
Latest Critical Vulnerabilities in Juniper Secure Analytics and Mastodon: CVE-2023-37920, CVE-2021-4048, CVE-2024-23832
The latest serious issues demanding attention include severe vulnerabilities found in Juniper Networks’ Secure Analytics and the decentralized social network “Mastodon”.
Of critical concern is the vulnerability in Mastodon, along with two vulnerabilities highlighted in the Juniper Secure Analytics advisory, each with CVSS scores exceeding 9.0.
In this blog post, we will explore the details of these vulnerabilities within Juniper Secure Analytics applications and Mastodon. Our objective is to provide insight into these recently addressed vulnerabilities and to guide readers through the latest developments in the cyber threat landscape, offering knowledge to facilitate the remediation process.
CISA Highlights That Updates Are Available for Critical Juniper Secure Analytics Vulnerabilities
Juniper Networks’ recent security updates tackle a total of 20 vulnerabilities across multiple Juniper Secure Analytics applications, spanning from medium to critical severity.
CISA has issued an alert regarding these vulnerabilities, cautioning that threat actors could exploit one of them to seize control of an affected system.
The affected applications and versions are:
- Log Collector prior to version v1.8.4
- SOAR Plugin App prior to version 5.3.1
- Deployment Intelligence App prior to 3.0.12
- User Behavior Analytics Application add-on prior to 4.1.14
The details of the critical and high-severity vulnerabilities mentioned in the advisory are as follows:
CVE-2023-37920 (CVSS: 9.8, Critical): Certifi, a curated collection of Root Certificates for SSL certificate validation, included “e-Tugra” root certificates in previous versions. Due to security concerns raised about “e-Tugra” systems, Certifi 2023.07.22 removes these root certificates from its store.

SOCRadar Vulnerability Intelligence card of CVE-2023-37920
CVE-2021-4048 (CVSS: 9.1, Critical): Lapack versions through 3.10.0, also utilized in OpenBLAS prior to 0.3.18, contain out-of-bounds read flaws in the CLARRV, DLARRV, SLARRV, and ZLARRV functions. Crafted inputs to these functions can crash applications using Lapack or potentially expose memory.

SOCRadar Vulnerability Intelligence card of CVE-2021-4048
CVE-2023-45133 (CVSS: 8.8, High severity): A vulnerability in Babel, a JavaScript compiler, affects ‘@babel/traverse’ versions prior to 7.23.2 and 8.0.0-alpha.4, as well as all versions of ‘babel-traverse’. Crafted code by an attacker may trigger arbitrary code execution during compilation, especially when using plugins that rely on the internal path.evaluate() or path.evaluateTruthy() methods.
CVE-2023-43804 (CVSS: 8.1, High severity): Urllib3, a Python HTTP client library, lacks specific handling of the `Cookie` HTTP header and does not provide helpers for managing cookies. As a result, users may unknowingly expose information via HTTP redirects to different origins if redirects are not explicitly disabled. This issue is resolved in urllib3 versions 1.26.17 and 2.0.5.
CVE-2023-31484 (CVSS: 8.1, High severity): CPAN.pm before version 2.35 neglects TLS certificate verification when downloading distributions over HTTPS.
CVE-2023-38019 (CVSS: 8.1, High severity): The IBM SOAR QRadar Plugin App allows remote directory traversal. By sending a specially crafted URL request containing “/../” sequences, an attacker can view arbitrary files on the system.
The advisory notes that there are no known workarounds for these vulnerabilities; it is strongly recommended to apply the updates for specific Juniper Secure Analytics applications to resolve the vulnerabilities. For more information, refer to the official advisory.
Keep up to date on the latest developments in identified vulnerabilities and hacker trends by using SOCRadar’s Vulnerability Intelligence. If an exploit is discovered for a specific vulnerability, you can access this critical information via Vulnerability Intelligence.
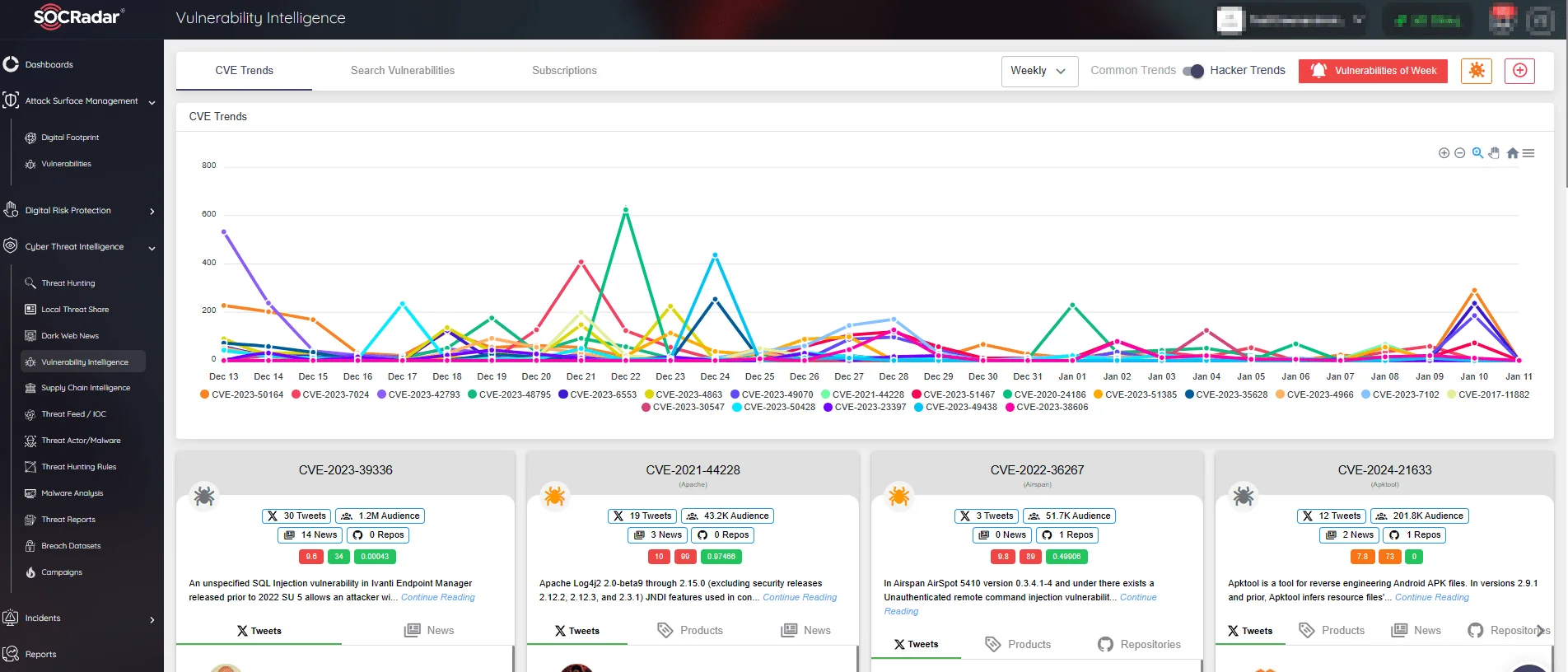
SOCRadar’s Vulnerability Intelligence
Critical Vulnerability in Mastodon Could Lead to Account Takeover (CVE-2024-23832)
Mastodon has recently disclosed a critical vulnerability, identified as CVE-2024-23832 (CVSS: 9.4). This vulnerability stems from an origin validation error, potentially allowing threat actors to impersonate and take control of remote accounts.
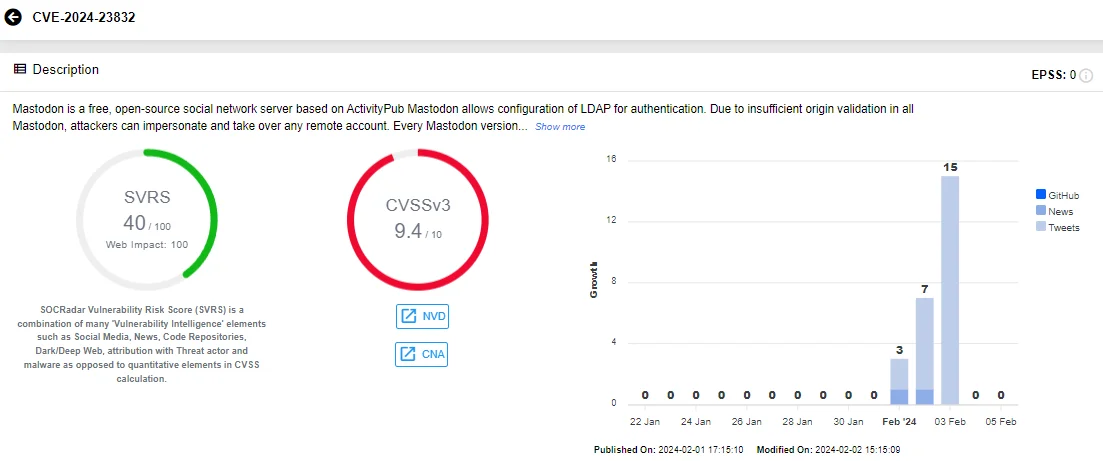
SOCRadar Vulnerability Intelligence card of CVE-2024-23832
CVE-2024-23832 affects all Mastodon versions prior to 3.5.17, including 4.0.x versions before 4.0.13, 4.1.x versions before 4.1.13, and 4.2.x versions before 4.2.5.
Mastodon, an open-source social network with independent servers/communities, operates similarly to Twitter. Differently, Mastodon operates on separate servers managed by individual administrators who establish their own rules; these admins must promptly update their Mastodon servers to prevent exploitation of the critical vulnerability.
The platform gained traction notably after Elon Musk’s acquisition of Twitter (now named X), with a significant portion of the security community recognizing Mastodon as the new Twitter for knowledge sharing.
According to the GitHub advisory, more details about the vulnerability will be released on February 15, 2024.
Mastodon has refrained from disclosing specific details about the vulnerability, credited to ‘arcaniscanis’ for its discovery, to provide administrators with sufficient time to update their servers before potential exploitation by threat actors.
Enhance Security Defenses with SOCRadar’s Attack Surface Management
SOCRadar provides ongoing surveillance of security vulnerabilities, offering timely insights for protecting organizational assets. Through the Attack Surface Management (ASM) module, you can access the details of vulnerabilities affecting your assets, facilitating patch prioritization.
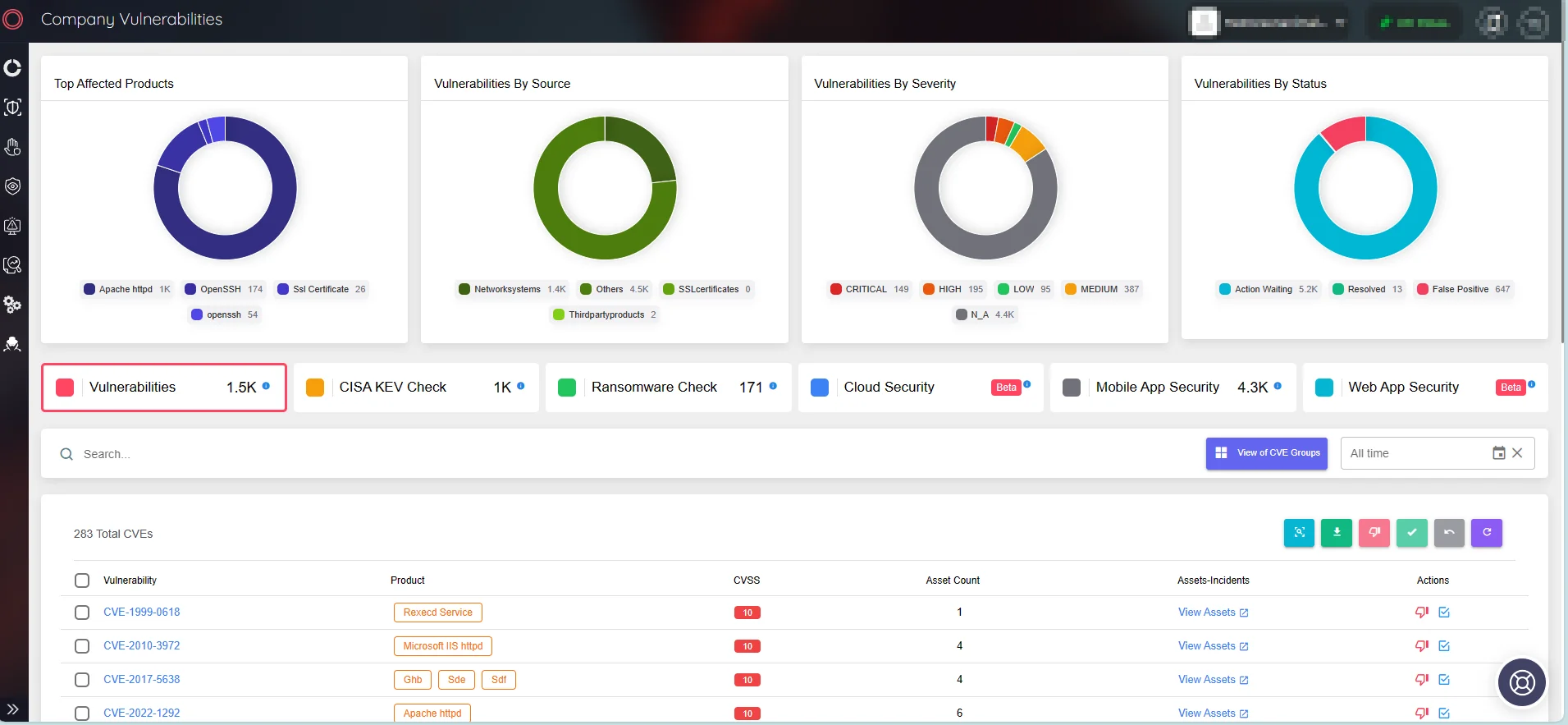
SOCRadar’s Attack Surface Management



































