
EU’s Proposed Reform: Article 45.2 May Allow Member Countries to Decrypt Traffic
The European Union‘s proposed legal reforms have sparked a significant debate among cybersecurity experts, industry organizations, and civil society. Central to this discussion is the proposed update to the bloc’s Electronic Identification, Authentication, and Trust Services (eIDAS) regulations, particularly the introduction of Qualified Website Authentication Certificates (QWACs). While enhancing digital identity and security, this reform has raised concerns about its potential to undermine the foundations of online security and privacy.
More than 300 of the world’s most respected cybersecurity experts have written to EU lawmakers, warning that this proposed reform could fundamentally compromise online security. Industry giants like the Linux Foundation, Cloudflare, and Mozilla have echoed these concerns, labeling the proposed regulations as a “dangerous intervention” that risks disrupting the delicate system of trust underpinning cryptographic certificates on the web.

The heart of the issue lies in the potential for QWACs to allow EU member states to issue cryptographic certificates that web browsers would be legally obligated to accept as valid. This could pave the way for governments to intercept encrypted web traffic globally, which raises profound questions about privacy, security, and the integrity of global internet traffic.
What is Article 45.2?
Article 45.2 is the key component of the European Commission’s proposed eIDAS (Electronic Identification, Authentication and Trust Services) Regulation update. This article specifically addresses the recognition and visibility of Qualified Website Authentication Certificates (QWACs) by web browsers. The Commission’s proposal, as outlined in Article 45, mandates web browsers, predominantly based in the United States, to recognize and make QWACs more visible. This move is seen as an effort to enhance secure and trustworthy information about the entities behind websites, thereby aiming to reduce fraud.

GPT generated image for Article 45.2
We will discuss it at greater length, but QWACs are a type of website authentication certificate governed by the eIDAS Regulation. They are issued by qualified trust service providers (QTSPs) and contain detailed information about the entities issuing and receiving the certificate. The European Telecommunications Standards Institute (ETSI) sets the standards for implementing QWACs, ensuring they meet the necessary criteria.
The revision of the eIDAS Regulation, proposed in 2021, has sparked a significant debate among various stakeholders. The Council’s general approach, adopted in December 2022, did not introduce significant changes to the Commission’s proposal regarding QWACs. However, the European Parliament’s position is still under discussion, with various committees expressing differing views on the amendment of Article 45.
Stakeholders’ concerns include web security issues, conflicting standards, technical neutrality, interoperability, and privacy risks. Notably, cybersecurity researchers, web browser Mozilla, advocacy group EDRi, the American Chamber of Commerce to the EU, and the Internet Society have expressed apprehension that the amendment proposed by the Commission could dramatically weaken web security. They criticize the proposal for potentially giving more power to government-appointed certificate authorities (CAs) and raising serious privacy risks in validating QWACs.
In short, Article 45.2 of the eIDAS Regulation revision proposal represents a significant shift in the web authentication landscape, with potential implications for web security, privacy, and the balance of power between private entities and government-appointed CAs.
What are the QUACKs?
Before diving into Qualified Web Authentication Certificates (QWACs), it’s essential to understand the basics of web certificates. Web certificates, commonly known as SSL/TLS certificates, are digital certificates that authenticate the identity of a website and enable an encrypted connection. They are a crucial component of secure web browsing, ensuring that the data exchanged between a user and a website is private and secure.
Qualified Web Authentication Certificates (QWACs) are a specific type of digital certificate proposed under the EU’s eIDAS regulation. They are intended to provide a higher level of assurance about the website owner’s identity. QWACs are issued by Qualified Trust Service Providers (QTSPs) and are meant to offer a more robust verification process than standard SSL/TLS certificates.
The introduction of QWACs has been a subject of intense debate. Proponents argue that they will enhance trust and security in online transactions by providing more reliable identity verification. However, critics, including cybersecurity experts and organizations like the Internet Society, raise significant concerns. They argue that QWACs could undermine the current system of trust in web certificates. The primary concern is that QWACs, being government-mandated, could be used to facilitate the interception of encrypted web traffic, posing a threat to privacy and internet security.
According to discussions, the current text of Article 45 lacks clarity on the functional differences between QWACs and standard web certificates. This ambiguity could lead to confusion among users and weaken the established trust in the CA infrastructure. Furthermore, the global nature of the browser ecosystem means that once QWACs are implemented, they could be misused by governments outside the EU, potentially leading to a breach of fundamental rights and cybersecurity threats.
What are the Exact Concerns?
The proposed reform under Article 45.2, involving Qualified Web Authentication Certificates (QWACs), or QUACKs as they are colloquially known, raises significant cybersecurity concerns. While the intention behind this reform is to enhance security and trust in digital transactions within the EU, the implementation of such measures could inadvertently introduce new risks and vulnerabilities.
- Centralization of Trust
One of the primary concerns is the centralization of trust. By mandating the use of QWACs, the EU is effectively centralizing the issuance of web certificates to a limited number of providers. This centralization creates a single point of failure, making the system more vulnerable to attacks. If a QWAC provider is compromised, the implications could be far-reaching, affecting a multitude of services and users across the EU.
- Impact on End-to-End Encryption
The reform also poses a threat to end-to-end encryption. By allowing member countries to decrypt traffic, the integrity and confidentiality of communications are at risk. This undermines the foundation of secure digital communication, potentially exposing sensitive data to unauthorized access. The ability to decrypt traffic could be misused, either by state actors or, in the event of a security breach, by malicious entities.
- Potential for Abuse
There is also the risk of abuse of these capabilities by governments. While the intention might be to use decryption capabilities for legitimate purposes, such as law enforcement, the lack of robust oversight raises concerns about privacy and civil liberties. The potential for surveillance and the misuse of personal data is a significant concern, especially in light of past incidents where government surveillance has overreached.
- Technical Challenges and Costs
Implementing QWACs across the board will be technically challenging and costly. It requires significant changes to existing infrastructure and systems, which could be particularly burdensome for smaller businesses and organizations. Additionally, the technical complexity of managing these certificates and ensuring their security could lead to increased vulnerabilities, especially if not managed correctly.
- Further Implications
Some even say that, The EU’s mandate for browsers to trust certificates from government-appointed CAs could affect users globally, not just within the EU. Instead of enhancing security, this requirement might compel the integration of a feature that could hinder security for internet users both inside and outside the EU. This could lead to increased vulnerability to slow security responses, privacy breaches, and targeted malware due to reliance on these EU-mandated CAs.
Trust Services Forum – CA Day 2021 (eff.org)
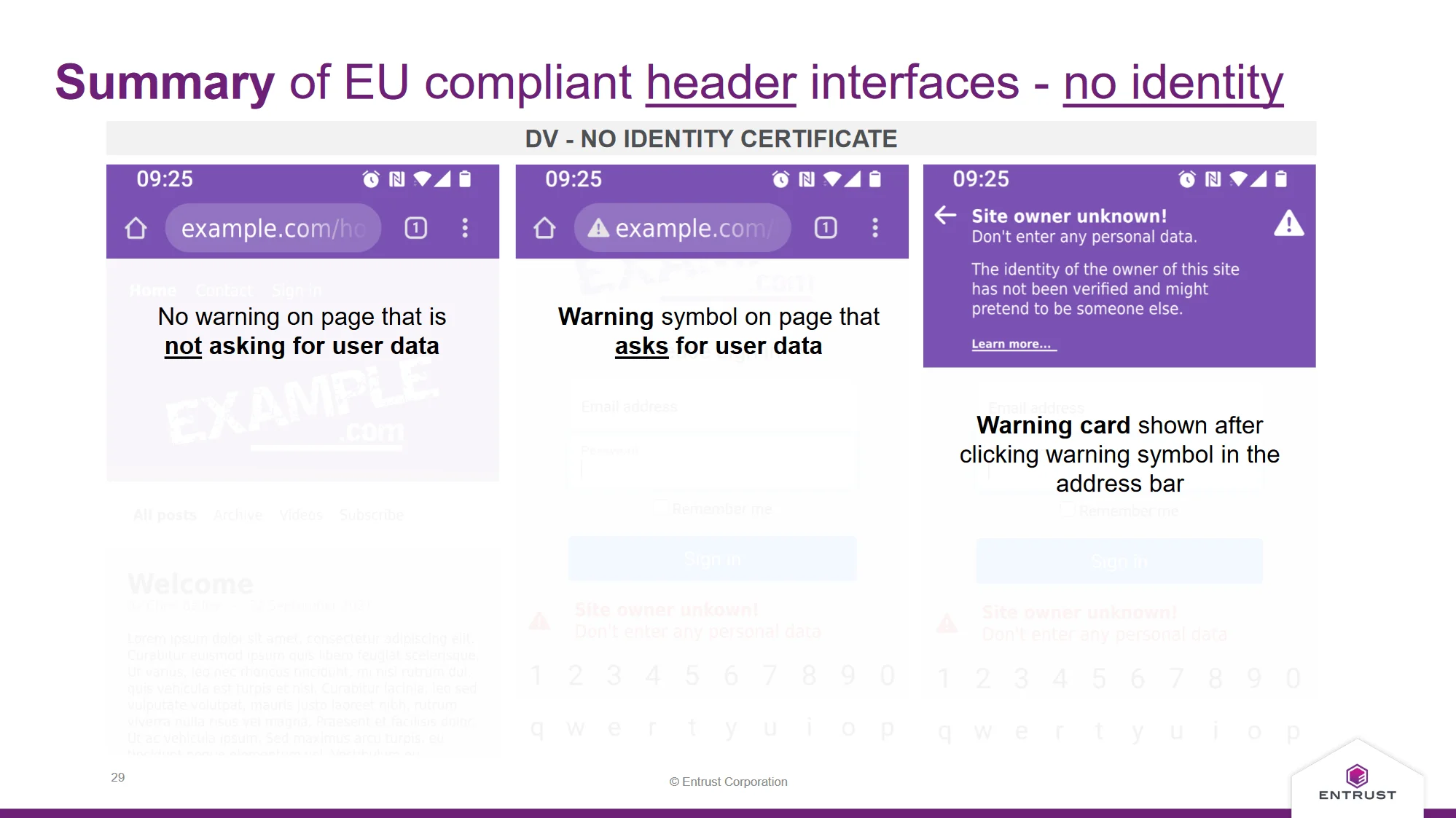
Entrust has proposed a Certificate Authority (CA) that browsers should flag any website not utilizing Qualified Web Authentication Certificates (QWACs) or Extended Validation (EV) certificates with a user warning upon data submission.
So, while the EU’s proposed reform under Article 45.2 aims to enhance digital security, it is crucial to carefully consider the potential cybersecurity risks it introduces. The centralization of trust, impact on end-to-end encryption, potential for abuse, and technical challenges present significant dangers that need to be addressed to ensure that the reform does not compromise the security and privacy of EU citizens.
Conclusion
The EU’s proposed Article 45.2 and the introduction of QWACs present a complex challenge, balancing enhanced digital security against potential privacy and internet integrity risks. While the intent to strengthen digital trust is clear, the implications of centralized trust, potential decryption capabilities, and the technical hurdles involved warrant a cautious approach. It’s essential for policymakers, cybersecurity experts, and stakeholders to collaboratively ensure that these reforms do not undermine the foundational principles of internet security and individual rights. The future of digital identity and security in the EU hinges on striking this delicate balance.




































