Hackers Exploit WinRAR SFX Archives to Install Backdoors Undetected
Threat actors exploit WinRAR self-extracting (SFX) archives containing decoy files by adding malicious functionality to install backdoors in target systems without detection.
SFX archives involve a decompressor stub allowing users to decompress and view the contents without additional software. Compressor software like WinRAR and 7-Zip use SFX technology to make it easier to distribute software and files.
For SFX, WinRAR provides advanced options like the ability to execute commands both before and after setup and to overwrite any existing files or directories in the target directory.
The attack does not require the target user to have WinRAR or any other compression software, as SFX files are designed to grant access to contents to these users as well.
SFX archives have been used for legitimate purposes for a long time. Security detections may miss hidden malicious functionality within these archives. Researchers have discovered that an apparently empty SFX archive file can be risky, too, as it may provide hackers with a persistent backdoor to a victim’s environment when combined with a specific registry key.
Password-Protected SFX Archives Used as Backdoor by Attackers
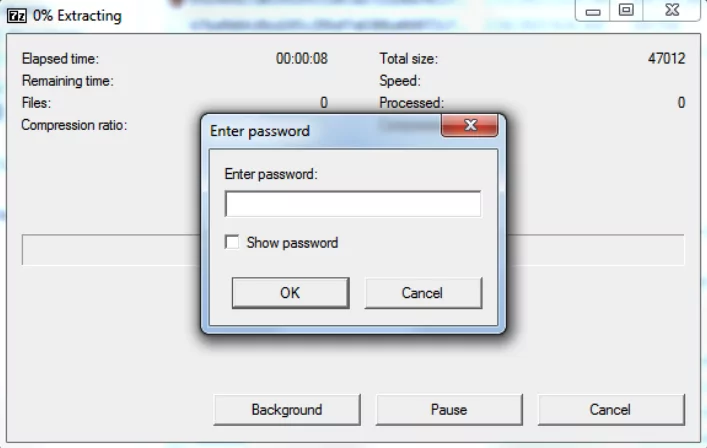
It is common for businesses to use password-protected SFX archives. These archives are encrypted using commercial products and can only be accessed with the correct password. Once the password is entered, the file becomes an SFX archive with an executable extension.
Recently, threat hunters discovered that an attacker used compromised credentials to gain access to a system and tried to establish persistence by setting up an Image File Execution Options debugger in the Windows registry.
reg add "HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindows NTCurrentVersionImage File Execution Optionsutilman[.]exe" /v "debugger" /d "[REDACTED PathToSFXArchive]" /fThe attacker used a command line to configure the debugger in the Windows registry so that whenever utilman[.]exe (an accessibility application) was run, it would pass it as a parameter to the specified debugger executable.
Attackers often abuse utilman[.]exe to run a binary of their choice without authenticating, bypassing security measures. Binaries run through this method have elevated privileges as they are executed under the local system account (NT AUTHORITYSYSTEM). This allows the execution of commands with higher privileges than a standard administrator account.
While this technique of abusing utilman[.]exe is not new, what was unusual in this case was that the binary being pointed to was an SFX archive that was password-protected, making it impossible to unarchive without the correct password.
WinRAR SFX archive files include a feature that allows to include extended SFX commands that will run once the file is unarchived. There is a setup option in these commands to specify the executables.
Attackers usually exploit the feature to execute malware contained within an SFX archive. Although this attack does not include malware, the threat actor added commands under the WinRAR setup menu to make the archive function as a password-protected backdoor.
The commands ensure that the decompressor stub can overwrite existing files when extracting, hides dialogs (via silent command), and execute PowerShell, command prompt, and task manager after the process is completed.
Traditional antivirus software may not be able to detect this type of attack because it does not involve any malware behavior to detect.
Recommendations
To prevent such attacks, some suggestions are as follows:
- Use unarchiving software or other tools to examine SFX archives for potential scripts or executables set to extract and run upon execution.
- Examine the SFX archive decompressor stub itself to identify any commands that will be run during, before, or after successful extraction rather than just examining the contents of the archive.
- Carefully inspect any SFX archive that contains only a null-byte file for added functionality.
- Check the registry for if an SFX file is set as a debugger. Look for the following IOC: HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindows NTCurrentVersionImage File Execution Options
One of the ways you can detect malicious activity through your assets is by using indicators of compromise. On SOCRadar’s Threat Feed & IOC Management tab, you can find IOCs and monitor threat actors, malware, and various other malicious activities.