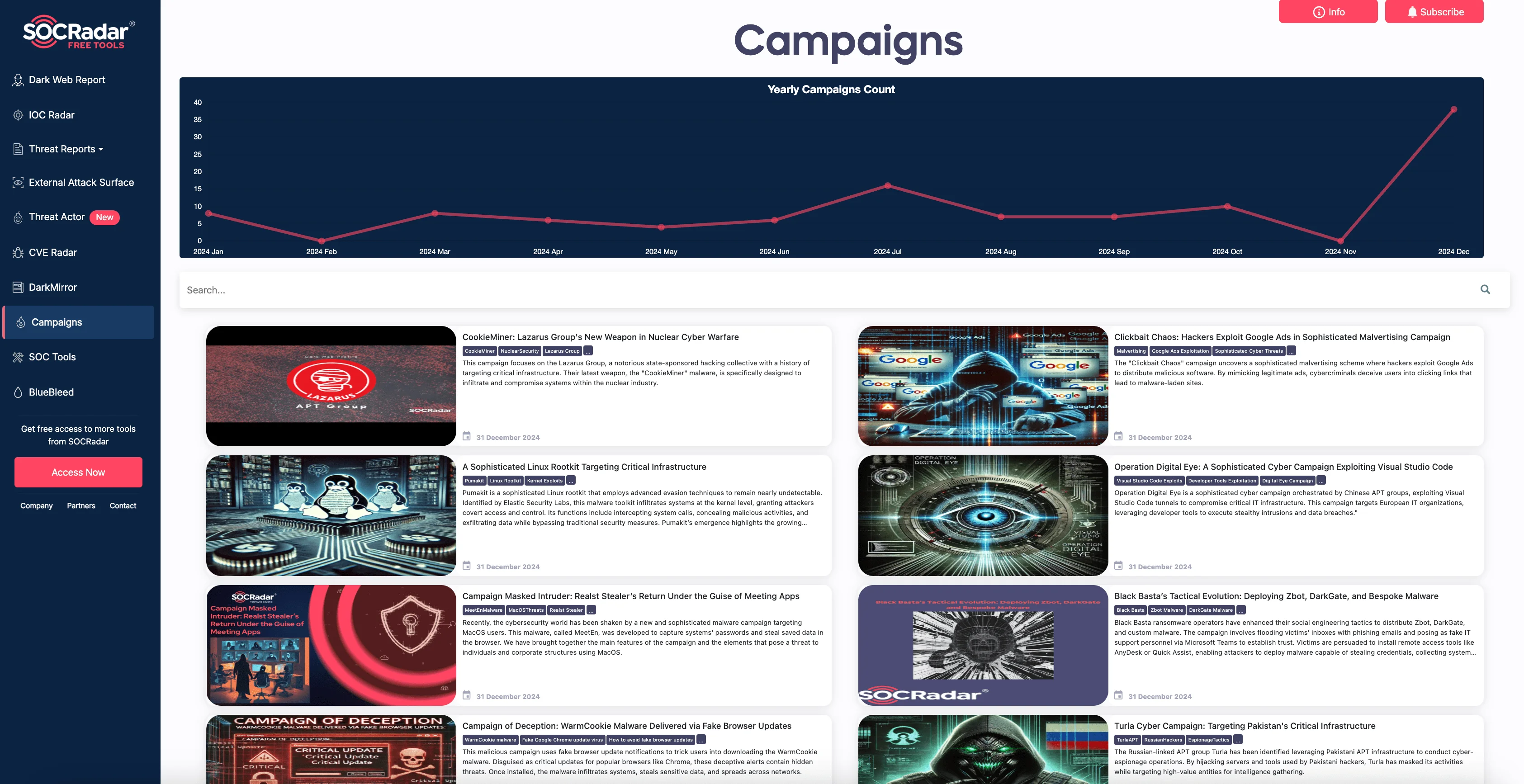
SOCRadar LABS Campaigns page provides the most recent updates and intelligence on campaign activities.
Visit SOCRadar’s LABS Campaigns page for in-depth information on a variety of cyber threat actor campaigns, covering both ongoing and past activities. SOCRadar’s Campaign analyses include Indicators of Compromise (IoCs) and details of attack methods, such as espionage tactics, malware, and more.
Mitigation Strategies and Security Recommendations
To tackle sophisticated threats like EagerBee, it’s critical to adopt a proactive cybersecurity strategy. Below are essential steps organizations should take:
- Implement Behavioral Analysis Tools
Deploy tools that can detect unusual behavior and suspicious activity across your networks and systems. SOCRadar’s Threat Hunting module empowers your team to identify emerging threats targeting your organization, allowing you to take action before they escalate into serious breaches. - Enhance User and Admin Training
Ensure all users and system administrators are educated on recognizing and avoiding social engineering tactics. SOCRadar’s Cyber Threat Intelligence provides valuable, up-to-date threat intelligence, helping organizations understand the latest attack vectors and giving security teams the knowledge they need to stay ahead of potential attacks. - Maintain Strong Patch Management and Secure Configurations
Regularly update and secure all systems, making sure your infrastructure is optimized against known vulnerabilities. SOCRadar’s Attack Surface Management (ASM) module continuously monitors your digital assets, highlighting vulnerabilities and offering insights on how to prioritize remediation efforts effectively.
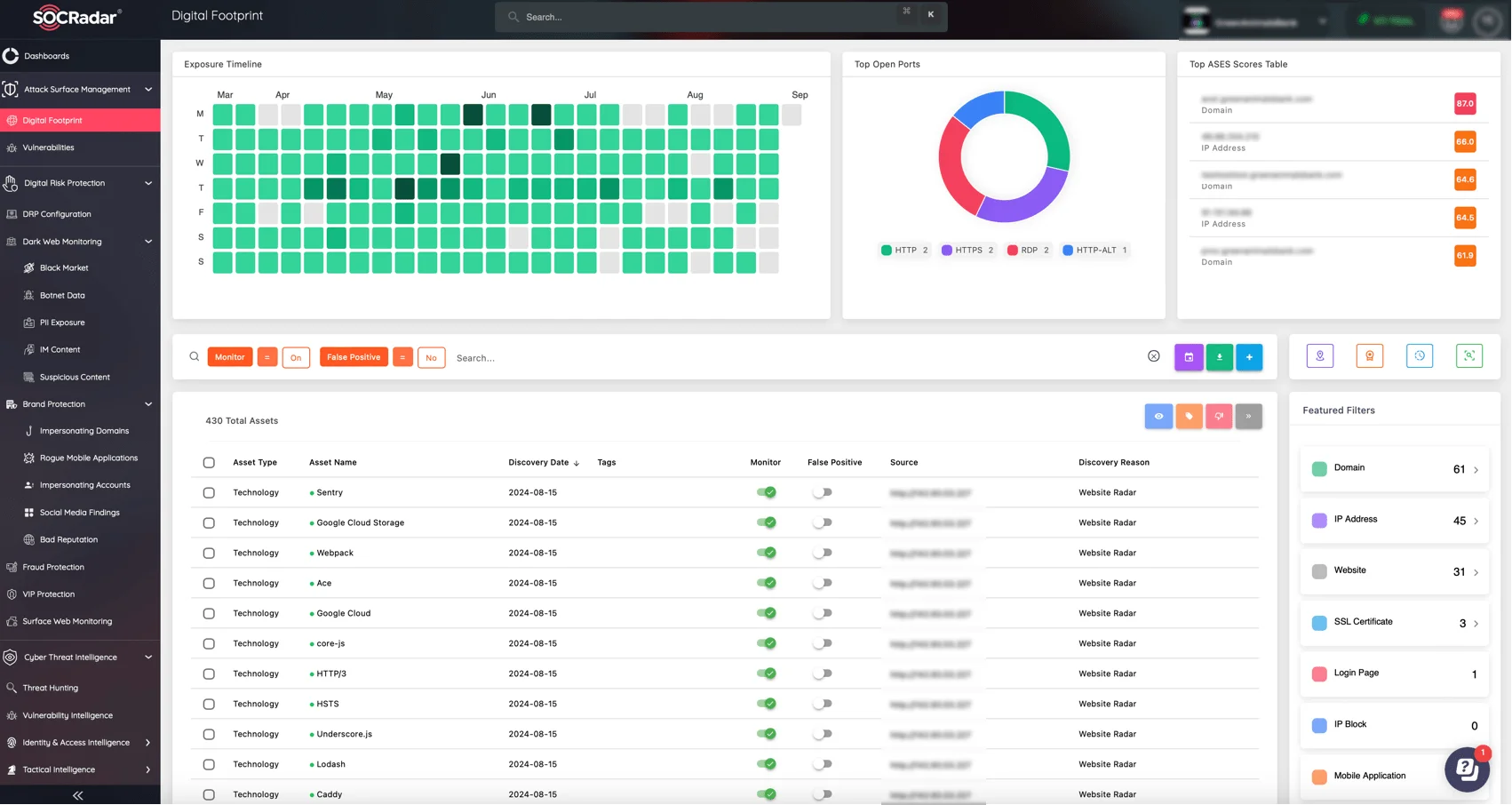
SOCRadar’s ASM module page, Digital Footprint
- Leverage SOCRadar’s Comprehensive Solutions
SOCRadar offers powerful tools, such as Threat Hunting, Attack Surface Management, and Cyber Threat Intelligence, to enhance your security posture. These modules work together to proactively detect, analyze, and mitigate threats, giving you a comprehensive defense system to manage evolving cyber risks.
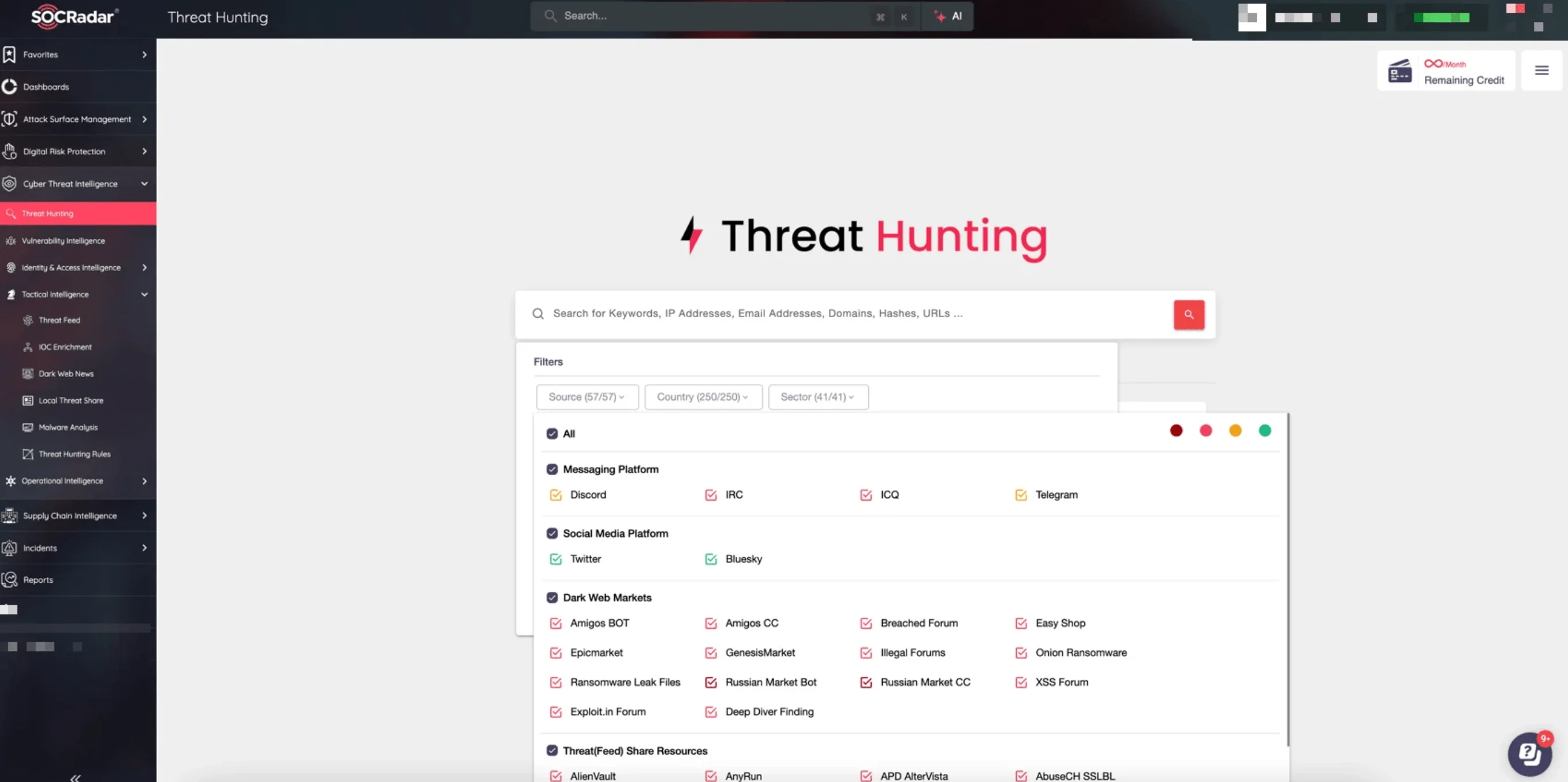
Threat Hunting search page on the SOCRadar XTI platform
The EagerBee campaign highlights the need for more advanced and dynamic security measures. Traditional defenses simply can’t keep up with today’s sophisticated threats. SOCRadar’s proactive solutions, like real-time threat hunting, attack surface monitoring, and up-to-date threat intelligence, give organizations the tools they need to stay ahead of attackers and mitigate risks before they escalate.

































