Critical Fortinet Vulnerability (CVE-2024-48887) Puts FortiSwitch Admin Credentials at Risk
A newly disclosed critical vulnerability in Fortinet’s FortiSwitch product line is raising urgent security concerns. Tracked as CVE-2024-48887, this flaw enables remote, unauthenticated attackers to change administrator passwords without any prior access – a serious breach risk for enterprises relying on FortiSwitch for network infrastructure.
What Is CVE-2024-48887?
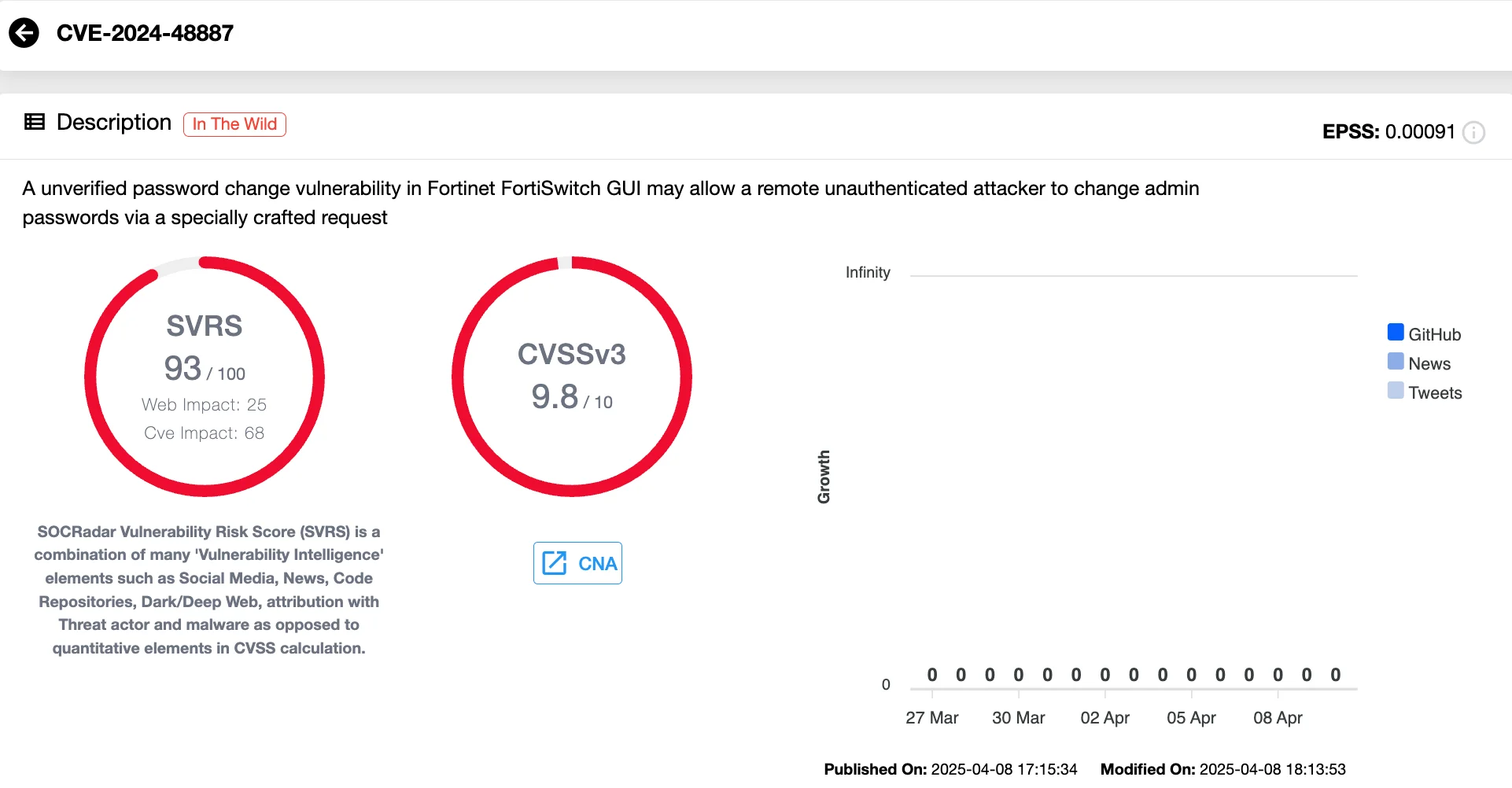
CVE-2024-48887 (CVSS 9.8) is an unverified password change vulnerability found in the FortiSwitch web-based GUI. The issue arises due to insufficient input validation on the set_password endpoint, allowing malicious actors to send specially crafted HTTP requests that bypass authentication altogether.
Attackers exploiting this flaw could easily hijack administrative control, manipulate configurations, or pivot further into internal networks.
Which FortiSwitch Versions Are Affected?
According to Fortinet’s official advisory, the vulnerability impacts the following versions of FortiSwitch:
- 7.6.0 (Patch to 7.6.1 or later)
- 7.4.0 to 7.4.4 (Patch to 7.4.5+)
- 7.2.0 to 7.2.8 (Patch to 7.2.9+)
- 7.0.0 to 7.0.10 (Patch to 7.0.11+)
- 6.4.0 to 6.4.14 (Patch to 6.4.15+)
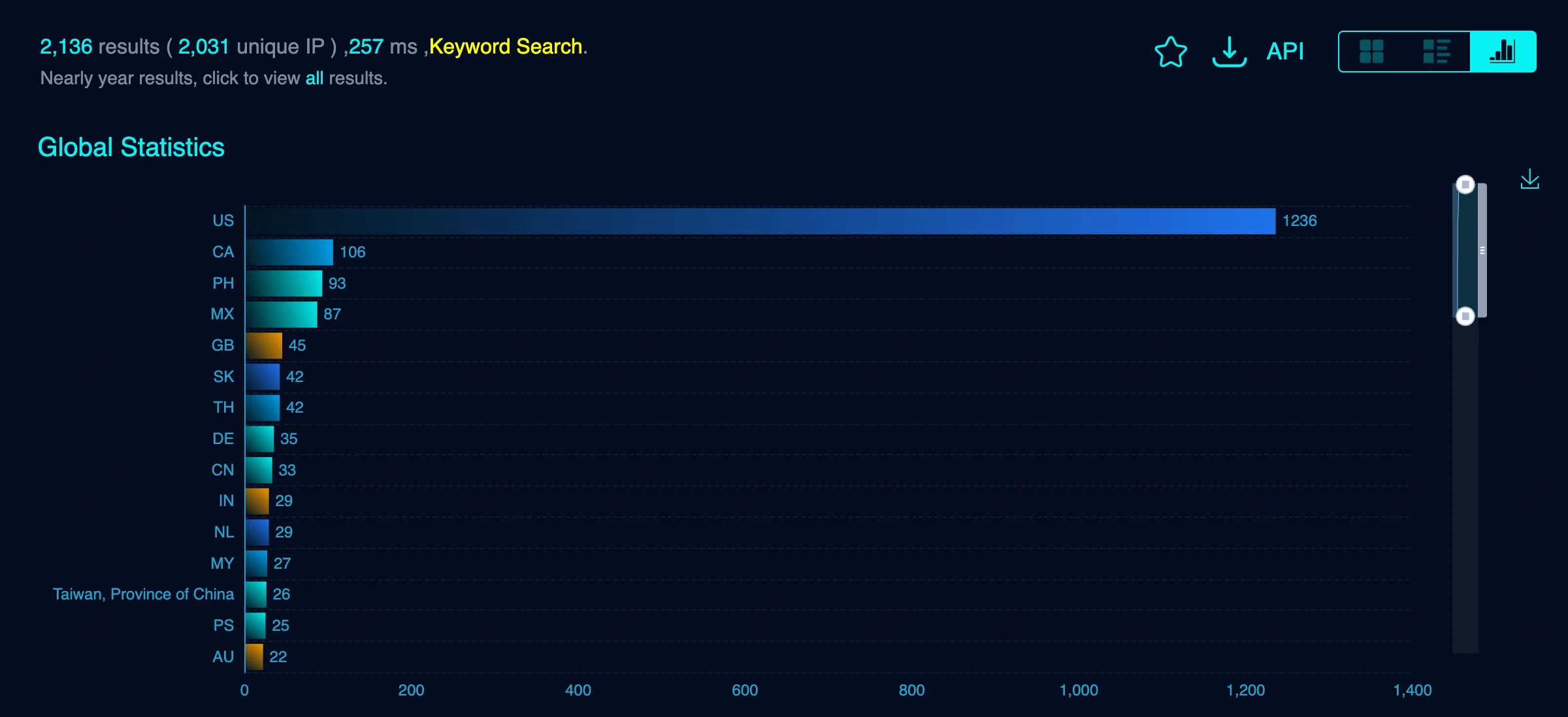
A FOFA search on FortiSwitch reveals over 2,000 internet-exposed instances, with the majority located in the United States. This level of exposure emphasizes the urgency of patching CVE-2024-48887, especially for organizations with publicly accessible FortiSwitch interfaces.
Technical Details: How the Exploit Works
The vulnerability originates from improper input validation in the FortiSwitch web interface. A remote attacker can exploit the flaw by crafting HTTP requests that inject commands or trigger an unverified password reset. The attacker does not need any prior authentication, which makes this vulnerability especially dangerous in exposed or improperly segmented environments.
Once access is gained, attackers may:
- Modify admin credentials
- Execute unauthorized configuration changes
- Move laterally across internal networks
Although there’s currently no evidence of active exploitation, past Fortinet vulnerabilities have quickly become tools in threat actors’ arsenals. The nature of this vulnerability – unauthenticated access with administrative impact – makes it a high-priority risk.
Organizations that delay patching could unknowingly expose themselves to data breaches, network compromise, or even ransomware.
To reduce exposure to risks like this, you should maintain continuous visibility into your organization’s digital assets, vulnerabilities, and misconfigurations. Explore SOCRadar’s Attack Surface Management (ASM) module to uncover exposed assets, detect unpatched vulnerabilities, and prioritize remediation efforts before attackers have a chance to exploit them.
Best Practices & Temporary Mitigations Until You Patch
It is always recommended to:
- Enable MFA where possible.
- Review logs for password changes and suspicious GUI activity.
- Monitor traffic for unusual HTTP requests to the FortiSwitch interface.
Also, while patching is the only complete fix, Fortinet has recommended the following mitigations if updating is not feasible:
- Disable HTTP/HTTPS GUI access on administrative interfaces.
- Restrict access to trusted hosts using CLI:
config system admin
edit <admin_name>
set {trusthost1 | trusthost2 | trusthost3 | trusthost4 |
trusthost5 | trusthost6 | trusthost7 | trusthost8 | trusthost9
| trusthost10} <address_ipv4mask>
next
end
Additional Fortinet Vulnerabilities Disclosed
Alongside CVE-2024-48887, Fortinet published two additional security advisories addressing high-severity vulnerabilities:
- CVE-2024-54024 (CVSS 7.2) – An OS command injection vulnerability in FortiIsolator’s GUI diagnose feature could let super-admin users execute unauthorized code. Read advisory
- CVE-2024-26013 (CVSS 7.5) & CVE-2024-50565 (CVSS 3.1) – A certificate verification issue affecting FGFM connections in FortiOS, FortiProxy, and others could expose devices to impersonation attacks via Man-in-the-Middle (MiTM) positioning. Read advisory
These advisories reinforce the need for rapid patching and strong authentication practices in Fortinet environments.
Staying on top of newly disclosed vulnerabilities is critical, but not all CVEs pose the same level of risk to your environment. With SOCRadar’s Vulnerability Intelligence, part of the Cyber Threat Intelligence module, you can monitor emerging threats, analyze exploit trends, map vulnerabilities to your tech stack, and receive real-time alerts for high-risk exposures. Leverage actionable intelligence to make faster, risk-based patching decisions and strengthen your defense posture.