
Why Is It Important? East-West and North-South Traffic Security
Data centers are physical facilities designed to support your business applications, AI activities, file sharing, communications and collaboration services, and many more. They contain servers, storage systems, routers, firewalls, and other components which are crucial for the well functioning of the activities mentioned above.
Even in a simple activity such as trying to access a web application via an online browser, there is a client and a data center involved. The client (being any internet user) asks for information, which is obviously held in a data center containing other components as well (being your company digital assets). To perform the activity:
- The client sends the request for access to the data center (communication between the data center and a component out of its boundary)
- The components inside of the data center (application server, database, etc.) prepare the content to send to the client (communication between different components within the data center)
To better express which type of traffic flow pattern is the topic, there are two terms used in the field of security: east-west traffic and south-west traffic.
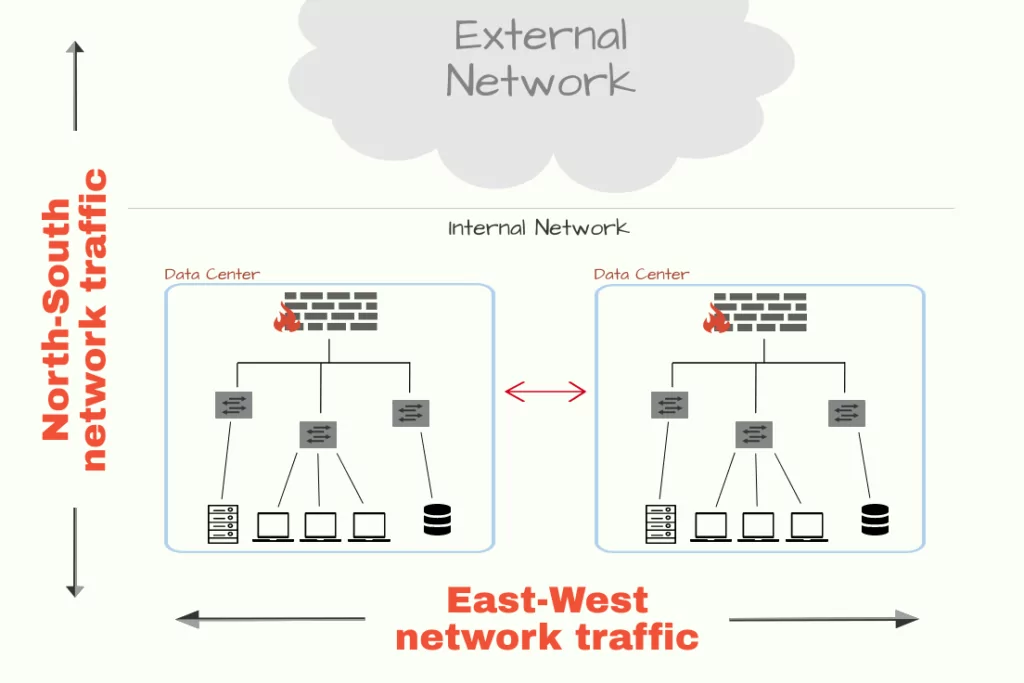
East-West traffic
Any communication between two or more components of a data center, or even communication between different data centers, is referred to as east-west traffic. For instance, east-west traffic occurs when routers within a data center exchange table information, or when a LAN client communicates with a server in the data center.
Because the usage of virtual systems has grown extensively, and because organizations now prefer private cloud infrastructure more and more, east-west traffic volumes have increased drastically. Nowadays there are many functions and services performed virtually, instead of how they used to – on physical hardware. This can help with many issues, however, the traffic on the network has increased as well, and as a result, there can be latency which impacts network performance.
North-South traffic
Any communication between components of a data center and another system, which is physically out of the boundary of the data center, is referred to as north-south traffic. In simpler words, it is any traffic coming to a data center, or going out of it to another system. That other system can be simply a client requesting access to a web application (as mentioned above).
Traffic coming into the data center through a firewall or other perimeter network device – is referred to as southbound traffic. The opposite of it, traffic going out of the data center is referred to as northbound.
North-south traffic usually includes queries, commands, and data in general, being requested from a data center or stored in one.
Securing your network traffic
Traffic can not be trusted just because it comes from within your physical boundaries. Either coming from within your assets (east-west), or from outside through a perimeter network device (north-south), Traffic is trusted only when all the services are secure.
North-South traffic is usually considered as more dangerous traffic because it comes from outside the perimeter, and that is a logical conclusion. That is why many security solutions focus more on it. However, considering that inside traffic makes the largest part of the whole traffic, it is more than possible that malicious activities can end up going from one service to another.
Why is East-West traffic security important?
Although east-west traffic is the biggest part of all traffic, being inside the physical boundaries of a data center, has led to many organizations considering it as secure and not using security controls to monitor it.
A possible reason why east-west traffic is considered secure is that it is assumed that network firewalls don’t let any nefarious function inside the network. And that is their purpose, to block unauthorized content from getting into the network.
Yet, threat actors find a solution for their actions long before companies think about securing the traffic inside the network. New malware keeps coming up, and as long as security experts do not have the right patch for a vulnerability (in time) threat actors can compromise the systems. After malware gets into the network, firewalls can not do anything about it. Then, as long as the company “trusts” its assets without properly evaluating them, threat actors get to be persistent in their nefarious activities. This includes surveilling the network, getting access to confidential data, and in general causing trouble to business operations, which may, in time, cause a bad reputation.
Insider threats can cause bigger trouble for a company since they are harder to catch and less suspected in the first place – the same goes for inside traffic threats.
What can SOCRadar do about it?
SOCRadar provides proactive protection to companies by tracking every change and risk posed to digital assets. Moreover, it provides actionable insights into future cybersecurity threats with a big data-powered threat investigation module. It assists in searching deeper context, real-time threat investigation, and analysis. Companies can track adversaries to get up-to-date information about various TTPs or see all the vulnerabilities that are being leveraged by those threat actors.
SOCRadar also continuously monitors your attack surface, and besides all, informs in case a vulnerability is found in any of your assets. This way, even if the firewall misses a malware, SOCRadar will be there to help you mitigate the risk before you east-west traffic gets compromised by a threat actor.


































