
How Web Skimming Attacks Happen & What You Can Do to Protect Yourself
What is web skimming?
The web skimming attack also referred to as online card skimming, steals credit card or payment information details from a website’s visitors when they make purchases or reservations. To achieve this, web skimmers hijack the route of the payment sites or some kind of payment forms and give the unsuspected users their own payment page. Previously this was known as form jacking, which was used by hackers to change forms and capture PII data from users.
Attackers use security flaws in third-party client-side code like JavaScript or open-source libraries to insert malicious code that steals information entered by users. They achieve this by taking advantage of known vulnerabilities to compromise the websites or apps serving these third-party libraries. Also, many developers forget their credentials in code repositories or use compromised credentials. Attackers can use these compromised credentials to take over third party websites and insert their malicious code. They also use zero-day vulnerabilities as an opening to websites and smartphone apps in third-party code. Furthermore, several developers erroneously store the hidden access codes in their Github repositories. After these access codes are given, the attackers have control over the content. Hackers inject malicious code into third party scripts and steal credit card data from the digital skimmers of your web site.
How does it work: A step-by-step guide
Typically a web skimmer is a malicious JavaScript (JS) code installed in browser-based payment sites to allow skimming. When malware is injected in a third party script provider to capture payment information, the payment page is jeopardized on a web site. These types of attacks mainly aim at online shoppers. The skimmer was mounted on the page itself and not in a document so that it was not reflected until the payment point was reached.
Step 1: Gaining access
Attackers can get access to your website either by breaking into your infrastructure/server and placing the skimmer there or they can try to find vulnerabilities for your third-party vendors.
Step 2: Collecting data
In general, malicious code is disguised in the absence of detection inside other code that appears innocuous. Skimmers always use some sort of JavaScript that listens and collects sensitive information.
Step 3: Harvesting sensitive information
After collecting critical data via your website, hackers can send this information to their own servers.
What is Magecart?
Magecart is a recognized hacker group who use mostly web skimming attacks. The name does not mean a single group anymore but the code itself. Despite their increasing prominence in eCommerce or other industries that gather bank card details from their clients, Magecart attacks have been largely ignored in the security world until recently.
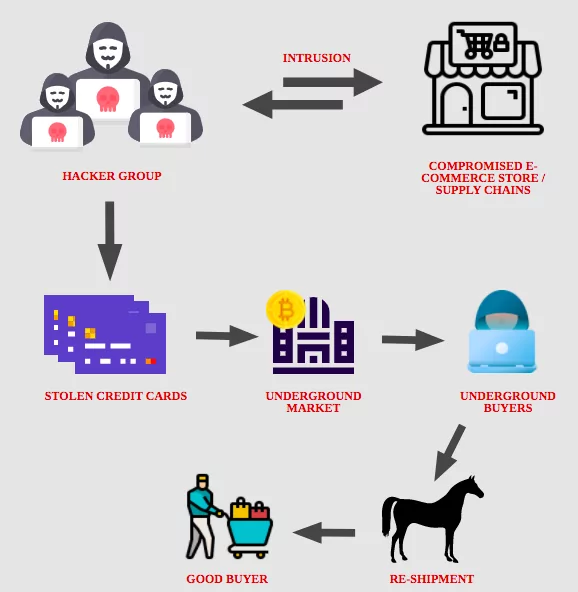
The scalability of the attack is an additional advantage with third-party compromises. Hackers may harm a whole network of websites that rely on it by hacking a single provider.
Magecart earned a spot on the list of The Most Dangerous on the Internet in 2018 by the Wired magazine.
What are the real-life scenarios?
These cyber threats, such as website skimming, crypto-monetary mining, fingerprinting, and water holing, have triggered some of the most significant violations of the recent past. The automated loss of security involves the hacking of British Airways, Ticketmaster, and Macy’s, which has resulted in cyber-attacks intercepting thousands of consumers’ credit card information.
British Airways breach
In 2018, payment card skimming software built on the British Airways web site affected over 380,000 credit cards. Payments via the website and the smartphone app of the airline have been stolen over a three-week period. Despite the credit cards that were stolen, information regarding customers’ travel was not compromised.
This unique skimmer was strongly tuned to how the payment page of British Airway is set up, which informs us that the attackers have been deliberately contemplating how to approach this website, rather than automatically dumping the usual Magecart skimmer. The same script affected mobile phones. Attackers stole customers’ names, billing addresses, email addresses, bank card details.

Ticketmaster hack
Web skimming attacks hit ticket-selling giant Ticketmaster in 2018. Based on the report, more than 40,000 customer’s data were captured by the skimmers. After Ticketmaster’s investigation, it became clear that the main reason for the breach was caused by a third-party partner and not Ticketmaster.
Inbenta Technology, a third-party vendor that supplies NLP solutions to Ticketmaster, updated a line of JavaScript code specifically for Ticketmaster’s requirements. This line of code was used on a payments page for Ticketmaster, which is what allowed threat actors to collect payment and user data from Ticketmaster.

Macy’s Magecart attack
Magecart attackers inserted malicious JavaScript code into the payment page of Macy’s The attackers changed the file ClientSideErrorLog.js, which enabled them to collect payment information and user data.
What you can do to protect yourself?
Many organizations have almost no visibility into their web-facing assets and the way their users interact with them. Because of this, browser-based cyber threats have become the go-to method for cyber threat actors to target organizations, their employees, and, perhaps most publicly, their customers.
Standard security procedures such as vendor evaluation, server patching, access management and external penetration monitoring are advised. In addition, malicious script updates can be avoided by the use of material protection policies and integrity configuration of sub-resources.

Following best practices can help you to harden your security and prevent Magecart attacks:
- Identifying all your third-party e-commerce and online advertising vendors.
- Monitor all third-party scripts on your site.
- Monitor code changes on websites.
- Implement client-side web skimming solutions.
- Use patch management effectively scan for web vulnerabilities.
- Replace admin passwords with multi-factor authentication.
- Configure firewall properly and frequently.
- Deploy a bot management solution to prevent browser-based bot attacks.
How to protect your organization against Magecart attacks by using SOCRadar?
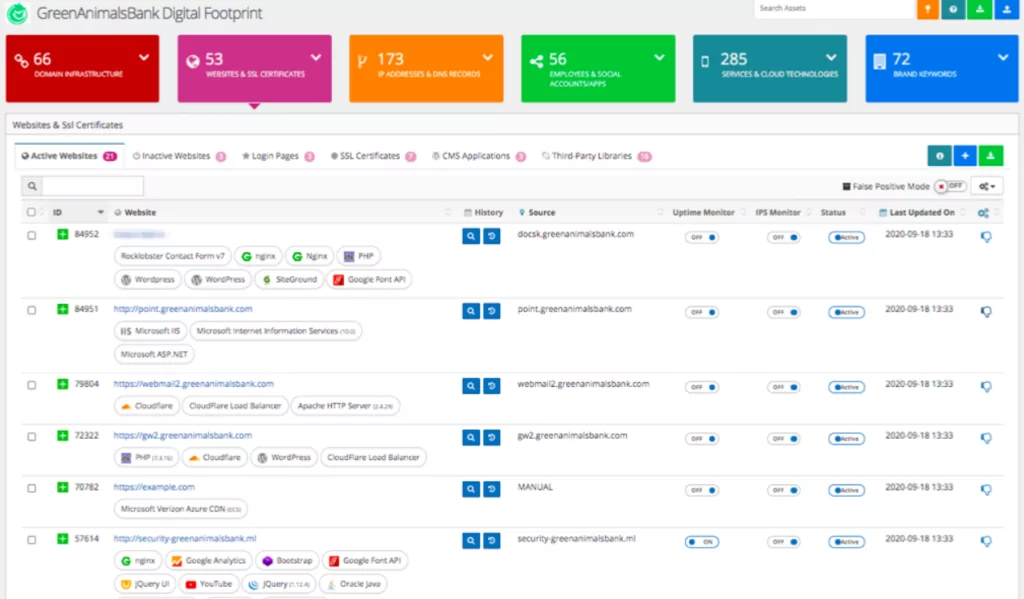
SOCRadar monitors all the code on a website including third-party JavaScripts. It immediately sends alerts for suspicious changes by monitoring the dynamic inventory. Thus, an organization can quickly detect the injected JavaScript.
SOCRadar allows you to spot unauthorized, suspicious code injections by continuously monitoring auto-discovered client-side web assets, login pages, and forms. With SOCRadar;
- Spot unauthorized code changes.
- Discover and monitor running third party libraries for vulnerabilities.
- Monitor if any JavaScript code manipulates the Document Object Model.
Discover SOCRadar® Community Edition for free
With SOCRadar® Community Edition, you’ll be able to:
- Discover your unknown hacker-exposed assets
- Check if your IP addresses tagged as malicious
- Monitor your domain name on hacked websites and phishing databases
- Get notified when a critical zero-day vulnerability is disclosed
Free for 12 months for 1 corporate domain and 100 auto-discovered digital assets.
































