GitLab Issues Security Patch in April 2025
GitLab has issued a new patch release covering versions 17.11.1, 17.10.5, and 17.9.7 for both the Community Edition (CE) and Enterprise Edition (EE), introducing critical security fixes and multiple bug patches. All self-managed GitLab users are strongly advised to update their instances immediately to mitigate exploitable vulnerabilities that pose significant security risks.
GitLab.com and GitLab Dedicated customers are already on the latest version and require no further action.
High-Severity Security Vulnerabilities Addressed
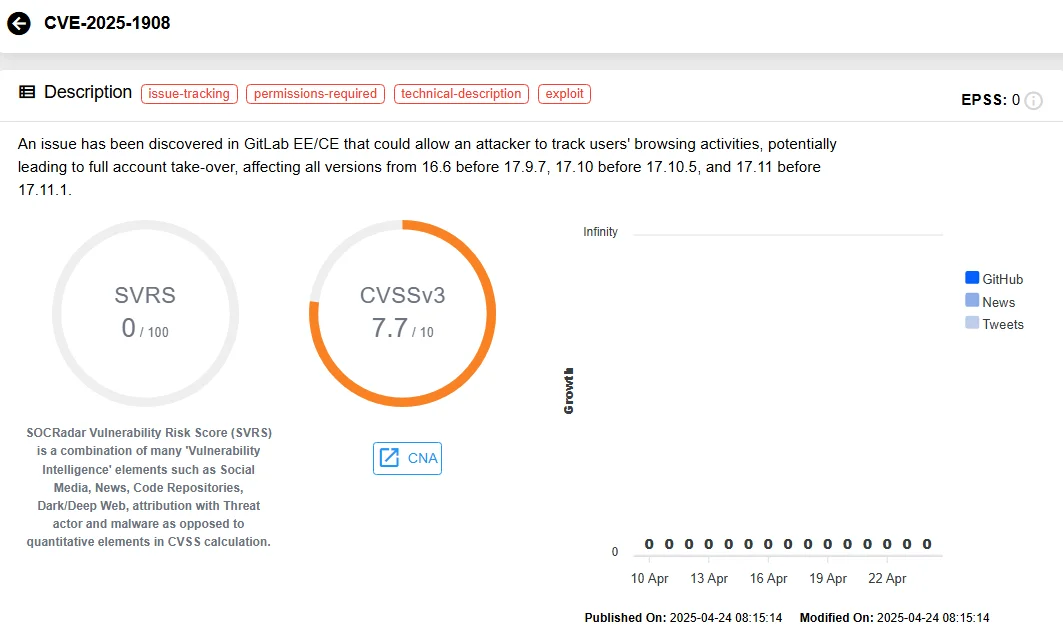
The patch resolves five security vulnerabilities, including three high-severity XSS flaws in the Maven Dependency Proxy and one Network Error Logging (NEL) header injection issue that may allow browser activity tracking. These issues impact GitLab versions as early as 16.6, and are now resolved in the latest updates.
| Vulnerability | CVE | Severity |
| XSS in Maven Dependency Proxy via CSP directives | CVE-2025-1763 | High |
| XSS in Maven Dependency Proxy via cache headers | CVE-2025-2443 | High |
| NEL Header Injection in Maven Dependency Proxy | CVE-2025-1908 | High |
| DoS via Issue Preview | CVE-2025-0639 | Medium |
| Unauthorized Access to Branch Names | CVE-2024-12244 | Medium |
- Two Cross-Site Scripting (XSS) Vulnerabilities (CVE-2025-1763, CVE-2025-2443): These high-severity flaws in the Maven Dependency Proxy could be exploited via manipulated CSP directives or cache headers, affecting GitLab versions from 16.6 up to the latest patches.
- NEL Header Injection Risk (CVE-2025-1908): A vulnerability in the handling of Network Error Logging (NEL) headers could enable threat actors to monitor browser activity and potentially hijack user accounts.
Bug Fixes Across All Patched Versions
Alongside security improvements, the updates include numerous bug fixes enhancing system stability and usability:
Version 17.11.1
- Improvements to Cloud Connector token syncing.
- Amazon Q integration fixes.
- Enhanced CI Inputs handling.
- Workhorse Gitaly client dependency updates.
Version 17.10.5
- Mailroom and UBI pipeline path fixes.
- Improved Zoekt indexing behavior and error handling.
- Session and cookie cleanup enhancements.
Version 17.9.7
- Stability improvements for FIPS and UBI pipelines.
- Finalization of database partitioning migrations.
- Enhanced error handling for GitLab doctor tasks.
Recommended Actions
SOCRadar urges organizations managing their own GitLab instances to:
- Immediately apply the latest patch release for your version stream (17.9.x, 17.10.x, or 17.11.x).
- Review and follow GitLab’s update instructions to ensure a smooth upgrade process.
- Audit your environment for any signs of exploitation or misconfiguration, particularly if delayed in applying updates.
To stay informed about GitLab patch releases, users can subscribe to GitLab’s patch release RSS feed.
Stay Ahead of Threats with SOCRadar
Tracking vulnerabilities in widely used DevOps platforms like GitLab is essential for reducing the attack surface and maintaining cyber hygiene. With SOCRadar’s Vulnerability Intelligence and Digital Risk Protection modules, organizations can gain real-time alerts on exploited CVEs, asset exposure, and patch recommendations across their tech stack.