How To Use Threat Intelligence for Fraud Detection and Prevention?
The cyber threat landscape is evolving rapidly, and threat intelligence data is becoming more and more important as cyber-threat actors launch new campaigns and eventually come into contact with each other.
Digital fraud is rising and new digital technologies draw adversaries’ attention to this field. Criminals are becoming more and more advanced with hacking, using the compromised account data to login other accounts. For instance, e-commerce fraud is predicted to increase by 14% by 2023 and could cost retailers $130 billion.1
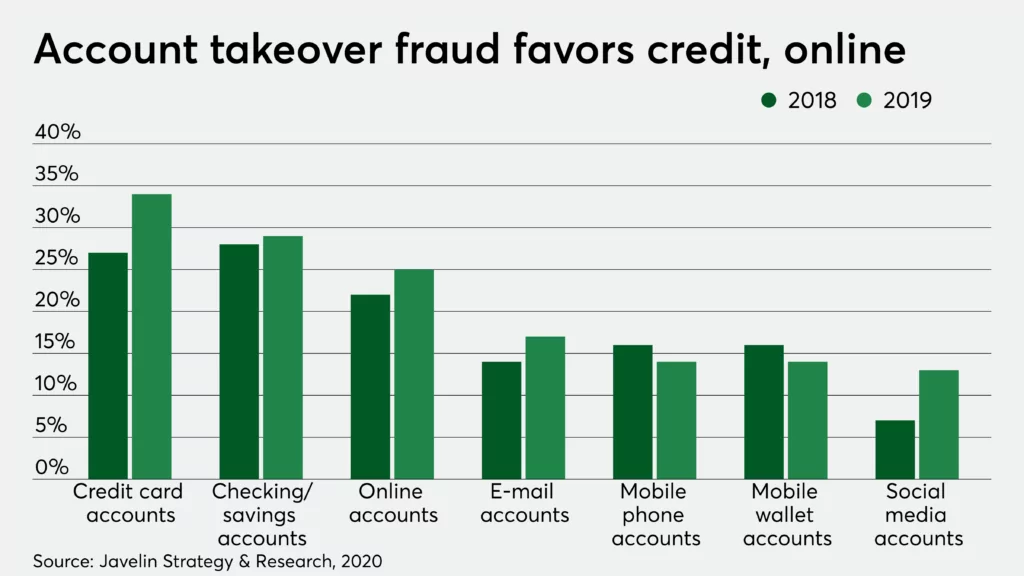
There are a couple of different types of fraud in the digital world. One of them is Account Takeover (ATO) where a malicious third party successfully gains access to a user’s account credentials. In case of payment fraud, a fraudster has stolen someone’s credit or debit card number, or checking account data, and uses that payment information to make an unauthorized purchase. Fake account registration is the automatic creation of multiple user accounts that are not affiliated with a valid one or which are generated without the knowledge of the data of a real individual.
How threat intelligence can help?
Most of the time, threat intelligence is much more effective than internal security products to detect and prevent digital fraud.
One of the ways organizations can address this is to integrate the feeds of the cyber threat into their existing security solutions, according to a recent National Security Agency (NSA) report.
Cyber threat intelligence tools can also help to support an overall strengthened security position by automating processes and providing administrators with tools to better prevent potential threats. A combination of threat analysis and data analysis using machine learning, if done properly, can help security teams quickly turn raw data into effective information about cyber threats. Threat information platforms can bring together internal and external data sources to help organizations better understand the cyber threats they are likely to face. Recognize the need to implement cyber threat intelligence in your organization according to its resources and capabilities.
Threat information can help to decipher the threat landscape and give security personnel an intelligence context to make better and faster decisions. Whether you are able to develop your own solution or use a threat information feed, integrated threat information will help to keep calm in today’s ever-growing threat landscapes.
By investing in cyber threat intelligence, companies can access a database that details a large number of threats. Properly applied information on cyber threats can provide better insight into cyber threats and enable a better understanding of and more effective response to the threat landscape. This is important because information about cyber threats can be distributed through data centers around the world.

How to use threat intel more effectively?
The intelligence of the cyber threat provides cybersecurity and system administrators with the knowledge they need to formulate a plan that best protects their networks. In some situations, information about cyber threats can provide knowledge by revealing unknown threats, allowing organizations to make better decisions about their security. Cyber threat analysis helps you determine whether your security and defense systems can actually deal with the threat and if so, improve it. In other situations, however, it is only useful for SOC teams, network administrators and IT teams to know which threats are most dangerous and how to attack, prevent, and respond to them.
From a maturity standpoint, make sure you have the right cyber hygiene before you start investigating cyber threats, according to the Cyber Threat Intelligence Center.
To achieve resilience in detecting and responding to threats, security experts should adopt a multi-layered threat intelligence approach that includes both malware-centric and enemy-centric approaches, according to the Cyber Threat Intelligence Center. A threat – messaging platform should be integrated into your cybersecurity solution and have the ability to automatically respond to identified threats. This form of threat Intelligence is called tactical threat information, while security products and automation can use it on a large scale to protect and detect potential threats, the center said. In addition, information about cyber threats can be integrated into a range of other security solutions, such as intrusion detection systems, so that individuals and organizations can develop a calculated and effective response to counter cyber attacks.
This can range from technical compromise indicators (IoC) to detailed profiles of actors involved in the cyber threat, to threats an organization may face. Threat information is usually organized in feeds, and these data points are correlated with information about the threat environment, such as threats to the network, network infrastructure, or organization infrastructure.
This type of threat information is picked up by cybersecurity solutions and used to detect and block incoming and ongoing attacks. Once the relevant information about cyber threats is extracted from the threat data, it undergoes structured processing, followed by an exchange with the required stakeholders, tightening security controls, and preventing future cyber attacks. This is becoming increasingly important as all levels of staff are forced to respond to cyber threats.
Use cases: Top fraud attack vectors
The intelligence of threats has rapidly become a must for fraud teams. Recognizing that preventing fraud by means of threat intelligence requires much more than just alerting is important.
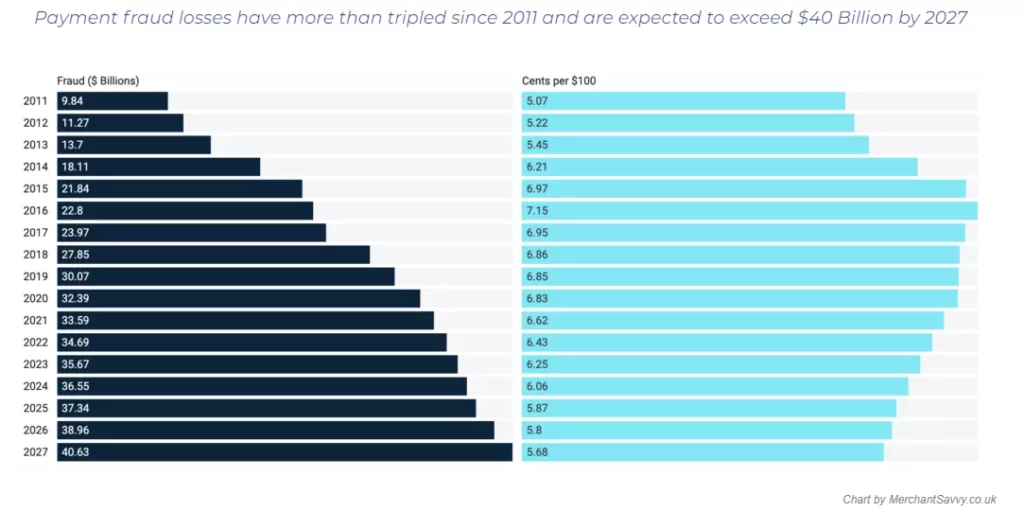
Dark web black markets trading compromised financial and credit card data are soaring. Due to the increasing use of innovative and complex fraud tactics, enterprises are expected to lose US $100 billion in card-not-present (CNP) fraud between 2018 and 2023. Global losses from payment fraud have tripled from $9.84 Billion in 2011 to $32.39 in 2020. It is projected to cost $40.62 billion in 2027.
Following statistics can show how serious digital fraud is;
Payment fraud
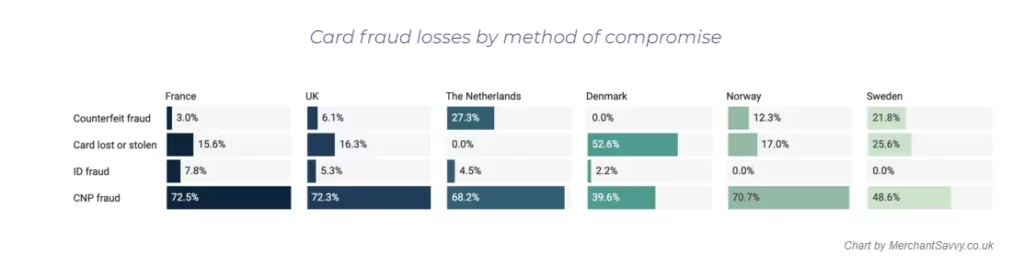
The next level of the payment ecosystem is the acquisition of banks and Payment Service Providers (PSPs). The problems of payment fraud posed by these firms vary from those faced by enterprises. Data sizes are far higher and several networks are used by acquirers and processors, often with reduced access to information than online retailers.
SOCRadar can detect instantly stolen credit cards by proactively monitoring the surface and dark web and notify when credit card data is detected on marketplaces to stop fraudsters.
Account takeover
Account takeover (ATO) is a form of identity fraud where adversaries have unauthorized access to any account. Any company’s user accounts are at risk of ATO. Usually, the key targets are verified and active accounts. The financial balance, money laundering, or potential reselling of account credentials could be the main reasons for ATOs. Account takeover fraud attempts to steal from consumers and e-commerce merchants swelled 282% between Q2 2019 to Q2 2020. 57% of businesses report higher fraud losses associated with the account opening and account takeover.
SOCRadar allows you to monitor suspicious activities beyond the traditional tools and those activities are easily flagged.
Fake account registration
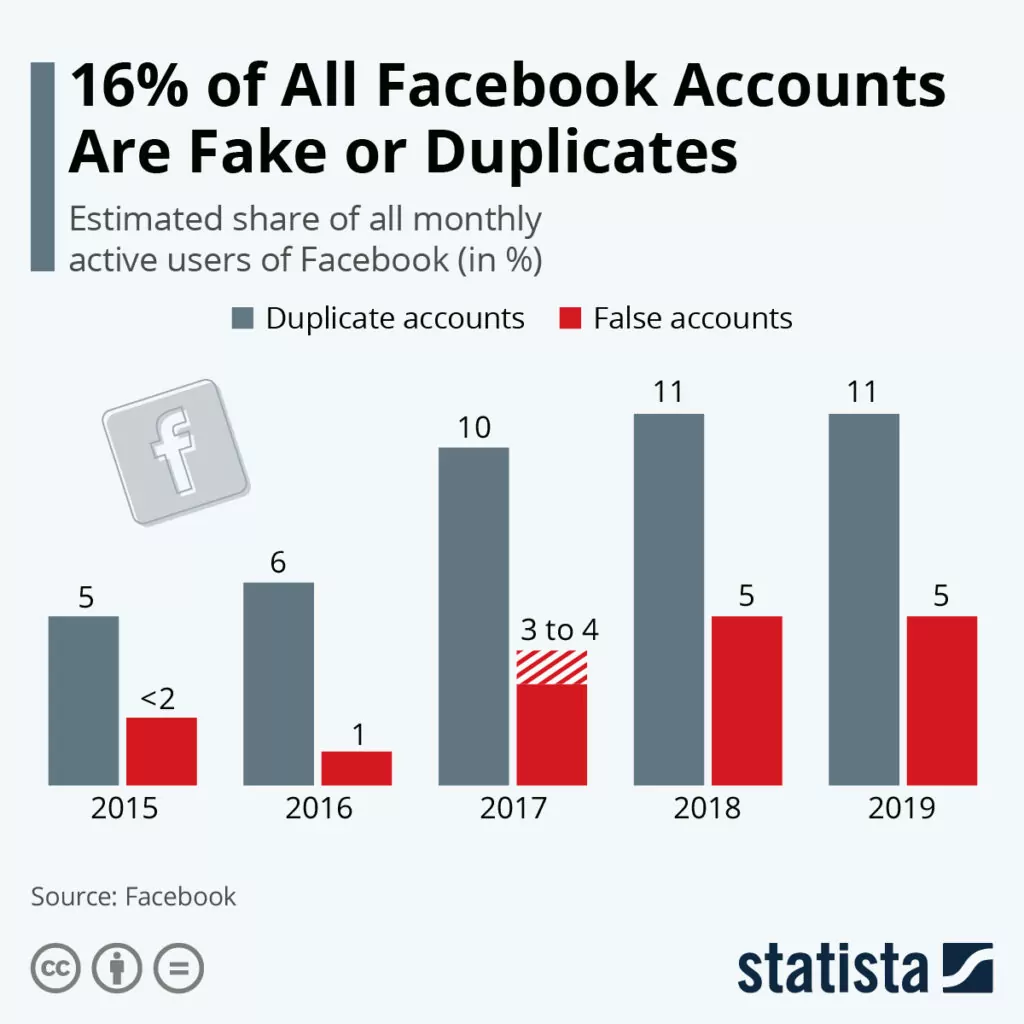
One in five account registrations is fraudulent. Over 2 billion fake Facebook accounts were taken down in 2019. 21.6 million fake LinkedIn accounts were either removed or blocked in the first half of 2019. FakeSpot, Inc. estimates that a third of the reviews on major websites, including Amazon, Walmart, and Steam, is fake.
It is highly difficult to spot fraudulent account attacks as intrusion techniques develop. The widely spread advanced fake account formation attacks use fake or stolen identification. These attacks are conducted in short rises or spread over long periods which render the use of conventional security measures difficult to detect effectively and stop alone.
Monitoring account registrations that can be done by SOCRadar for you is the forefront of any successful technique for fraud prevention. Custom lists for further monitoring contain records that are suspected but not decisively linked to positive behavior.
Loyalty abuse
Loyalty abuse is as important as payment fraud and ATO but mostly unnoticed or ignored. The risks involved with the operation of various customer loyalty schemes are frequently ignored and the fraud and risk control of the organization has been exposed to a failure. Losses from loyalty abuse are not typically so apparent and can remain unrecognized until proper reconciliation takes place for lengthy periods of time.
Gartner says there are over $140 billion in unspent loyalty points in the United States alone. For cybercriminals, this vector of fraud may be pretty profitable. LSE reports the amount of money at stake to be $3.1 billion in the redeemed points are fraudulent.

Learn how SOCRadar’s solution enables your team to use cyber threat information effectively and efficiently. SOCRadar’s AI-enabled and the automated platform allows you to monitor dark web carding forums, black markets, and channels for credit card information stolen from your customers or employees.
Discover SOCRadar® Community Edition for free
With SOCRadar® Community Edition, you’ll be able to:
- Discover your unknown hacker-exposed assets
- Check if your IP addresses tagged as malicious
- Monitor your domain name on hacked websites and phishing databases
- Get notified when a critical zero-day vulnerability is disclosed
Free for 12 months for 1 corporate domain and 100 auto-discovered digital assets.