
Lazarus Group’s Latest Cyber Espionage Tactics Involving LinkedIn
The Lazarus Group, a North Korean government-backed hacking team, has increased its spying efforts by taking advantage of work networking sites like LinkedIn. Their new attack hits people in the money and travel fields by pretending to be recruiters, wanting to use smart malware on many systems.
The Fake Job Hunt Tactic
The assault starts with a tempting LinkedIn note proposing to work together on projects linked to decentralized cryptocurrency exchanges. The proposition underlined appealing perks like remote work, part-time flexibility, and competitive pay to reel in potential victims. After expressing interest, the target is then asked by the fake recruiter for a CV or an associated link to their GitHub repository seemingly to assess qualifications. These requests serve as tactics to collect personal information and thereby establish legitimacy in the interaction.
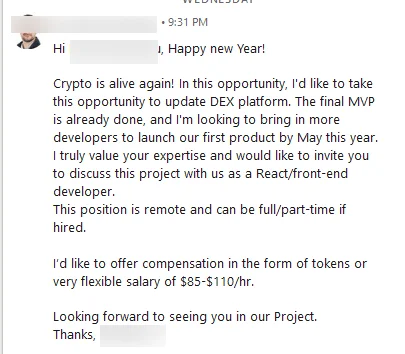
Example of a LinkedIn message sent by the attackers (BitDefender)
Cross-Platform Malware Deployment
After the initial contact, they share a purported minimum viable product for a decentralized exchange project via a GitHub or Bitbucket repository. This repository contains scripts with obfuscated code, which download next-stage payloads from a remote server. Cross-platform JavaScript information stealer, this tool infects Windows, macOS, and Linux systems. Its main purpose is to steal data from several cryptocurrency wallet extensions in the browser of the victim. The loader thief then acts as a means to install a Python-based backdoor on the victim machine, which can persist for remote access and allows monitoring of clipboard contents as well as downloading more malware components.
SOCRadar LABS Campaigns page
SOCRadar’s LABS Campaigns page provides detailed insights into a wide range of cyber threat actor campaigns, both ongoing and previous. Here, you can find Indicators of Compromise (IoCs) and in-depth analysis of various attack methods, including espionage tactics, malware, and more. For the latest intelligence and updates on campaign activities, visit the SOCRadar LABS Campaigns page.
Indicators of Compromise (IoCs)
To assist organizations in identifying potential compromises, several IoCs associated with this campaign have been identified:
Here is a table containing the IoCs (Indicators of Compromise) for easy reference:
| Category | IoCs |
| Domains | support.cloudstore[.]business
support.docsend[.]site |
| IP Addresses | 104.168.165[.]203
104.168.157[.]45 |
| URLs | hxxps://filedn[.]com/lY24cv0IfefboNEIN0I9gqR |
These IoCs can be utilized to enhance detection and prevention measures within organizational networks.
Cross-Platform Malware Deployment
After the initial contact, they share a purported minimum viable product for a decentralized exchange project via a GitHub or Bitbucket repository. This repository contains scripts with obfuscated code, which download next-stage payloads from a remote server. Cross-platform JavaScript information stealer, this tool infects Windows, macOS, and Linux systems. Its main purpose is to steal data from several cryptocurrency wallet extensions in the browser of the victim. The loader thief then acts as a means to install a Python-based backdoor on the victim machine, which can persist for remote access and allows monitoring of clipboard contents as well as downloading more malware components.
How It Can Be Mitigated
In order to guard against such sophisticated attacks, organizations and individuals should take the following measures:
- Careful Verification: Job offers, especially those proposing projects or asking for personal repositories, should be scrutinized.
- Code Analysis: Analyze thoroughly any code shared with you before running it to check for obfuscated or malicious scripts.
- Endpoint Protection: Advanced security solutions should be used that can identify and mitigate multi-stage malware across different operating systems.
Set up monitoring tools to catch unusual outbound traffic. This kind of activity might indicate data exfiltration or communication with malicious servers.
Enhancing Security with SOCRadar’s Extended Threat Intelligence Platform
In light of evolving cyber threats, leveraging comprehensive threat intelligence platforms is crucial. SOCRadar’s Extended Threat Intelligence (XTI) platform offers a unified solution to proactively identify and analyze threats with actionable intelligence. The platform comprises several modules designed to bolster security postures:
- Cyber Threat Intelligence: Provides real-time threat insights and deep contextual analysis, enabling organizations to stay ahead of potential threats.
- Attack Surface Management: Offers visibility into external-facing assets and services, identifying vulnerabilities that could be exploited by attackers.
- Brand Protection: Monitors for impersonating domains, brand abuse, and unauthorized use of brand assets, helping safeguard the organization’s reputation.
- Supply Chain Intelligence: Assesses risks associated with third-party vendors using advanced scoring systems, enabling proactive management of supply chain vulnerabilities.
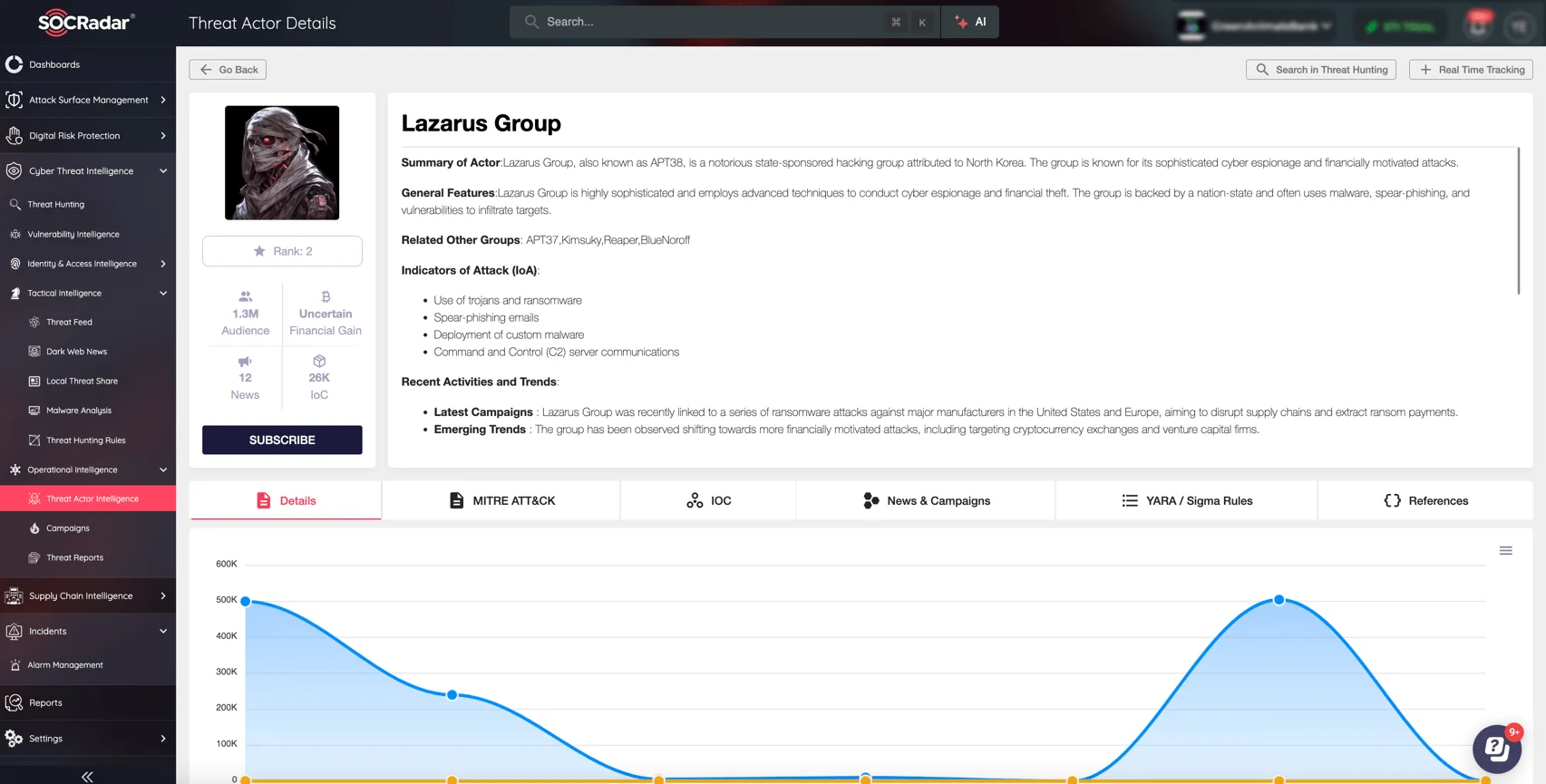
Details of Lazarus Group on the SOCRadar XTI platform (Threat Actor Intelligence, CTI module)
By integrating SOCRadar’s XTI platform into their cybersecurity strategy, organizations can enhance their defenses against sophisticated threats like those employed by the Lazarus Group, ensuring a more resilient security posture in an increasingly complex threat landscape.


































