
How To Learn Which 3rd Party Libraries Your Website Is Using?
Websites are the most critical assets and most important components of your business. They are a linking bridge between your products and services, and the potential targeted customers. With well designed and properly secured websites, you gain the trust of your users. The opposite will cause your business great damages and reputation loss.

Website monitoring
Threat actors target recent vulnerabilities in the system to check for misconfigurations in the website or the web application code. This way they can get access to your website and finalize it with exploitation. They can steal company data, user information like payment data, personal credentials, and passwords, inject spam, and perform other actions that can harm both the company and the end-users. Some of the most common cases are seen in the e-commerce and financial sectors, but we can’t say other sectors are safe, especially now that websites are one of the essentials for a successful business. As the business grows, so does the risk of your websites, and other digital assets as well. This makes it crucial for businesses to assure limiting and preventing damages before they occur. But can a company do that, when there are many third-party components used to build the websites?
Third-party components usage in websites
A third-party component is a software developed by an entity that can be distributed as an open-source or commercial component (sold) to other entities who can reuse it to develop, in this case, a website. Using third-party components, like web servers, frameworks, or libraries, makes the development process easier for the developer because they allow them to use already tested software. Hence, time and sometimes the cost of development is automatically saved.

Why are third-party components important to monitor
In this case, you need to answer this question first: what if the vendor (developer of the component) updates the third-party component?
Website developers are not usually notified of new updates, so there might be security issues in the older versions they are using. For this reason, they need to catch up with the technologies their websites are utilizing and be up-to-date. Unless done so, they can end up not only with lower performance but also with security and privacy issues which can lead to bigger company problems – bad reputation and GDPR fines.
Mostly for security reasons, companies need to know what they are using in their websites and need to monitor those technologies to avoid vulnerabilities. This makes these components become one of the biggest threats to organizational security.
The best way to do so is to find out all the technologies used, follow up on their updates, perform those updates, and repeat this periodically.
Of course, the level of criticality of a vulnerability depends on where the component is integrated into the web application, and not all of them are highly critical. However, vulnerabilities always need to be patched and never overlooked, but first, you need to be aware of the vulnerability.
All that needs to be done, is use the right tool to get into a page’s source code and find out what is being utilized.
OSINT tools to find third party libraries
Just like OSINT can be used by attackers to identify the digital assets of a company and gather information to prepare for attacks, it can be used by companies to prevent these attacks. With the help of many OSINT tools to identify third-party components, companies can be aware of what their websites are utilizing, which versions of those components are currently active, and be informed in case those versions are affected by any exploitable vulnerability.
Here is a list of tools you can use to find out what technologies your website is using:
SimilarTech

Except for giving very detailed information about the website infrastructure, SimilarTech gives historical changes in technologies used during the time. This way companies can track if there is any malicious activity performed by a threat actor.
To make things even easier, SimilarTech has a very useful browser extension as well, that gives not only technical information, but also general information about the company, website traffic, and more.
WhatRuns – Chrome Extension
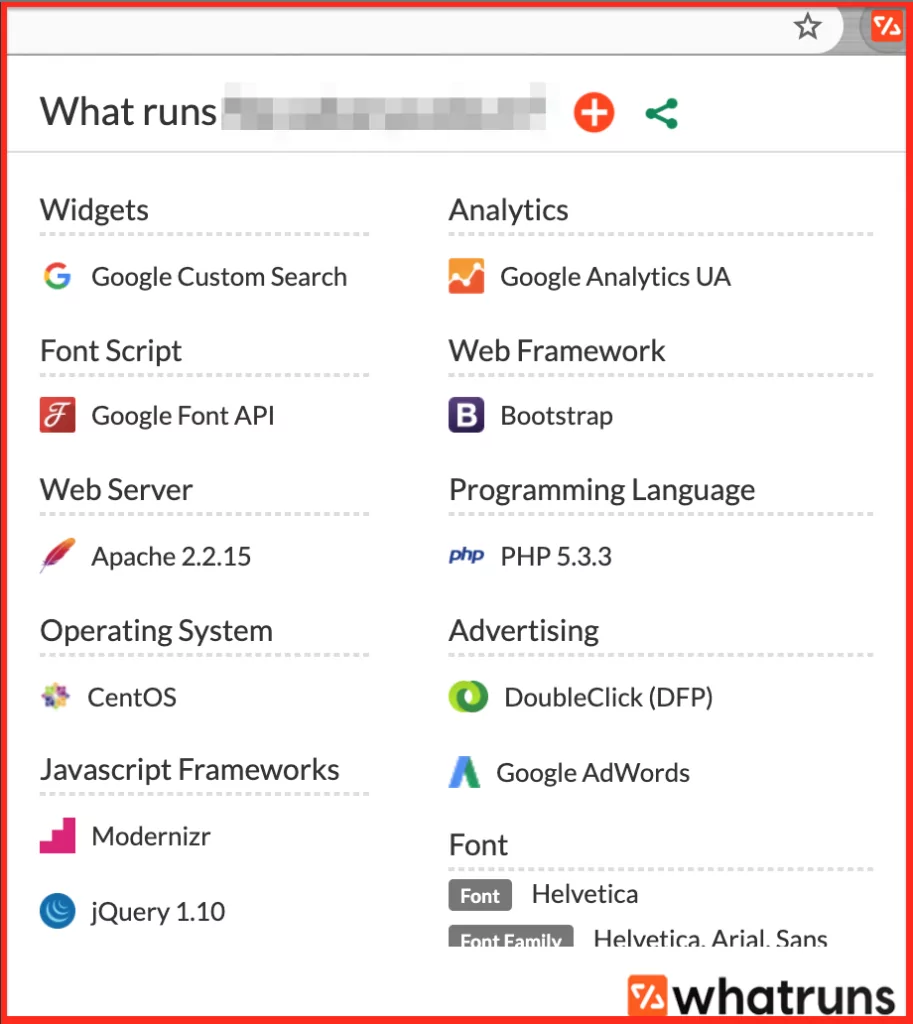
WhatRuns is a browser extension for Chrome that shows the technologies a website utilizes. No need to write a website URL, you only need to click the extension icon and it lists.
Wappalyzer
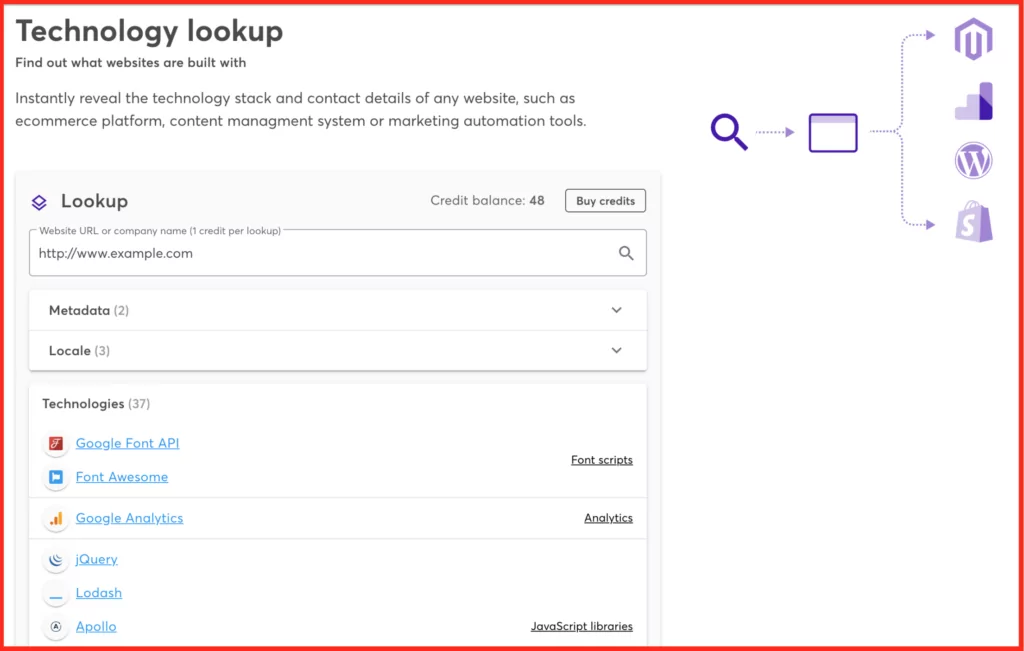
Using Wappalyzer you can find out what technologies a website is using, like analytics, CMS, platform, and much more. A nice feature is that it also notifies you of changes. This will allow you to be always up-to-date information on new technologies being integrated.
Wappalyzer also allows you to perform multiple searches at once, this way avoid wasting time and focus on all the technologies used in your website ecosystem.

Yes, it also has a browser extension for Chrome, Firefox, Edge and Safari.
BuiltWith
This is an OSINT tool, which only by getting a domain name gives you back a categorized technology info profile or a website. Not only that, but it also shares related technology trend statistics to help you decide for future websites.
LargerIO
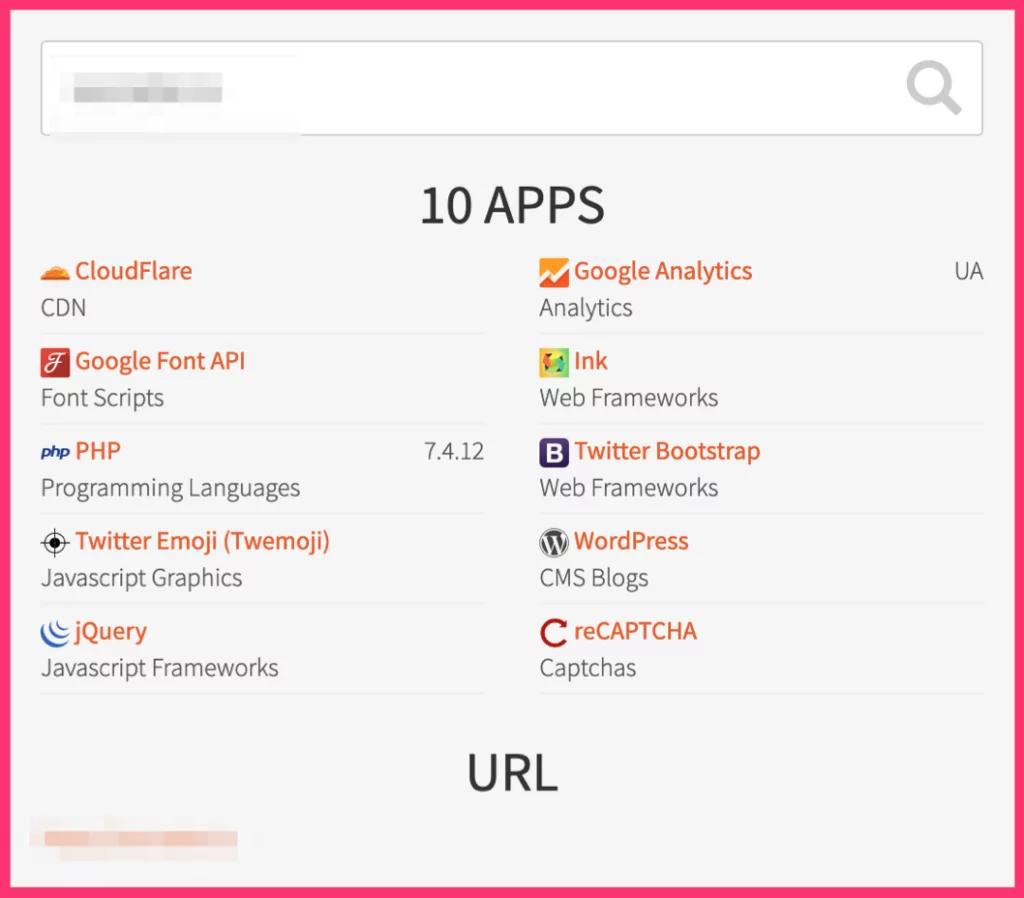
LargerIO is another OSINT tool to find out which technologies a website is utilizing. It categorizes them and lists them in a box.
Netcraft Site Report
Netcraft Site Report is a very useful tool to find identify much information of a website besides only the technologies used in it: SSL/TLS certificates, hosting information, security information, network information as well as general background.
W3techs
A little bit of a more primitive looking site yet gives plenty of useful information regarding the website technology profile.
Due to the algorithms these tools use, they don’t always give the same results. To get better information about a website’s components, it’s a smart move to check a few tools at once. However, doing this action manually can be time-consuming, especially for bigger companies.
SOCRadar’s website monitoring service
A better solution would be using automated tools that detect third-party libraries and other components that are utilized by a website, that also monitor them continuously, and notify you of any changes of possible vulnerabilities. That is exactly what SOCRadar includes in the services. By first detecting all the active and inactive websites of a company, then doing deep digital footprinting of them to detect login pages, CMS applications, and third-party libraries, SOCRadar offers a complete website monitoring of not only performance but also security posture as well.
SOCRadar empowers you to keep your brand reputation intact by early spotting and warning of web security issues from web defacement to cryptographic weaknesses that can result in data breaches as well.
Discover SOCRadar® Community Edition for free
With SOCRadar® Community Edition, you’ll be able to:
- Discover your unknown hacker-exposed assets
- Check if your IP addresses tagged as malicious
- Monitor your domain name on hacked websites and phishing databases
- Get notified when a critical zero-day vulnerability is disclosed
Free for 12 months for 1 corporate domain and 100 auto-discovered digital assets.


































