Hackers Utilize AWS to Launch Phishing Attacks
Phishing attacks are being launched by hackers using a tactic called Static Expressway. The newly-spread tactic lets hackers get their emails past Amazon Web Services (AWS) automated security scanners.
Email security provider Avanan claims that scammers can send phishing emails, including the Amazon Web Services’ name, into corporate email systems to get past scanners that otherwise would block suspicious communications and give extra validity to fool targets.
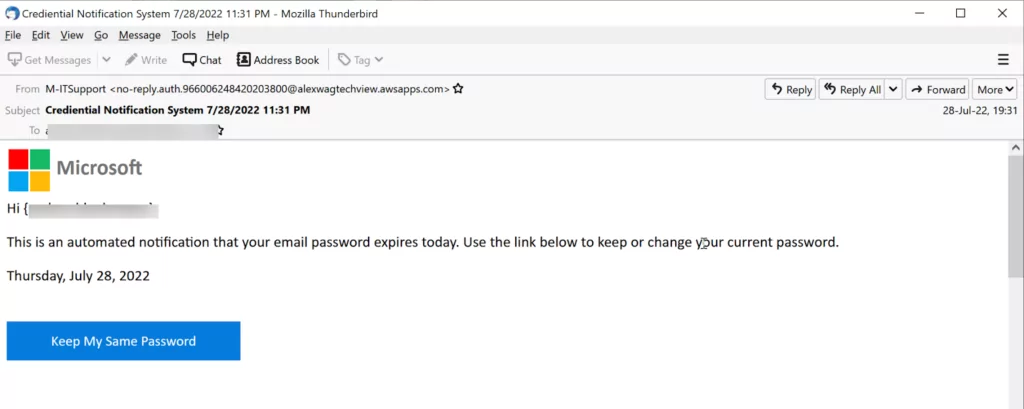
Researchers cited an instance of a tactic in which a cybercriminal used AWS to create and host a phishing message informing receivers that their password would soon expire. The user was instructed to click a button in the email with the Microsoft logo to maintain or change the password.
The Static Expressway Technique
Attacks utilizing the Static Expressway technique have increased significantly recently. This technique lets threat actors enter inboxes by piggybacking on legitimate services.
Attacks leveraging the Static Expressway technique can also affect email services that use static allowlists. Some services are seen as secure in the static allowlist by default, and some services, such as Google, cannot even be blocked. Because a phishing email hosted by Amazon Web Services will be perceived as secure, it can pass the static solution.
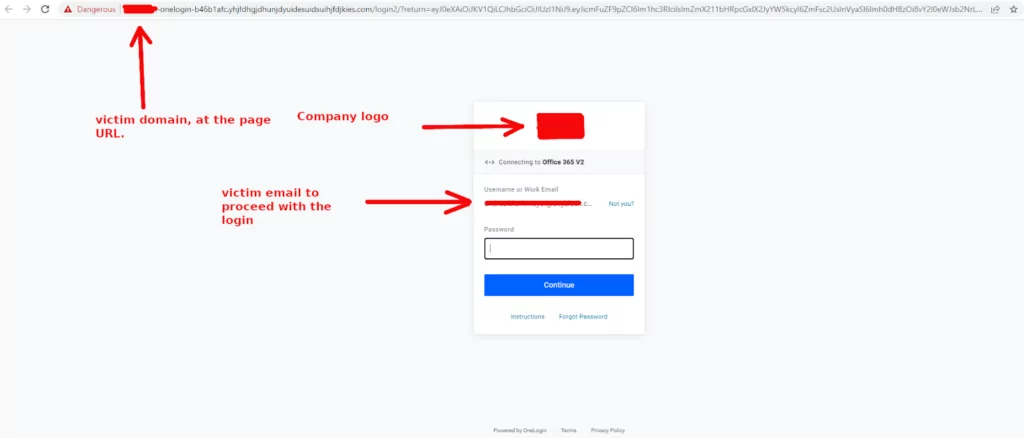
The user’s domain and logo are visible when a user clicks on a malicious link sent by the threat actor. The technique is too widespread to be blocked all at once, and for the hacker to succeed, the user only needs to put minimal effort into entering their password.