
GNU C Library Affected by Several Vulnerabilities, Attackers Could Obtain Root Access (CVE-2023-6246)
Researchers have recently discovered several vulnerabilities in GNU C Library (glibc), impacting various Linux distributions. One of them, CVE-2023-6246, poses a significant risk, potentially granting unauthorized root access.
GNU C Library, also known as glibc, serves as a critical component of Linux distributions. Given its widespread adoption, the security implications of the newly discovered vulnerabilities could be serious.
Details of the Latest GNU C Library Vulnerability, CVE-2023-6246
CVE-2023-6246, residing in the glibc’s __vsyslog_internal() function, which is called by syslog() and vsyslog(), represents a heap-based buffer overflow vulnerability.
According to Qualys, this vulnerability enables local privilege escalation, allowing an unprivileged user to attain full root access by crafted inputs to applications employing the logging functions syslog() and vsyslog().
CVE-2023-6246 was introduced inadvertently in glibc 2.37 in August 2022 by a specific commit, also backported to glibc 2.36; the commit was initiated as a fix for a previous memory read vulnerability (CVE-2022-39046).
Major Linux distributions like Debian (versions 12 and 13), Ubuntu (23.04 and 23.10), and Fedora (37 to 39) are confirmed to be vulnerable to CVE-2023-6246, as researchers note that it requires specific conditions for exploitation, such as an unusually long argv[0] or openlog() ident argument.
To access timely notifications and comprehensive intelligence to help you address critical vulnerabilities proactively, you can utilize the SOCRadar XTI platform. The Vulnerability Intelligence feature allows users to obtain detailed information on vulnerabilities and monitor related activities, such as hacker trends.
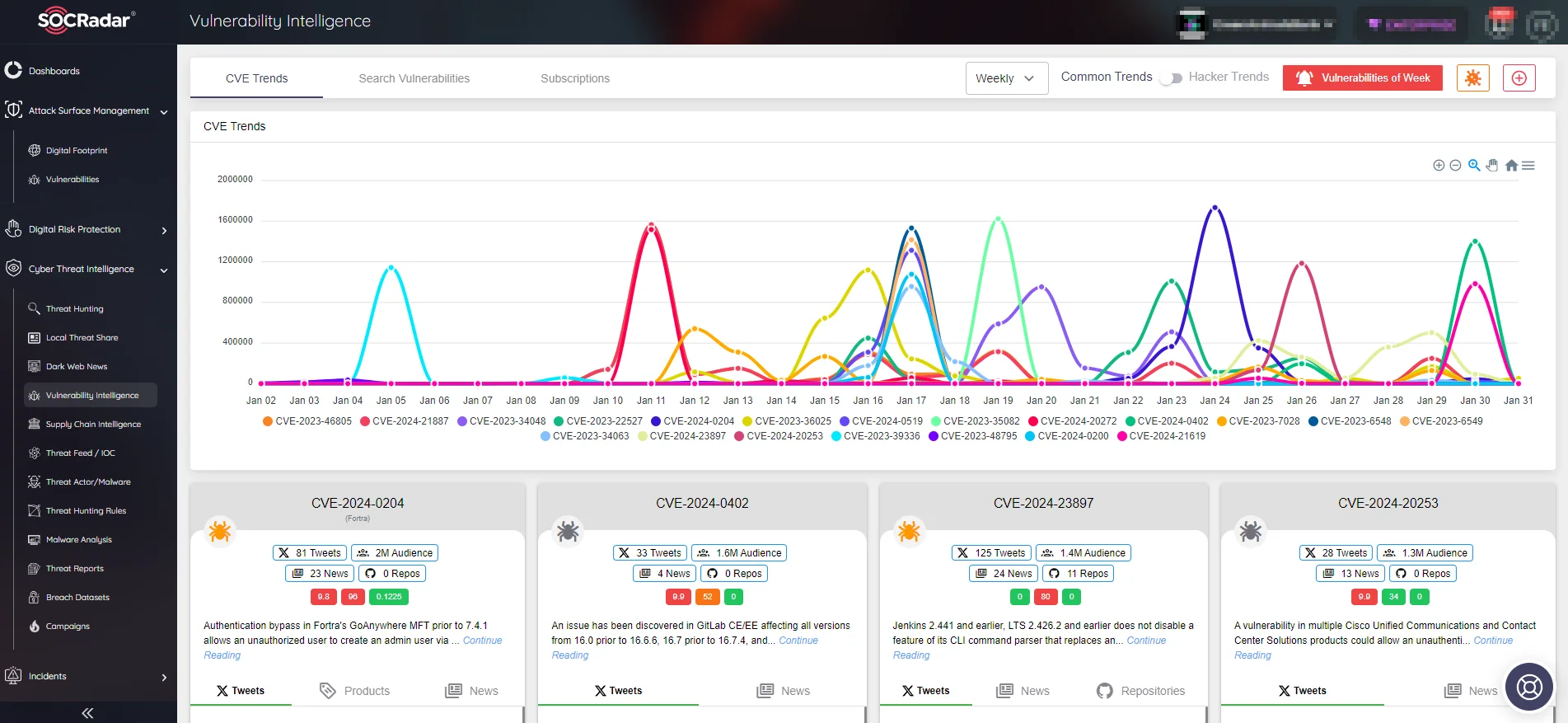
SOCRadar’s Vulnerability Intelligence
Other Vulnerabilities Affecting GNU C Library: CVE-2023-6779, CVE-2023-6780, and a Memory Corruption Issue
Qualys detected additional vulnerabilities while analyzing the __vsyslog_internal() function, namely CVE-2023-6779 (an off-by-one heap-based buffer overflow) and CVE-2023-6780 (an integer overflow vulnerability). Researchers report that these vulnerabilities are more challenging to exploit than CVE-2023-6246.
Furthermore, a vulnerability was discovered in glibc’s qsort() function due to a missing bounds check. The vulnerability is not mentioned with a CVE identifier, but researchers note that it could lead to memory corruption.
This memory corruption vulnerability, which has been present in all versions of glibc since version 1.04 (released in 1992), can occur when qsort() is used with a nontransitive comparison function and a high number of attacker-controlled elements. This circumstance may cause a malloc() failure within qsort(), allowing exploitation.
Monitor Your Attack Surface with SOCRadar
The Attack Surface Management module gives organizations the tools they need to quickly identify, evaluate, and mitigate vulnerabilities, while allowing them to view information about their asset inventory and components, and receive notifications about security issues. These notifications give timely and actionable information, expediting the reaction process.
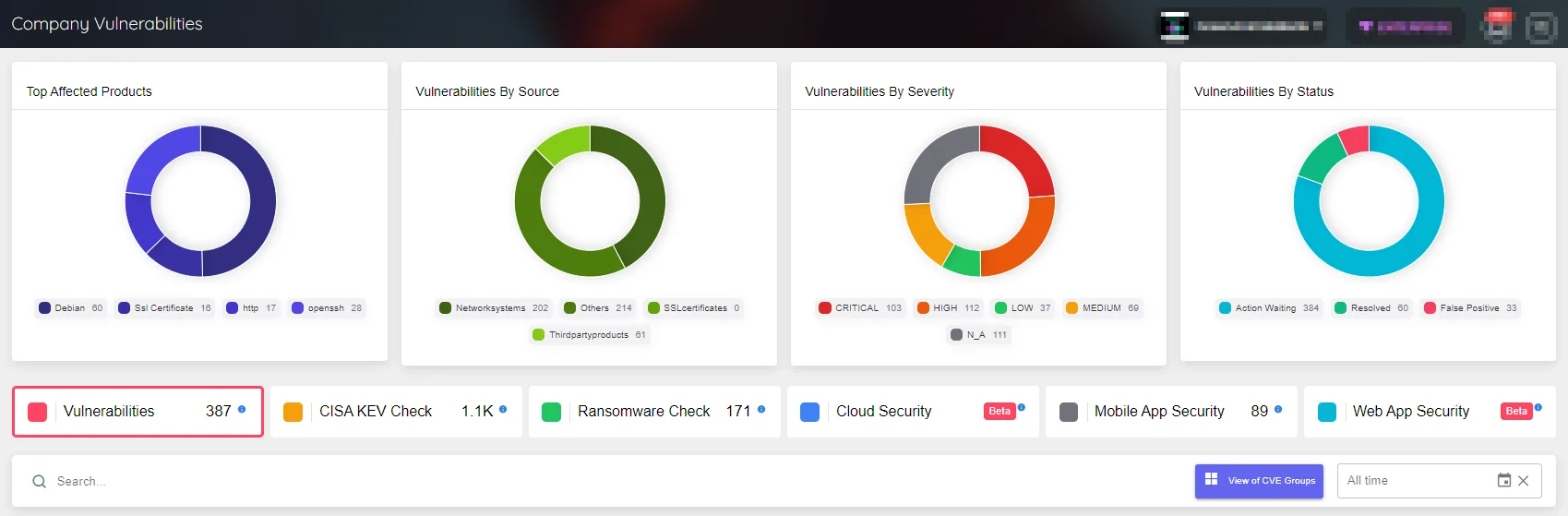
Company Vulnerabilities page under SOCRadar’s ASM

































