
IntelBroker Claims Apple, AMD Data Breaches; NSA Data Allegedly Leaked
The SOCRadar Dark Web Team has uncovered several alarming posts on hacker forums, revealing significant breaches and data sales involving prominent companies. Notable incidents include the alleged sale of Apple and AMD databases by IntelBroker, a notorious cyber threat actor.
Additionally, a new stealer tool capable of extensive data theft has been leaked, and unauthorized network access to an American software company is for sale. Furthermore, the Deanon Club claims to have leaked over 30GB of data allegedly from the NSA, raising serious cybersecurity concerns.
Receive a Free Dark Web Report for Your Organization:
The Alleged Database of Apple is on Sale
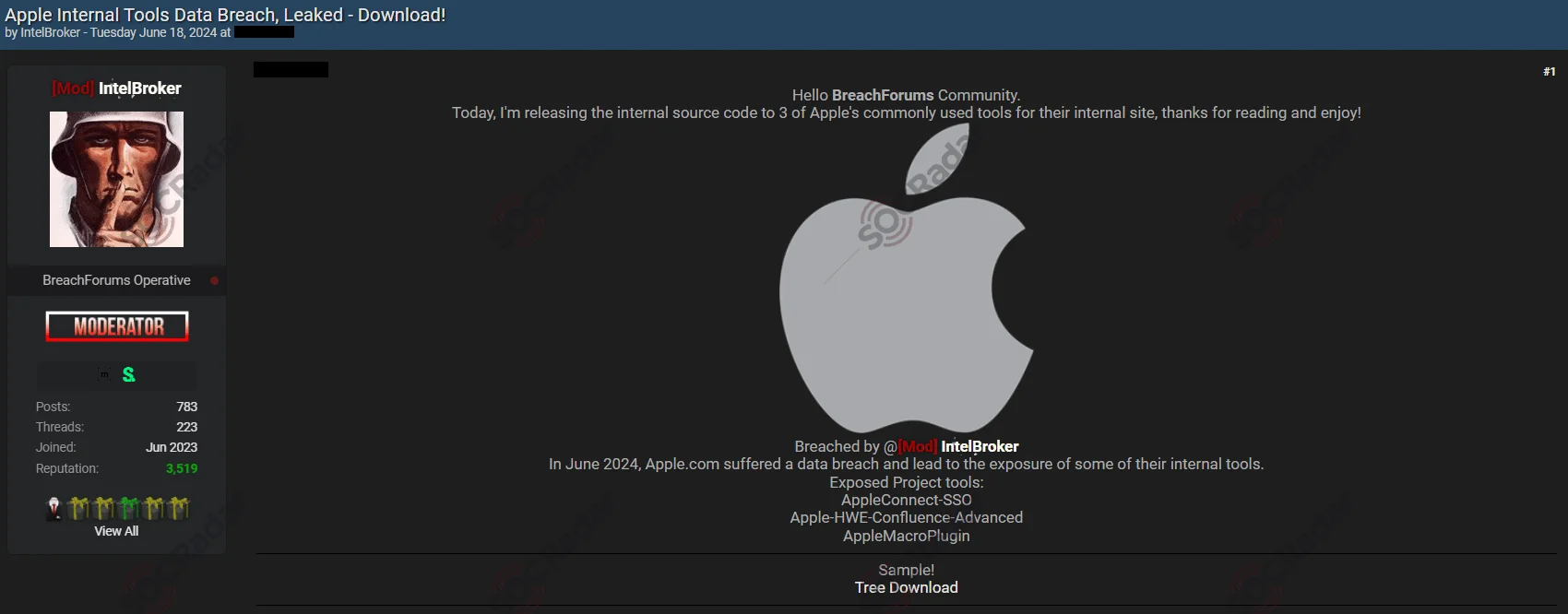
On June 18, The SOCRadar Dark Web Team detected a post in a hacker forum where a threat actor, IntelBroker, claimed to have a new alleged database for sale, involving Apple.
The threat actor alleges a breach of Apple’s internal site, exposing tools such as AppleConnect-SSO, Apple-HWE-Confluence-Advanced, and AppleMacroPlugin.
IntelBroker, a notorious member of a racist cyber threat group named CyberNiggers with a track record of orchestrating high-profile cyberattacks. Operating within the realm of initial access brokering, IntelBroker specializes in identifying and selling access to compromised systems, paving the way for various malicious activities.
Alleged Database of AMD on Sale
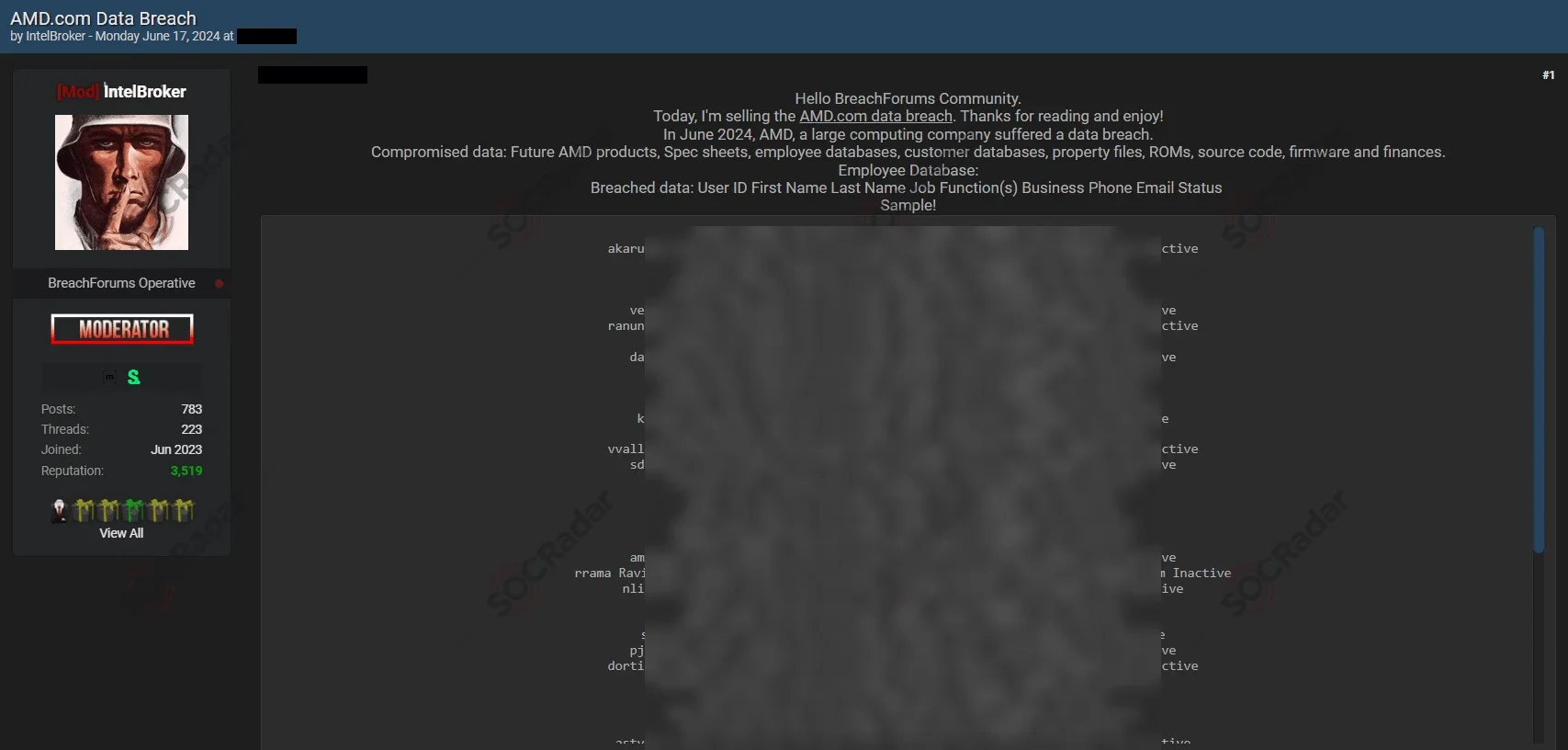
The SOCRadar Dark Web Team detected a post in a hacker forum that a threat actor is allegedly selling a database of AMD.
The threat actor, IntelBroker, claims to have breached AMD’s database, exposing sensitive information. The alleged data includes future AMD products, spec sheets, customer databases, property files, ROMs, source code, firmware, financial information, and employee data (user IDs, full names, job functions, phone numbers, emails, etc.).
New Stealer Tool is Leaked
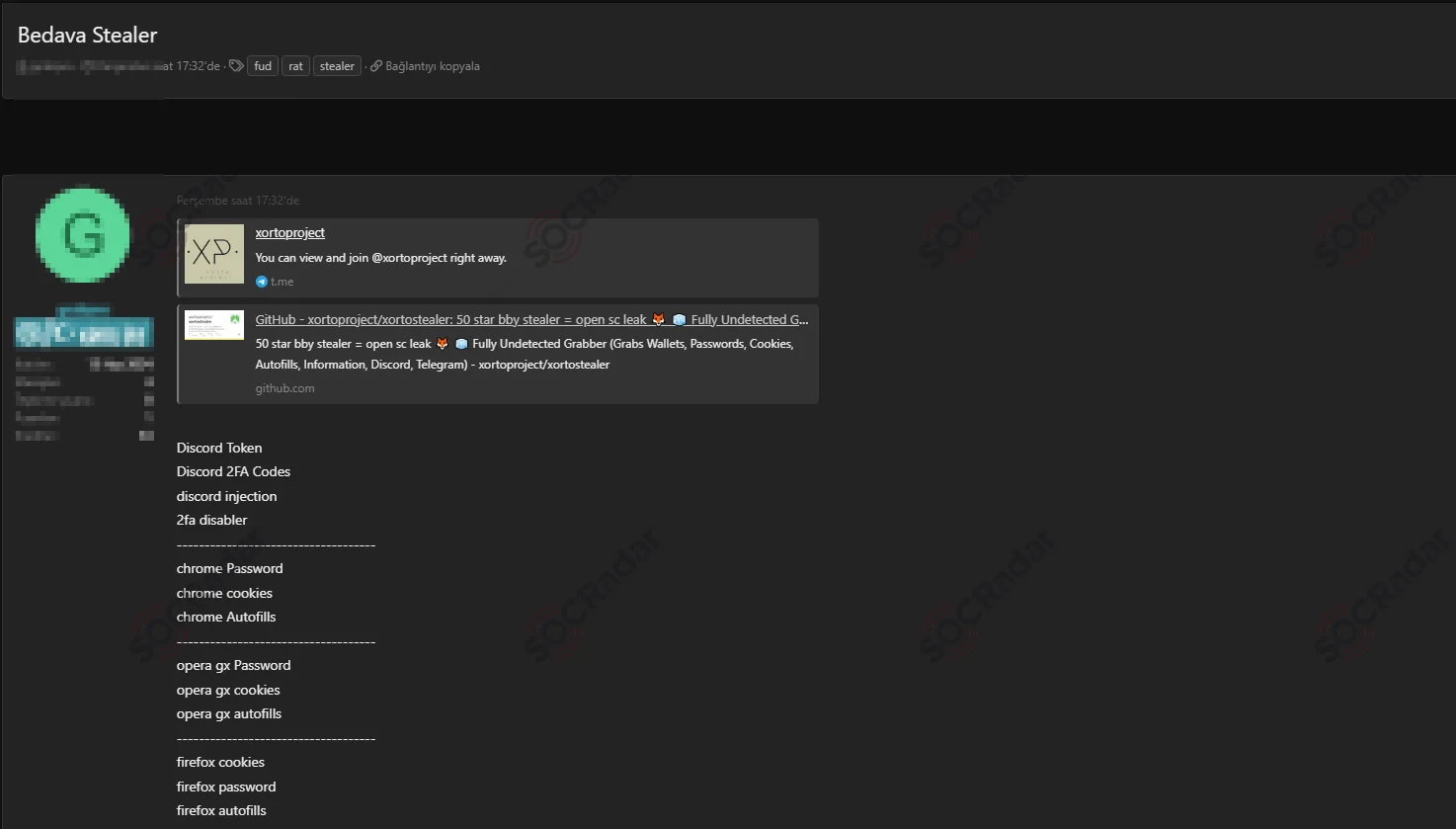
The SOCRadar Dark Web Team detected a post in a hacker forum that a threat actor claims to have leaked a new stealer tool. The alleged tool is capable of stealing a wide range of sensitive information, including:
- Discord tokens, 2FA codes, and injection methods
- Chrome, Opera GX, Firefox, Opera, Edge, and Brave browser passwords, cookies, and autofills
- Session data for Steam, Instagram, TikTok, Reddit, Valorant, Twitter, Telegram, and Roblox
- Credit/debit card information
- All browser wallets and PC information
This tool, if real, poses a significant threat by enabling the theft of extensive personal and financial data.
The Alleged Unauthorized Network Access Sale is Detected for an American Software Company
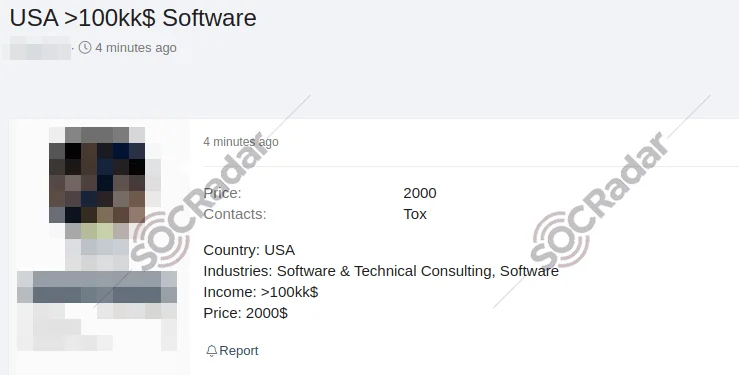
The SOCRadar Dark Web Team uncovered a post in a hacker forum that a threat actor is allegedly selling unauthorized network access belonging to a software company operating in the US.
The threat actor claims that the network access is available for $2000 and provides contact information via Tox. The company in question is involved in software and technical consulting with an income exceeding $100 million.
Deanon Club Leaks Data Allegedly Belonging to the NSA

The SOCRadar Dark Web Team detected a post in a Telegram channel where the Deanon Club threat group claimed to have leaked over 30GB of data allegedly belonging to the NSA. The credibility of this claim is questionable, as it may be a repost for attention-grabbing purposes. The Deanon Club, known for its financial motivations and its acquisition of the pro-Russian hacktivist group KillNet, has potentially duplicated previously leaked information shared by the Homeland Justice threat group. The new Telegram channel, where the data was posted, advertises itself as a source for exclusive hacking material, indicating that the claim might be made to attract attention.
Although the Deanon Club published the data claiming it belonged to the NSA (National Security Agency), the file names suggest they may actually be associated with the domain nsa[.]gov[.]al, which belongs to the Autoriteti Kombëtar për Sigurinë e Informacionit të Klasifikuar in Albania. This indicates that the NSA does not appear to be linked to the data in question.
Powered by DarkMirror™
Gaining visibility into deep and dark web threats can be extremely useful from an actionable threat intelligence and digital risk protection perspective. However, monitoring all sources is simply not feasible, which can be time-consuming and challenging. One click-by-mistake can result in malware bot infection. To tackle these challenges, SOCRadar’s DarkMirror™ screen empowers your SOC team to follow up with the latest posts of threat actors and groups filtered by the targeted country or industry.



































