Google’s Response to Pixel Zero-Days: CVE-2024-29745, CVE-2024-29748; Chrome V8 Zero-Day, CVE-2024-3159
[Update] April 5, 2024: “CISA Urges Immediate Action on Pixel Zero-Day Vulnerabilities”
Google addressed two zero-day vulnerabilities affecting Google Pixel devices, which are reportedly under exploitation.
Despite the Android April 2024 updates not including any severe issues, the Pixel-specific bulletin revealed active exploitation of CVE-2024-29745 and CVE-2024-29748.
Notably, the only critical vulnerability in the Android security bulletin was CVE-2023-28582, concerning a memory corruption in Data Modem with a CVSS score of 9.8.
April 2024 Google Pixel Updates: One Critical, Two Zero-Day Vulnerabilities
The April 2024 updates for Pixel devices addressed 24 vulnerabilities; among them, the only critical vulnerability is CVE-2024-29740, which was classified as an elevation of privilege issue.
Additionally, Google flagged two high-severity zero-day vulnerabilities, CVE-2024-29745 and CVE-2024-29748, with indications of limited, targeted exploitation.
![]()
CVE-2024-29745 and CVE-2024-29748 may be under exploitation (April 2024 Pixel Security Bulletin)
CVE-2024-29748 concerns an elevation of privilege vulnerability in the firmware, whereas CVE-2024-29745 relates to an information disclosure issue in the bootloader. It is reported that forensic firms have been exploiting these vulnerabilities to circumvent PIN protection and gain access to stored data.
What is CVE-2024-29745? How is it exploited?
CVE-2024-29745 denotes a vulnerability within the fastboot firmware, utilized for tasks like unlocking, flashing, and locking devices. Forensic firms exploit this vulnerability by rebooting devices, such as Pixels, into fastboot mode after the first unlock, enabling them to exploit vulnerabilities and extract memory data.
GrapheneOS suggested a solution involving memory zeroing in the firmware during reboot to fastboot mode, aiming to thwart such attacks entirely. Google adopted this proposal, ensuring memory is zeroed upon booting into fastboot mode.
Consequently, USB access is only enabled after memory zeroing is completed, effectively blocking these exploitation attempts.
What is CVE-2024-29748?
CVE-2024-29748 involves a flaw allowing the interruption of a factory reset initiated by a device admin app.
While Google’s firmware fix addressed part of the issue, GrapheneOS pointed out that it remains possible to halt the wipe by cutting power to the device.
In response, GrapheneOS is developing a more comprehensive solution. This includes implementing a stronger duress PIN/password feature and a secure ‘panic wipe’ action that can be executed without the need for a device reboot.
How critical are CVE-2024-29745 and CVE-2024-29748?
While the severity scores for the zero-day vulnerabilities, CVE-2024-29745 and CVE-2024-29748, have not been officially assigned, currently, these vulnerabilities have a SOCRadar Vulnerability Risk Score (SVRS) of 38, signaling heightened discussion and potential exploitation risks.
Exploitation of Google Pixel Zero-Day Vulnerabilities
On X, security researchers at GrapheneOS, a privacy and security-focused mobile OS compatible with Android apps, stated that forensic companies actively exploited these Pixel zero-day vulnerabilities. This is because they enable companies to unlock and access memory on Google Pixel devices when they have physical access.
Initially discovered and reported by GrapheneOS in January 2024, the specifics of the vulnerabilities were not disclosed to prevent exploitation before a patch was available.
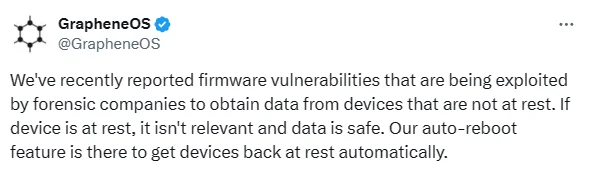
Disclosure by GrapheneOS for vulnerabilities’ exploitation (X)
Despite the researchers’ efforts to keep the details under wraps, the vulnerabilities are being exploited, leading to zero-day attributions.
For real-time monitoring of CVE and exploitation trends, leverage SOCRadar’s Vulnerability Intelligence. With its extensive database and advanced analytics, you can track updates, detect exploits, and receive actionable insights for proactive vulnerability management.
SOCRadar’s Vulnerability Intelligence
CISA Urges Immediate Action on Pixel Zero-Day Vulnerabilities
On April 4, 2024, CISA included the Pixel zero-day vulnerabilities CVE-2024-29745 and CVE-2024-29748 in its Known Exploited Vulnerabilities (KEV) Catalog.
Exploiting these vulnerabilities allows attackers to extract memory data and elevate privileges, posing serious threats. Such vulnerabilities are frequently targeted by threat actors and also pose risks to the federal enterprise.
Organizations and federal agencies are urged to address these severe vulnerabilities affecting Pixel phones by the April 25, 2024 deadline to mitigate the risk of exploitation.
How can you patch the Pixel zero-days, CVE-2024-29745 and CVE-2024-29748?
For Pixel users, addressing these security vulnerabilities requires installing the security patch level of 2024-04-05. To do so, follow these steps:
- Navigate to Settings on your Pixel device.
- Select Security & privacy.
- Go to System & updates.
- Choose Security update.
- Tap on Install and follow the on-screen prompts.
- Restart your device to complete the update process.
Google Tackles Chrome V8 Zero-Day Demonstrated in Pwn2Own: CVE-2024-3159
Google recently addressed yet another zero-day vulnerability, identified as CVE-2024-3159, a high-severity out-of-bounds issue. This vulnerability targets Chrome’s V8 JavaScript engine and was showcased during Pwn2Own 2024 Vancouver.
Exploitation of CVE-2024-3159 allows remote attackers to access data beyond the memory buffer through crafted HTML pages, leading to heap corruption. This could potentially result in the exposure of sensitive information or system crashes. The vulnerability carries a CVSS score of 9.8, indicating a critical risk.
Exploiting out-of-bounds vulnerabilities typically demands a level of expertise due to their complexity and the intricacies involved in manipulating memory beyond its intended bounds. Security researchers Edouard Bochin and Tao Yan successfully demonstrated a novel technique to exploit CVE-2024-3159, bypassing V8 hardening mechanisms and achieving arbitrary code execution in the renderer.
Google has addressed this zero-day in the stable channel version 123.0.6312.105/.106/.107 for Windows and Mac, and 123.0.6312.105 for Linux. These updates will be rolled out globally in the coming days.
Organizations can leverage SOCRadar’s vulnerability detection capabilities to identify and assess vulnerabilities in their systems. The platform offers real-time alerts for critical vulnerabilities or exploits affecting defined product components and digital technologies.
SOCRadar’s Attack Surface Management




































