
How to (Safely) Access the Deep Web and Darknet
You have definitely heard there is a deep side to the internet where not everyone can access it. That is considered by many as hazardous and even illegal.
We have prepared this blog post to clear some misconceptions and guide you on how to safely browse the Deep Web. Here we will explain what Deep Web is, why it is important to search for content in the Deep Web, who and how can access it, and provide # of tips for you about how to stay safe when you surf in the deep web.
What is the surface web?
Everyone who has access to the internet uses the Surface web, or as some like to call it – the Clearnet. That content is indexed by different search engines like Google, Bing, Yandex, Duckduckgo, Yahoo, Baidu, etc. A typical search query consists of only keywords and even when you do not know the exact address of a website, those keywords are taken as inputs by the search engines to use their algorithms and give you the best results possible. Again – results consist of only indexed content by that search engine.
Although we use the Surface web for quite a long part of our days and feel like it is infinite, it actually is just a fraction of the whole package. The remaining part is hidden or invisible, but it is not impossible to access it.
What is the deep web?
What is not on the surface web, is definitely hidden, and it is also known as the deep web. As we said before, the surface is just a small part of what we can access and do on the internet. The ‘remaining’ part is not much of remaining, for it accounts for over 90% of the whole internet and contains stuff like:
- Private company databases
- Employee and customer records
- Important company backups
- Bank details
- Different kinds of archives and documents
- Scientific white papers
- Content of social media, email and even online banking accounts
- Medical records and much more
So where can we get data like this on the Deep web? The largest quantity of the data is found in Pastebin, as well as hacker forums and hidden sites.
As you can get it by now, the Deep Web contains any content that is protected by a password or any other type of authentication, and which isn’t and mustn’t be indexed by standard search engines. With one simple word, it consists of content that can be misused and cause problems to companies.
From all this, we can highlight the most common definition of the Deep Web which is as simple as this: the non-indexed content of the internet, – but so is the darknet.
What is the difference between these two, and why do people always confuse one for the other?
The difference between the deep web and darknet
It is not quite uncommon to hear people use the terms ‘darknet’ and ‘deep web’ interchangeably, but that is very inaccurate. There is a slight difference between them, that might take you from scrolling down interesting hidden content – to conducting an illicit activity, and sometimes even gamble with your fate.
When we said above “the remainder of the internet” is the deep web, it gives you the idea that there are only two parts of the internet, the surface, and the deep web. So you might be saying, “ it means deep and dark are the same” – but that is still not correct.
The answer is simple, and you might have already guessed it by now – Deep web, on its own, has a darker subset, which is used by many to purchase credit cards, data dumps, fraudulent documents, and commit any other illegal activity you can imagine. This part is what we call the darknet.
As you see – the selling point of the data detected on the Deep Web is in the darknet, more specifically, in the black markets.
To clarify the confusion, everything on the darknet is also part of the deep web, but everything on the deep web is not necessarily illegal, therefore these terms shouldn’t be used interchangeably.
Who uses it?
Everyone from individual users to black/white hackers can find a reason to access the Darknet. Individuals might use it to make sure they haven’t fallen prey to identity theft, check if any of their accounts have been compromised, or wander around onion websites just out of curiosity – as we mentioned before Darknet makes the biggest part of the whole internet. However, too much curiosity may lead people to illegal activity.
For companies, there is a different case. It is truly important for them to know if their brand name, products, employee/customer data, or confidential documents are being mentioned, even worse sold, in any of these Darknet content. That is why white hackers also surf these contents and try to keep companies up-to-date.
Basically everyone who has confidential files needs to make sure they are not being compromised.
Now, let’s get started with how you can take yourself into the deep web journey.
Let’s get started!
To your surprise, you don’t need any special tools or a darknet browser to access the deep web; you just need to know where to look. Specialized search engines, directories, paste sites, and wikis can help users locate the data they’re looking for.
Yet, you might have noticed, this journey can be risky. You have to proceed safely because the curiosity might lead you to want to access the Darknet, too. So it is strictly important to be one step ahead and stay secure. You need to know exactly what you are trying to look for, how to look for it, and where.
Therefore, you must use some special tools to gain access. Common examples can be the Tor browser, Freenet, or I2P. These provide point-to-point links, friend-to-friend connections.

These routes do the biggest job to keep you safe on your surfs – they enable the transmission of traffic over encrypted layers to ensure your anonymity on the network. And this is definitely what we all want when we surf on the deep – Anonymity.
We have prepared for you a few simple but compulsory steps you need to follow if you are about to access the deep web.
Here are the main steps you need to take, and as you can see it is quite simple:
- Get a VPN and log in
- Install Tor Browser
- Run Tor over VPN
- VPN over Tor
- Explore the deep web / darknet with double encryption (VPN and Tor)
- Use Freenet
- Use I2P
or
or
Now let’s see all the steps in more detail.
Get a VPN

First off, you must know that accessing the deep web means going below the surface, and even the tools you use are not the usual ones. You might be using a VPN for other reasons too, but to access the deep web it is a ‘must’ because it is the only way to hide your identity, i.e. your IP address. What a VPN does to protect you, is simply – create a virtual private network (as you get it from its name – VPN) from a public connection.
You have many options, like ExpressVPN, NordVPN, PrivateVPN, etc.
Install Tor
One of the most important things when browsing in the deep web is to leave as little traces as possible. With the tracking technologies of standard browsers like Chrome, you might put yourself at risk, so the best option you have is to use Tor. Tor is the best onion browser because it hides your network traffic with Tor routing by constantly changes your IP, and leaves no traces to reveal your identity.
To download it, go to the torproject and get the right version for your operating system.
However, only Tor is not always enough. With Tor node IPs being public, Internet providers can detect when it is being used. That’s why for private and more secure browsing, the best option is to use Tor combined with a VPN.
There are, however, two options here, you either use Tor over VPN or VPN over Tor, and there are slight differences regarding privacy and anonymity.
Tor over VPN
This happens when you first connect to your VPN, then start browsing on Tor. This is, so far, the most used option for surfing on the deep web. You are actually counting on your VPN to keep you safe because what this connection basically means is that – you browse anonymously on the deep web with Tor, and your only secret-keeper is your VPN. For this kind of connection, you can use a logless VPN that doesn’t store any traffic logs – things you search on the internet, or session logs – your IP address and similar information.
VPN over Tor
This is a less common way of accessing the deep web. In this alternative, you don’t let the VPN see your IP address since the internet traffic first goes through Tor. However, your connection to Tor is not pretty private since your Internet Service Provider can see it.
Freenet
Unlike TOR, there is no need for a server to host content in Freenet. Users get it in a distributed data store – which is the anonymity provider part of Freenet. Freenet users get involved by giving some of their bandwidth and hard drives. The data is kept encrypted and can be shared with other users. As is happens in TOR, the extensions of the sites here are not familiar TLDs either. This basically means – sites do not end with extensions such as .com, .net and similar TLDs surface web users are used to seeing.
The format is “http: // localhost: 8888 / [Freenet Key]” and it can uniquely be used in Freenet.
Freenet allows users to connect in two modes: darknet and opennet. Opennet doesn’t have any specifications on who you share content with, but Darknet mode allows you to select a group of friends, who also are on the network, and you can only connect and share content with them. This allows groups of people to create closed anonymous networks made up solely of people they know and trust.
I2P
Used to access the Darknet, I2P is an anonymous network that provides point-to-point (P2P) access. It contains layers that allow anonymous and secure applications to transmit messages to each other. The network is messaging-based and uses a library to ensure secure streaming. Furthermore, the whole communication is end-to-end encrypted. When sending a message, encryption is done in 4 different layers.
Even endpoints (sender and receiver) are cryptographic identifiers. It is like parties with an asymmetric key pair. Here too, the TLDs are not the familiar ones used in the surface web – websites here have the .i2p extension.
5 tips to safer access
- Use a VM or disposable OS
- Use a VPN and an adequate browser (TOR) / Use Freenet / Use I2P
- Prefer “Tor over VPN” over the opposite
- Understand .onions
- Use a new USB for the files you download
How to access deep web hacker forums or black markets?
We understood what deep web and darknet are, who needs them, and how you can access them – how about we see some real examples of deep web surfing now. Let’s SAFELY access some forum sites on the deep, and check out what topics are being discussed there.
We prepared some examples for you – a step-by-step guide to entering those forums and their content. Since it is the most commonly used method, we will use Tor over VPN. Now, let’s dive in!
First of all, you’ll need a VPN – now you know – it provides additional privacy and security online by changing your IP address. We selected a random country to connect through it, and the VPN shows we are in.
Secondly, make sure you have previously installed a Tor browser – if you read the whole blog, you must know – it’s an anonymous web browser without which you wouldn’t be able to access the .onion links. In case you don’t have it installed, don’t panic, it is as simple as installing any other browser. Go to https://www.torproject.org/download/ and you know what you’ll have to do next.
Voila! The deep web is open for you, and you are untraceable using the best shield Tor + VPN.
These steps are all the same if you want to access anything on the deep web. Now, what you want to surf on, depends all on you. To get access to a forum, though, you need the exact .onion address because searches here are not exactly the same as standard Google searches. A “.onion” addresses are only accessible via Tor Browser. This suggests hackers can extract data about browsing activities by monitoring Tor exit nodes. It also means someone hosting an internet site can hide that server using the Tor network, so it is practically not easy to find.
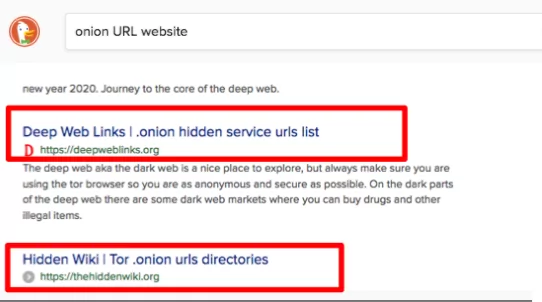
Looking for lists of best forums related to hacking and what to get their .onion addresses? Search the web for lists of .onion sites and you’ll find some places to start across the first results you will find .deepweblinks and .thehiddenwiki.
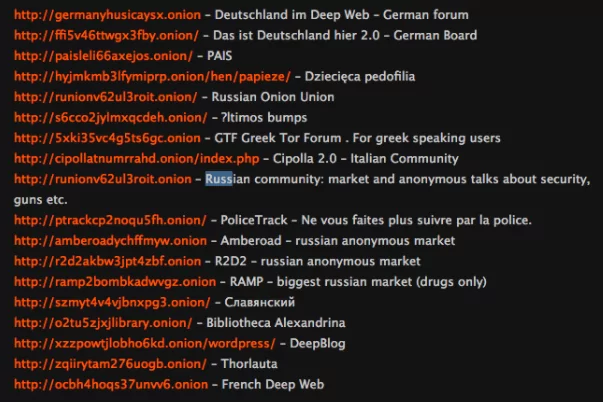
You may not be able to access some of the extensions here because they are constantly changing. So you’ll have to search a little more.
Let’s visit the Hackerplace from them. It is another underground forum. Different from other forums, here is the fact that users can not actually communicate with each other, all they can do is see and get different materials related to hacking.
Some forum sites will provide .onion addresses in themselves. For example; sky-farud.ru

This one is a Russian forum that offers PII – Personal Identifiable Information and CC – Credit Card data, botnets, exploit, malware and so much more. Once you go to this website, you will be able to find the .onion extension.
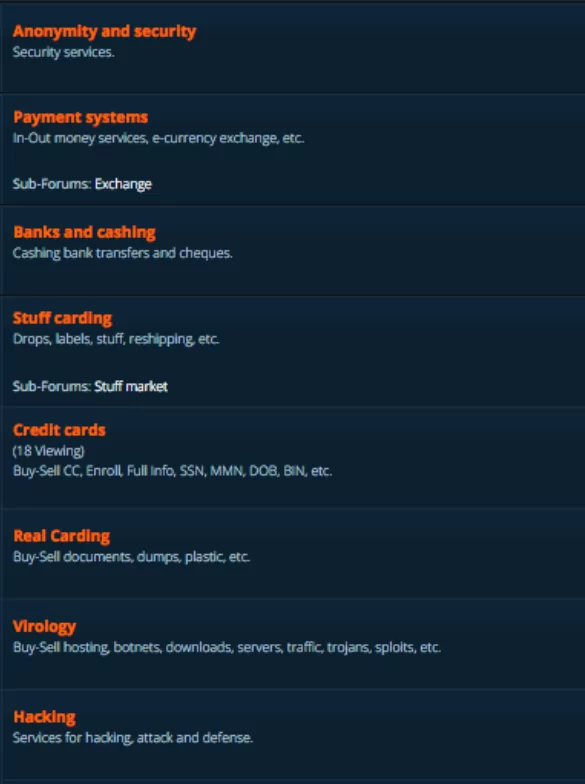
Similar to these, you can visit any other underground hacker forum. Basically, the steps are pretty simple – connect to a VPN – Open TOR – find the .onion website – search for what you were looking for. Some of the websites give you a link to the .onion extension – as sky-fraud does. Some others don’t do so, and you need to know the exact URL.
SOCRadar deep/dark web monitoring
SOCRadar provides a thorough Dark Web monitoring solution that enables organizations to identify and mitigate threats across the surface, deep and dark web. Socradar searches the Deep Web for private information such as the institution’s email addresses, IP addresses, URL addresses, or source codes. It also monitors hacker chatters to detect any mention of company name and domain in deep web.
Receive a Free Deep Web Report for Your Organization
- Deep web mentions
- Compromised credentials
- Malware/bot-infected users
- Highly critical data exposure findings
- Date of the latest exposure
SOCRadar, the early warning system for information security, analyzes thousands of deep web resources including hacker forums and social channels every day. Wouldn’t be great to see the deep web data related to your organization?



































