
Google’s 2024 Zero-Day Report: Key Trends, Targets, and Exploits
In late April, Google’s Threat Intelligence Group (GTIG) published its annual report on zero-day exploitation, offering a detailed account of in-the-wild attacks observed throughout 2024. The report draws on GTIG’s original breach investigations, technical analysis, and insights from trusted open-source reporting.
GTIG tracked 75 zero-day vulnerabilities that were actively exploited before patches became publicly available. While this represents a drop from the 98 cases reported in 2023, it remains above pre-2022 levels and fits a four-year pattern of sustained activity.
But raw numbers only tell part of the story. As Google’s 2024 Zero-Day Report shows, attackers have shifted from opportunistic broad targeting to more strategic objectives, exploiting vulnerabilities in enterprise software, security appliances, and systems that offer deeper access with fewer detection points. The steady refinement in attacker behavior underscores a difficult reality for defenders: even as vendors improve their response and mitigation capabilities, the bar for staying secure keeps getting higher.
This blog breaks down the key findings from GTIG’s report, exploring who’s exploiting what, which technologies are being hit hardest, and how defenders can respond.
From Browsers to Firewalls, The New Focus of Zero-Day Exploits
One of the most notable trends GTIG observed was a redirection of attacker attention from everyday end-user software to the backbone of enterprise operations.
Google’s 2024 Zero-Day Report details that nearly half (44%) of the tracked zero-day exploits targeted enterprise technologies. These include firewalls, VPN appliances, and security software, which are products that are essential to organizational defenses but often lack monitoring or EDR integration. These high-privilege systems are especially attractive to attackers. Once compromised, they can offer expansive access across networks while flying under the radar.
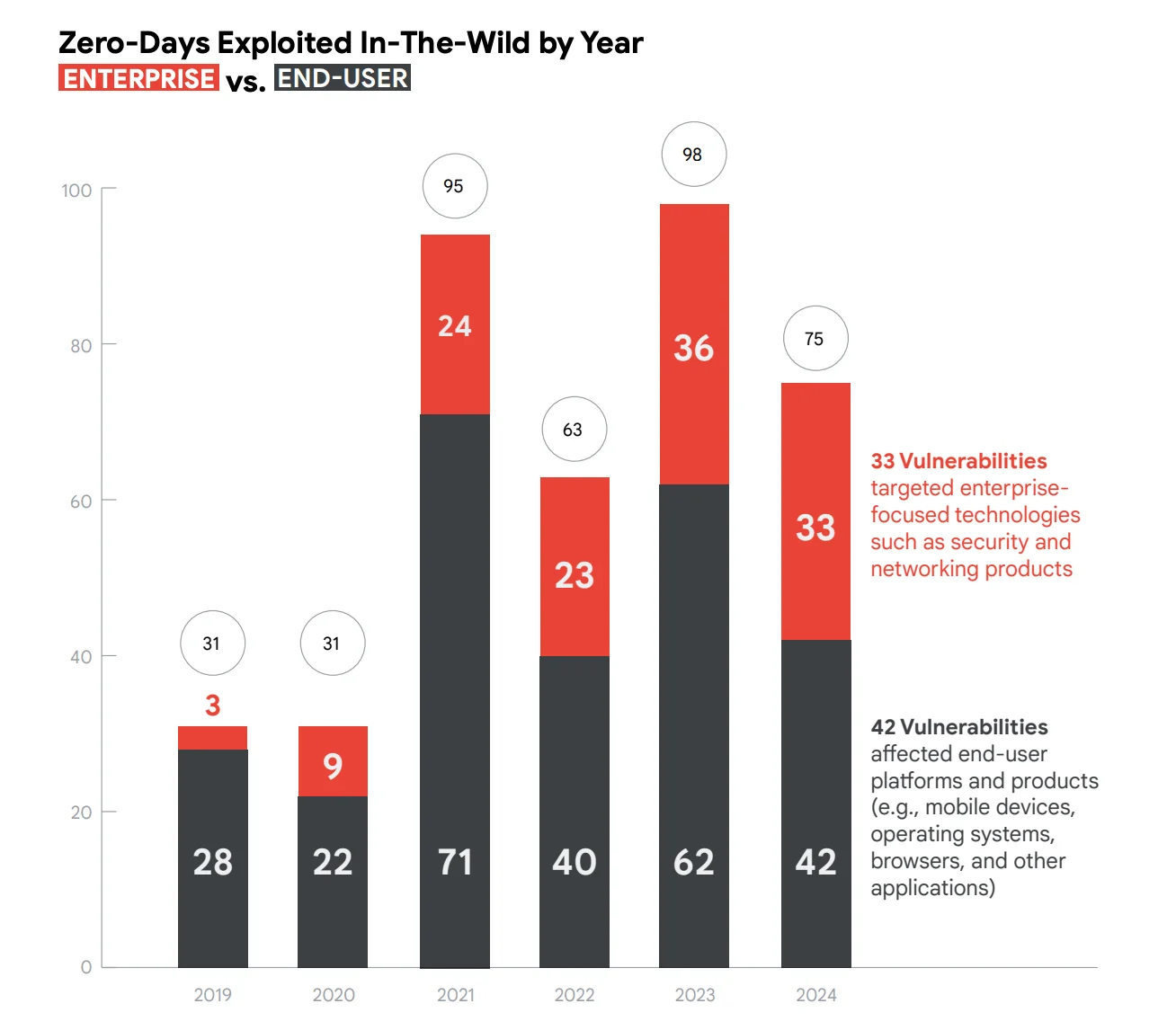
Zero-days used against Enterprise vs. End-Users in 2024 (Google’s 2024 Zero-Day Exploitation Analysis)
Google also noted that while the number of unique enterprise vendors targeted dropped from 22 to 18, those 18 made up 90% of all vendors tracked.
Devices like Ivanti Connect Secure VPNs, Cisco ASA firewalls, and Palo Alto PAN-OS were all among this year’s most frequently targeted technologies. The report highlights that many of these appliances are difficult to monitor and rarely receive the same patching urgency as user-facing software, making them ideal candidates for exploitation.
In contrast, traditional targets like mobile devices and browsers saw notable declines. Browser zero-days dropped from 17 to 11, and mobile zero-days fell from 17 to just 9. GTIG attributes this to stronger exploit mitigations and quicker patch deployment by major vendors like Google and Apple. Still, attackers have not abandoned end-user tech completely – Chrome remained the top browser exploited in 2024.
Recurring Vulnerabilities, Recurring Problems
Despite shifts in attacker strategy, many of the exploited weaknesses in 2024 were far from new. Google’s 2024 Zero-Day Report highlights that use-after-free, command injection, and cross-site scripting (XSS) remain top vulnerability classes, just as they have for years.
- Use-after-free (8 cases): Frequently found in browsers, operating systems, and low-level software. These bugs allow attackers to execute arbitrary code by referencing memory that’s been freed but not yet reallocated.
- Command injection (8 cases): Almost exclusively observed in security and networking appliances. Successful exploitation can grant system-level access – no exploit chain required.
- Cross-site scripting (6 cases): Targeted webmail servers, enterprise tools, and browsers. When paired with clever delivery, XSS can leak sensitive data, steal cookies, or hijack sessions.
For organizations managing high-value systems like VPNs, firewalls, or enterprise software, the takeaway is clear: Preventing the next breach starts with better code and patch management. If these basics go unaddressed, the same vulnerabilities will keep showing up, and attackers will keep exploiting them.
SOCRadar’s Attack Surface Management helps organizations map and monitor high-risk assets, identifying vulnerable systems before attackers do. When VPN appliances and edge devices become the new frontline, proactive mapping and monitoring can make all the difference.
SOCRadar’s ASM module, Company Vulnerabilities
Zero-Days for Hire: Espionage and the CSV Market
While state-backed groups continue to dominate zero-day exploitation, 2024 reaffirmed the growing role of Commercial Surveillance Vendors (CSVs) in this ecosystem. These companies develop and offer exploit chains, often to governments, which are then deployed in targeted surveillance campaigns.
According to Google’s 2024 Zero-Day Report, 8 of the 75 zero-days tracked last year were attributed to CSV customers. That’s slightly down from 2023, but still significantly higher than historical norms. The report notes that CSVs have grown more careful operationally, making attribution harder, but their activity remains a major driver of exploit proliferation.
One of the most striking examples comes from Cellebrite, a forensic tech vendor. Google reported that forensic tools built by such vendors were involved in USB-based zero-day chains (e.g., CVE-2024-53104) that allowed physical unlocking of Android devices. In one case, Serbian authorities reportedly used these capabilities against an activist.
These developments show that zero-days are no longer just the domain of sophisticated APTs. When surveillance capabilities can be purchased and operationalized by clients around the world, the gap between state-sponsored and commercial exploitation continues to narrow.
Attribution Deep Dive – China, North Korea, and Non-State Actors
Behind nearly half of the zero-days tracked in 2024, GTIG could identify specific threat actors. The attribution map shows a mix of state-sponsored espionage, commercial exploit providers, and financially motivated groups with nation-state links.
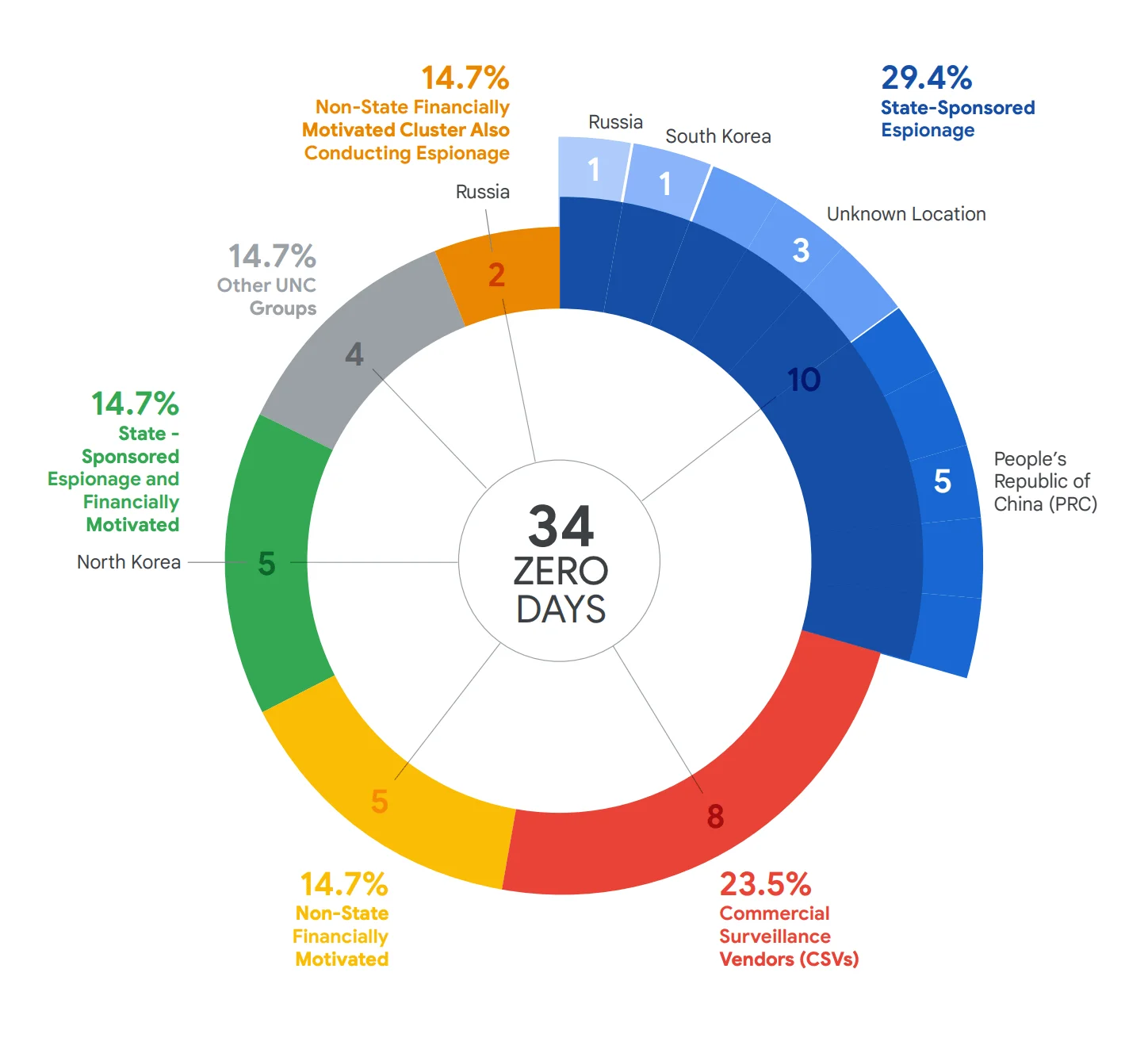
2024 zero-day exploitation attributions (Google’s 2024 Zero-Day Exploitation Analysis)
China-linked groups remained consistent in their focus on network infrastructure:
- Five zero-days were attributed to PRC-backed actors.
- UNC5221 stood out by chaining vulnerabilities in Ivanti appliances (CVE-2023-46805 and CVE-2024-21887).
- These attacks aligned with China’s long-standing preference for targeting VPNs, firewalls, and security devices, typically assets with privileged access and weak monitoring.
North Korea matched China in zero-day volume:
- Five zero-days were attributed to North Korean actors.
- Targets included both espionage (Chrome) and financially motivated attacks (Windows-based privilege escalation).
- Notable cases included APT37’s suspected abuse of CVE-2024-38178 in a malvertising campaign, and CVE-2024-21338 to disable endpoint defenses using a vulnerable Windows driver.
Google identified multiple non-state, financially motivated groups leveraging zero-days, some with possible state ties:
- FIN11 exploited CVE-2024-55956 in Cleo file transfer software, continuing a three-year pattern of abusing enterprise-grade MFT solutions for extortion.
- CIGAR/UNC4895 deployed a Firefox-to-Windows SYSTEM exploit chain (CVE-2024-9680 & CVE-2024-49039), likely for espionage and financially driven campaigns, potentially on behalf of Russian interests.
Notable Discoveries by Google
Beyond aggregate trends and attribution data, Google’s 2024 Zero-Day Report also shares several hands-on discoveries from GTIG’s own investigations. Here’s a quick look:
- Diplomatic Academy of Ukraine (MacOS WebKit Exploit):
GTIG found a JavaScript-based zero-day embedded in the Diplomatic Academy’s website. It exploited WebKit flaws (CVE-2024-44308 & CVE-2024-44309) on Intel Mac devices to steal cookies, including those tied to login.microsoftonline.com. - CIGAR’s Firefox + Windows SYSTEM Exploit Chain:
A use-after-free in Firefox (CVE-2024-9680) was combined with a Windows privilege escalation zero-day (CVE-2024-49039), allowing full SYSTEM access. The attack abused RPC weaknesses in Windows’ WPTaskScheduler. - Exploit Reuse on a Compromised Crypto News Site:
Another threat actor deployed the exact same Firefox and Windows exploits via a watering hole on a cryptocurrency news platform, underscoring how high-value zero-days get recycled across campaigns.
Monitoring exploit chatter, attack surfaces, and leaked credentials can help spot these campaigns early. With SOCRadar’s Cyber Threat Intelligence and Dark Web Monitoring modules, you can trace adversary infrastructure, identify leaked assets, and respond to active exploitation faster.
Monitor exploit shares and more with SOCRadar’s Dark Web News
Conclusion
Google’s 2024 Zero-Day Report highlights a shift in how exploitation is evolving, not necessarily in volume, but in precision. Threat actors are focusing on high-impact enterprise technologies like VPNs, firewalls, and security appliances, where visibility is low and privileges are high.
Even as vendors improve defenses, attackers continue to rely on long-standing flaws like use-after-free, command injection, and cross-site scripting – exploits rooted not just in code, but in decisions about how that code is built and maintained.
Defending against this reality requires more than fast patching. It calls for:
- Secure development practices and code audits
- Zero-trust implementation at all layers
- Proactive monitoring of critical infrastructure
- Context-rich threat intelligence that informs response
Platforms like SOCRadar help organizations respond faster by mapping exposures, tracking attacker infrastructure, and surfacing relevant threat signals. And with SOCRadar Labs CVE Radar, you can freely explore trending vulnerabilities, exploits, IOCs, and real-time chatter – a window into the most active CVEs shaping today’s risk environment.
CVE Radar – Explore more free tools at SOCRadar Labs
For more information, you can read Google’s full 2024 Zero-Day Exploitation Trends report here.




































