
How to Protect Against Digital Risks in Three Steps
For many organizations, digital initiatives are a lifeline. IoT, social, machine learning, big data analytics, artificial intelligence, and augmented reality enable digital startups to streamline operations, adopt new business models, and improve customer experience, maximizing speed, agility, efficiency, and profitability.
Digital transformation creates tremendous business opportunities, along with new forms of digital risks.
What is Digital Risk?
Digital risk refers to unwanted outcomes stemming from digital transformation and the adoption of related technologies. Cybersecurity, third-party, business continuity, data privacy, and other forms of digital risk add to the uncertainty of achieving business objectives.
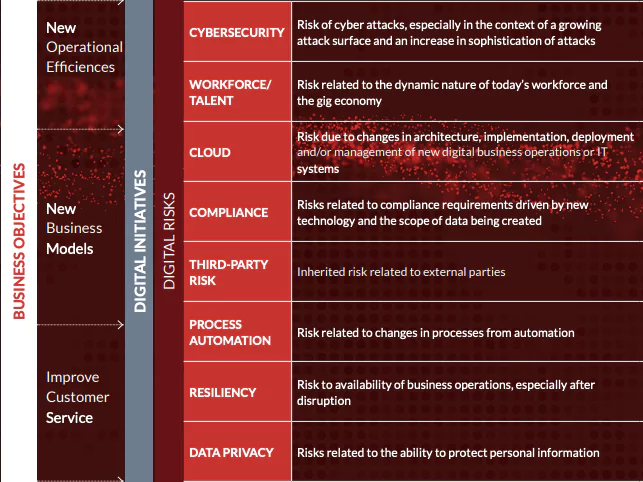
Strategic business objectives are the driving force behind digital initiatives such as big data analytics, IoT, and AI. But these initiatives have spawned different types of digital risk that every organization must learn to manage. The Cybersecurity field is one of them.
Risk of cyber attacks, especially in the context of a growing attack surface and an increase in sophistication of attacks. Therefore, this article discusses ways to protect against digital risks within the concept of the attack surface.
Attack Surface Analysis
The attack surface of a software environment is the sum of all the distinct locations (called “attack vectors”) where an unauthorized user (called an “attacker”) can try to enter or extract data from the environment. A primary security measure is to keep the attack surface as minimal as possible.
Attack Surface is designed to help developers identify and manage application security risks by creating and altering applications and applying security specialists to risk assessment. The emphasis here is on defending an application from external assault; it does not consider attacks on the system’s users or operators (e.g., malware injection, social engineering attacks).
There is less emphasis on insider threats, while the concepts remain the same. Internal attack surfaces are likely to differ from external attack surfaces, and some users may have extensive privileges.
Therefore Attack Surface Analysis is a must for avoiding digital risks; Attack Surface Analysis is helpful to:
1- Determine which functions and sections of the system need to be reviewed and tested for security flaws.
2- Identify high-risk code sections that need to be protected.
-in-depth defense — which elements of the system must be protected
3- Determine when the attack surface has changed, and a threat assessment is required.
Providing Risk Protection
Even though security leaders rely on their teams to protect against regulatory fines, damaged reputation, and loss of intellectual property, their limited visibility outside their perimeter means they fall short of communicating the entire risk landscape to the business.
Brand Protection mitigates the risks associated with digital transformation by protecting an organization’s data, brand, and attack surface, as well as delivering actionable information about threats from the open, deep, and dark web.
By identifying data loss, securing your online brand, and minimizing your attack surface, a managed service can help you reduce your digital risk. Our DRP Solution is the premier solution because of its unrivaled coverage, knowledge, and relevance.
A powerful, user-friendly search engine that integrates organized technical data with content from the open, deep, and dark web. Thanks to the strong syntax and configurable notifications, you can quickly examine security problems and discover adversaries targeting your organization and brand.
Knowing the Risks Before They Happen
Information on threats and threat actors that assists in the mitigation of adverse events in cyberspace is referred to as cyber threat intelligence. Examples of cyber threat intelligence sources are open-source, social media, human, technical, and deep and dark web intelligence.
In today’s world, digital technologies are at the core of nearly all industries. Automation and increased connectivity have transformed the world’s economic and cultural institutions, but they’ve also introduced risk in the form of cyberattacks.
Threat intelligence is information that enables you to avoid or reduce threats. Threat intelligence is based on facts and gives context — such as who is attacking you, their motive and skills, and what indicators of system compromise to look for — to help you make informed security decisions.
Discover SOCRadar® Free Edition
With SOCRadar® Free Edition, you’ll be able to:
- Discover your unknown hacker-exposed assets
- Check if your IP addresses tagged as malicious
- Monitor your domain name on hacked websites and phishing databases
- Get notified when a critical zero-day vulnerability is disclosed
Free for 12 months for 1 corporate domain and 100 auto-discovered digital assets.
Try for free


































